Protect Your Clients - A Practical Guide
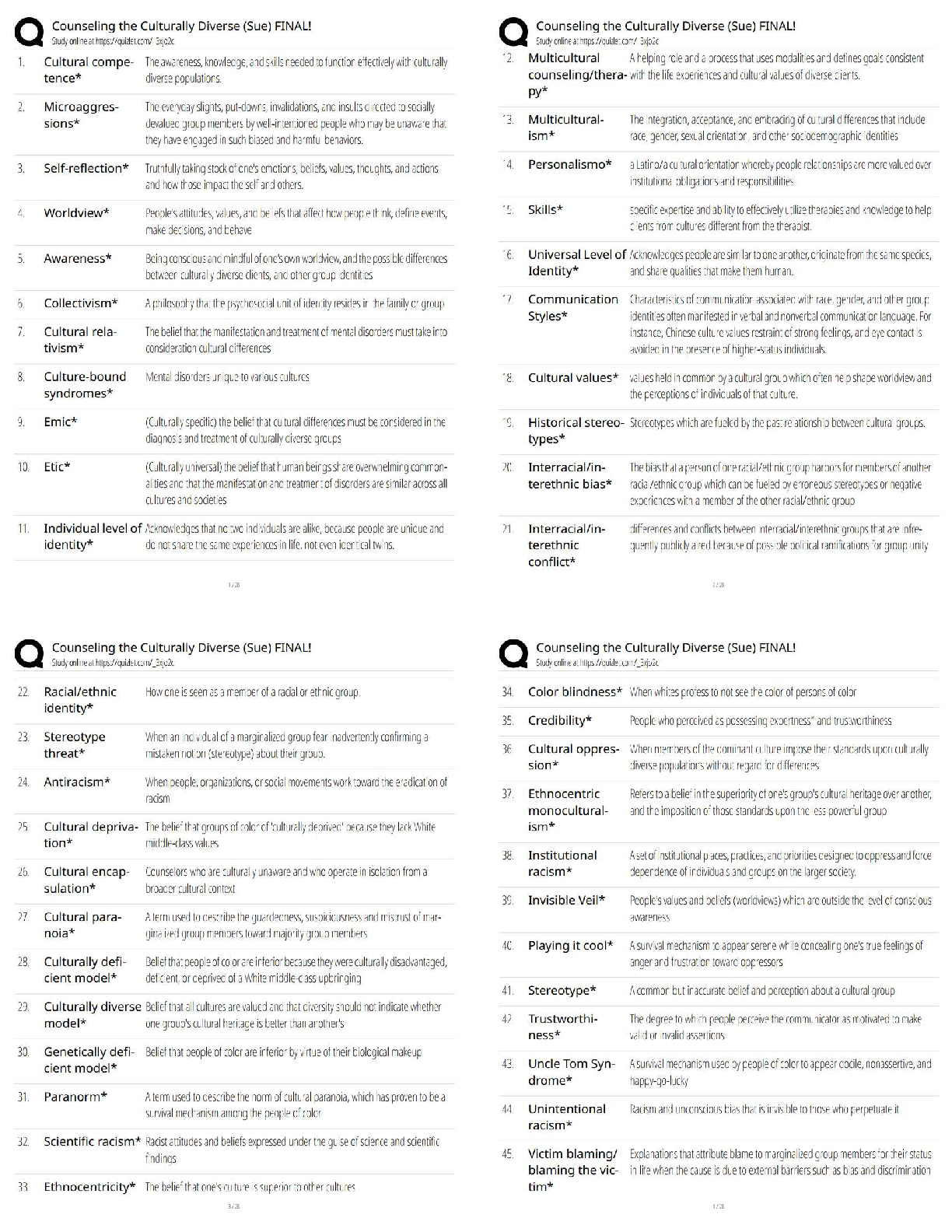
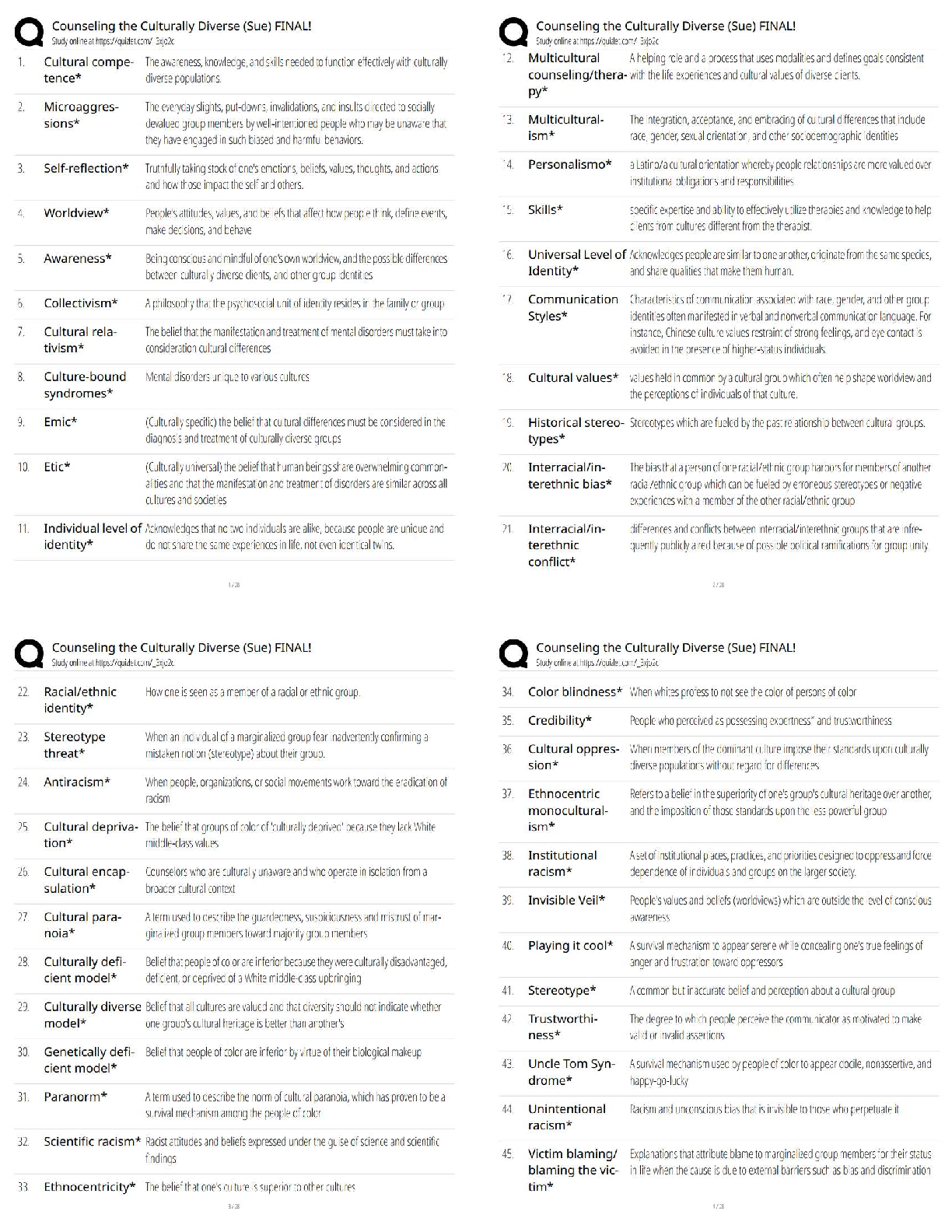
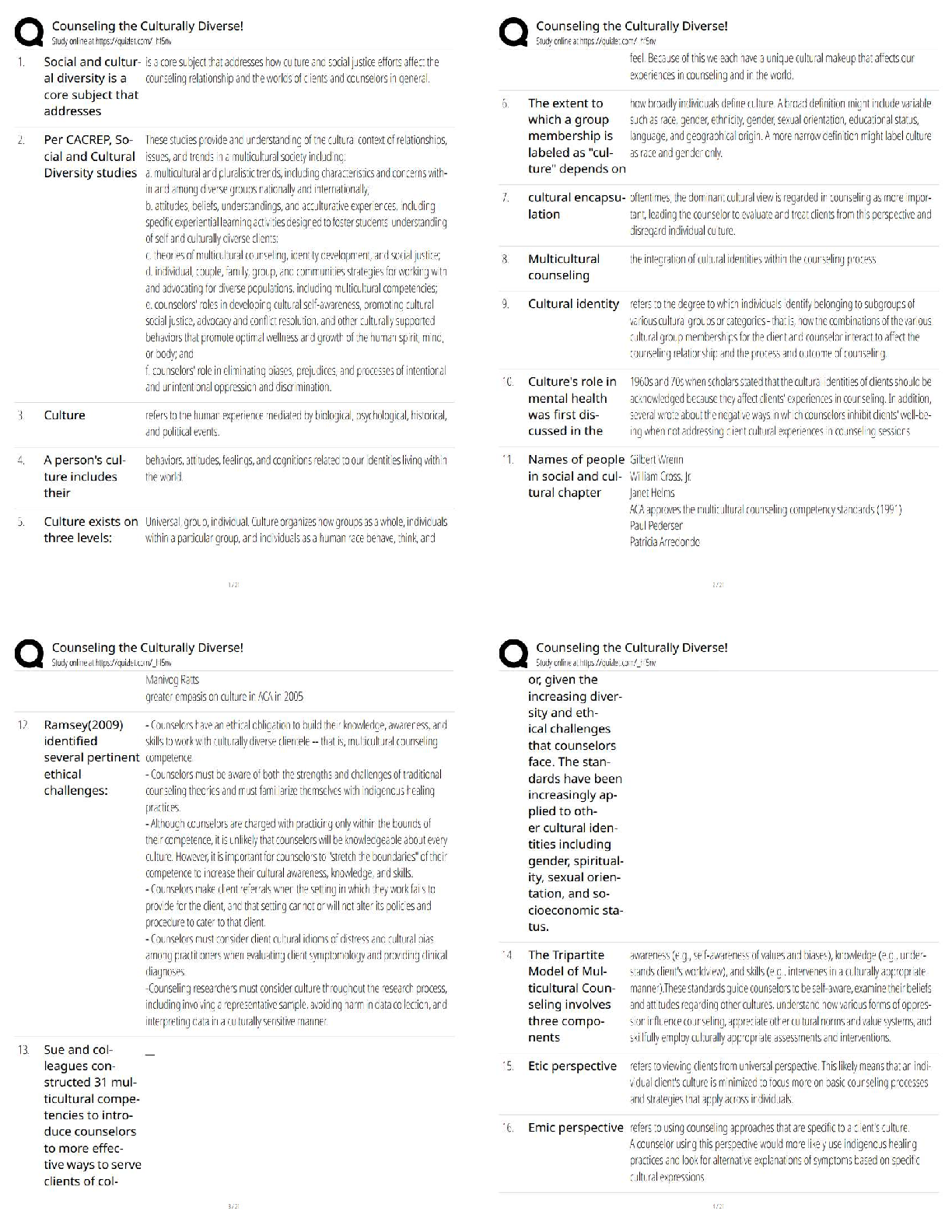
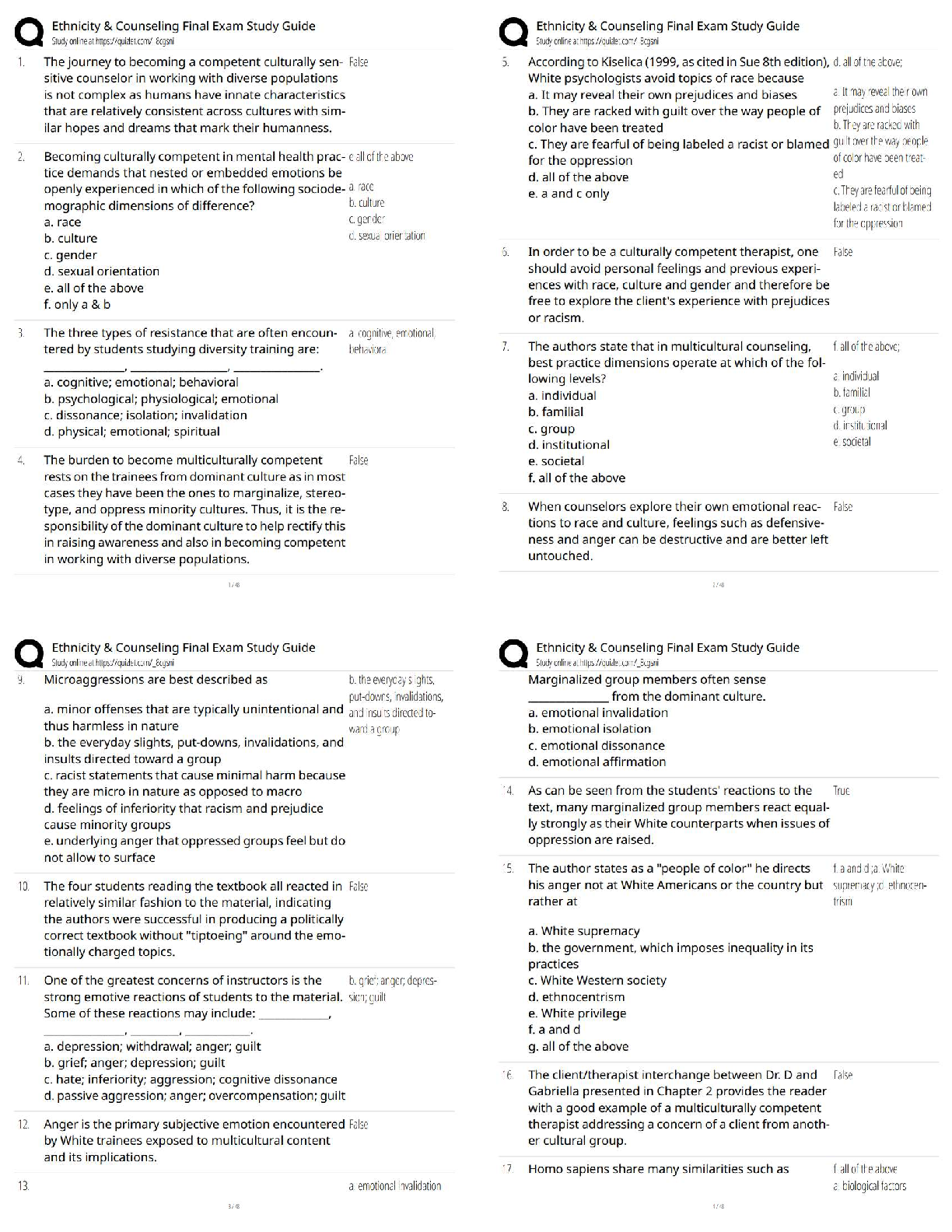
to Cybersecurity (Oregon)
Protect Your Clients - A Practical Guide to Cybersecurity (Oregon) ✔✔
Quiz 1: Reasons for Cybersecurity ✔✔
A hacker who can be hired to assist your c
...
Protect Your Clients - A Practical Guide
to Cybersecurity (Oregon)
Protect Your Clients - A Practical Guide to Cybersecurity (Oregon) ✔✔
Quiz 1: Reasons for Cybersecurity ✔✔
A hacker who can be hired to assist your company with identifying weaknesses in the
cybersecurity protections is known as a:
A) Grey Hat Hacker.
B) White Hat Hacker.
C) Hacktivist.
D) Black Hat Hacker. ✔✔B) White Hat Hacker.
White hat hackers are hackers who sell their services and skills to "test" the firewalls and
security methods your company has put in place. White hat hackers will not invade your
company's security mechanisms without approval; while grey hat hackers will breach systems
without permission before informing your company.
According to the National Cyber Security Alliance, what percentage of small or midsized
companies go out of business within six months of being hacked?
A) 30%
B) 50%
C) 60%
D) 90% ✔✔C) 60%
The NCSA estimates that some 60% of small and midsize companies go bankrupt within a half
year of being hacked. This is typically because the companies must pay for the forensics and
insurance.
Modern technology has begun to link digital consumer goods, such as cell phones, smart
printers, and computers, allowing machines to learn your patterns or otherwise connect all
devices together for ease of use. What is the term we use for this network?
A) The Internet of Things
B) The Smart Connect
C) The device-web
D) The Digital Network ✔✔A) The Internet of Things
The Internet of Things refers to the connected web of consumer digital devices. While the
Internet of Things can be convenient and assist a company's efficiency, it also opens up different
avenues for hackers to exploit vulnerabilities within that digital network.
All of the following are broad descriptions of cyber-attacks EXCEPT
A) attacks on integrity.
B) attacks on confidentiality.
C) attacks on availability.
D) attacks on personnel. ✔✔D) attacks on personnel.
Attacks on availability, confidentiality, and integrity are the broad descriptions of cyberattacks.
Attacks on availability limit access to networks, attacks on integrity limits the credibility of your
systems;,and attacks on confidentiality are violations of your company's privacy.
A real estate agent's email account was compromised. The hacker was able to send an email to a
client explaining that "last-minute closing changes" required a "correction" to a bank account
number being used to hold closing cost funds. The client followed the email's instructions and
transferred the money to pay for closing costs to the updated bank account.
When the client was contacted by the real estate agent and learned that the earlier email was a
spoof, they soon discovered that the transferred money had been removed from the account and
was unrecoverable. What would this sort of attack be considered?
A) Attack on availability
B) Attack on confidentiality
C) Advanced persistent threat
D) Attack on integrity ✔✔D) Attack on integrity
This would be an example of an attack on integrity because it uses the credibility of the real
estate agent's email account to convince the client to change closing information.
Quiz 2: Cyber Threats ✔✔
Which of the following best describes baiting?
A) Directing a client to transfer their closing funds to an escrow company
B) Sending an email with the subject line, "YOU ARE A WINNER!"
C) Intentionally leaving a trojan-infected USB device on the sidewalk
D) Searching for unsecured wifi networks to use as the source for an attack ✔✔C) Intentionally
leaving a trojan-infected USB device on the sidewalk
Baiting is oftentimes a very simple form of social engineering where a cd, laptop, or USB stick is
left in the open to tempt the victim into usi
[Show More]
.png)












.png)