Systems Analysis and Design > QUESTIONS & ANSWERS > PCI-DSS ISA Exam Questions and Answers Graded A+ (All)
PCI-DSS ISA Exam Questions and Answers Graded A+
Document Content and Description Below
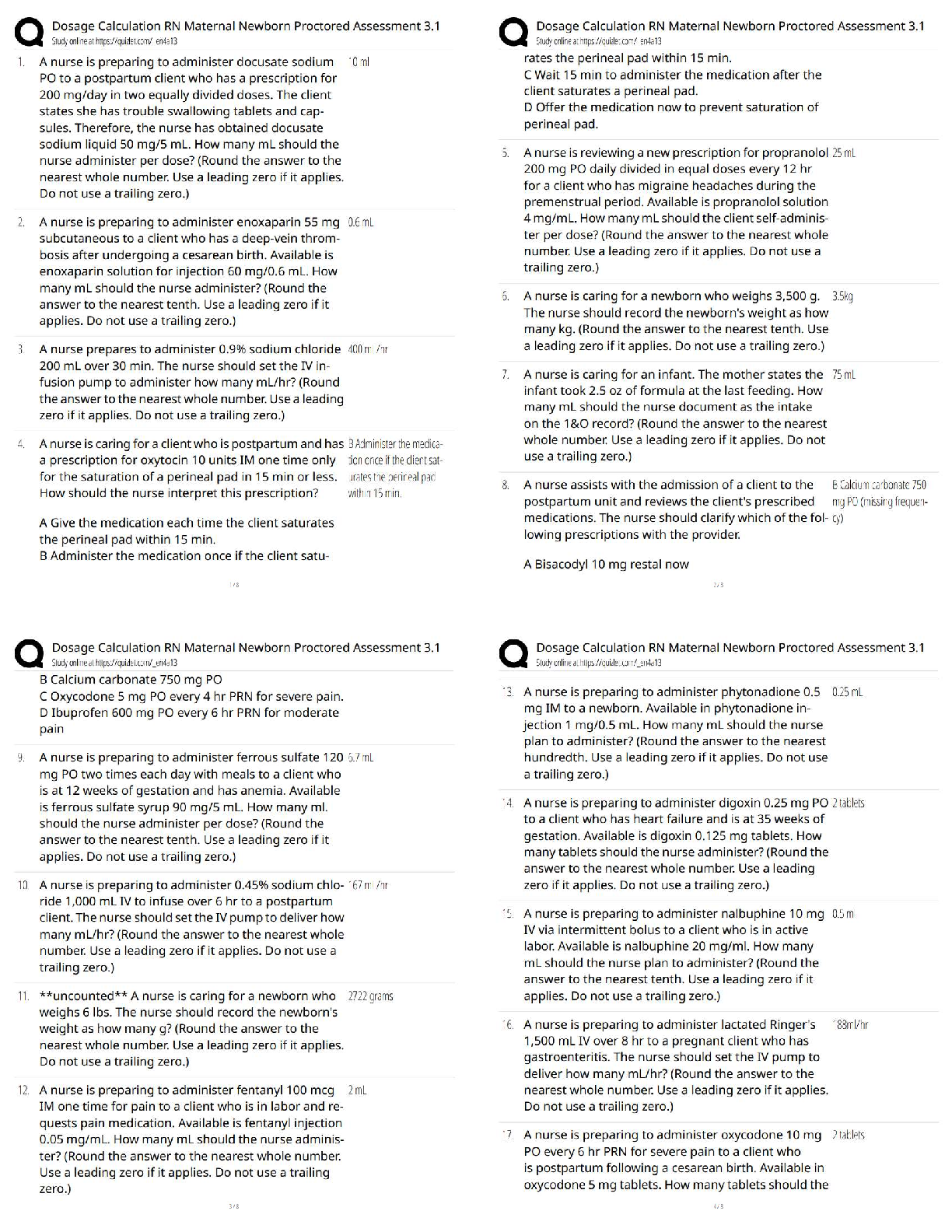
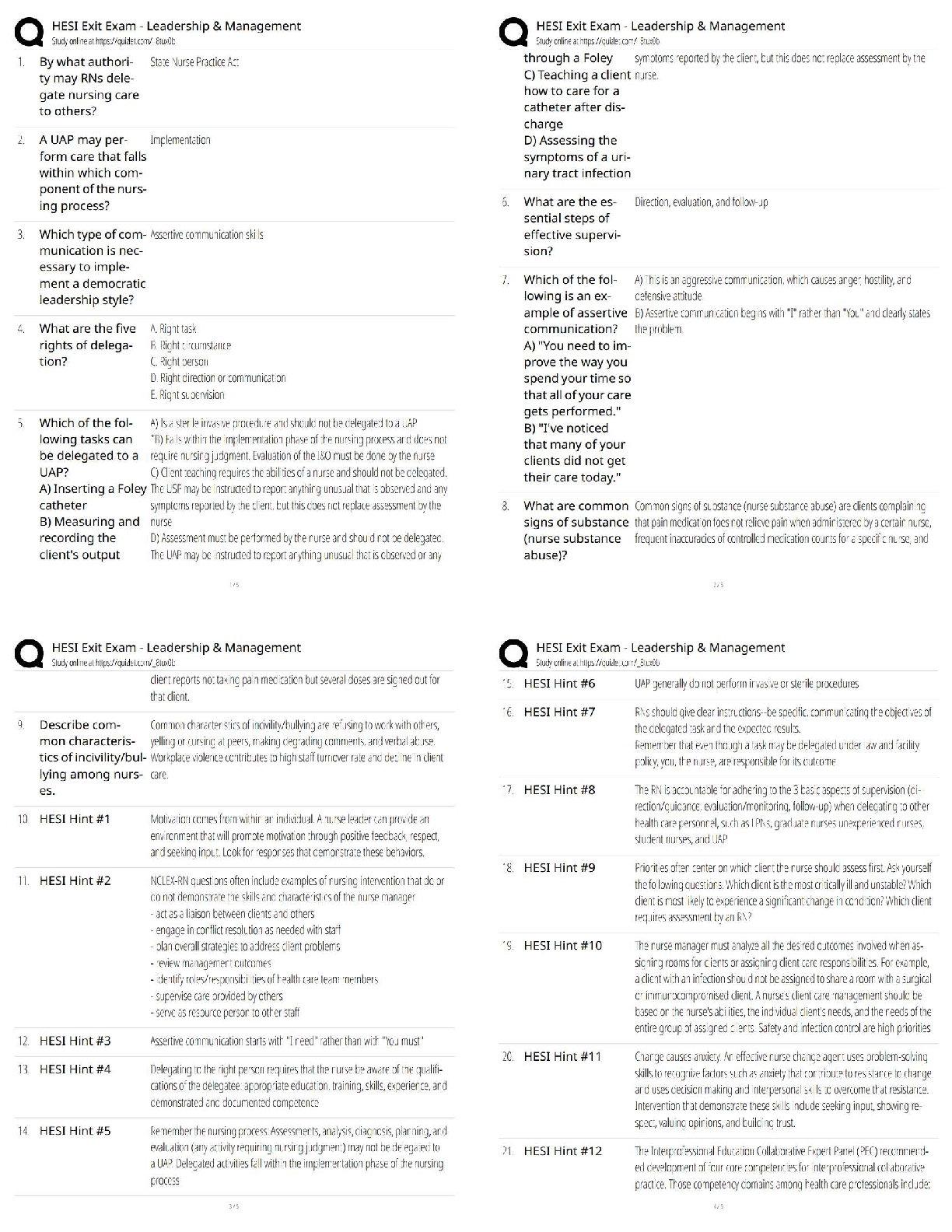
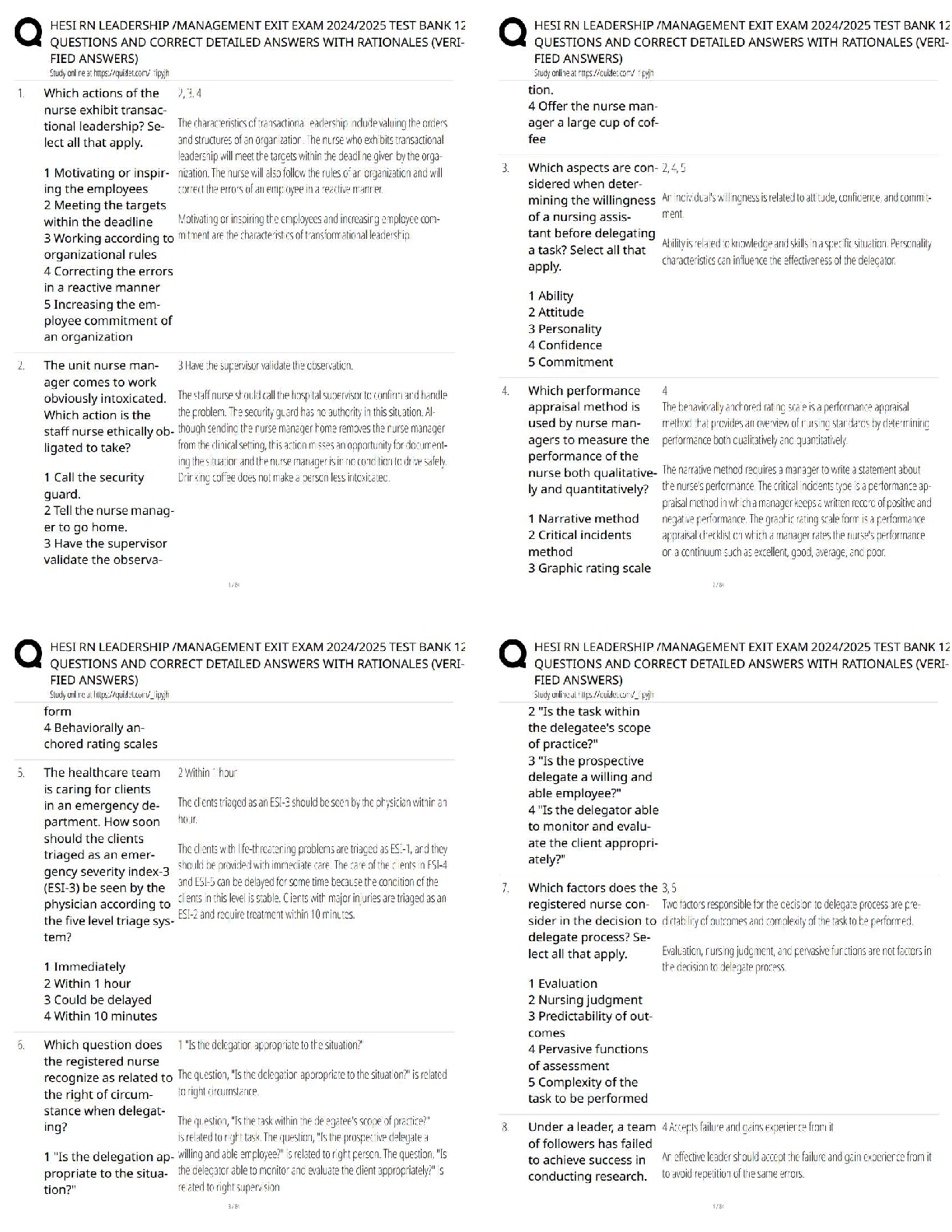
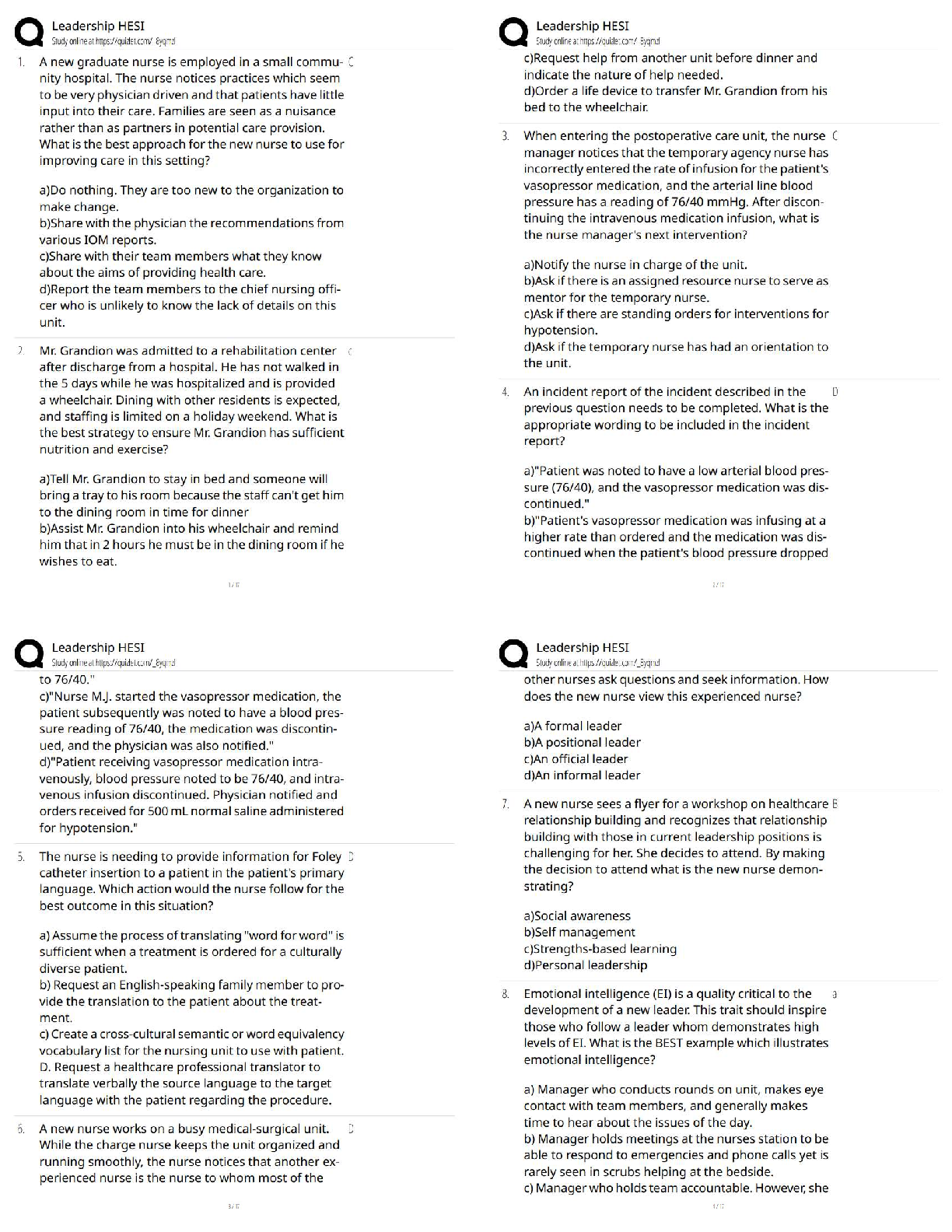
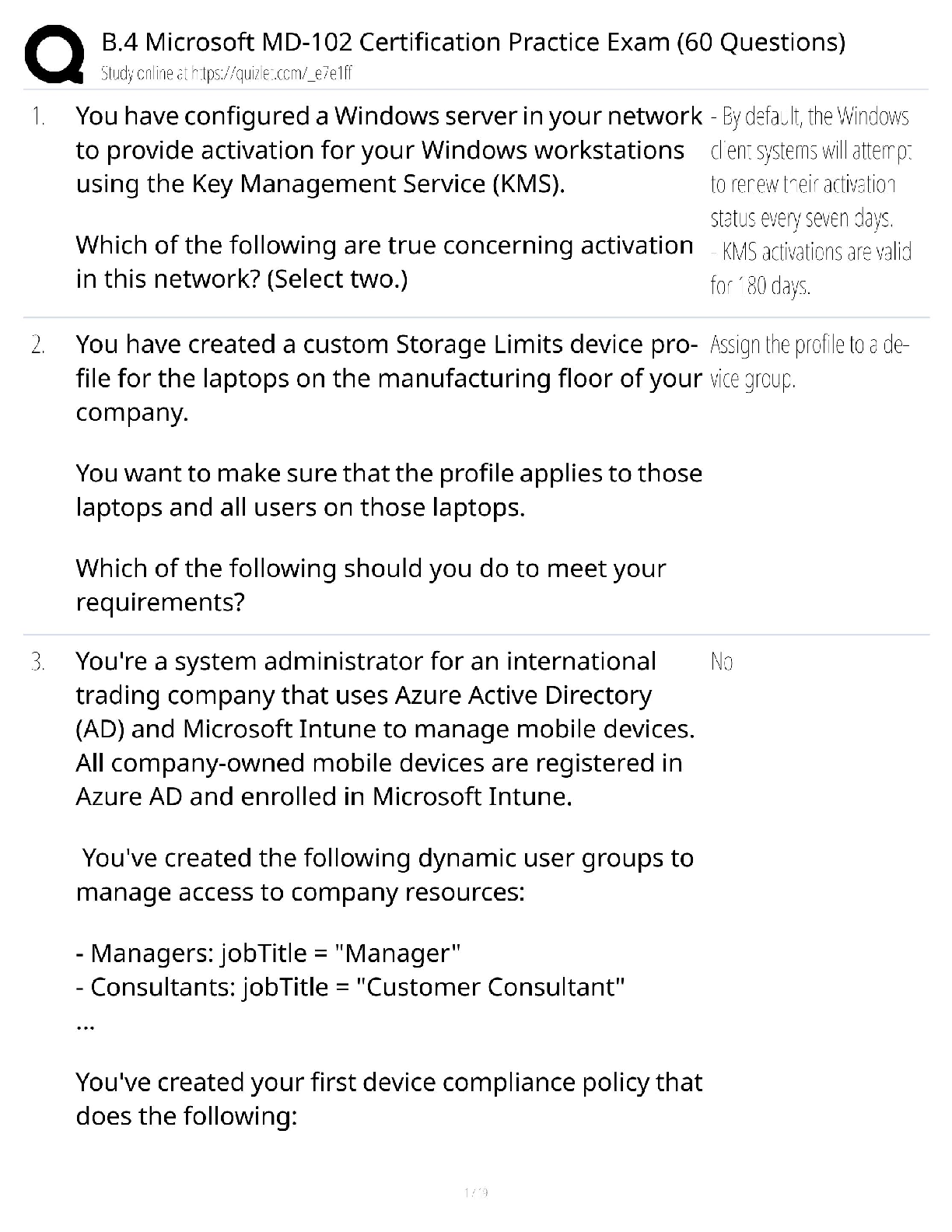
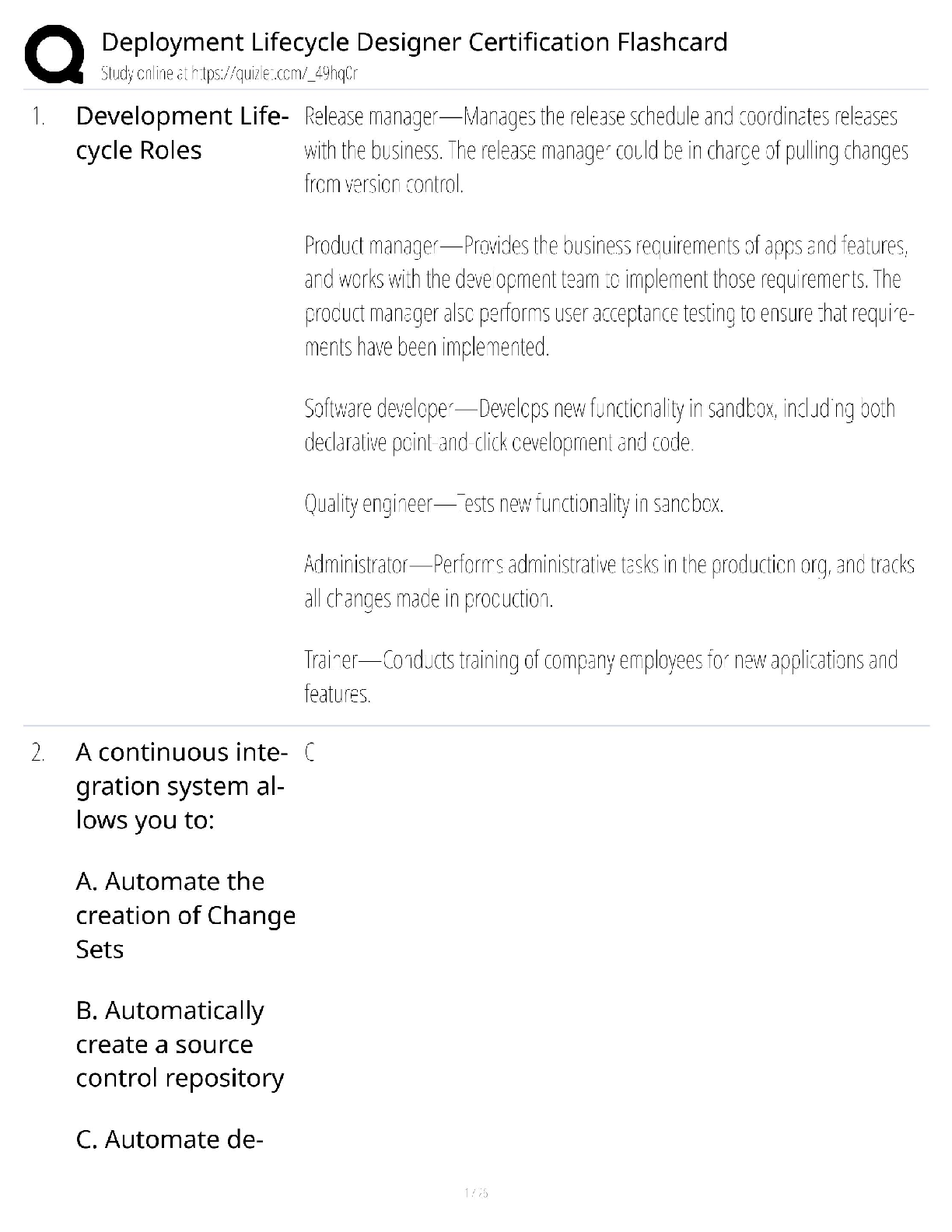
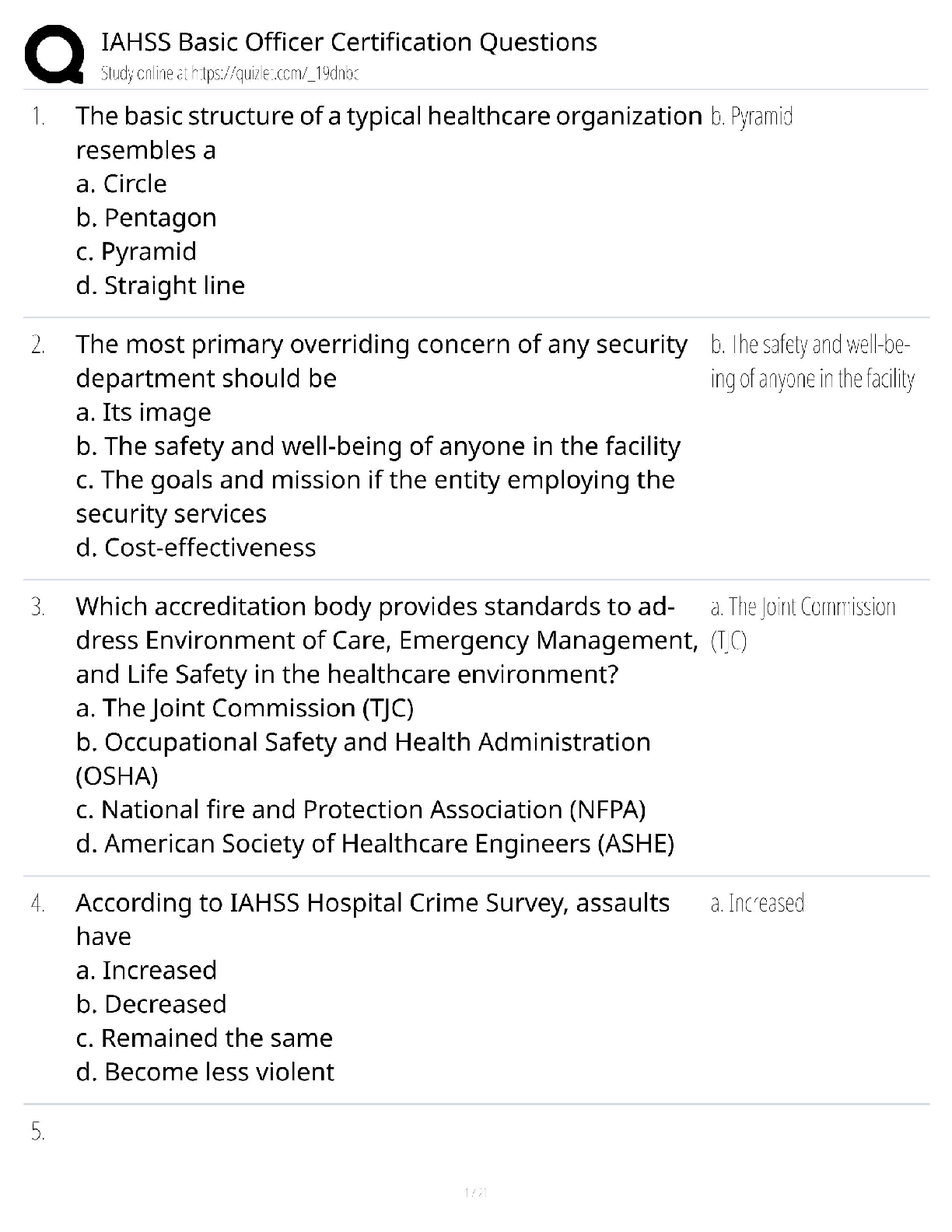
PCI-DSS ISA Exam Questions and Answers Graded A+ Perimeter firewalls installed ______________________________. ✔✔between all wireless networks and the CHD environment. Where should firewalls b ... e installed? ✔✔At each Internet connection and between any DMZ and the internal network. Review of firewall and router rule sets at least every __________________. ✔✔6 months If disk encryption is used ✔✔logical access must be managed separately and independently of native operating system authentication and access control mechanisms Manual clear-text key-management procedures specify processes for the use of the following: ✔✔Split knowledge AND Dual control of keys What is considered "Sensitive Authentication Data"? ✔✔Card verification value When a PAN is displayed to an employee who does NOT need to see the full PAN, the minimum digits to be masked are: All digits between the ___________ and the __________. ✔✔first 6; last 4 Regarding protection of PAN... ✔✔PAN must be rendered unreadable during the transmission over public and wireless networks. Under requirement 3.4, what method must be used to render the PAN unreadable? ✔✔Hashing the entire PAN using strong cryptography Weak security controls that should NOT be used ✔✔WEP, SSL, and TLS 1.0 or earlier Per requirement 5, anti-virus technology must be deployed_________________ ✔✔on all system components commonly affected by malicious software. Key functions for anti-vius program per Requirement 5: ✔✔1) Detect 2) Remove 3) Protect Anti-virus solutions may be temporarily disabled only if ✔✔there is legitimate technical need, as authorized by management on a case-by-case basis When to install "critical" applicable vendor-supplied security patches? ---> within _________ of release. ✔✔1 month When to install applicable vendor-supplied security patches? ✔✔within an appropriate time frame (for example, within three months). When assessing requirement 6.5, testing to verify secure coding techniques are in place to address common coding vulnerabilities includes: ✔✔Reviewing software development policies and procedures Requirements 7 restricted access controls by: ✔✔Need-to-know and least privilege Inactive accounts over _____________days need to be removed or disabled. ✔✔90 days To verify user access termination policy, an ISA need to select a sample of user terminated in the past _______________ months, and review current user access lists—for both local and remote access—to verify that their IDs have been deactivated or removed from the access lists. ✔✔6 months How many logon attempts should be allowed until resulting temporarily account locked-out? ✔✔6 attempts Once user account is locked-out, it will remain locked for a minimum of ________________________ or until a system administrator resets the account. ✔✔30 minutes System/session idle time out must be set to_________ minutes or less. ✔✔15 minutes What are the methods to authenticate users? ✔✔- "Something you know", such as a password or passphrase - "Something you have", such as a token device or smart card, or - "Something you are", such as a biometric. Where passwords or pass-phrases are used, they must be at least _______ characters long and contain both numeric and alphabetic characters. ✔✔7 Passwords must be changed at least once every__________________. ✔✔90 days Password history must also be in place to ensure that users' ________ previous passwords can't be re-used. ✔✔4 An example of a "one-way" cryptographic function used to render data unreadable is: ✔✔SHA-2 Data from video cameras and/or access control mechanisms is reviewed, and that data is stored for at least ________________. ✔✔3 months The visitor logs must contain the relevant information and be retained for at least_________________. ✔✔3 months Verify that the storage location security is reviewed at least ____________________ to confirm that backup media storage is secure. ✔✔annually Review media inventory logs to verify that logs are maintained and media inventories are performed at least______________. ✔✔annually Using time-synchronization technology, synchronize all critical system clocks and times and ensure that the following is implemented for: ✔✔acquiring, distributing, and storing time All security events and logs of (a) all system components that store, process, or transmit CHD; (b) critical system components; (c) components that perform security functions (for example, firewalls, intrusion-detection systems/intrusion-prevention systems (IDS/IPS), authentication servers, e-commerce redirection servers, etc.) to be reviewed at least ______________. ✔✔daily Audit logs must be immediately available for analysis for a period of ________ and must be retained for a period of _________. ✔✔3 months; 1 year Detection and identification of authorized and unauthorized wireless access points must occur _________________. ✔✔quarterly Run internal and external network vulnerability scans at least ____________________ and after any significant change in the network ✔✔quarterly "External" vulnerability scans must be run by ____________ and perform ________________. ✔✔an ASV; quarterly For external scans, no vulnerabilities exist that are scored _____________ by the CVSS. ✔✔4.0 or higher Penetration testing for "Service Provider" in which targeting segmentation controls must be perform every __________________. ✔✔6 months FIM tools must be configured to perform critical file comparisons check at least_______________, ✔✔weekly A retail location that does not use wireless devices in store must test for the presence of unauthorized wireless devices every ________________. ✔✔quarter Verify that personnel attend security awareness training upon hire and at least ___________________. ✔✔annually Appendix A1 applies to ✔✔hosting providers Appendix A2 applies to ✔✔entities using SSL/Early TLS Appendix A3 applies to ✔✔Designated Entities Supplemental Validation (DESV) An entity is required to undergo an assessment according to this Appendix ONLY if instructed to do so by an acquirer or a payment brand. Designated entities (DESV) must document and confirm the accuracy of PCI DSS scope at least_________ and upon significant changes to the in-scope environment. ✔✔quarterly Designated Entities (DESV) must ensure that pen tests are performed on "segmentation controls" every _________________, and after significant changes. ✔✔6 months In regards to DESV, user accounts and access privileges are reviewed at least every______________. ✔✔6 months ASV scans must cover__________________________________. ✔✔ALL Internet-Facing IP addresses in existence at the entity. Compensating controls need to be evaluated at least_________________. ✔✔annually Compensating controls requirement 1: ✔✔Constrains Compensating controls requirement 2: ✔✔Objective Compensating controls requirement 3: ✔✔Risk Compensating controls requirement 4: ✔✔Definition Compensating controls requirement 5: ✔✔Validation Compensating controls requirement 6: ✔✔Maintenance QSAs are required to retain work papers for a minimum of ____________, and it is also recommended that ISAs retain work papers for a minimum of ___________. ✔✔3 years; 3 years The decision about a merchant's level is made by the: ✔✔merchant's acquirer Service provider levels are defined by ___________________________. ✔✔the payment brands according to transaction volume and/or type of service provider. Issuer ✔✔Bank or other organization issuing a payment card on behalf of a Payment Brand. Merchant ✔✔Organization accepting the payment card for payment during a purchase Acquirer ✔✔Bank or entity the merchant uses to process their payment card transactions Acquirer is also called: Merchant Bank ISO (sometimes) Payment Brand - Amex, Discover, JCB Never Visa or MasterCard only one primary function ✔✔Verify system configurations that ________________________________ is implemented per server. Do not store _____ AFTER authorization even if ___________. ✔✔sensitive authentication data; encrypted (sensitive auth data: track data, verification code, PIN) Req 3.3: Protection of PAN that displayed on screens, paper receipts, etc. by _____________________ ✔✔masking the PAN and only show first 6 digits and last 4 digits. Req 3.4: Protection of PAN when stored in files, databases, etc. by ______________. (hint: do what to the information?) ✔✔render the information unreadable. Disk Encryption ✔✔Must verify that logical access to encrypted file systems is implemented via a mechanism that is separate from the native operating system's authentication mechanism. Key-encrypting keys are ___________________ as data-encrypting keys and ___________________. ✔✔at least as strong; stored separately. Key Management documentation must specifies the following: ✔✔Procedures to: 1. Generate strong keys 2. Securely distribute keys 3. Securely store keys 4. Defined cryptoperiod PAN must be ✔✔render unreadable during transmission over PUBLIC wireless network. Split knowledge ✔✔Two or more entities need to separately have key components that individually convey no knowledge of the resultant cryptographic key Dual control ✔✔Required the present of two individuals to perform a task Critical vendor supplied patches should be installed within_______________. ✔✔1 month What is the proper handling of displaying an error message? ✔✔by returning generic rather than specific error details (to not leak too much information about the system) For public web facing application, do we use both or either one of these methods? 1) Use either manual or automated vulnerability security assessment tools or methods at least annually and after any changes. 2) Use of automated technical solution that detects and prevents web-based attacks (WAP) ✔✔Either One Req 7.1 - Limited access to what user roles based on _______________. ✔✔Least privileges and need-to-know basis based on job functions. Req 7.2 - Access control system must be set to _____________ by default. ✔✔deny-all Multi-factor authentication is required for: ______________________ and _________. ✔✔All remote access by personnel (user and administrator) and all third-party/vendor remote access An example of a "one-way" cryptographic function used to render data unreadable is: ✔✔SHA-2 Req 10.4: Time-synchronization technology - What type of server is required to receives time signals from external sources, and time signals from external sources are based on International Atomic Time or UTC. ✔✔Central time server(s) - Where there is more than one designated time server, the time servers peer with one another to keep accurate time - Systems receive time information only from designated central time server(s). IDS and IPS must be in place to monitor all traffic at ______________ and ____________. ✔✔the perimeter and at critical points Reviewing and confirming that personnel are following security policies and operational procedures, and that reviews cover: - Daily log reviews - Firewall rule-set reviews - Applying configuration standards to new systems - Responding to security alerts - Change management processes This must be review at least ______________. ✔✔Quarterly [Show More]
Last updated: 2 years ago
Preview 1 out of 14 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Also available in bundle (1)
Click Below to Access Bundle(s)

PCI ISA BUNDLED EXAMS QUESTIONS AND ANSWERS WITH VERIFIED SOLUTIONS
PCI ISA BUNDLED EXAMS QUESTIONS AND ANSWERS WITH VERIFIED SOLUTIONS
By Nutmegs 2 years ago
$17
7
Reviews( 0 )
$10.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Apr 03, 2023
Number of pages
14
Written in
All
Additional information
This document has been written for:
Uploaded
Apr 03, 2023
Downloads
0
Views
121





.png)