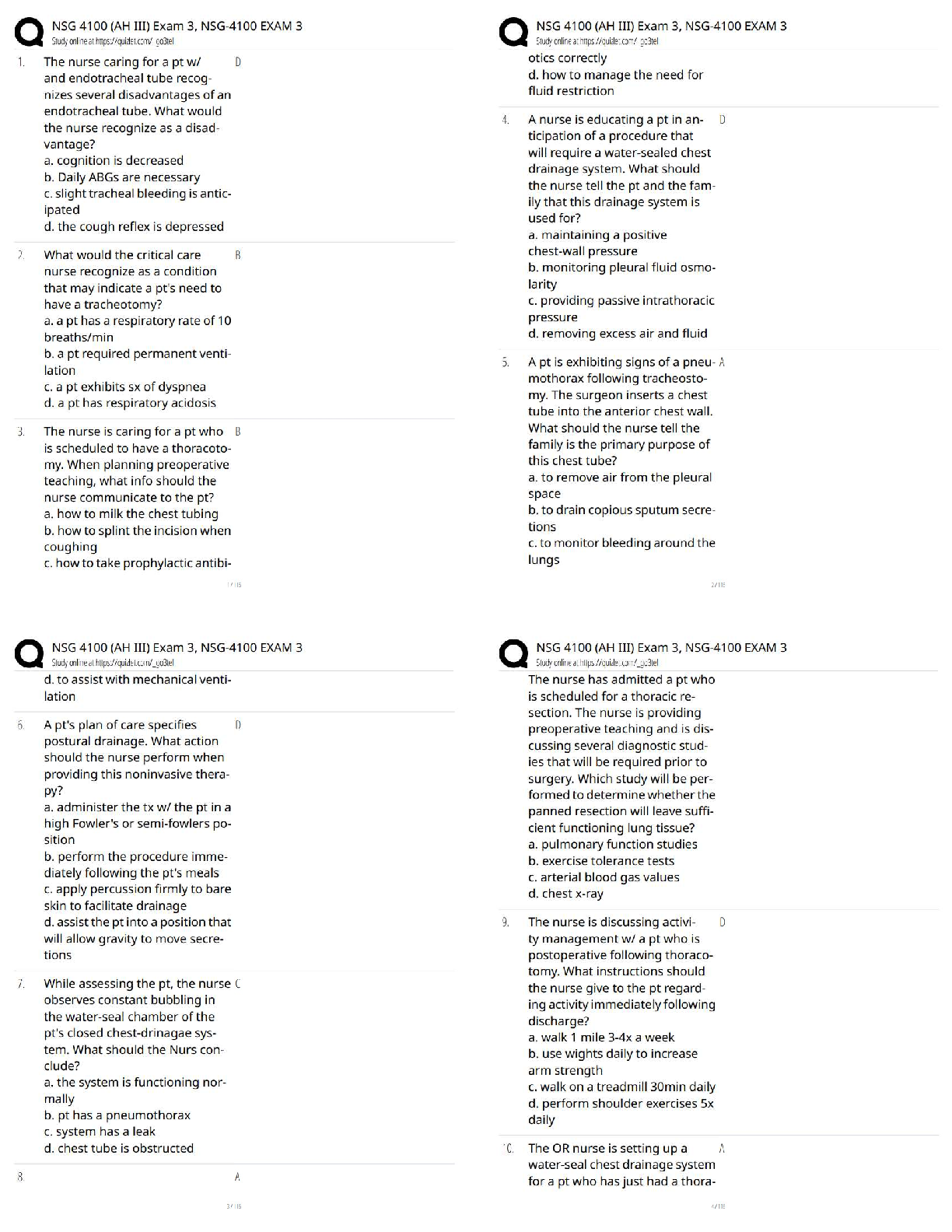
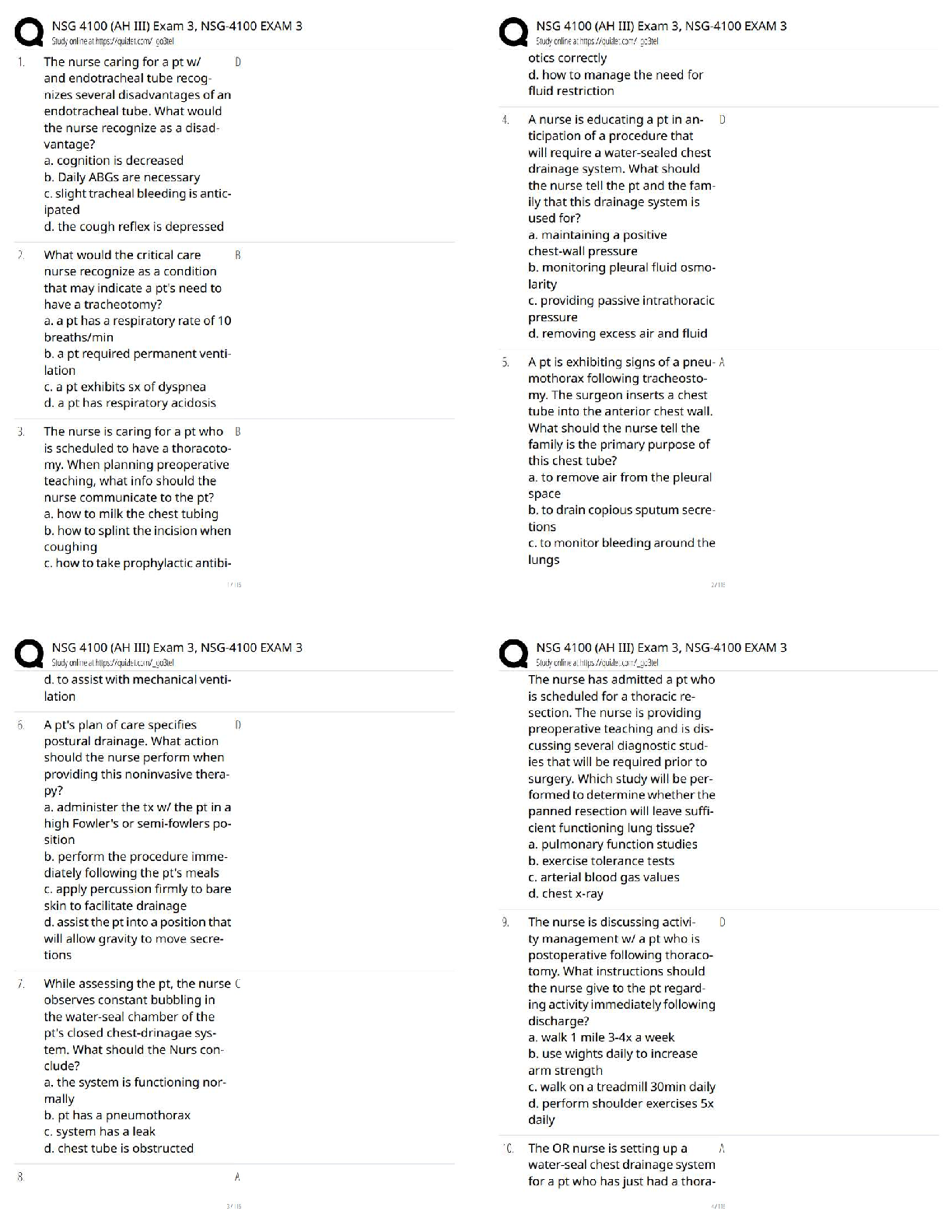
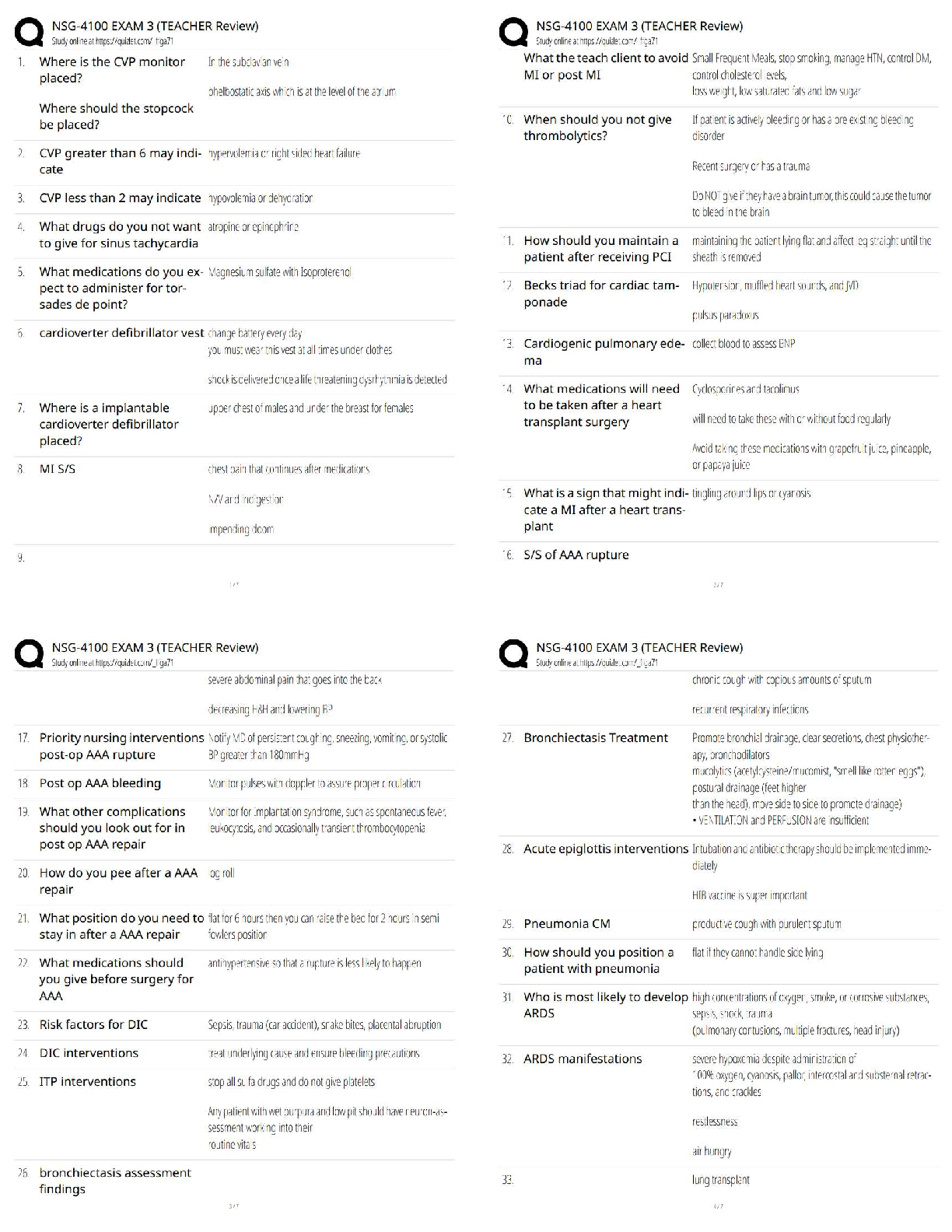
BCIS 2610 EXAM 3 UNT
Sending an e-mail that looks like it came from someone else in order to obtain information for
fraudulent purposes is called ____. - ✔✔phishing
True or False: Most spyware is installed on a PC wit
...
BCIS 2610 EXAM 3 UNT
Sending an e-mail that looks like it came from someone else in order to obtain information for
fraudulent purposes is called ____. - ✔✔phishing
True or False: Most spyware is installed on a PC without the user's knowledge - ✔✔True
Using someone else's identity to purchase goods or services or perform other transactions is
called ____ - ✔✔Identity Theft
You can find out if someone else has signed up for a credit card in your name by viewing your
____. - ✔✔credit report
True or False: A digital signature is used to encrypt the contents of an email message so it cannot
be understood if intercepted - ✔✔False
Digital certificates are obtained from a(n) ____. - ✔✔Certificate Authority
Repeated threats or other harassment carried out online is referred to as ____ - ✔✔Cyberstalking
True or False: Cyberstalkers often find their victims online - ✔✔True
Bullying an individual online is typically referred to as ____ - ✔✔Cyberbullying
Which of the following is not a common-sense precaution against cyberstalking? -
✔✔Monitoring your credit report
True or False: "Bikinigirl" would be a good name to avoid attracting unwanted attention in a chat
room - ✔✔False
____ occurs when someone sees a teen's explicit photo in a text message or on the Internet and
threatens to expose the teen's behavior unless the teen sends more explicit photos -
✔✔Sextortion
Which of the following laws refers to protecting health information stored electronically? -
✔✔HIPAA
True or False: It is virtually impossible to create laws that cover network and Internet security
issues today - ✔✔False
The ____ Act requires archiving a variety of electronic records and protecting the integrity of
corporate financial data - ✔✔SarbanesOxley
Which of the following is not a possible computer security concern? - ✔✔Sending a nonsensitive file via e-mail
True or False: All individuals should be concerned about security issues surrounding computers
and related technology - ✔✔True
Safeguarding a PC against theft and backing up files so that you do not lose important documents
are all computer _____ concerns - ✔✔Security
Which of the following would not likely be a reason for stealing a notebook PC? - ✔✔To use in
a denial of service (DoS) attack
True or False: It is only important to use a surge suppressor during bad weather, when a lightning
strike may occur - ✔✔False
A copy of a file that is created in case the original is damaged is called a(n) - ✔✔Backup
Using a computer to make illegal copies of currency to circulate as real currency is a form of
____. - ✔✔digital counterfeiting
True or False: Software piracy is rarely performed today - ✔✔False
is the unauthorized copying of a computer program - ✔✔Software piracy
Which of the following is a possible result of a data breach - ✔✔Damaged corporate reputation
and Expense of notifying the ind
[Show More]