Business Management > EXAM > WGU C702 pre-test CHFI v9 Questions and Answers,100% CORRECT (All)
WGU C702 pre-test CHFI v9 Questions and Answers,100% CORRECT
Document Content and Description Below
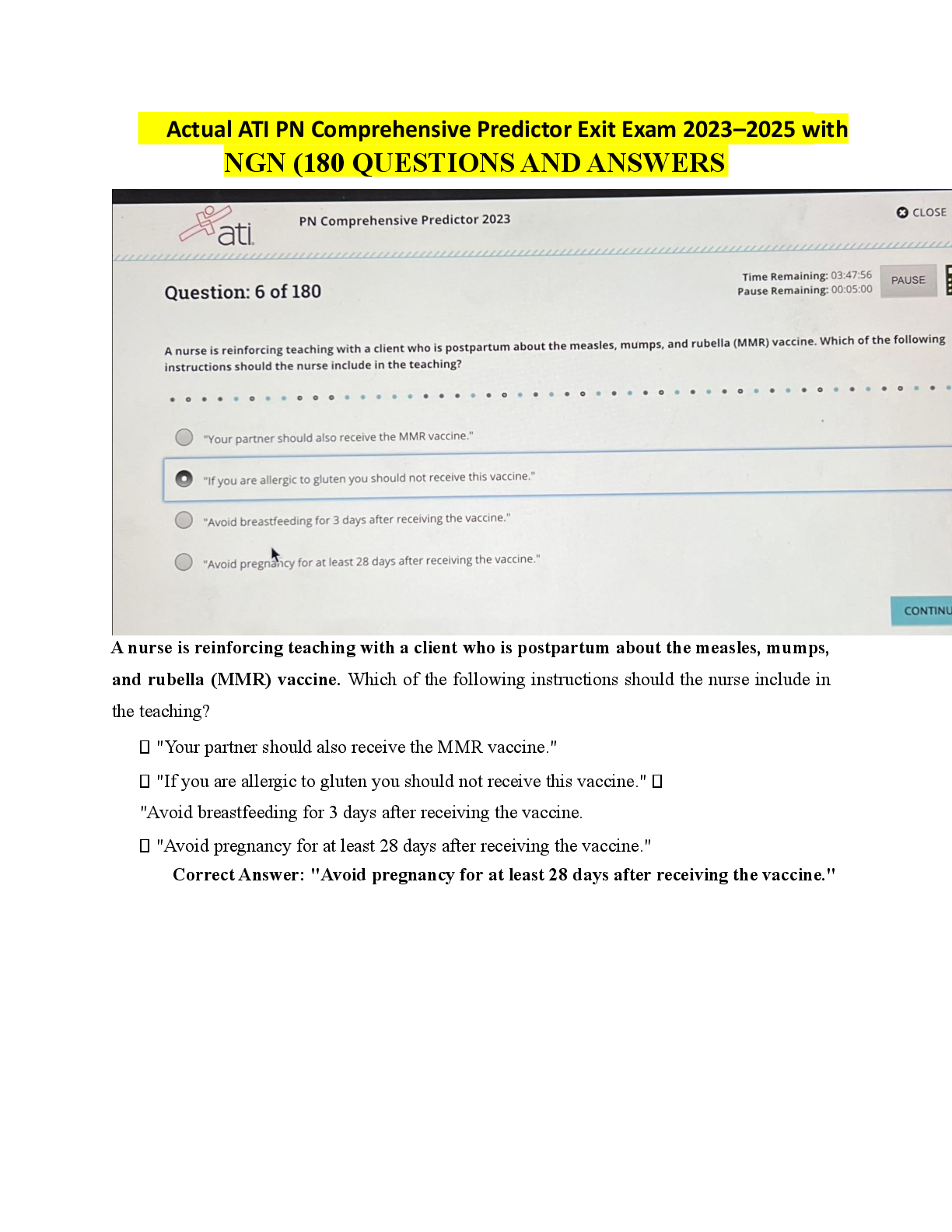
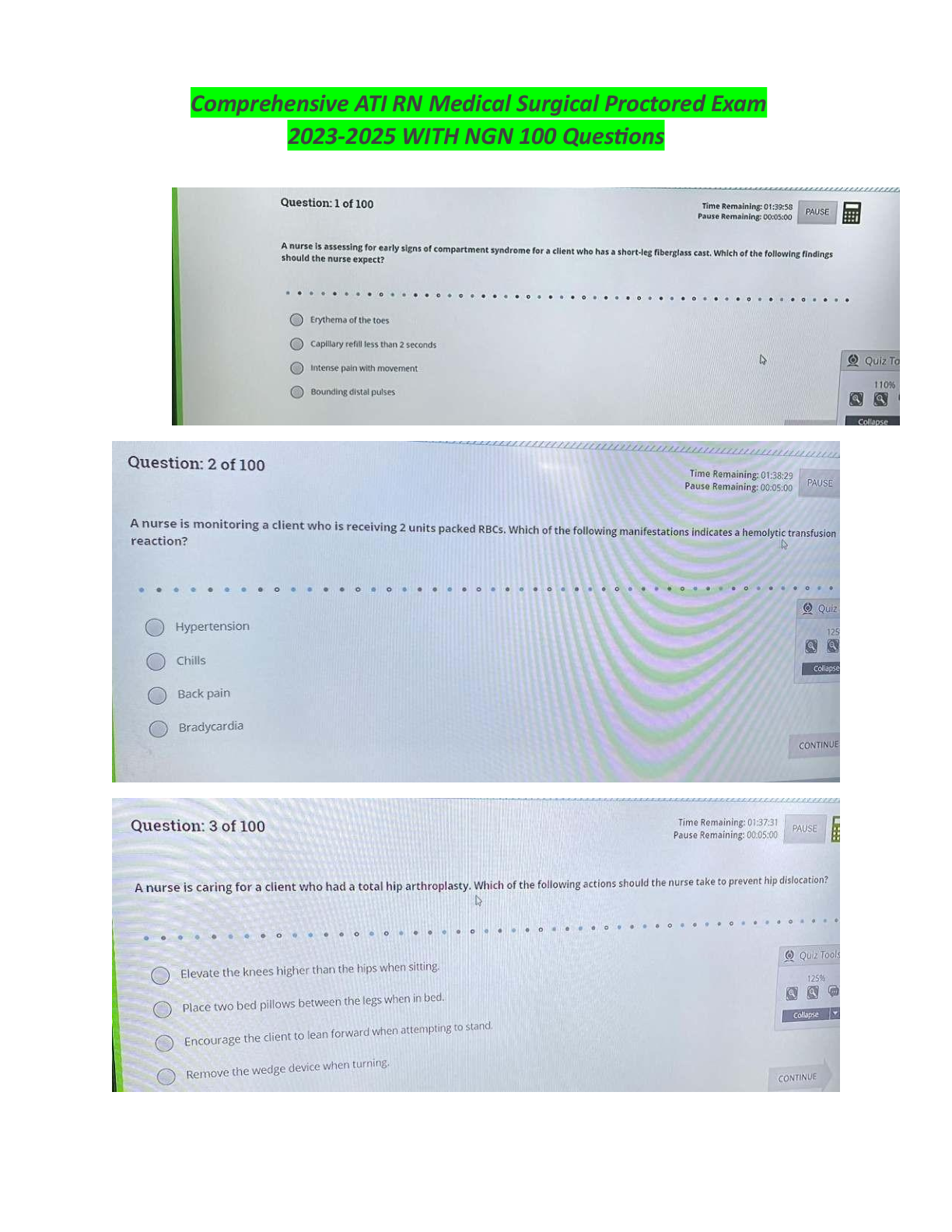
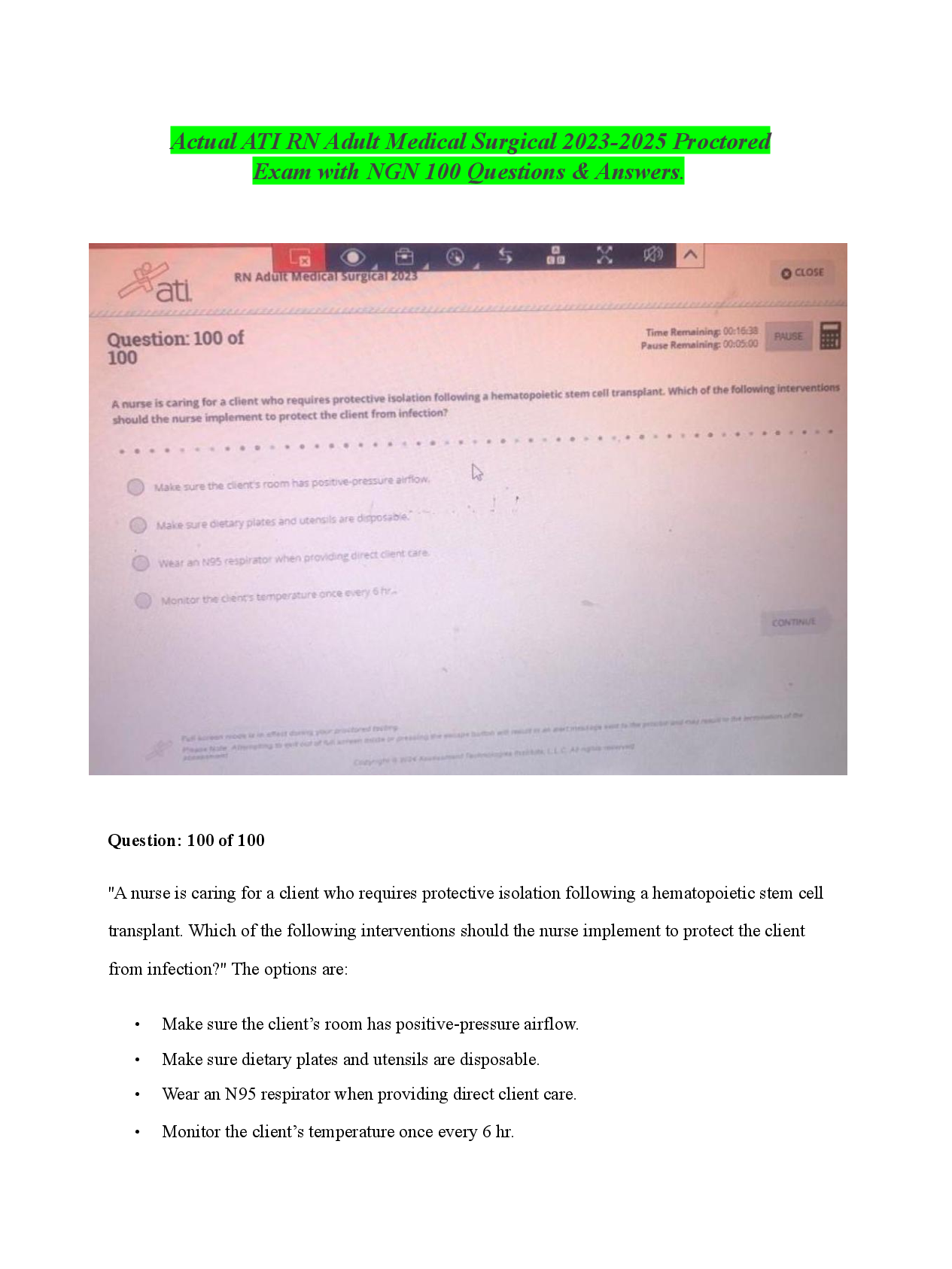
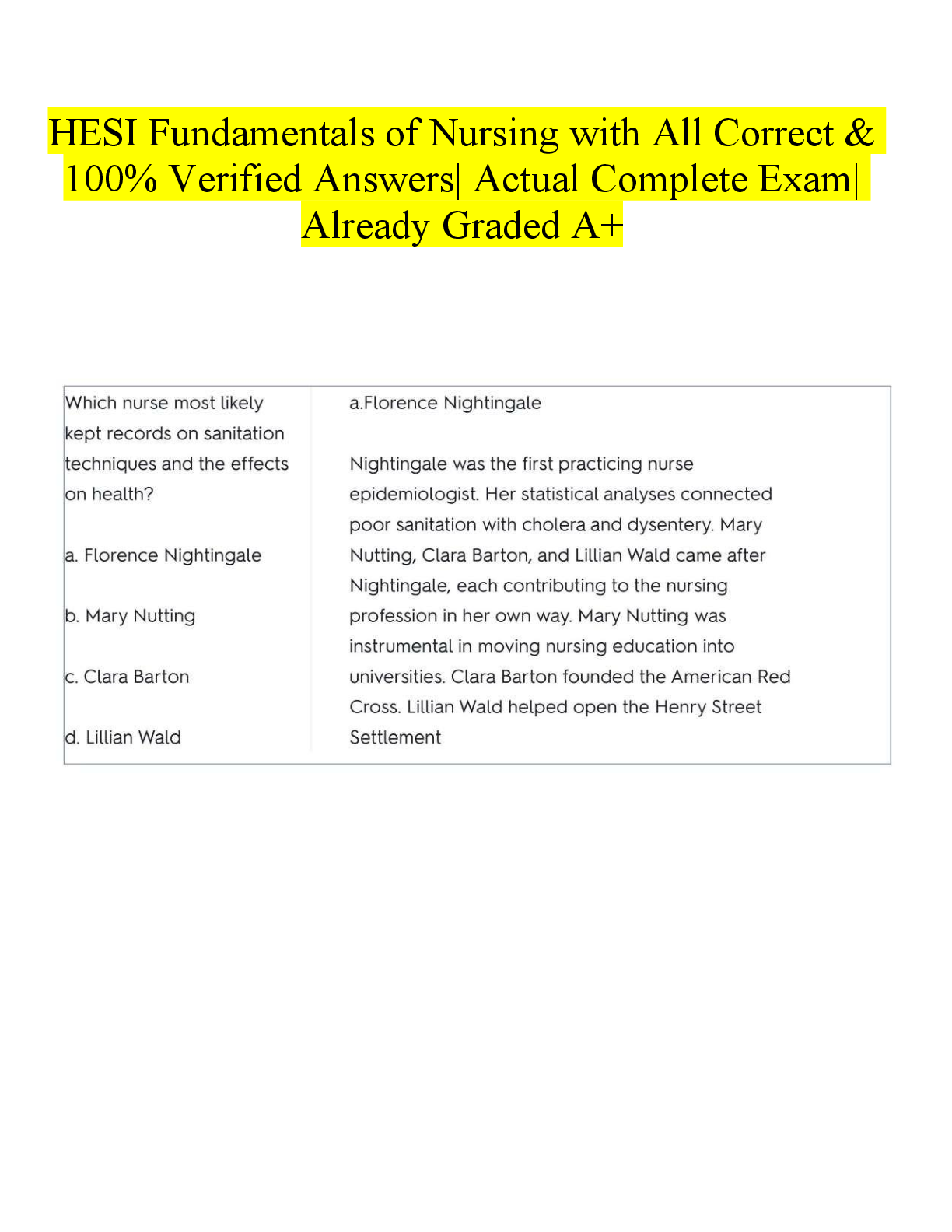
WGU C702 pre-test CHFI v9 Questions and Answers What is the role of an expert witness? to support the defense to educate the public and court to evaluate the court’s decisions to testify against ... the plaintif Under which of the following circumstances has a court of law allowed investigators to perform searches without a warrant? Expediting the process of obtaining a warrant may lead to a delay in prosecution of a perpetrator. Delay in obtaining a warrant may lead to the destruction of evidence and hamper the investigation process. Expediting the process of obtaining a warrant may lead to the timely prosecution of a perpetrator. Delay in obtaining a warrant may lead to the preservation of evidence and expedite the investigation process. Which of the following is NOT an objective of computer forensics? Interpret, document, and present the evidence to be admissible during prosecution. Track and prosecute the perpetrators in a court of law. Mitigate vulnerabilities to prevent further loss of intellectual property, finances, and reputation during an attack. Identify, gather, and preserve the evidence of a cybercrime. Forensic readiness refers to: an organization’s ability to make optimal use of digital evidence in a limited period and with minimal investigation costs. the establishment of specific incident response procedures and designated trained personnel to prevent a breach. having no impact on prospects of successful legal action. replacing the need to meet all regulatory requirements. Which of the following is true of cyber crimes? The claimant is responsible for the collection and analysis of the evidence. Investigators attempt to demonstrate information to the opposite party to support the claims and induce settlement. The searching of the devices is based on mutual understanding and provides a wider time frame to hide the evidence. Investigators, with a warrant, have the authority to forcibly seize the computing devices. Which of the following should be physical location and structural design considerations for forensics labs? Lab exteriors should have no windows. Room size should be compact with standard HVAC equipment. Light weight construction materials need to be used. Computer systems should be visible from every angle. Which of the following should be work area considerations for forensics labs? Additional equipment such as note pads, printers, etc., should be stored elsewhere. Physical computer examinations should take place in a separate workspace. Examiner station has an area of about 50-63 square feet. Multiple examiners should share workspace for efficiency. Which of the following is NOT part of the Computer Forensics Investigation Methodology? Testify as an expert defendant. data acquisition data analysis Testify as an expert witness. Which of the following is a user-created source of potential evidence? printer spool cookies log files address book Which of the following is a computer-created source of potential evidence? swap file spreadsheet steganography bookmarks Under which of the following conditions will duplicate evidence not suffice? when original evidence is in possession of the originator when original evidence is destroyed due to fire and flood when original evidence is in possession of a third party when original evidence is destroyed in the normal course of business Which of the following Federal Rules of Evidence ensures that the truth may be ascertained and the proceedings justly determined? Rule 103 Rule 102 Rule 105 Rule 101 Which of the following Federal Rules of Evidence states that the court shall restrict the evidence to its proper scope and instruct the jury accordingly? Rule 103 Rule 102 Rule 105 Rule 101 Which of the following is a consideration of HDDs but not SSDs? access time seek time RPM speed transfer time Which of the following is NOT an advantage of SSDs over HDDs? non-volatile memory faster data access higher reliability less power usage How many tracks are typically contained on a platter of a 3.5" HDD? 512 1000 2000 256 Which of the following is NOT a common computer file system? NTFS EFX3 EXT2 FAT32 Which of the following items is used to describe the characteristics of the file system information present on a given CD-ROM? volume descriptor POSIX attribute track header boot sector Which of the following file systems are used for adding more descriptors to a CD-ROM’s file system sequence? Romeo and MDF ISO 9660 ISO 13490 Joliet and UDF Which field type in a volume descriptor refers to a boot record? Number 2 Number 3 Number 0 Number 1 Which field type refers to the volume descriptor as a supplementary? Number 0 Number 2 Number 3 What do GPTs use instead of the addressing used in modern MBRs? Logical Block Addressing (LBA) Which of the following is one of the five UEFI boot process phases? RT Phase NTLdr Stage Which HFS volume structure is one of the boot blocks, which includes system startup information? Logical block 1 Logical block 2 Logical block 4 Logical block 3 Which HFS volume structure is the starting block of the volume bitmap? Logical block 1 Logical block 2 Logical block 4 Logical block 3 Which file system is utilized by UNIX operating systems and derived from the Berkeley Fast File System? HPFS HTFS ZFS UFS What UFS file system part includes a magic number identifying the file system and vital numbers describing the file system’s geometry and statistics and behavioral tuning parameters? data groups boot blocks cylinder groups super block Which of the following is one of the features added to HFS Plus? supports files 16 bits in length permits file names of 256 characters uses 16-bit allocation for the mapping table uses B-tree to store the data What is a technology that uses multiple smaller disks simultaneously that function as a single large volume? SSD RAID HDD DEET What is the RAID level which is the only level that does not implement one of the standard techniques of parity, mirroring, or striping, but uses a technique similar to striping with parity? RAID 2 RAID 0 RAID 1 RAID 3 What is a computing standard developed along with the UCS standard for encoding, representation, and management of texts, and provides a unique number for every character irrespective of the platform, program, or language? UNICODE .NET XML JAVA What is a lossless image format intended to replace older formats and is copyright and license free? BMP PNG JPEG GIF What is the proprietary Microsoft Office text file extension used in Word? TXT PDF DOC/DOCX RTF What is the proprietary Microsoft Office spreadsheet file extension used in Excel? PDF XLS/XLSX RTF TXT Which command from The Sleuth Kit (TSK) displays general details of a file system? istat fls img_stat fsstat Which command from The Sleuth Kit (TSK) lists the files and directory names in an image and can display file names of recently deleted files for the directory using the given inode? img_stat istat fls fsstat Where are deleted items stored on Windows 98 and earlier versions of Windows? Drive:\RECYCLED Drive:\$Recycle.Bin Drive:\RECYCLER Drive:\Recycle.Bin$ What is the maximum size limit for the Recycle Bin in Windows prior to Windows Vista? 0 3.99 GB 3.99 MB None What tool is used for format recovery, unformatting, and recovering deleted files emptied from the Recycle Bin or data lost due to partition loss or damage, software crash, virus infection, or unexpected shutdown and supports hardware RAID? Quick Recovery EaseUS DiskDigger FileSalvage Which tool recovers files that have been lost, deleted, corrupted, or even deteriorated? Quick Recovery DiskDigger EaseUS Recover My Files What tool for Mac recovers files from a crashed or virus-corrupted hard drive? DiskDigger Recover My Files EaseUS FileSalvage Which of the following consists of volatile storage? RAM ROM hard drive compact disc What is NOT a command used to determine open files? Net file PsFile Openfiles Open files Which tool helps collect information about network connections operative in a Windows system? Ipconfig Nbtstat Netstat Ifconfig Which is a completely open collection of tools, implemented in Python under the GNU General Public License, for the extraction of digital artifacts from volatile memory (RAM) samples? Volatile Extractor Volatility Framework Volatility Extractor Volatile Framework What prefetch does value 1 from the registry entry, EnablePrefetcher, tell the system to use? Both application and boot-prefetching are enabled. Application prefetching is enabled. Boot prefetching is enabled. Prefetching is disabled. What prefetch does value 3 from the registry entry, EnablePrefetcher, tell the system to use? Both application and boot-prefetching are enabled. Prefetching is disabled. Boot prefetching is enabled. Application prefetching is enabled. What tool enables you to retrieve information about event logs and publishers in Windows 10? Regedit EventViewer Wevtutil Msconfig Which is NOT a log management system function? log reduction log compression log conversion log generation What is NOT one of the three major concerns regarding log management? log creation and storage log viewing log analysis log protection and availability Which is a type of network-based attack? eavesdropping phishing social engineering spamming Which is NOT a valid type of digital evidence? text file application data executable file DNA sample What type of analysis do investigators perform to detect something that has already occurred in a network/device and determine what it is? real-time analysis past-time analysis premortem postmortem Which of the following is an internal network vulnerability? spoofing enumeration eavesdropping bottleneck Where can Congressional security standards and guidelines be found, with an emphasis for Federal agencies, for the development, documentation, and implementation of organization-wide programs for information security? HIPAA FISMA GLBA PCI DSS Which of the following includes security standards for health information? PCI DSS HIPAA FISMA GLBA What is a proprietary information security standard for organizations that handle cardholder information for major debit, credit, prepaid, e-purse, ATM, and POS cards? GLBA PCI DSS SOX FISMA Which is NOT an indication of a web attack? access denied to normally available web services web pages redirected to an unknown website network performance being unusually slow logs found to have no known anomalies Which of the three different files storing data and logs in SQL servers is optional? MDF NDF PDF LDF What file format is used by Windows Vista and later versions to store event logs as simple text files in XML format? TXTX EVTX .log .txt What layer of web application architecture contains components that parse the request (HTTP Request Parser) coming in and forwards the response back? web server layer client layer database layer business layer What layer of web application architecture is composed of cloud services which hold all commercial transactions and a server that supplies an organization’s production data in a structured form? business layer web server layer client layer database layer Which web application threat refers to the modification of a website’s remnant data for bypassing security measures or gaining unauthorized information? information leakage bufer overflow SQL injection cookie poisoning Which web application threat refers to vulnerable management functions, including user updates, recovery of passwords, or resetting passwords? broken account management cookie poisoning SQL injection bufer overflow Which web application threat occurs when attackers insert commands via input data and are able to tamper with the data? bufer overflow SQL injection cookie poisoning denial-of-service Which web application threat is a method intended to terminate website or server operations by making resources unavailable to clients? cookie poisoning bufer overflow SQL injection denial-of-service Which web application threat occurs when attackers bypass the client’s ID security mechanisms, gain access privileges, and inject malicious scripts into specific fields in web pages? SQL injection bufer overflow cookie poisoning cross-site scripting Which web application threat occurs when an authenticated user is forced to perform certain tasks on the web application chosen by an attacker? cookie poisoning cross-site request forgery SQL injection bufer overflow What cloud service enables subscribers to use fundamental IT resources, such as computing power, virtualization, data storage, network, etc., on demand? IaaS AaaS SaaS PaaS What cloud service offers application software to subscribers on demand, over the internet, and the provider charges by a pay-per-use basis, subscription, advertising, or sharing among multiple users? AaaS IaaS PaaS SaaS What is a cloud environment composed of two or more clouds that remain unique entities but are bound together to offer the benefits of multiple deployment models? Private Cloud Hybrid Cloud Community Cloud Public Cloud Which cloud environment allows the provider to make services—such as applications, servers, and data storage—available to the public over the internet? Community Cloud Public Cloud Hybrid Cloud Private Cloud Which of the following stakeholders is responsible for conducting forensic examinations against allegations made regarding wrongdoings, found vulnerabilities, and attacks over the cloud? incident handlers law advisors investigators IT professionals Which of the following stakeholders is responsible for making sure all the forensic activities are within the jurisdiction and not violating any regulations or agreements? investigators law advisors IT professionals incident handlers Which is a violation of the Controlling the Assault of Non-Solicited Pornography and Marketing Act? taking advantage of open relays or open proxies with permission accessing someone else’s computer to send spam mails with permission using legitimate information to register for multiple email accounts or domain names retransmitting spam messages through a computer to mislead others about the origin of the message What is the primary information required for starting an email investigation? the SMTP log the date and time the unique message the unique IP address What is NOT true of email crimes? Email crime is not limited by the email organization. Communication can occur without human intervention. Forging the email header can hide the attacker’s identity. Unsolicited commercial email is considered spam. What is a common technique used to distribute malware on the web by injecting malware into legitimate-looking websites to trick users into selecting them? Blackhat SEO drive-by downloads click-jacking malvertising What is a common technique used to distribute malware on the web by mimicking legitimate institutions in an attempt to steal passwords, credit cards, and bank account data? drive-by downloads malvertising Blackhat SEO spear phishing sites What is a common technique used to distribute malware on the web when an attacker exploits flaws in browser software to install malware just merely by visiting a website? click-jacking drive-by downloads Blackhat SEO malvertising Which architectural layer of mobile-device environments simplifies the process of interacting with web services and other applications such as email, internet, and SMS? client application communication API GUI API phone API Which architectural layer of mobile-device environments contains items that are responsible for mobile operations such as a display device, keypad, RAM, flash, embedded processor, and media processor? hardware communication API client application operating system What operating system was Android based on? Windows Linux iOS Mac What must an investigator do in order to offer a good report to a court of law and ease the prosecution? authorize the evidence prosecute the evidence obfuscate the evidence preserve the evidence Which of the following is NOT a digital data storage type? magnetic storage devices quantum storage devices flash memory devices optical storage devices Which of the following best describes Flash Memory? Flash Memory is expensive and less efficient compared to other storage devices. Flash Memory is a non-volatile, electronically erasable and reprogrammable storage medium. Flash Memory is used in all SCSI hard drives. Flash Memory is a volatile, electronically erasable and reprogrammable storage medium. Where are deleted items stored on Windows Vista and later versions of Windows? Drive:\Recycle.Bin$ Drive:\$Recycle.Bin Drive:\RECYCLED Drive:\RECYCLER [Show More]
Last updated: 2 years ago
Preview 1 out of 22 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$15.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Feb 02, 2023
Number of pages
22
Written in
All
Additional information
This document has been written for:
Uploaded
Feb 02, 2023
Downloads
0
Views
167