Code HS Questions and Answers with
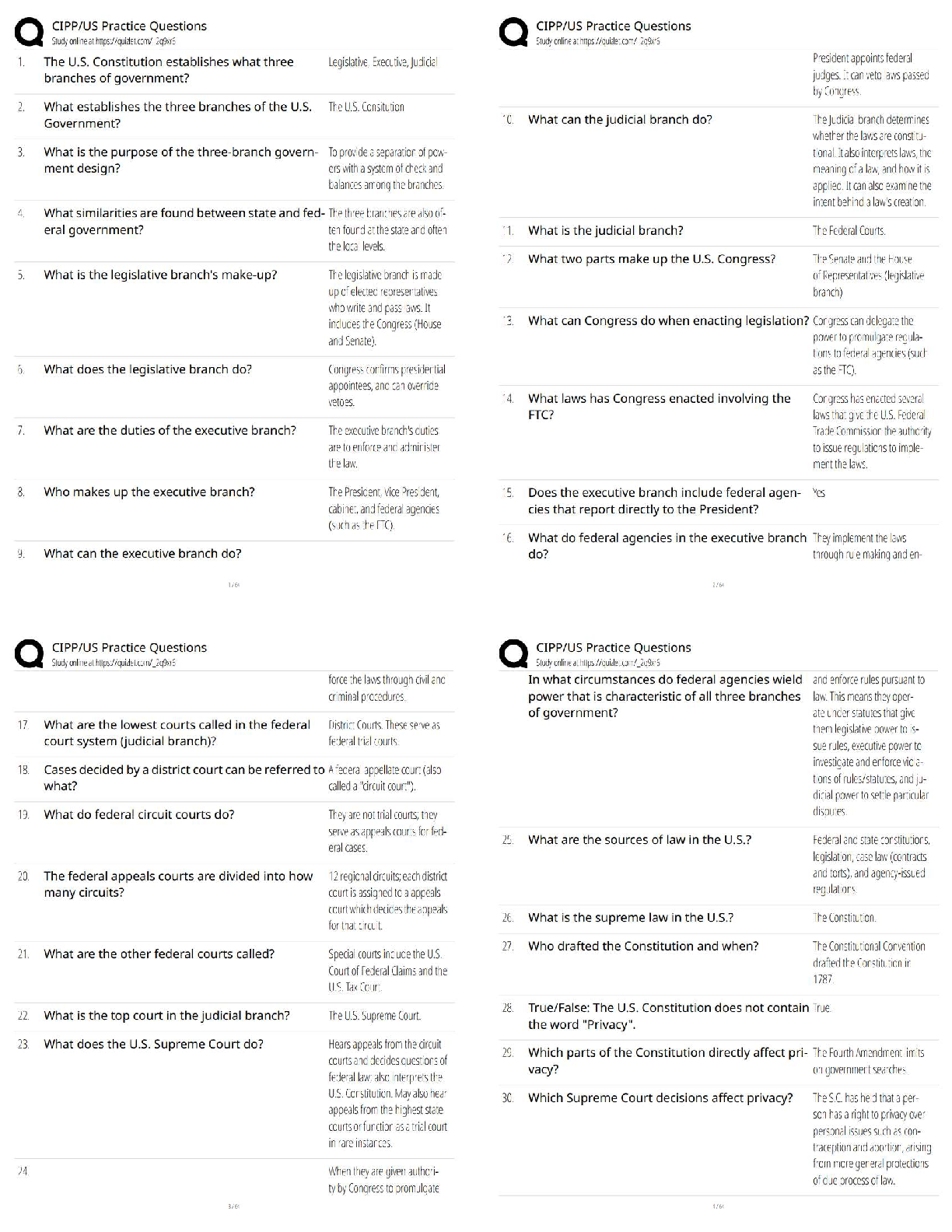
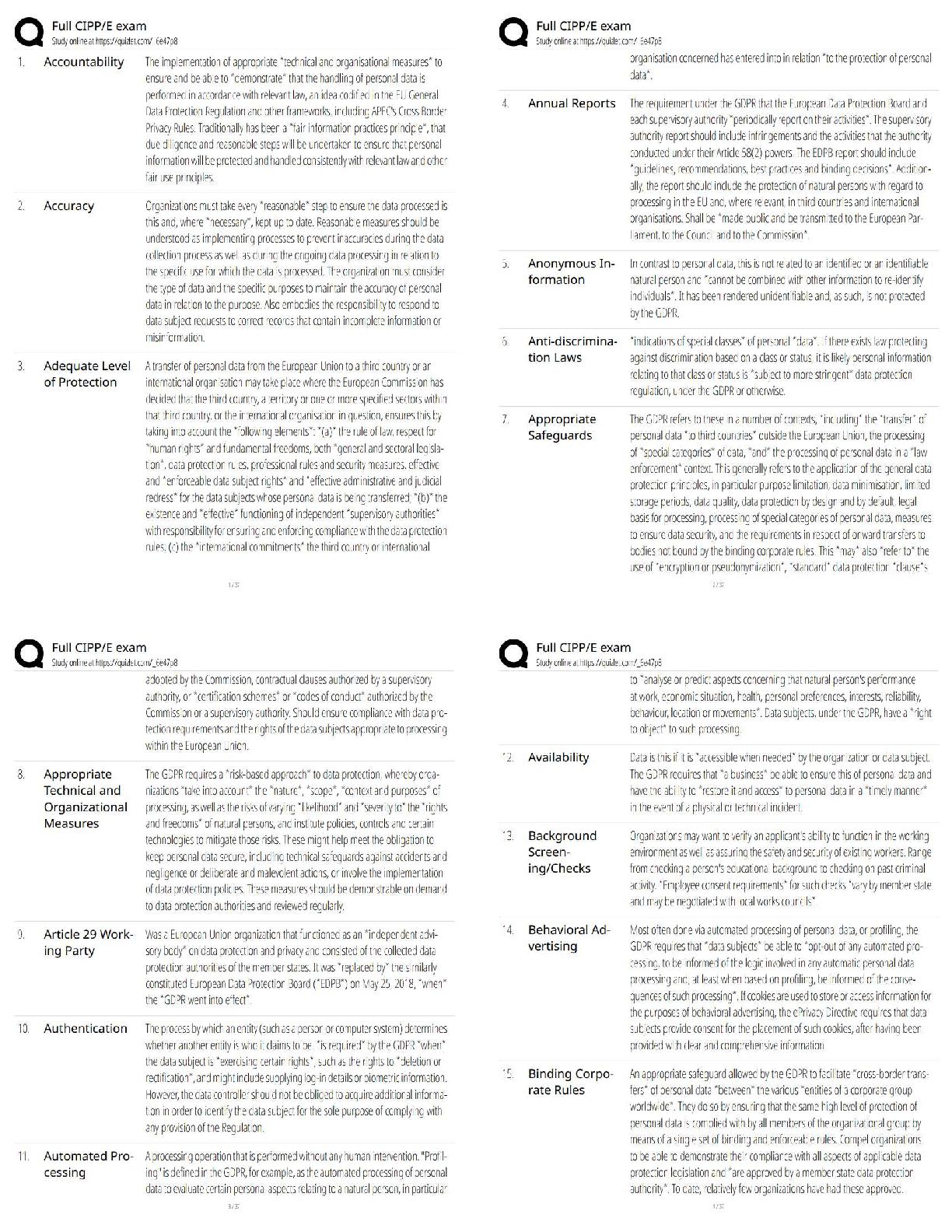
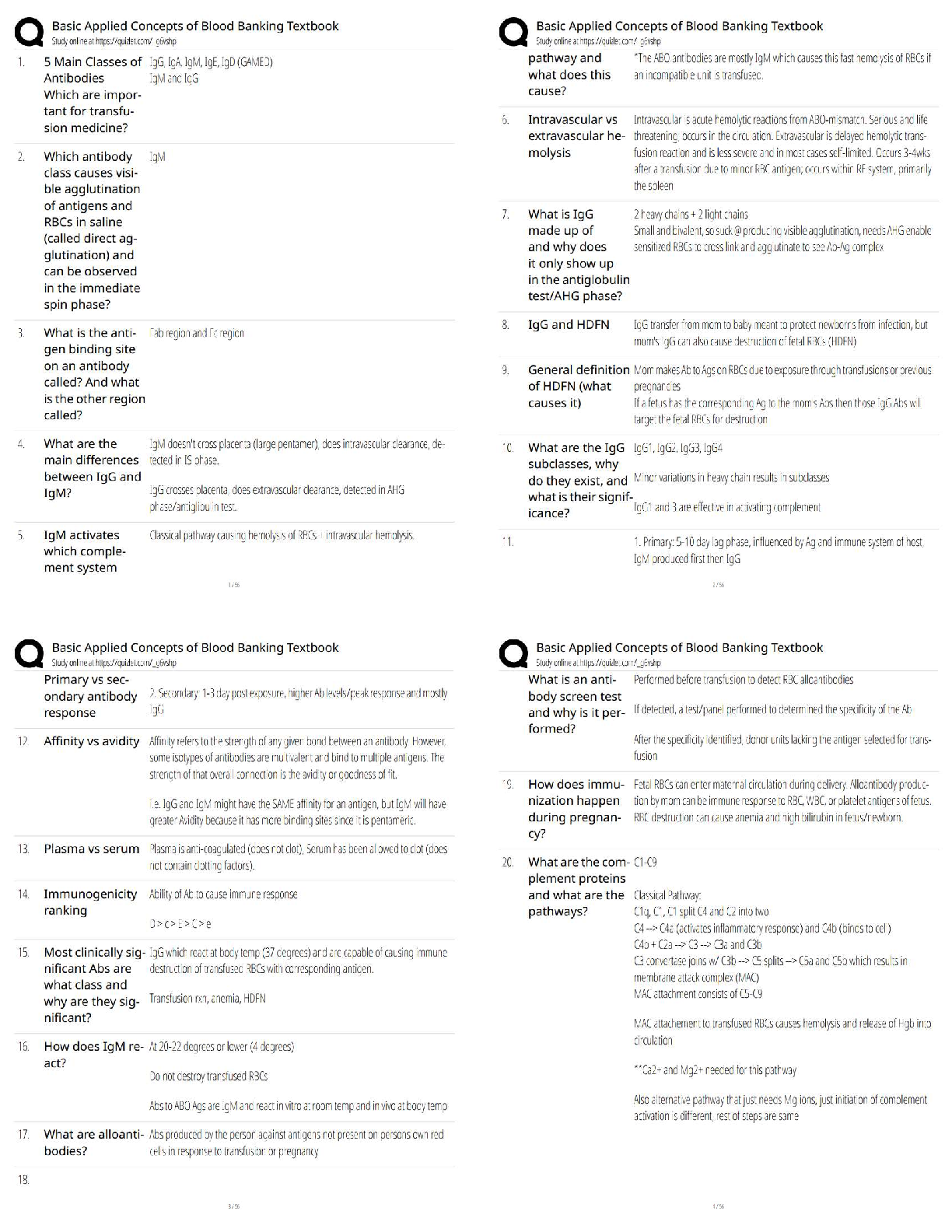
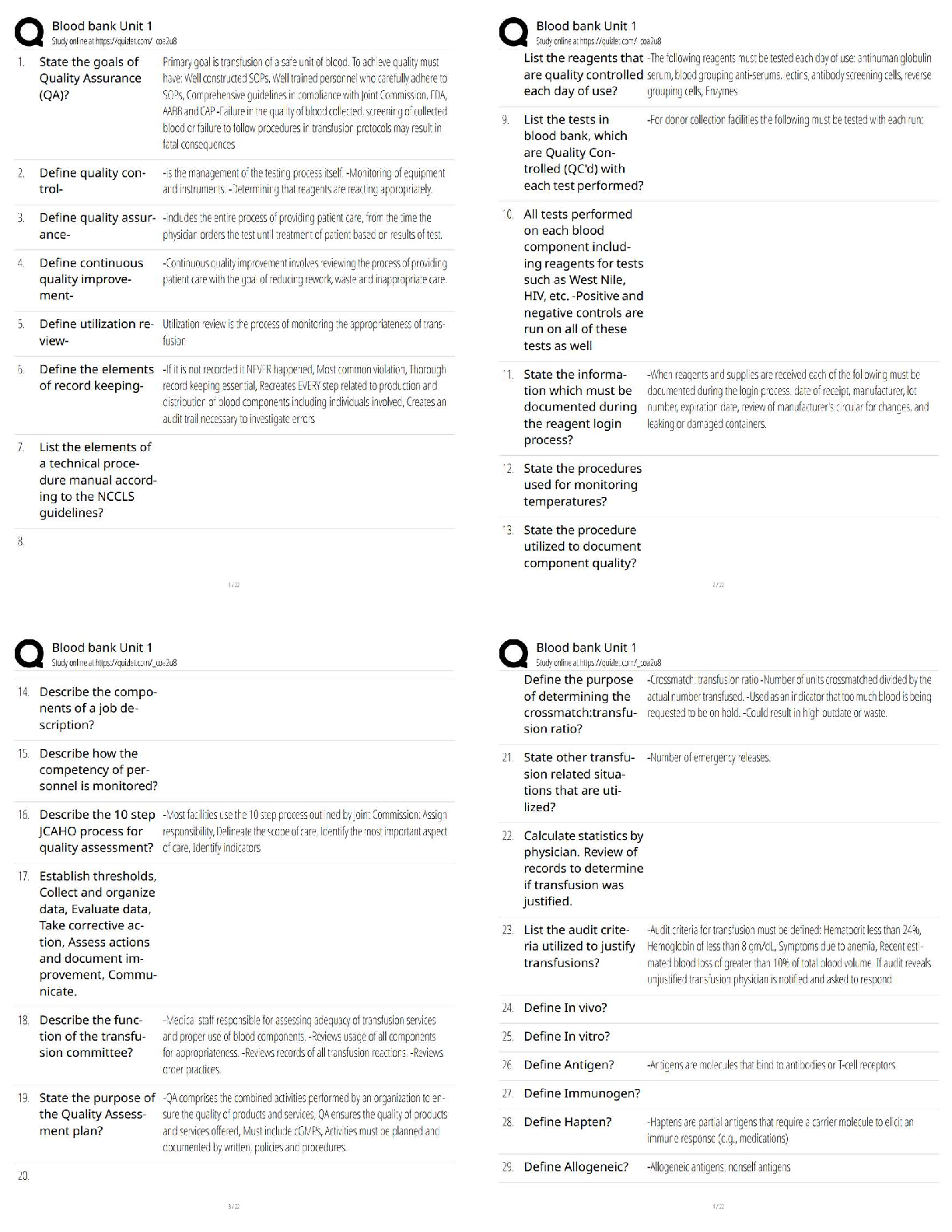
Certified Solutions
Which of the following statements are true about the Internet?
I - The Internet connects devices and networks all over the world
II - The Internet helps people c
...
Code HS Questions and Answers with
Certified Solutions
Which of the following statements are true about the Internet?
I - The Internet connects devices and networks all over the world
II - The Internet helps people collaborate to solve problems
III - The Internet helps people communicate
IV - There are no negative consequences of the Internet, it is purely positive ✔✔I, II, and III
Which of the following refers to a widely agreed upon set of rules that standardize
communication between machines? ✔✔Protocol
True or False: The Internet is non-existent in the developing world. ✔✔False
Which of the following makes sure that each request is forwarded to its intended recipient?
✔✔Router
True or False: The Internet is a network connecting individual networks. ✔✔True
How is the bandwidth of a network measured? ✔✔Bitrate. Higher bitrate means higher
bandwidth.
What is the bitrate of a system? ✔✔The amount of data (in bits) that can be sent in a fixed
amount of time
What is the latency of a system? ✔✔Time it takes for a bit to travel from sender to receiver
What is the Internet Protocol (IP)? ✔✔A protocol that defines the structure of an Internet address
and assigns a unique address to every device on the Internet
IP addresses are hierarchical. This means: ✔✔The information in an IP address goes from broad
to specific.
What is the function of the Domain Name System (DNS)? ✔✔To translate domain names into IP
addresses
According to the Domain Name System (DNS), which of the following is a subdomain of the
domain example.com? ✔✔about.example.com
What does redundancy mean in the context of Internet routing? ✔✔Multiple paths exist between
any two points
Which of the following is a benefit of the fault-tolerant nature of Internet routing? ✔✔The
ability to provide data transmission even when some connections between routers have failed
What information is contained in a packet? ✔✔A small part of a digital message, and metadata
about the message, including where it came from and where it is going.
True or False: All data sent over the Internet is broken down into several packets and sent over
the network. ✔✔true
Which of the following protocols allows for sending multiple packets between two computers by
checking that all packets arrived and that they can be put back together in the proper order?
✔✔Transmission Control Protocol (TCP)
A user enters a Web address in a browser, and a request for a file is sent to a Web server. Which
of the following best describes how the file is sent back to the user? ✔✔The file is broken into
packets and sent over a network. The packets must be reassembled by the user's computer when
they are received. If any packets are missing, the browser re-requests the missing packets.
What is the purpose of packet metadata? ✔✔Metadata helps route the data to the correct
destination, and helps piece the data together at the destination
Which of the following does not demonstrate a harmful consequence of increased anonymity on
the Internet? ✔✔Users can avoid targeted discrimination in an online forum.
What is the purpose of the Digital Millennium Copyright Act? ✔✔To criminalize the act of
circumventing, or getting around, access controls that block access to copyrighted works.
To criminalize the act of circumventing, or getting around, access controls that block access to
copyrighted works. ✔✔A government filtering search results to limit the access of information
and suppress discussion amongst its citizens
A company's server is flooded with data until it can no longer cope with the volume, rendering
the server unreachable. What type of attack is this? ✔✔(Distributed) Denial of Service
Social engineering is one of the most effective ways to attack a network. ✔✔true
Having network users login with a username and password is an example of: ✔✔Authentication
AAA in network security is a protocol that stands for: ✔✔Authorization, Authentication,
Accounting
Allowing network users to delete certain files from a directory is an example of:
✔✔Authorization
Tracking how long network users spend on FaceBook or Instagram is an example of:
✔✔Accounting
[Show More]