Qualys Vulnerability Management Self-Paced Training Exam 2023 with complete solution
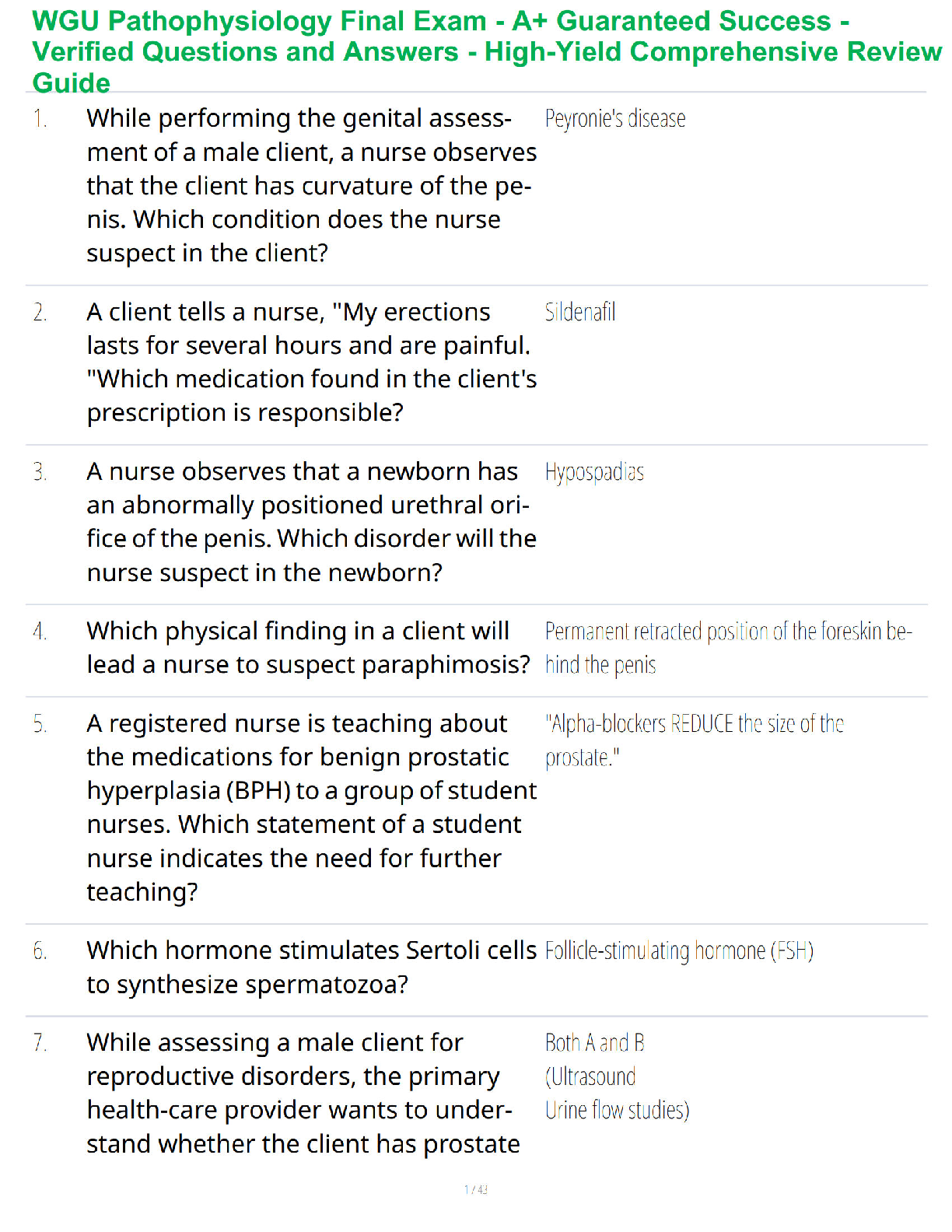
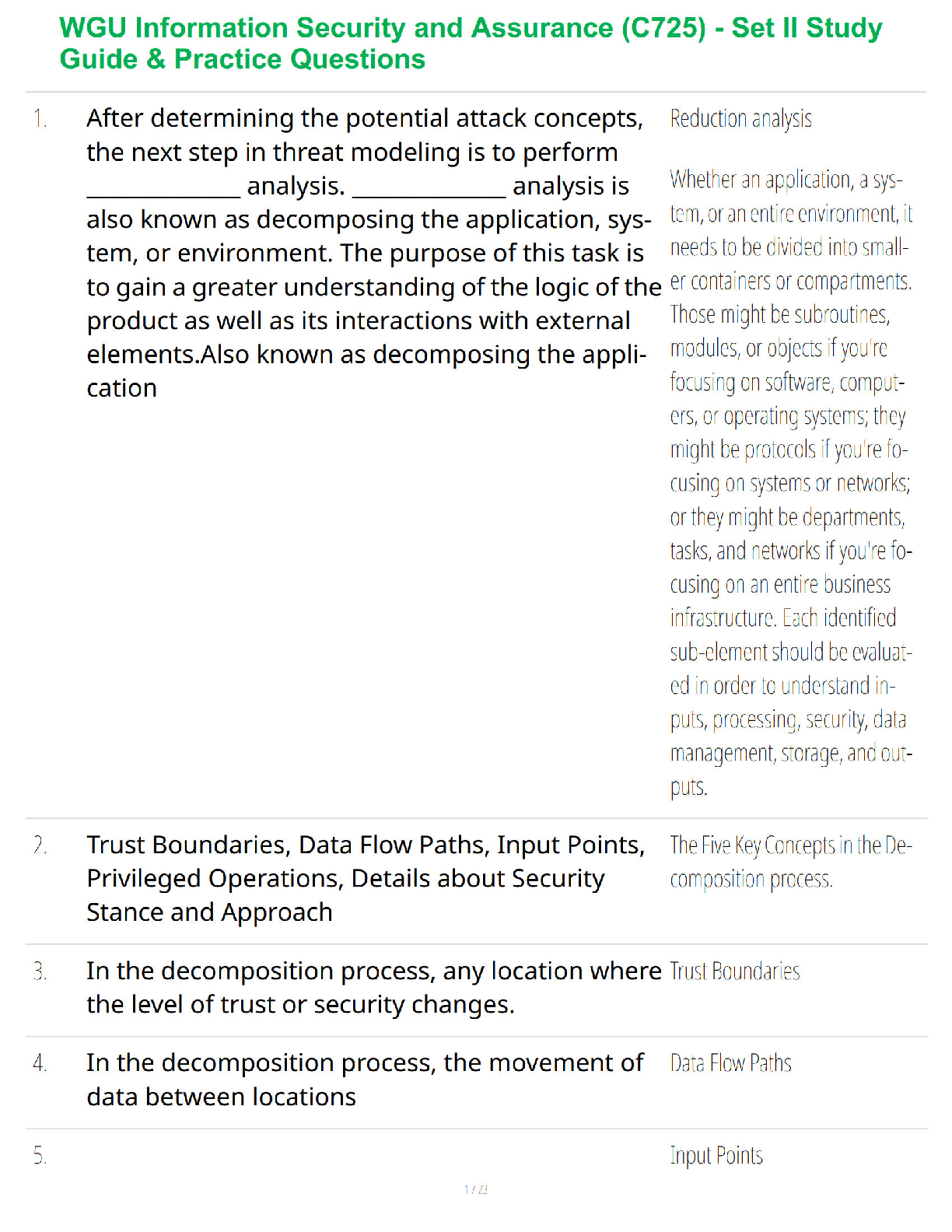
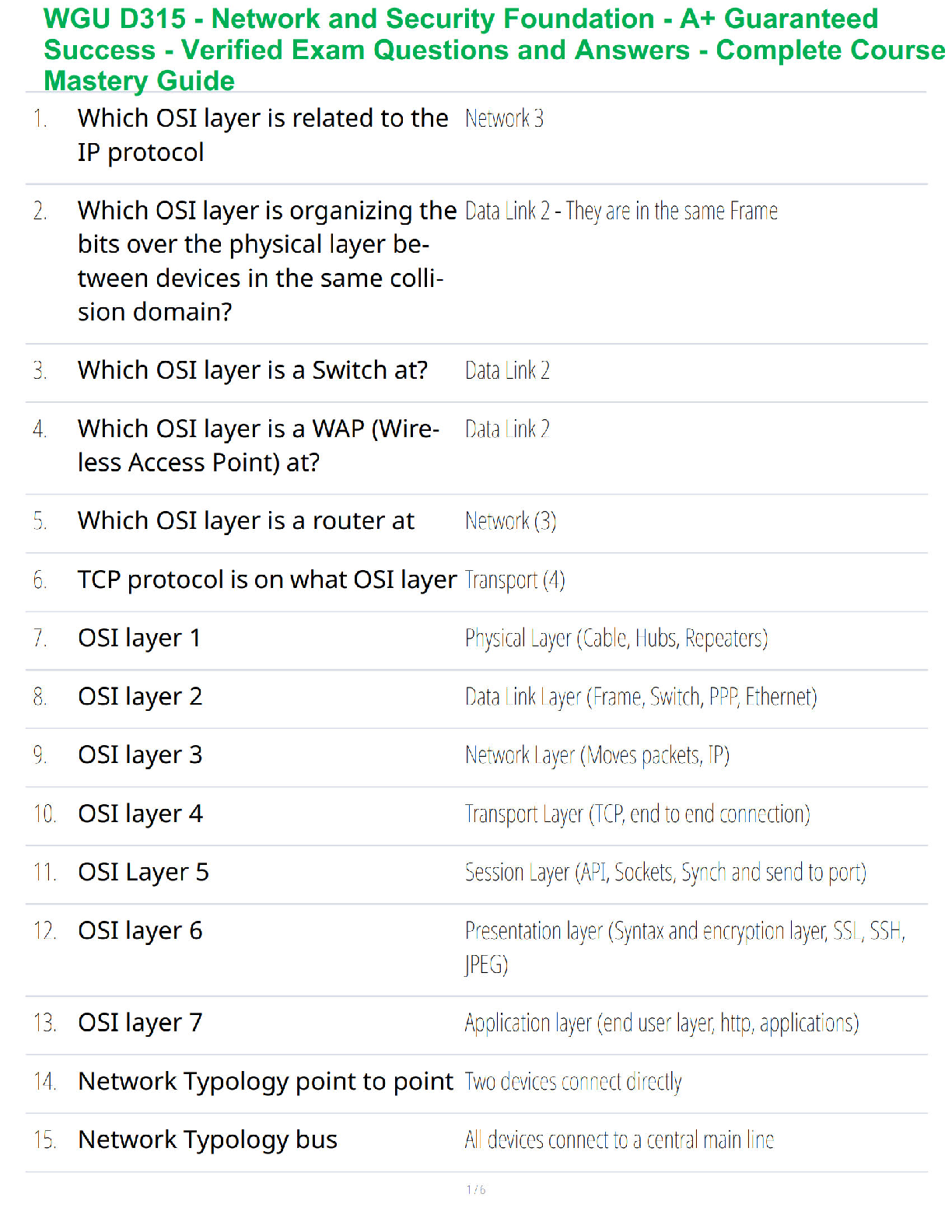
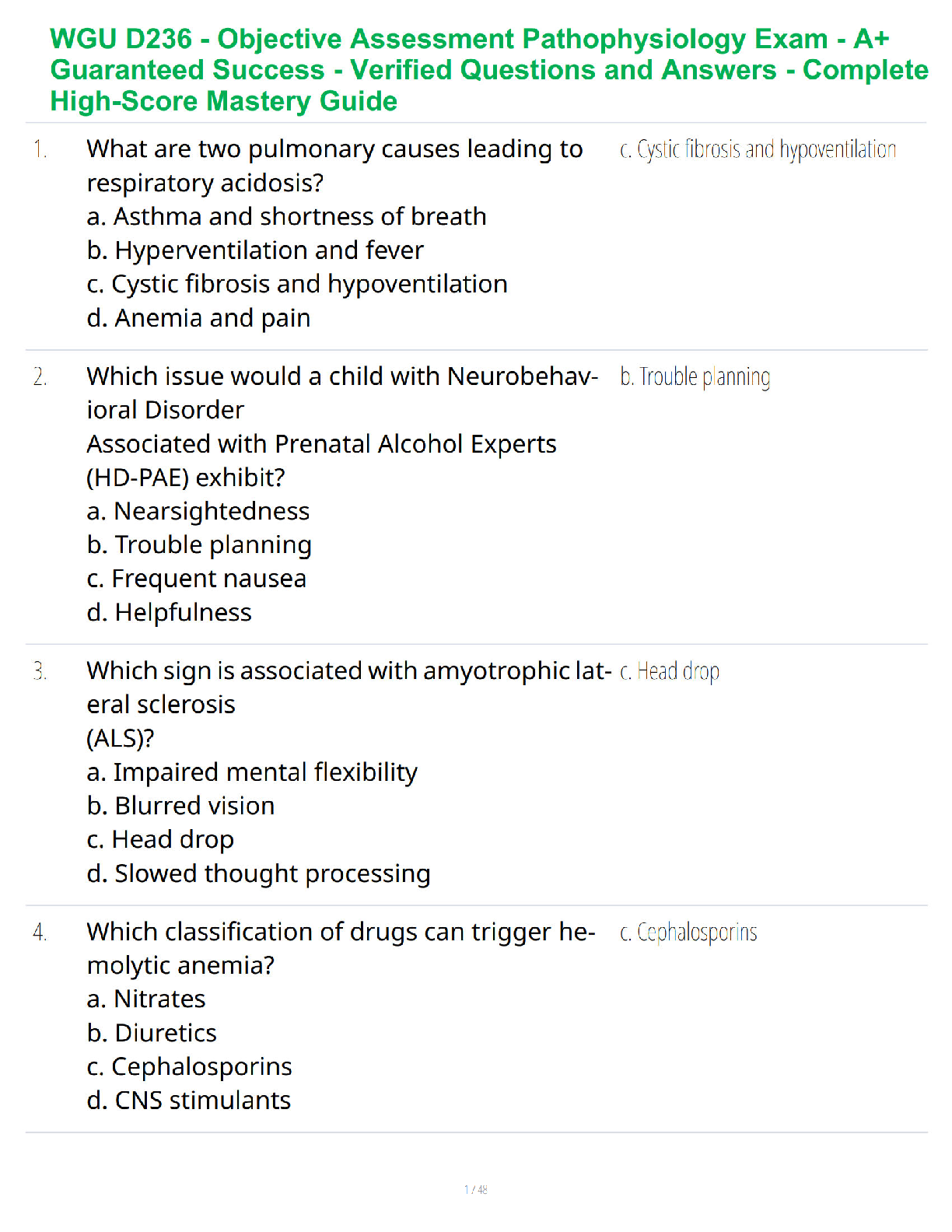
List the default tracking methods available for adding assets to your "scanning" subscription. (Select Three)
(A) DNS Name
(B) N
...
Qualys Vulnerability Management Self-Paced Training Exam 2023 with complete solution
List the default tracking methods available for adding assets to your "scanning" subscription. (Select Three)
(A) DNS Name
(B) NetBIOS Name
(C) CVE ID
(D)Qualys Host ID
(E) IP Address ✔Ans✔ (A) DNS Name
(B) NetBIOS Name
(E) IP Address
Name the phase or step of the Qualys Vulnerability Management Lifecycle that produces scan results containing vulnerability findings?
(A) Report
(B) Discover
(C) Remediate
(D) Assess ✔Ans✔ (D) Assess
Which of the following is the default tracking method used by Qualys Cloud Agents?
(A) IP Address
(B) Qualys Host ID
(C) DNS Name
(D) NetBIOS Name ✔Ans✔ (B) Qualys Host ID
Which of the following are phases of the Vulnerability Management Lifecycle?
(A) Maintenance
(B) Remediate
(C) Design
(D) Discover
(E) Report ✔Ans✔ (B) Remediate
(D) Discover
(E) Report
Name the type of scanner appliance (by default) available to all Qualys users with "scanning" privileges?
(A) External (Internet-based) Scanner
(B) Offline Scanner
(C) Virtual Scanner
(D) Internal Scanner ✔Ans✔ (A) External (Internet-based) Scanner
Only the _________ user role can edit QIDs in your account KnowledgeBase.
(A) Manager
(B) Administrator
(C) Scanner
(D) Unit Manager ✔Ans✔ (A) Manager
Potential vulnerabilities are automatically verified. (True/ False)
(A) True
(B) False ✔Ans✔ (B) False
A severity ____________ vulnerability is the most urgent.
(A) Level 5
(B) Level 1
(C) Level 2
(D) Level 4 ✔Ans✔ (A) Level 5
Which of the following criteria can be used to create a dynamic Search List? (Select Three).
(A) Host Name
(B) Severity Level
(C) IP Address
(D) CVE ID
(E) CVSS Score ✔Ans✔ (B) Severity Level
(D) CVE ID
(E) CVSS Score
What is the name given to a custom list of QIDs taken from the Qualys KnowledgeBase?
(A) Search List
(B) Host Assets
(C) Asset Group
(D) Authentication Record ✔Ans✔ (A) Search List
You have just created a Search List. Where can you use or apply it? (Select Three)
(A) Report Template
(B) Remediation Policy
(C) Asset Group
(D) Business Unit
(E) Asset Tag
(F) Option Profile ✔Ans✔ (A) Report Template
(B) Remediation Policy
(F) Option Profile
A static Search List is created and updated ____________.
(A) Manually
(B) Explicit
(C) By Default
(D) Automatically ✔Ans✔ (A) Manually
What are the primary methods available in Qualys VM, for grouping, labeling, and organizing host assets? (Select Two)
(A) Severity Levels
(B) Search Lists
(C) Asset Groups
(D) Asset Tags ✔Ans✔ (C) Asset Groups
(D) Asset Tags
Which of the following options can be used to add assets to an Asset Group? (Select Three)
(A) DNS name
(B) MAC address
(C) IP address
(D) NetBIOS name ✔Ans✔ (A) DNS name
(C) IP address
(D) NetBIOS name
Scans must be performed in "________________" mode to produce a list of installed software applications.
(A) Authorized
(B) Administrative
(C) Temporary
(D) Authenticated ✔Ans✔ (D) Authenticated
Why is it beneficial to configure the Business Impact of an Asset Group?
(A) It's used to calculate Business Risk
(B) It's used to calculate storage space
(C) It's used to calculate Severity Levels
(D) It's used to calculate CVSS Scores ✔Ans✔ (A) It's used to calculate Business Risk
A "static" Asset Tag will adjust dynamically and automatically to changes made to your host assets. (True/False)
(A) True
(B) False ✔Ans✔ (B) False
The service creates some initial asset tags based on the existing objects (configurations) in your account. List those asset tags. (Select Four)
(A) Asset Groups
(B) Business Units
(C) Malware Domaine Assets
(D) Web Application Assets
(E) Software Installed ✔Ans✔ (A) Asset Groups
(B) Business Units
(C) Malware Domaine Assets
(D) Web Application Assets
Which of the following is NOT a benefit or characteristic of Asset Tags?
(A) Dynamically updated
(B) Hierarchical organization (support nesting)
(C) Helps to automate scanning and reporting tasks
(D) Identifies the "Business Impact" of host assets ✔Ans✔ (D) Identifies the "Business Impact" of host assets
[Show More]







 Answered 2023.png)