Assignment 4 Sample Answer
1. (3 points) DHCP Attack 1
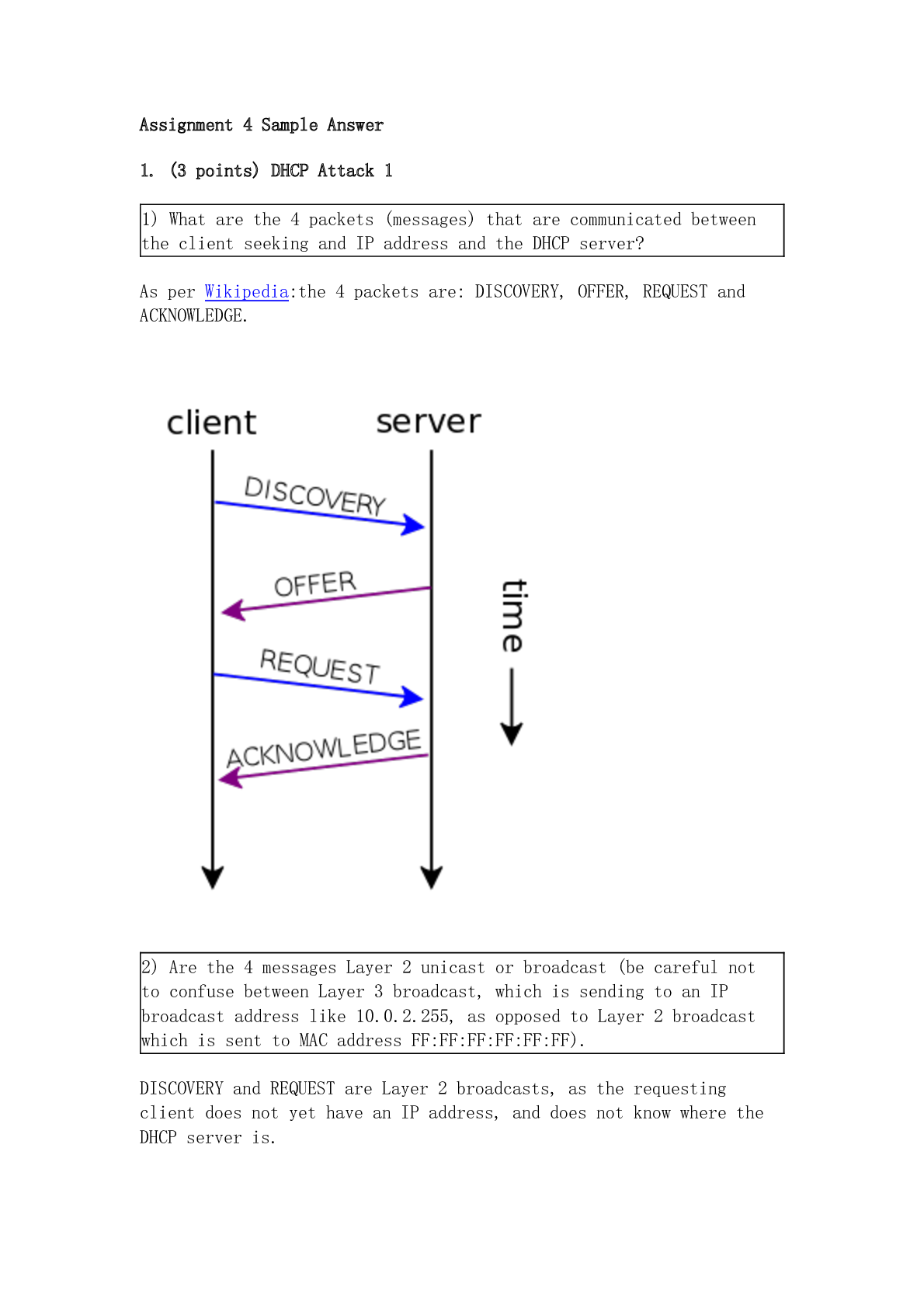
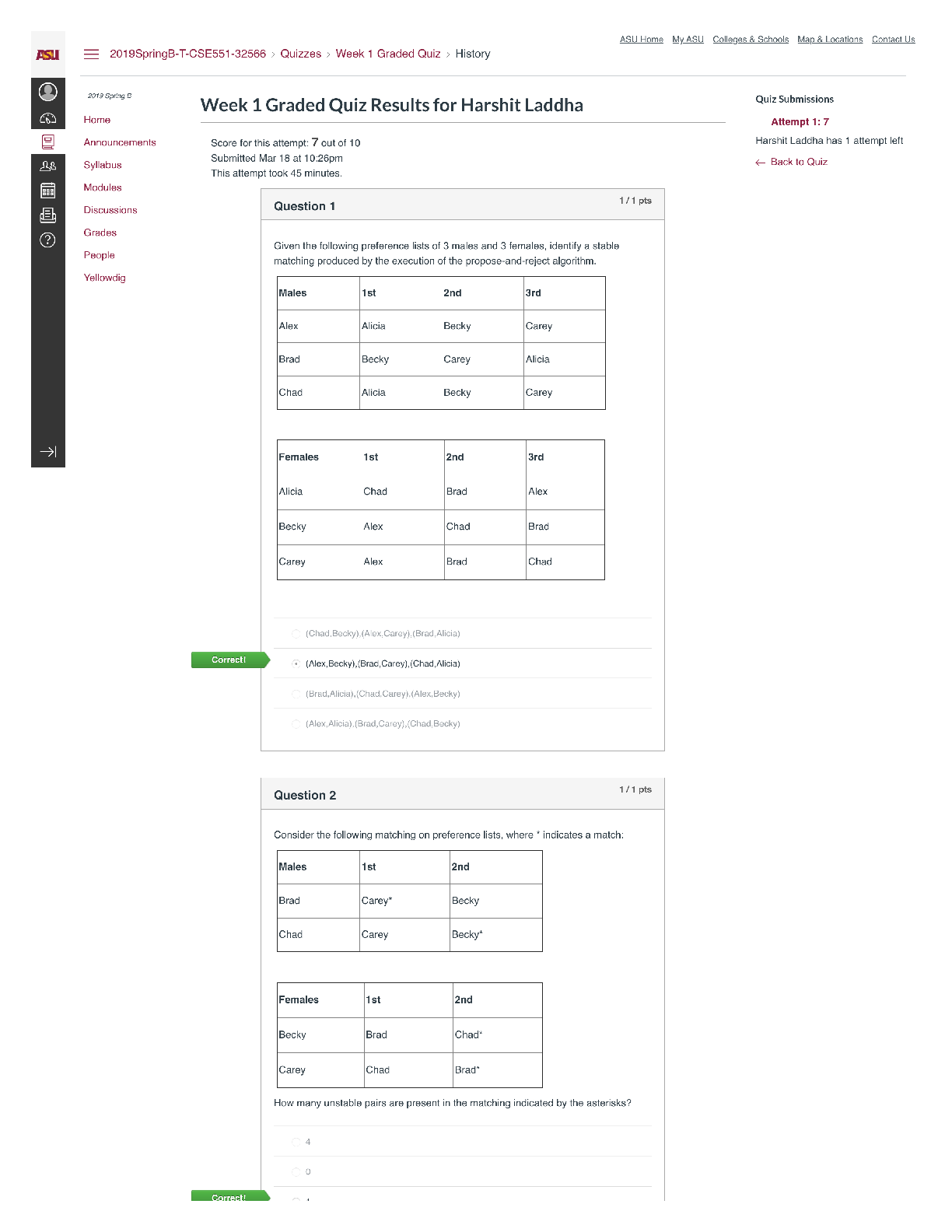
1) What are the 4 packets (messages) that are communicated between
the client seeking and IP address and the DHCP server?
As per Wikipedia:the 4 packets are: DIS
...
Assignment 4 Sample Answer
1. (3 points) DHCP Attack 1
1) What are the 4 packets (messages) that are communicated between
the client seeking and IP address and the DHCP server?
As per Wikipedia:the 4 packets are: DISCOVERY, OFFER, REQUEST and ACKNOWLEDGE.
2) Are the 4 messages Layer 2 unicast or broadcast (be careful not to confuse between Layer 3 broadcast, which is sending to an IP broadcast address like 10.0.2.255, as opposed to Layer 2 broadcast which is sent to MAC address FF:FF:FF:FF:FF:FF).
DISCOVERY and REQUEST are Layer 2 broadcasts, as the requesting client does not yet have an IP address, and does not know where the DHCP server is.
OFFER and ACKNOWLEDGE in theory are Layer 2 unicasts, as the DHCP server know the physical (MAC) address of the requesting computer.
3) Therefore, in a switched network, which of the 4 messages in the
DHCP negotiation would the attacker be able to observe?
Even on a Layer 3 switched network, the attacker is able to observe DISCOVERY and REQUEST, unless DHCP snooping is enabled on the switch.
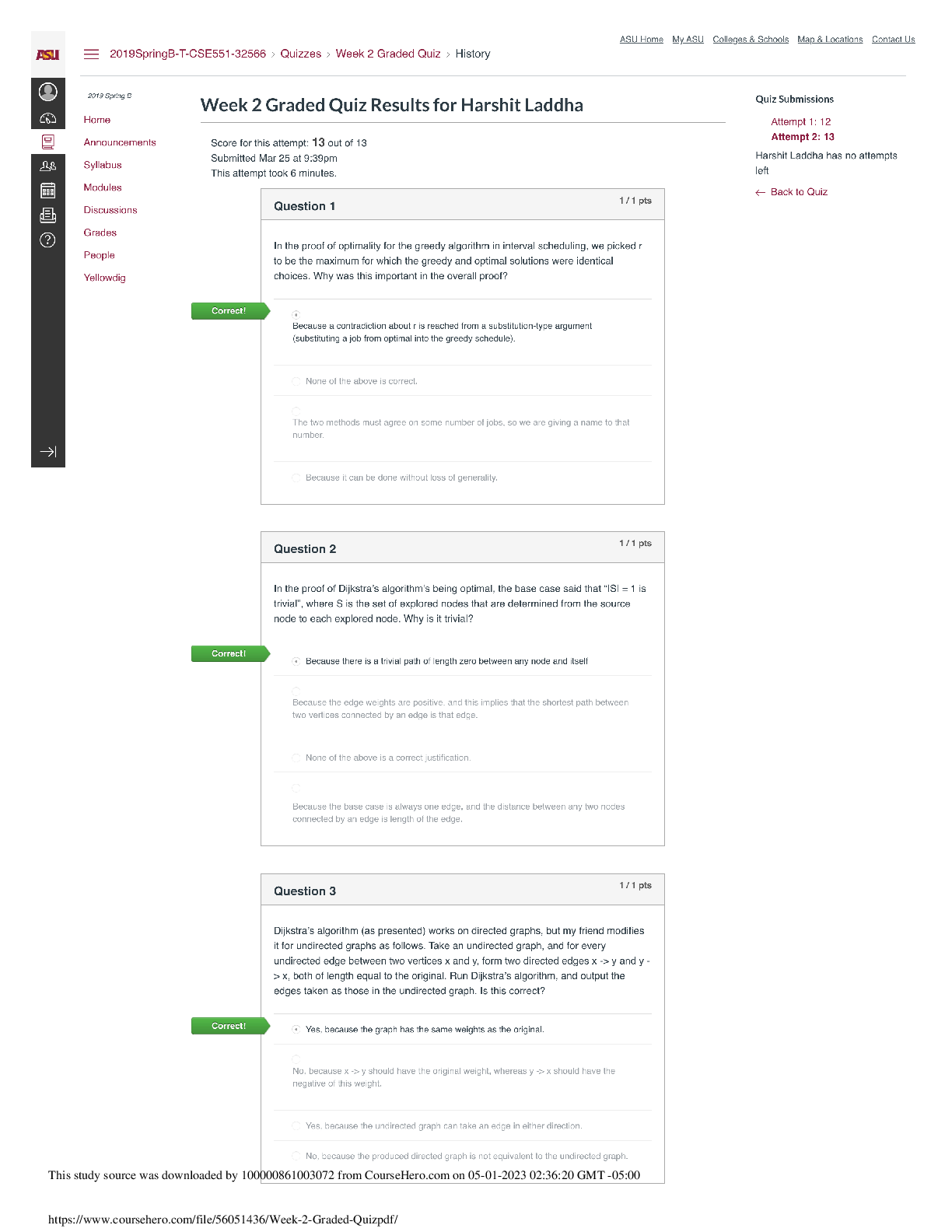
4) Briefly explain what DHCP spoofing and DHCP starvation attacks
are executed, and how the two can be used in combination.
DHCP spoofing is simply the attacker sending a forged (spoofed) DHCP ACKNOWLEDGE response with crafted options like DNS and default route that is useful for the attacker to perform man-in-the-middle attacks.
DHCP starvation attack is a kind of a DoS attack performed against the DHCP server. The attacker sends many forged DISCOVERY/REQUEST packets with forged MAC addresses, quickly exhausting the DHCP server of available IP pool.
It is often useful (for the attacker) to perform a DHCP starvation attack before DHCP spoofing, so that the real DHCP server will be unable to respond to requests.
5) For an adversary looking to perform MITM, which DHCP
configuration option(s) would you try to manipulate?
The 2 most useful options are DNS (to perform DNS spoofing) and default gateway IP address (to perform full MITM).
6) Briefly explain how "DHCP snooping" configuration in a switch
work to prevent DHCP spoofing?
DHCP Snooping is a configuration on a Layer 3 switch that specifies the MAC address of the trusted DHCP server and the physical switchport it's connected to, and drops any forged DHCP packets. In a network where DHCP snooping is enabled, the attacker's spoofed packets are simply dropped, as it is not connected to the trusted switchport.
2. (2 points) DHCP Attack 2
1. In your VirtualBox, change the Network setting to Promiscuous
Mode = Allow Any on both Kali and DSL.
2. Run Wireshark on Kali (on eth0) and restart DSL
3. Capture the 4x DHCP messages between DSL and DHCP server
(10.0.2.3) on Wireshark and take a screenshot.
4. Repeat while simulating a switched network (set Promiscuous
Mode = Deny) and capture the 2x DHCP messages. You should not
need to reboot Kali after changing the network settings, but
you do need to reboot DSL to refresh DHCP.
With Virtual Box's virtual DHCP server and, the same result is obtained. The attacker always see all 4 messages.
3. (3 points) DHCP Attack 3
1. Keep Wireshark running on Kali.
2. Use Ettercap's DHCP spoofing function to demonstrate how you
can supply the victim (DSL) with a rogue DNS server, to make
it easy for the attacker to spoof DNS replies. Try to perform
DHCP spoofing to inject DNS server of 1.2.3.4.
3. Reboot DSL and confirm that DNS has been poisoned by looking
at /etc/resolv.conf. Take a screenshot (do cat
/etc/resolv.conf).
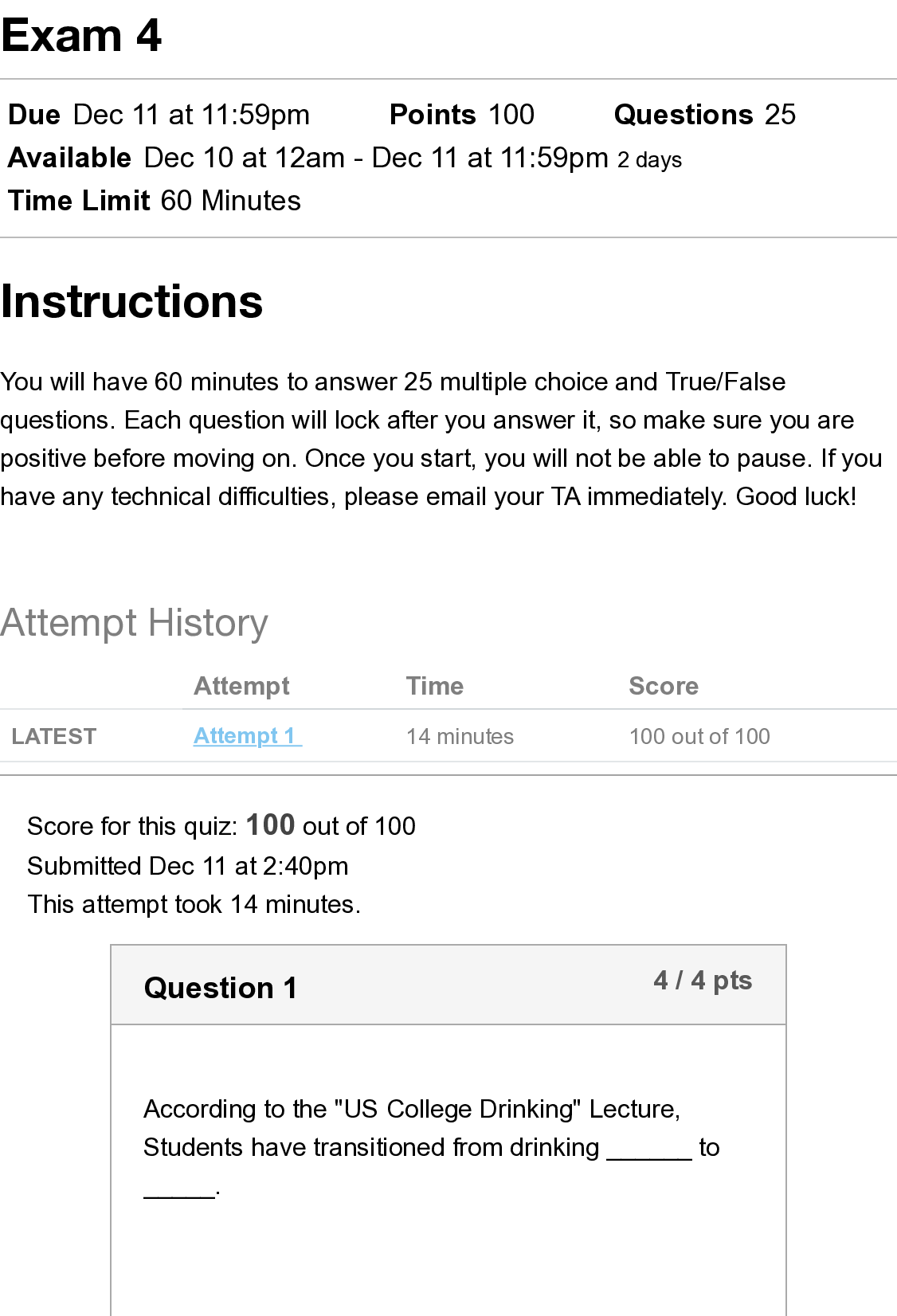
4. Go to Wireshark, and identify the REAL DHCP ACK (coming from
the 10.0.2.3 MAC address) and FAKE DHCP ACK (from the Kali
MAC address) being sent to DSL. Take a screenshot.
Ettercap:
Restarting DSL gives it fake DNS address in /etc/resolv.conf
Wireshark has recorded the real and fake ACK as follows. You can see that the fake one has beaten the legit one.
[Show More]