WGU C701 > QUESTIONS & ANSWERS > WGU C701 - CEH Pre Assessment Already Passed (All)
WGU C701 - CEH Pre Assessment Already Passed
Document Content and Description Below
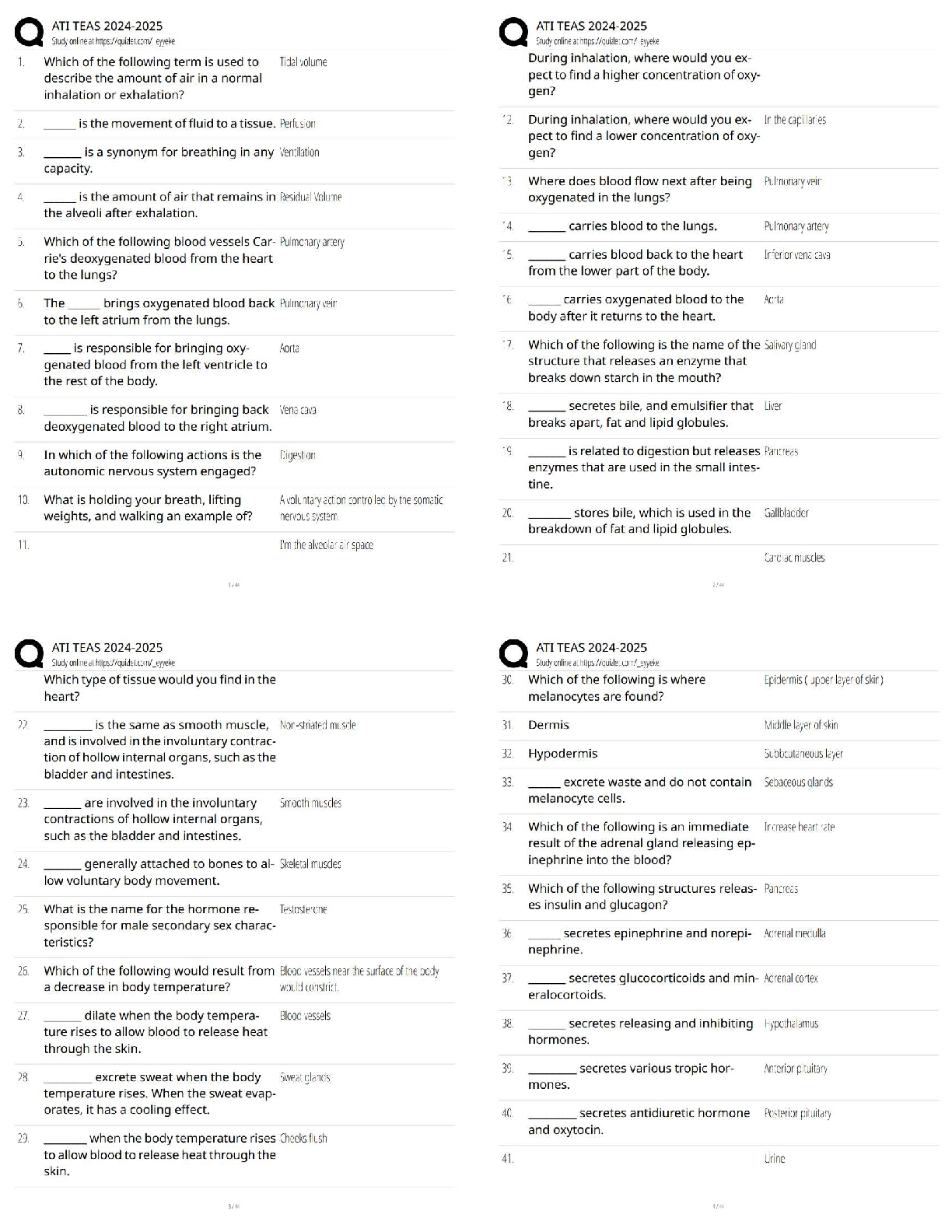
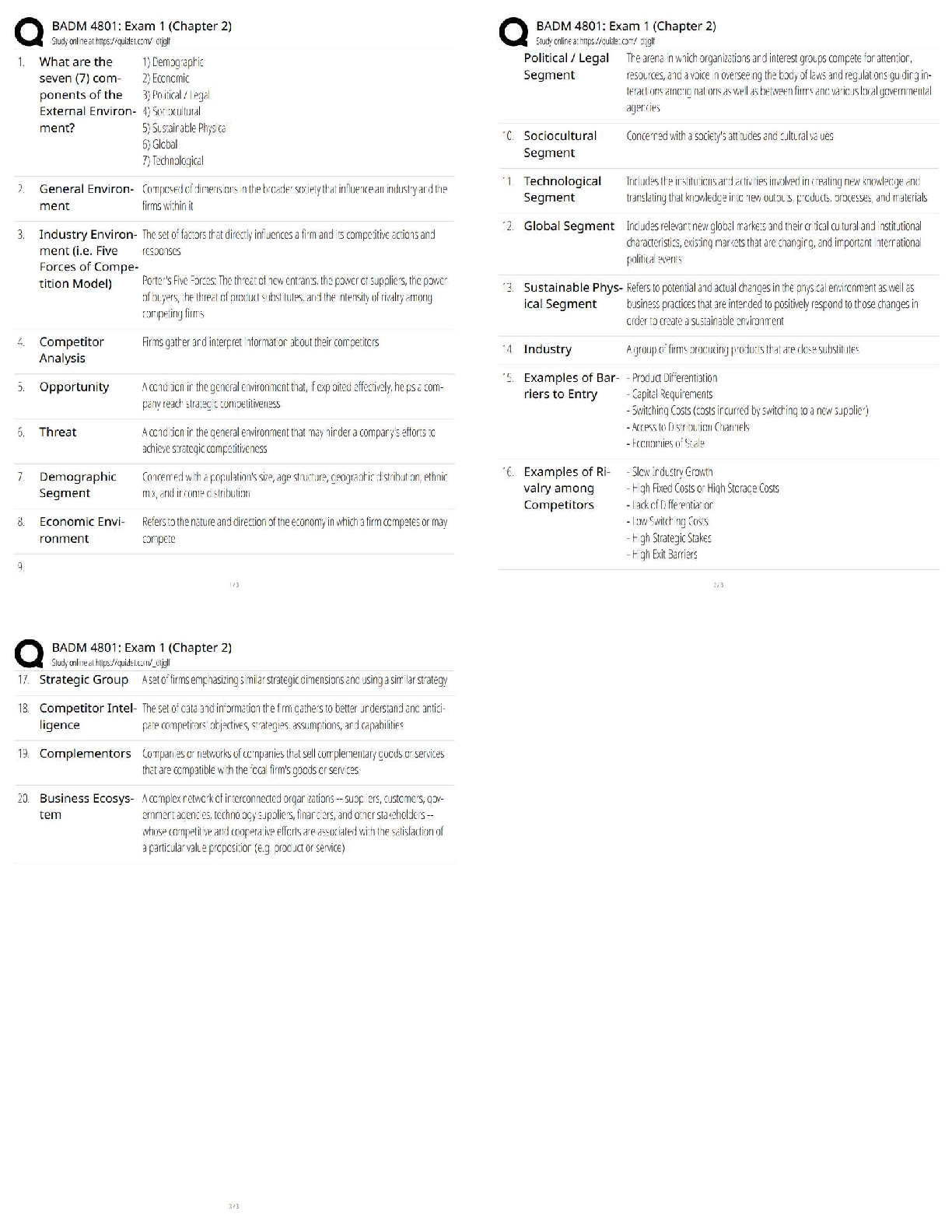
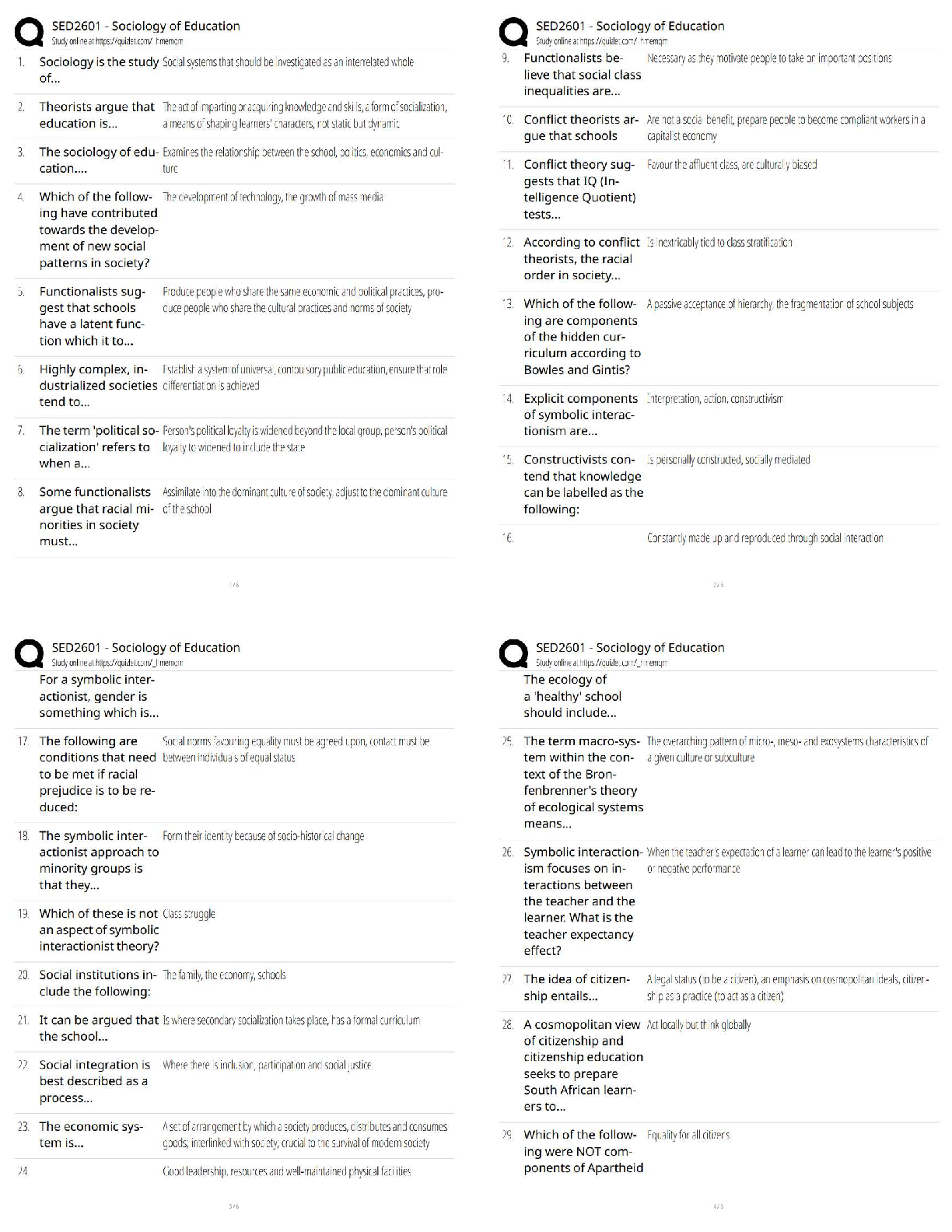
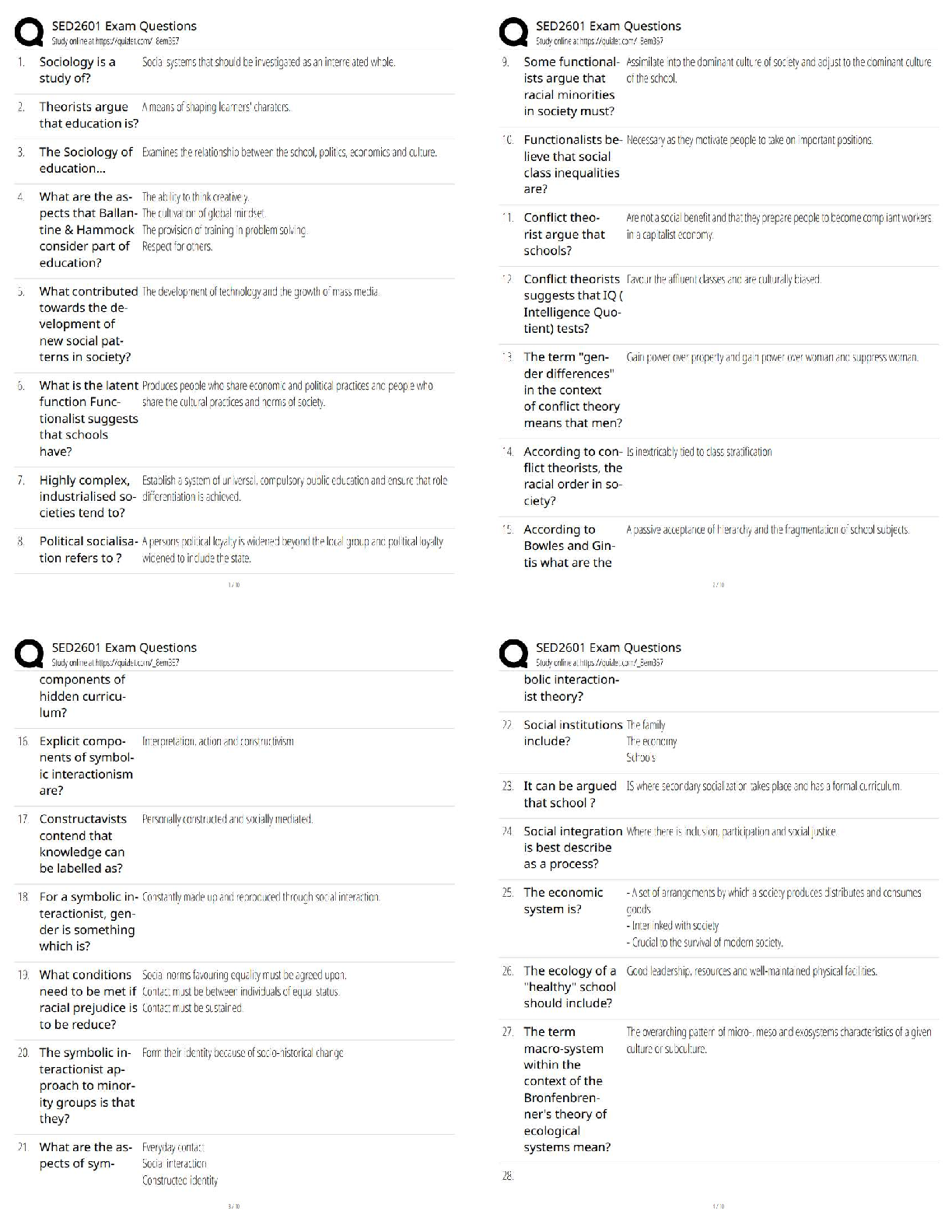
WGU C701 - CEH Pre Assessment Already Passed Defense-in-depth is a security strategy in which several protection layers are placed throughout an information system. It helps to prevent direct attac ... ks against an information system and data because a break in one layer only leads the attacker to the next layer. ✔✔True Penetration testing is a method of actively evaluating the security of an information system or network by simulating an attack from a malicious source. Which of the following techniques is used to simulate an attack from someone who is unfamiliar with the system? ✔✔Black box pen testing Which of the following scanning technique attackers use to bypass firewall rules, logging mechanisms, and hide themselves as usual network traffic? ✔✔Stealth scanning technique Which of the following scan only works if operating system's TCP/IP implementation is based on RFC 793? ✔✔NULL scan OS fingerprinting is the method used to determine the operating system running on a remote target system. It is an important scanning method, as teh attacker will have a greater probability of success if he/she knows the OS. Active stack fingerprinting is one of the types of OS fingerprinting. Which of the following is true about active stack fingerprinting? ✔✔Is based on the fact that various vendors of OS implement the TCP stack differently Proxy is a network computer that can serve as an intermediary for connecting with other computers. Which of the followng sentences is true about a proxy? ✔✔Protects the local network from outside access IP spoofing refers to the procedure of an attacker changing his or her IP address so that he or she appears to be someone else. Which of the following IP spoofing detection technique succeed only when the attacker is in a different subnet? ✔✔Direct TTL probes technique Enumeration is defined as the process of extracting user names, machine names, network resources, shares and services from a system. Which of the following enumeration an attacker uses to obtain list of computers that belongs to a domain? ✔✔Netbios enumeration Network Time Protocol (NTP) is designed to synchronize clocks of networked computers. Which of the following port NTP uses as its primary means of communication? ✔✔UDP port 123 Rootkits are kernel programs having the ability to hide themselves and cover up traces of activities. It replaces certain operating system calls and utilities with its own modified versions of those routines. Which of the following rootkit modifies the boot sequence of the machine to load themsevles instead of the original virtual machine monitor or operating system? ✔✔Hypervisor level rootkit Steganography is a technique of hididng a secret message within an ordinary message and extracting it at the destination to maintain confidentiality of data. Which of the following steganography technique embed secret message in the frequency domain of a signal? ✔✔Transform domain techniques A virus is a self-replicating program that produces its own code by attaching copies of it into other executable codes. Which of the following virus evade the anti-virus software by intercepting its requests to the operating system? ✔✔Stealth/tunneling virus Lawful intercept is a process that enables a Law Enforcement Agency (LEA) to perform electronic surveillance on a target as authorized by a judicial or adminstrative order. Which of the following statements is true for lawful intercept? ✔✔Hides information about lawful intercepts from all but the most privileged users Sniffer turns the NIC of a system to the promiscuous mode so that it listens to all the data transmitted on its segment. It can constantly read all information entering the computer through the NIC by decoding the information encapsulated in the data packet. Passive sniffing is one of the types of sniffing. Passive sniffing refers to: ✔✔sniffing through the hub Address Resolution Protocol (ARP) is a protocol for mapping an IP address to a physcial machine address that is recognized in the local network. ARP Spoofing involves constructing a arge number of forged ARP request and reply packets to overload: ✔✔Switch Denial of Service (DoS) is an attack on a computer or network that prevents legitimate use of its resources. In a DoS attack, attackers flood a victim system with non-legitimate service requests or traffic to overload its resources, which prevents it from performing intended tasks. Which of the following is a symptom of a DoS attack? ✔✔Unavailability of a particular website Session hijacking refers to the exploitation of a valid computer session where an attacker takes over a session between computers. Which of the following factors contribute to a successful session hijacking attack? ✔✔Weak session ID generation algorithm Buffer Overflow occurs when an application writes more data to a block of memory, or buffer, than the buffer is allocated to hold. Buffer overflow attacks alow an attacker to modify the _______ in order to control the process execution, crash the process and modify internal variables. ✔✔Target process's address space Which wireless standard has bandwidth up to 54 Mbps and signals in a regulated frequency spectrum around 5GHz? ✔✔802.11a Which device in a wireless local area network (WLAN) determines the next network point to which a packet should be forwarded toward its destination? ✔✔Wireless router Wireless antenna is an electrical device which converts electric currents into radio waves, and vice versa. Which of the following antenna used in wireless base statins and provides a 360 degree horizontal radiation pattern? ✔✔Omnidirectional antenna Wi-Fi Proctected Access (WPA) is a data encryption method for WLANs based on 802.11 standards. It improves on the authentication and encryption features of WEP (Wired Equivalent Privacy). Temporal Key Integrity Protocol (TKIP) enhances WEP by adding a rekeying mechanism to provide fresh encryption and integrity keys. Temporal keys are changed for every ______. ✔✔10,000 packets Firewall is a set of related programs, located at a network gateway server that protects the resources of a private network from users from other networks. A firewall examins all traffic routed between the two networks to see if it meets certain criteria. Packet filter is one of the categories of firewall. Packet filtering firewall works at which of these layers of the OSI model? ✔✔Network layer Keystroke loggers are stealth software packages that are used to monitor keyboard activities. Which is the best location to place such keyloggers? ✔✔Keyboard hardware and the operating system You have invested millions of dollars for protecting your corporate network. You have the best IDS, firewall with strict rules and raouters with no configuration errors. Which of the following techniques practiced by an attacker exploits human behavior to make you network vulnerable to attacks? ✔✔Social Engineering Firealls are categorized into two; namely hardware firewall and software firewall. Identify the correct statement for a software firewall. ✔✔Software firewall is placed between the normal application and the networking components of the operating system Nmap is a free open source utility, which is designed to rapidly scan large networks. identify the nmap scan method that is often referred to as half open scan because it does not open a full TCP connection. ✔✔SYN stealth As a system administrator, you are responsible for maintaining the website of your company which deals in online recharge of mobile phone cards. One day to your surprise, you find the home page of your company's website defaced. What is the reason for webpage defacement? ✔✔DNS attack through cache poisoning Which of the following protocols are susceptible to sniffing? ✔✔Telnet Hacker is a person who illegally breaks into a system or network without any authorization to destroy, steal sensitive data, or to perform any malicious attacks. Black hat hackers are: ✔✔Individuals with extraordinary computing skills, resorting to malicious or destructive activities and are also known as crackers In order to compromise or to hack a system or network the hackers go through various phases of the hacking. What is the first hacking phrase that hacckers perform to gather information aobut a target prior to launching an attack? ✔✔Reconnaissance RSA is a public-key cryptosystem developed by MIT professors Ronald L. Rivest, Adi Shamir, and Leonard M. Adleman in 1977 in an effort to help ensure Internet security. RSA uses modular arithmetic and elementary number theory to do computations using two very large prime numbers. Identify the statement which is true for RC6 algorithm: ✔✔Includes integer multiplication and the use of four 4-bit working registers Password cracking is a technique used to extract user's password of application/files without the knowledge of the legitimate user. Which of the password cracking technique will the attacker use if he/she gets some information about the password to crack? ✔✔Rule-based attack Secure Hashing Algorithm (SHA) is an algorithm for generating cryptographically secure oneway hash, published by the National Institute of Standards and Technology as a U.S. Federal Information Processing Standard. What is the block (word) size used by SHA-512 algorithm? ✔✔64-bit Which of the following cryptographic attack refers to extraction of cryptographic secrets (e.g. the password to an encrypted file) from a person by coercion or torture? ✔✔Rubber-Hose Attack Which of the following cryptographic attack refers to extraction of cryptographic secrets (e.g. the password to an encrypted file) from a person by coercion or torture? ✔✔Randomly replace the NOPs with functionally equivalent segments of the code (e.g.: x++; x-; ? NOP NOP) Firewall implementation and design for an enterprise can be a daunting task. Choices made early in the design process can have far-reaching security implications for years to come. Which of the following firewall architecture is designed to host servers that offer public services? ✔✔Screened subnet An intrusion detection system (IDS) gathers and analyzes information from within a computer or a network, to identify the possible violations of security policy, including unauthorized access, as well as misuse. Attackers use various IDS evasion techniques to bypass intrusion detection mechanisms. Which of the following evasion technique rely on Time-to-Live (TTL) fields of a TCP/IP packet? ✔✔Insertion attack Attackers craft malicious probe packets and scan for services such as HTTP over SSL (HTTPS), SMTP over SSL (SMPTS) and IMAP over SSL (IMAPS) to detect honeypots in a network. Which of the following condition shows the presence of a honeypot? ✔✔Ports show a particular service running but deny a three-way handshake connection Identify the denial-of-service attack that is carried out using a method known as "bricking a system." Unlike other DoS attacks, it sabotages the system hardware, requiring the victim to replace or reinstall the hardware. ✔✔Phlashing Some viruses affect computers as soon as their code is executed; other viruses lie dormant until a pre-determined logical circumstance is met. Identify the virus that modifies the directory table entries so that directory entries point to the virus code instead of the actual program. ✔✔Cluster Viruses Which of the following Wi-Fi chalking method refers to drawing symbols in public places to advertise open Wi-Fi networks? ✔✔WarChalking Wired Equivalent Privacy (WEP) is an IEEE 802.11 wireless protocol which provides security algorithms for data confidentiality during wireless transmissions. WEP uses stream cipher RC4 for confidentiality, and the CRC-32 checksum for integrity of wireless transmission. What is the size of WEP initilization vector (IV)? ✔✔24-bit Bletooth hacking refers to exploitation of Bluetooth stack implementation vulnerabilities to compromise sensitive data in Bluetooth-enabled devices and networks. Which of the following Bluetooth attacks refers to sending unsolicitied messages over Bluetooth to Bluetooth-enabled devices such as PDA and mobile phones? ✔✔Bluejacking Enumeration is defined as the process of extracting user names, machine names, network resources, shares and services from a system. Which of the following commands can be used in UNIX environments to enumerate the shared directories on a machine? ✔✔Showmount CAM table in switch stores information such as MAC addresses available on physcial ports with their associated VLAN parameters. What happens with the CAM table is full? ✔✔Additional ARP request traffic will flood every port on the switch Identify the web application attack where attackers exploit webpage vulnerabilities to force an unsuspecting user's brows to send malicious requests they did not intend. The victim holds an active session with a trusted site and simultaneously visits a malicious site, which injects an HTTP request for the trusted site into the victim user's session, compromising it's integrity. ✔✔Cross-site request forgery (CSRF) Jason, a penetration tester, is testing a web application that he knows is vulnerable to a SQL injection but the results of the injection are not visible to him. He tried waitfor delay command to check the SQL execution status which confirmed the presence of the SQL injection vulnerability. Which type of SQL injection Jason is attempting on the web application? ✔✔Blind SQL injection Consider the attack scenario given below: 1. User broswes a web page 2. Web server replies with requested page and sets a cookie on the user's browser 3. Attacker steals cookie 4. Attacker orders for product using modified cookie 5. Product is delievered to attacker's address ✔✔Cookie Poisoning An Intrusion detection system (IDS) gathers and analyzes information from within a computer or a network, to identify the possible violations of security policy, including unauthorized access, as well as misuse. Which of the following IDS detection technique detects the intrusion based on the fixed behavioral characteristics of the users and components in a computer system? ✔✔Anomaly detection [Show More]
Last updated: 2 years ago
Preview 1 out of 12 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Also available in bundle (1)
Click Below to Access Bundle(s)

WGU Master's Course C701 Bundled Exams with Verified Solutions
WGU Master's Course C701 Bundled Exams with Verified Solutions
By Nutmegs 2 years ago
$15
5
Reviews( 0 )
$10.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
May 21, 2023
Number of pages
12
Written in
All
Additional information
This document has been written for:
Uploaded
May 21, 2023
Downloads
0
Views
171










.png)