Computer Architecture > EXAM > IT Fundamentals Practice Exam ALL ANSWERS 100% CORRECT SPRING FALL-2023/24 EDITION GUARANTEED GRADE (All)
IT Fundamentals Practice Exam ALL ANSWERS 100% CORRECT SPRING FALL-2023/24 EDITION GUARANTEED GRADE A+
Document Content and Description Below
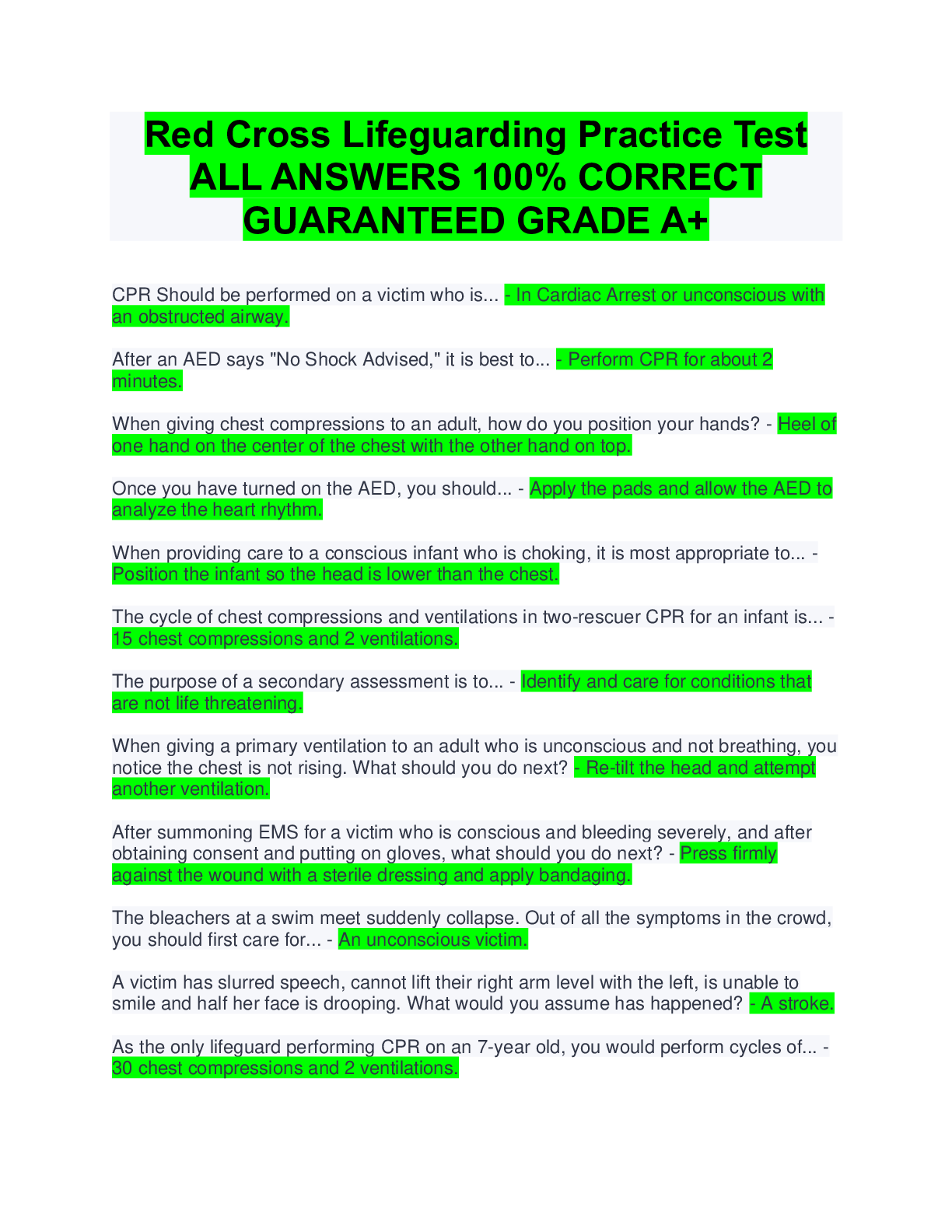
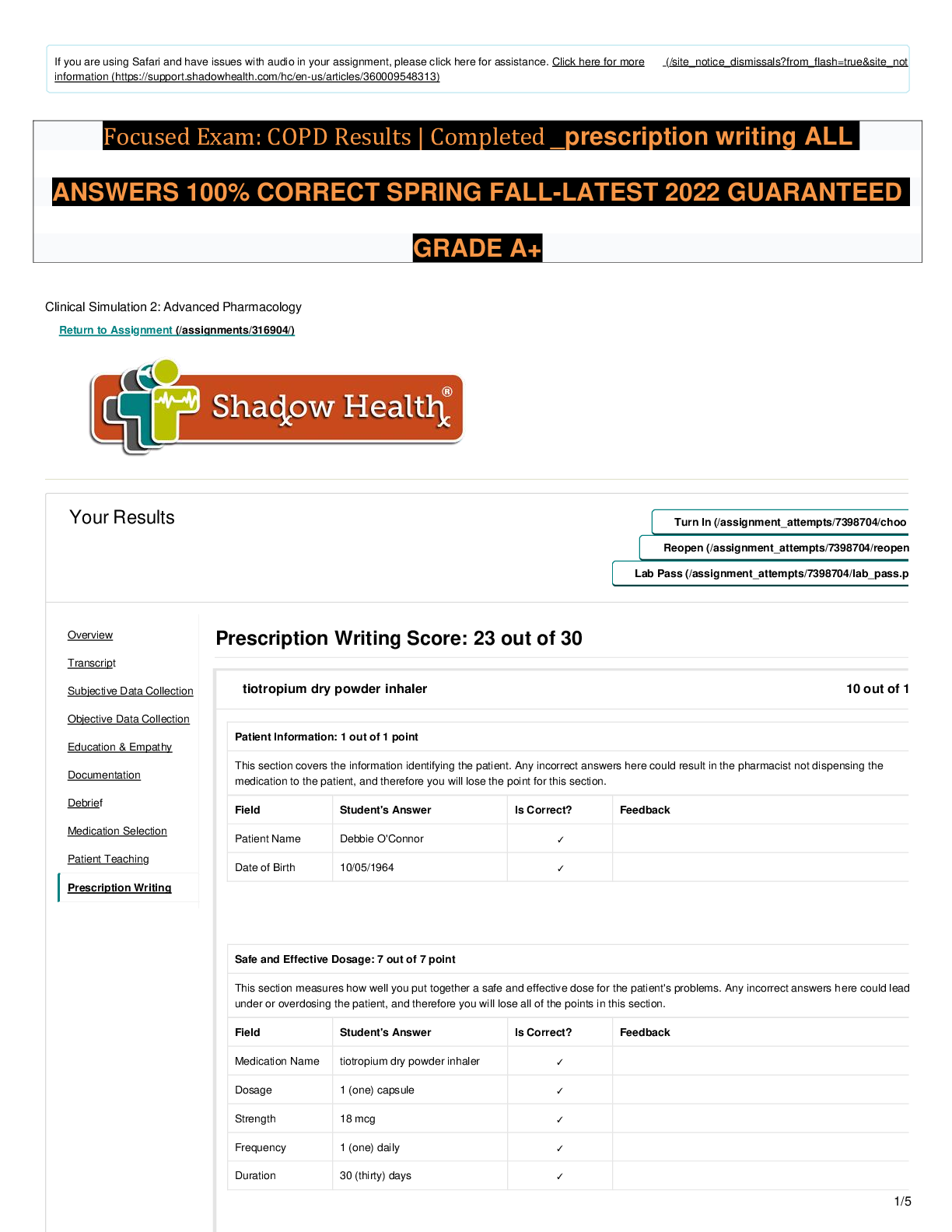
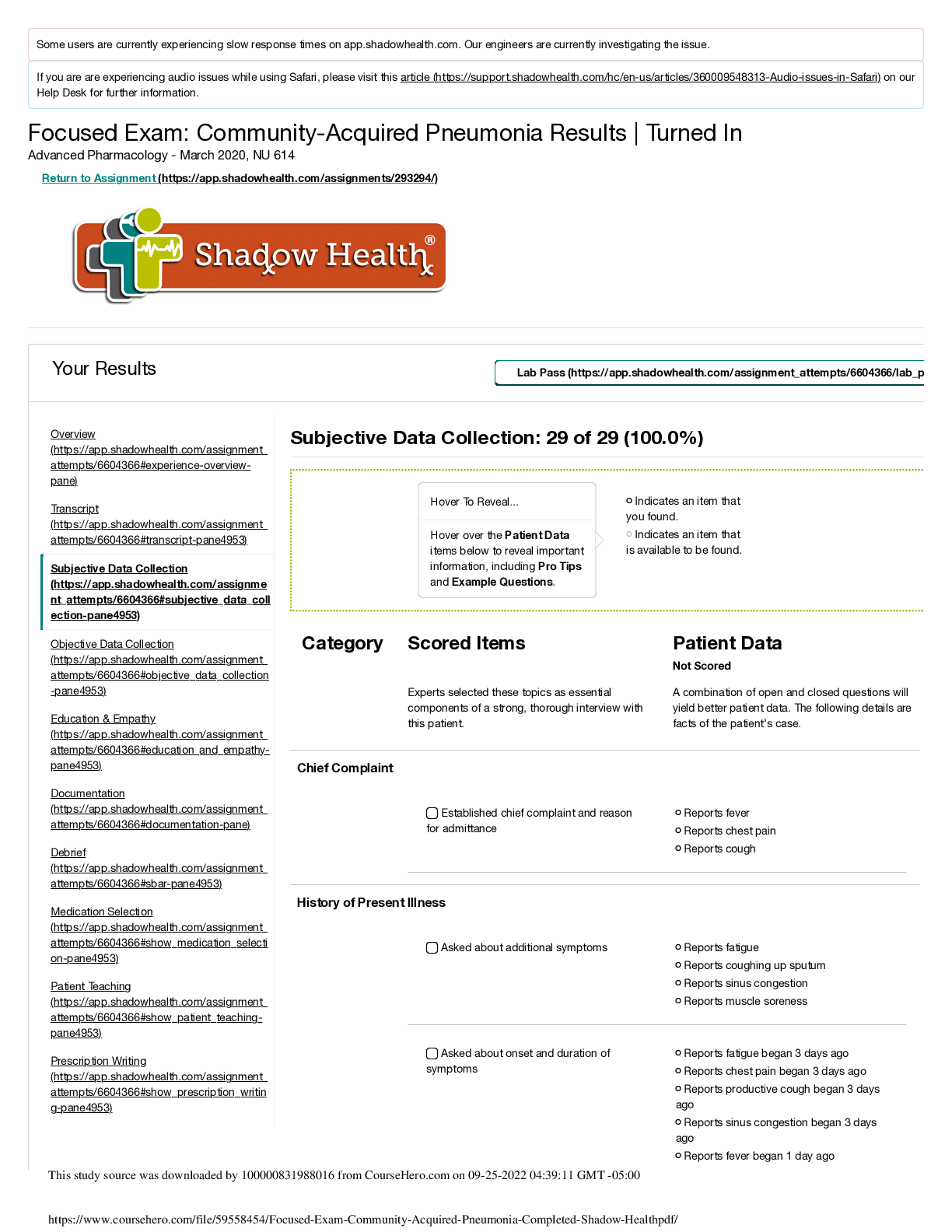
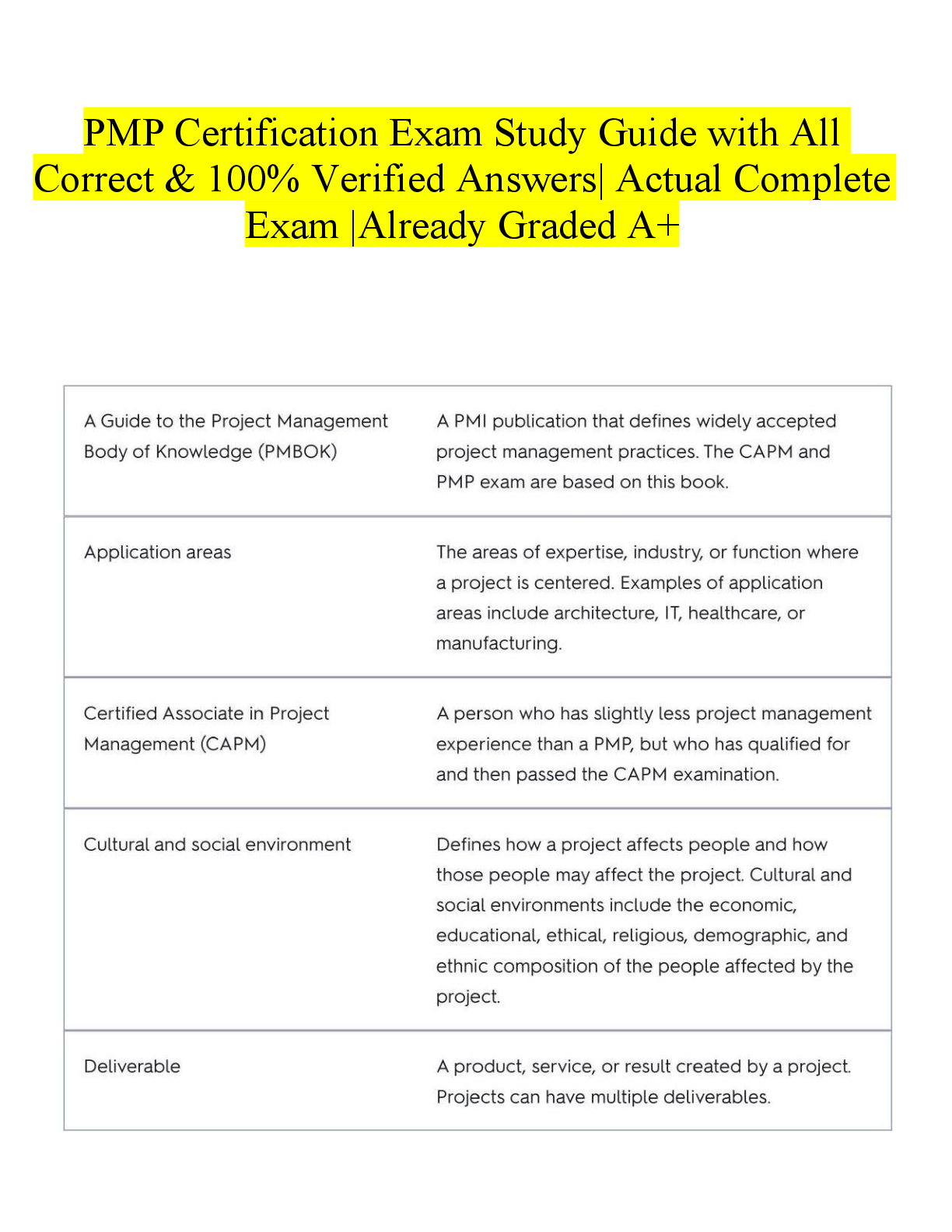
Which of the following is a file on a computer that links to another program or file somewhere else on the same computer? A. Shortcut B. URL C. Attachment D. FTP A Which of the following operat ... ing systems is MOST likely to be found on a desktop where its primary functions include professional video and audio editing? A. Chrome OS B. Windows 7 Home C. Mac OS X D. iOS C A technician is trying to access a users files and is unable to open any folder or file. Which of the following BEST describes the situation? A. The folders contain older versions of the files. B. The files are corrupted. C. The technician needs to change the file attributes. D. The technician does not have permissions. D A user has a username and password to log onto a banking website. The user would like to keep access to the account as secure as possible. Which of the following security best practices should the user follow? (Select TWO). A. Use only public computers to access the website B. Create a complex password C. Change the default password D. Write the password down E. Use the original password B C Which of the following components provides the FASTEST medium for hosting and storing an operating system? A. Blu-Ray disc B. 7200RPM HDD C. SSD D. DVD-RW C An RoHS label on hardware indicates which of the following? A. The hardware produces EMI when used. B. The hardware is certified to be energy efficient. C. The hardware provides battery backup for power outages. D. The hardware needs to be properly disposed. D Which of the following settings will a user configure as part of the initial operating system setup wizard? (Select TWO). A. Backup schedule B. Accessibility options C. Multiple user accounts D. Time zone E. Computer name D E After initial OS and application installation on a laptop, an application warns that it will only work 24 more times. Which of the following should be done NEXT? A. The application has to be registered to the user. B. The application must be upgraded to a 64-bit version. C. The application must be activated. D. The application needs to be reinstalled. C Which of the following should be performed after a backup has been completed? A. Delete the backup B. Verify the backup C. Save the backup D. Schedule the backup B Which of the following connections provide data with the MOST secure protection from interception? A. Wired B. WiFi C. IR D. Cellular A A technician is configuring a wireless router for a small office and the business owner would like the wireless network to be secured using the strongest encryption possible. Which of the following should the technician choose? A. WPA2 B. WAP C. WPA D. WEP A Which of the following is the MOST sensitive Personally Identifiable Information (PII) and should be shared cautiously and only with trusted resources? A. Email address B. Phone number C. Mother's maiden name D. Last name C Which of the following operating systems is available for free and can be modified by anyone? A. Windows B. Linux C. Mac OS D. Chrome OS B A user is browsing the Internet when suddenly a threatening message appears on screen demanding a payment in order to avoid the system being disabled. Which of the following BEST describes this type of malware infection? A. Ransomware B. Adware C. Spyware D. Virus A Which of the following features of a smartphone controls the screen orientation? A. Gyroscope B. NFC C. Accelerometer D. GPS A Which of the following printer types uses a powder based consumable with a lower cost per page compared to other printers? A. Thermal B. Laser C. Dot matrix D. Inkjet B Which of the following components are used to store data? (Select TWO). A. Motherboard B. RAM C. CPU D. GPU E. SSD B E A user has downloaded an application file with the .dmg file extension. Which of the following operating systems can be used with this file by default? A. iOS B. Windows C. Mac OS D. Chrome OS C Which of the following operating systems is very lightweight and relies heavily on Internet applications? A. Chrome OS B. Windows C. Linux D. Blackberry OS A Ann, a user, is doing her daily job on her company laptop at a coffee shop. She opens an Internet browser and tries to go to her home page. Instead, she is sent to an unfamiliar website. She clears all temporary files and deletes the history, but this continues to occur. Which of the following is the cause of the problem? A. The company has configured a policy on her computer that forces her to stay on their website. B. Her computer is infected with adware and is redirecting her browser to another site. C. The memory of the browser is corrupt, and she needs to have the browser reinstalled. D. She did not reboot her computer after clearing the temporary files. B Ann, a user, wishes to free space in her documents folder. Which of the following is the BEST characteristic to sort by in order to ensure that the most space is freed by deleting the least amount of files? A. Date modified B. File path C. Size D. Extension C A user has finished setting up a new computer. Now the operating system requires activation, but the user discovers the computer has no Internet connection. Which of the following should the user do FIRST? A. Contact technical support. B. Reboot the computer. C. Check the Ethernet cable. D. Review manufacturer's website. C Which of the following will allow a user to move a file from one folder to another using the LEAST number of steps, while ensuring that the file is removed from its original location? A. Open the file from its original location, save it to the new location, and delete it from the original location. B. Cut the file from its original location and paste it to the new location. C. Rename the file in its original location to a name that is not already taken in the new location. D. Copy the file from its original location and paste it to the new location. B Which of the following software package types is designed to accept input from multiple users? A. Utility B. Operating system C. Specialized D. Collaborative D Ann, a user, reports that her computer was working this morning, but now the screen is blank. The power indicator for the monitor is on. Pressing the space bar or mouse does not fix the problem. Which of the following is the cause? A. The monitor power cable is unplugged. B. The video cable has become disconnected. C. The video driver is not installed. D. The operating system has encountered a stop error. E. The screen saver has activated. B Which of the following are examples of keyboard connectors? (Select TWO). A. USB B. RJ-11 C. Serial D. FireWire E. PS/2 A E A user had to replace the hard drive in a computer. The user would like to install the games that came with the computer but were not installed as part of the initial OS setup wizard. The user can install the games by performing which of the following? A. Schedule automatic updates. B. Enable installed OS features. C. Update hardware drivers. D. Reinstall productivity applications. B A user is at the office and has a cellular phone that previously functioned properly. The phone is powered on with a fully charged battery. However, the phone does not have connectivity. Which of the following describes the problem? A. Phone is disconnected from WiFi B. Provider is conducting system testing C. MAC address is bad D. Phone is in airplane mode D Which of the following alternative technologies allows a computer to run multiple operating systems without partitioning the hard drive? A. Web applications B. Dual boot C. Telepresence D. Virtualization D Which of the following is a 15-pin video connection? A. DVI B. S-video C. Component D. HDMI E. VGA E Which of the following is considered an optical storage medium? A. SSD B. Blu-Ray C. Flash drive D. Memory card B Which of the following are best practices when it comes to using a computer in a public location? (Select TWO). A. Notify the administrator when finished. B. Use strong passwords. C. Turn off the computer when finished. D. Disable the save password function on web pages. E. Make sure to clean the keyboard when finished. F. Make sure to log out of websites when done. D F Which of the following is a feature of a basic power strip? A. Protects against lightning strikes B. Provides multiple outlets for power C. Generates power for devices D. Provides battery backup for devices B Which of the following connectors consists of three separate plugs for video? A. Display port B. S-video C. Thunderbolt D. Component D Which of the following technologies allows people to communicate all over the world inexpensively? A. Virtualization B. SSID C. Kinetics D. VoIP D Several users want to share a common folder with high availability. Which of the following devices is BEST to use for this requirement? A. Large USB flash drive connected to a PC B. Medium capacity SATA hard drive C. Network attached storage appliance D. Firewall with security management C Which of the following is MOST likely required during installation in order to legally install software? A. Automatic updates B. Service level agreement C. License key D. Antivirus software C Which of the following would BEST be described as password best practices? (Select THREE). A. Use of long passwords B. Sharing passwords with a trusted source C. Limiting password reuse D. Keeping default passwords E. Use of special characters F. Writing down difficult passwords A C E A user wants to purchase a CAD application that requires 8GB of RAM to operate. Which of the following operating system types is required? A. 8-bit B. 16-bit C. 32-bit D. 64-bit D Which of the following BEST describes the pros and cons of a home wired network? A. Low throughput, low mobility, high availability, high latency, high security B. High throughput, high mobility, low availability, low latency, high security C. High throughput, low mobility, high availability, low latency, high security D. Low throughput, high mobility, low availability, high latency, low security C Joe, a user, wishes to allow his roommate to access his personal computer for Internet browsing, but does not want his roommate to have the ability to make changes to the system. Which of the following BEST describes the type of account Joe should create for his roommate? A. Standard B. Guest C. Administrator D. Power user B A user, Ann, receives a call asking for her password to troubleshoot a problem. Which of the following describes this type of security threat? A. Malware B. Social engineering C. Spam D. Physical security B Where can a user find the latest updates, upgrades, or firmware for an electronic device that the vendor supports? A. Internet search engine B. Internet forum C. Technical community groups D. OEM website D A user needs to download tax documents from a financial website. Which of the following is the website MOST likely to use for transmission of the tax document to the users browser? A. HTTP B. HTTPS C. SFTP D. FTP B When connecting a printer to a network, which of the following is needed to complete the process? (Select TWO). A. IP address B. User's password C. Computer's name D. Subnet mask E. HTTP port F. Fax number A D Which of the following is a reason that a user might upgrade a video card driver? (Select TWO). A. To decrease the screen resolution B. To access monitor standby mode C. To fix an error message D. To use additional features E. To adjust the brightness/contrast C D Before purchasing a new video card for a PC, which of the following should be checked to ensure there will be enough electricity for the video card to function properly? A. GPU B. CPU C. GUI D. PSU D A laptop owner, Ann, can no longer see web pages when she opens her browser, and she can only see her search bars and plug-ins. Which of the following is the MOST likely source of this issue? A. The computer does not have current antivirus software installed B. The computer needs to have its components upgraded C. The downloaded toolbars are filling the browser screen D. The owner was not using complex passwords C Which of the following are considered input devices for a computer? (Select TWO). A. Mouse B. Printer C. Speakers D. Microphone E. Monitor A D While browsing the Internet, a user receives a warning regarding the display of mixed content. The address bar includes https, and the lock symbol is showing. Which of the following does this warning indicate about the website? A. It stores data in cache or cookies, but not both. B. It requires login credentials for some sections. C. It contains both secure and non-secure parts. D. It is best viewed with a different browser. C Which of the following is the BEST example of productivity software? A. Word processing software B. Entertainment software C. Image editing software D. Anti-malware software A Which of the following file formats contain other files within them? (Select TWO). A. tiff B. dmg C. png D. mp3 E. iso F. flac B E Which of the following printers requires a special type of paper in order to print? A. Impact B. Thermal C. Inkjet D. Laser B When applying ergonomics to a workstation area, which of the following are the MOST important to consider? (Select TWO). A. Proper sitting position B. Amount of time computer will be used C. Clarity of the display D. Proper keyboard and mouse height E. Number of speakers in sound system F. Brightness and contrast of the display A D By default, which of the following types of operating systems can automatically detect a users location while the user is traveling in a bus? A. Server B. Desktop workstation C. Virtual server D. Mobile D A technician is typing the password to logon to a system. A user is standing in close proximity to the technician and is able to see the password being typed. Which of the following BEST describes this situation? A. Dumpster diving B. Shoulder surfing C. Phishing D. Social engineering B Which of the following is the function of a CPU? A. Encrypts data for remote transmission B. Performs data computation C. Supplies electricity to components D. Provides storage location for files B A technician is setting up a computer that was shipped. After everything is plugged in, the computer will not turn on. Which of the following should the technician do FIRST to identify the issue? A. Check for physical damage on the computer. B. Search for a solution on the Internet. C. Reference the manufacturer's documentation. D. Ensure the power supply is set at the correct voltage. D A user installing a printer can connect it to which of the following ports? (Select FOUR). A. PS/2 B. VGA C. DVI D. USB E. FireWire F. Serial G. RJ-11 H. Parallel D, E, F, H When operating under optimal network conditions, which of the following has the HIGHEST reliability? A. Bluetooth B. Wired C. Cellular D. WiFi B When setting up a new workstation, which of the following should be configured during the initial OS setup wizard? A. Additional software B. Date and time settings C. Peripheral devices D. Security software D. Security software B When applying ergonomics to a workstation area, which of the following are the MOST important to consider? (Select TWO). A. Proper sitting position B. Amount of time computer will be used C. Clarity of the display D. Proper keyboard and mouse height E. Number of speakers in sound system F. Brightness and contrast of the display A D Which of the following allows for the FASTEST printer connections? A. Bluetooth B. USB C. Parallel D. Serial B A user has purchased some new software from a vendor and wants to install it on all of the Windows computers in the house. Which of the following will help the user accomplish the task and ensure compliance with the software vendor? A. Copy and paste the program between computers. B. Purchase a multi-user license. C. Purchase a single-user license. D. Use remote desktop to share the program between computers. B An employee, Joe, forgot his laptop at the airport. Joe is worried about unauthorized access. Which of the following BEST protects against data theft in this instance? A. Security software B. Full disk encryption C. Cable lock D. Username and password E. Patching the OS and third party software B Which of the following printers requires a special type of paper in order to print? A. Impact B. Thermal C. Inkjet D. Laser B Which of the following is a common characteristic of open source software? A. Update cycles are dictated by the manufacturer B. Modifications to core functionalities are made by the manufacturer C. Can only run on certain manufacturer processors D. Can be fully modified by the user D A user, Ann, is experiencing slow browsing on a website she frequently visits that displays constant pop-up ads. Which of the following is the MOST likely cause? A. The browser is incompatible with the website B. The workstation has been infected with malware C. The website is not secured by SSL D. The certificate of the website has expired B Which of the following components is required to send faxes via POTS? A. NIC B. Power supply C. Modem D. Wireless adapter C Which of the following file formats contain other files within them? (Select TWO). A. tiff B. dmg C. png D. mp3 E. iso F. flac B E A user working on a laptop notices the mouse cursor frequently moves to random locations in a document while typing. Which of the following should the user do FIRST to help resolve this issue? A. Ask tech support for help. B. Reboot the laptop. C. Turn off the touchpad. D. Reconnect the mouse. C A users laptop hard drive contains sensitive information. The user often plugs the laptop into the corporate network. A sensitive file from the laptop has been found on another users laptop. How could the user have prevented this breach? A. Disable file and print sharing on the laptop. B. Delete unused drives from network. C. Remove shared keys from the key ring. D. Set the read-only attribute on the files. A Which of the following is the BEST reason to backup data? A. To ensure data encryption B. To ensure data stability C. To ensure data security D. To ensure data availability D A users operating system is set to automatically update as updates are released. However, last weeks updates failed to download. Which of the following should the user do FIRST to install the updates? A. Reference the OS manufacturer's website. B. Run a virus scan to remove viruses. C. Reinstall the operating system. D. Change the automatic update schedule. E. Manually download the updates. E Which of the following will allow the easiest and fastest way to share a single file between two modern smartphones without joining the same WiFi network? A. Micro SD card B. Bluetooth C. USB connection D. Infrared B An employees new computer came with a free 30-day trial version of antivirus software. The employees company provides enterprise antivirus software from a different vendor. Which of the following should the employee do in order to use a full version of antivirus software? A. Enter the company product key for the antivirus software, enabling the full version. B. Uninstall the current version antivirus software and install the company version. C. Verify Internet connectivity and run online virus scanning software. D. Update the trial antivirus software to the latest version. B Which of the following can a user configure on an operating system so that an audible sound is made when an error message is displayed? A. Encryption B. Hot keys C. Accessibility options D. Screen captures C A user is setting up an older wireless access point that has only WEP for encryption. Which of the following additional steps will help to secure the network? (Select TWO). A. Disable SSID broadcast. B. Refresh the MAC address. C. Filter the MAC address. D. Refresh the IP address. E. Use CAT6 cables. A C Which of the following extensions identifies a video file? A. .msi B. .tar C. .img D. .mp4 D A technician has just finished setting up a SOHO wireless router but the client does not want the PC on the wireless network for security reasons. The technician connects an RJ- 45 cable to the computer and the router, but does not receive network connectivity. Which of the following is the NEXT step to diagnose the problem? A. Change the IP address on the computer to match the router. B. Reseat the power cable on the computer and reboot. C. Check for link light activity on the computer and the router. D. Change the hostname of the router to match the computer's network. C Multiple laptops that contain confidential data are stolen from a company. Which of the following is a likely policy change resulting from this incident? A. Enabling full disk encryption B. Requiring screensaver password C. Disabling Bluetooth adapters D. Adding multifactor authentication A A user is configuring a SOHO wireless router. The user should change the routers default administrator password for which of the following reasons? A. To prevent improper data transmission encryption B. To prevent unauthorized configuration changes C. To prevent social engineering attacks D. To increase wireless signal strength B A user will be traveling with a smartphone that contains confidential information. Which of the following should be disabled? (Select TWO). A. Keyboard B. Speakers C. Mouse D. Bluetooth E. NFC D E Which of the following security threats occurs when a user receives an email from an illegitimate source asking for login information? A. Hacking B. Phishing C. Spam D. Cracking B An attacker cracks a user's password for all social media, email, and bank accounts. The user needs to change the passwords for all these accounts. Which of the following should the user do in the future to prevent this from happening? A. Disable unused browser toolbars. B. Clear the browser cache. C. Avoid credential reuse. D. Delete tracking cookies. C After installing the OS on a workstation, a technician notices that everything is displayed in large windows and the viewing area is limited. Which of the following will the technician need to adjust to resolve this issue? A. Color depth B. Orientation C. DPI settings D. Resolution D Joe, a user, needs to store a large amount of data, but does not have enough space on his local computer. Which of the following are the BEST options for him to use? (Select TWO). A. Network attached storage B. External hard drive C. Optical drive D. USB thumb drive E. Another computer A B A technician has just finished setting up a SOHO wireless router but the client does not want the PC on the wireless network for security reasons. The technician connects an RJ- 45 cable to the computer and the router, but does not receive network connectivity. Which of the following is the NEXT step to diagnose the problem? A. Change the IP address on the computer to match the router. B. Reseat the power cable on the computer and reboot. C. Check for link light activity on the computer and the router. D. Change the hostname of the router to match the computer's network. C Which of the following could be described as both an input and output device? A. Flat-screen monitor B. Multi-function printer C. Microphone D. Scanner B A technician has been tasked with changing the settings for a used SOHO router, but does not have the administrator password because the previous owner changed it. Which of the following actions will resolve this issue? A. Click "Forgot password." B. Use a password cracker. C. Hold the reset button. D. Use the password: password. C A user learns of an operating system vulnerability that would allow a hacker to access the computer. The user would like to keep the operating system up to date to prevent such vulnerabilities from occurring. Which of the following should the user configure? A. Additional OS features B. Automatic updates C. Software firewall D. Anti-malware software B CONTINUED... [Show More]
Last updated: 2 years ago
Preview 1 out of 55 pages
Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$19.50
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Apr 10, 2023
Number of pages
55
Written in
All
Additional information
This document has been written for:
Uploaded
Apr 10, 2023
Downloads
0
Views
95