Social Sciences > QUESTIONS & ANSWERS > SPēD SFPC - Study Guide 2022/2023 (questions and answers 100% correct) (All)
SPēD SFPC - Study Guide 2022/2023 (questions and answers 100% correct)
Document Content and Description Below
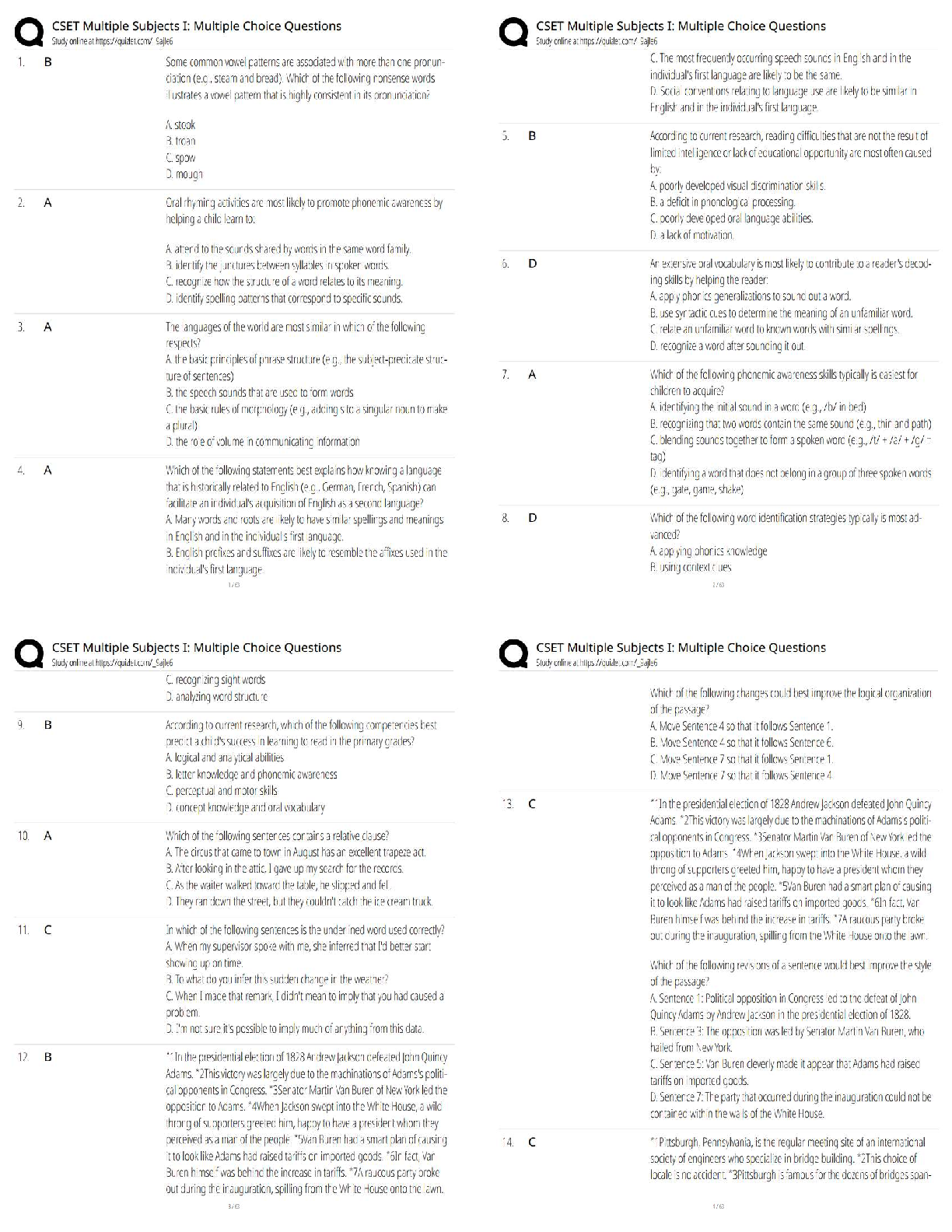
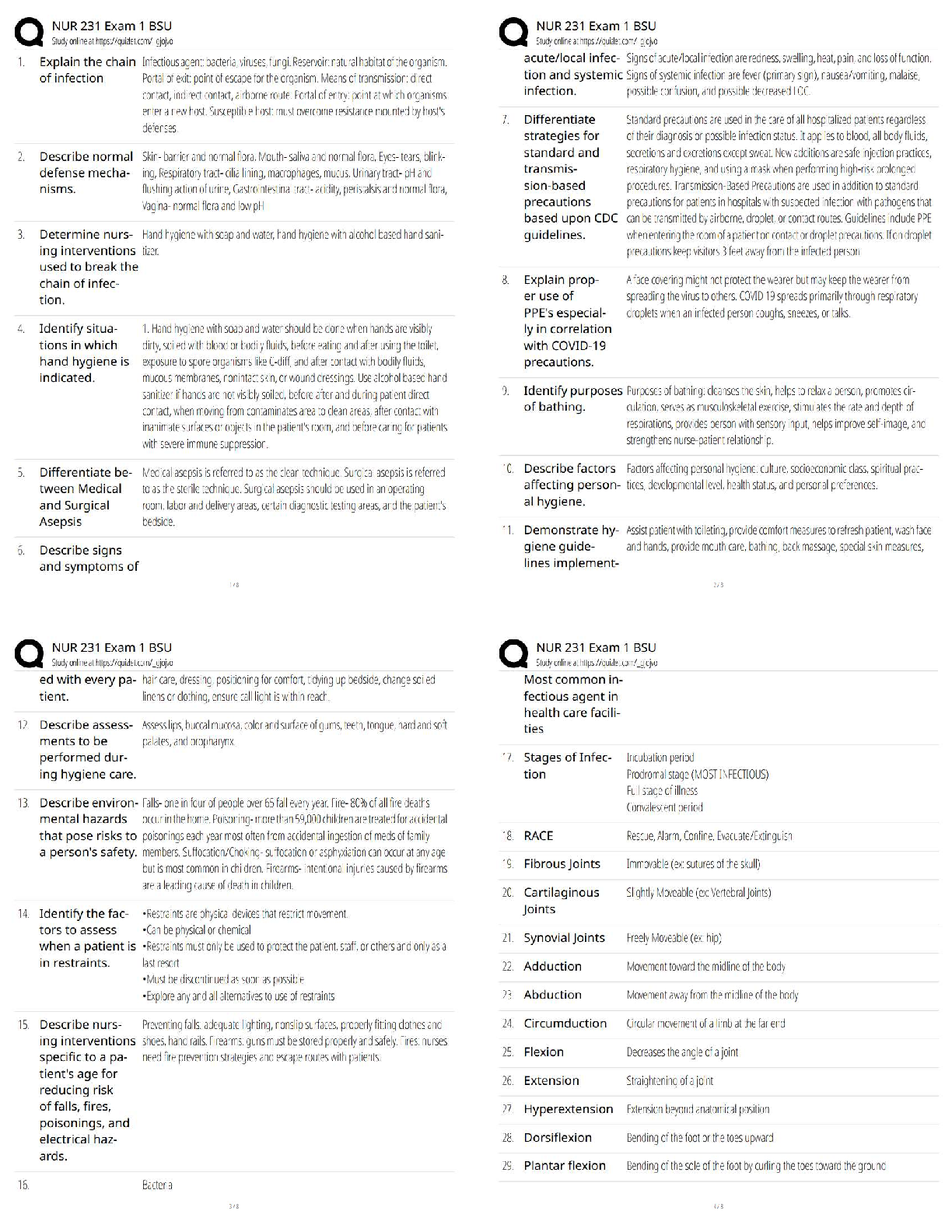
SPēD SFPC - Study Guide 2022/2023 (questions and answers 100% correct) Tier 1 investigations are conducted for positions designated as ✔Ans✔ - Low-risk, nonsensitive, and for physical and log ... ical access; HSPD-12 credentialing - Has a basic scope of five years - Investigative form is SF-85 - Replaces NACI Tier 2 investigations are conducted for positions designated as ✔Ans✔ - Nonsensitive, moderate risk public trust. - Has a basic scope of five years - Investigative form is SF-85P. - Replaces the Moderate-Risk Background Investigation, or MBI. Tier 3 investigations are conducted for positions designated as ✔Ans✔ - Noncritical-sensitive, and/or requiring Confidential, Secret or DOE " L " access eligibility and military accessions. - Has a basic scope of five years - The investigative form is SF-86 - Replaces NACLC and ANACI Tier 4 investigations are conducted for positions designated as ✔Ans✔ - Nonsensitive, high-risk public trust. - Has a basic scope of five to seven years - The investigative form is SF-85P - Replaces Background Information (BI) Tier 5 investigations are conducted for positions designated as ✔Ans✔ - Critical-sensitive or special-sensitive and/or requiring DOE "Q" access or access to Top Secret or Sensitive Compartmented Information, or SCI. - Has a basic scope of five to seven years - The investigative form is SF-86 - Replaces Single Scope Background Investigation (SSBI) The Statement of Reasons (SOR) contains ✔Ans✔ - A comprehensive and detailed written explanation of the basis for the unfavorable determination. - An explanation of the subject's rights and a detailed statement explaining the intent (Letter of Intent (LOI)) to deny or revoke a security clearance eligibility by the DoD Consolidated Adjudications Facility (DoD CAF). The Executive Orders: E.O. 12968 establishes ✔Ans✔ A uniform federal Personnel Security Program for employees who are considered for initial or continued access to classified information Automated Access Control Systems (AACS) fall into three general types ✔Ans✔ - Coded device (keypad/PIN code) - Credential devices (smart card/CAC) - Biometric devices (hand geometry, fingerprint, facial recognition, iris pattern, voice verification, and retinal scanning) Secret classification definition ✔Ans✔ Information that could be expected to cause serious damage to the national security if unauthorized disclosure occurs. Confidential classification definition ✔Ans✔ Information that reasonably could be expected to cause damage to the national security if unauthorized disclosure occurs Top Secret classification definition ✔Ans✔ Information that reasonably could be expected to cause exceptionally grave damage to the national security if unauthorized disclosure occurs. Compilation ✔Ans✔ Items of information that are individually unclassified or classified at a lower level, may be classified, or classified at a higher level, only if the compiled information reveals an additional association or relationship. [Show More]
Last updated: 2 years ago
Preview 1 out of 28 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Also available in bundle (1)
Click Below to Access Bundle(s)

SFPC Exams Bundled Together with complete solutions Questions and Answers (Verified Answers)(Full Solution Pack)
SFPC Exam Prep with 100% correct answers 2022/2023 SFPC Exam Prep with 100% correct answers 2022/2023 SPēD SFPC - Study Guide 2022/2023 (questions and answers 100% correct) SFPC Practice Test...
By Crescent 2 years ago
$14
5
Reviews( 0 )
$9.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Feb 13, 2023
Number of pages
28
Written in
All
Additional information
This document has been written for:
Uploaded
Feb 13, 2023
Downloads
0
Views
173




 Answered 2023.png)