SPēD SFPC > QUESTIONS & ANSWERS > SPēD SFPC: General Questions and Answers Graded A (All)
SPēD SFPC: General Questions and Answers Graded A
Document Content and Description Below
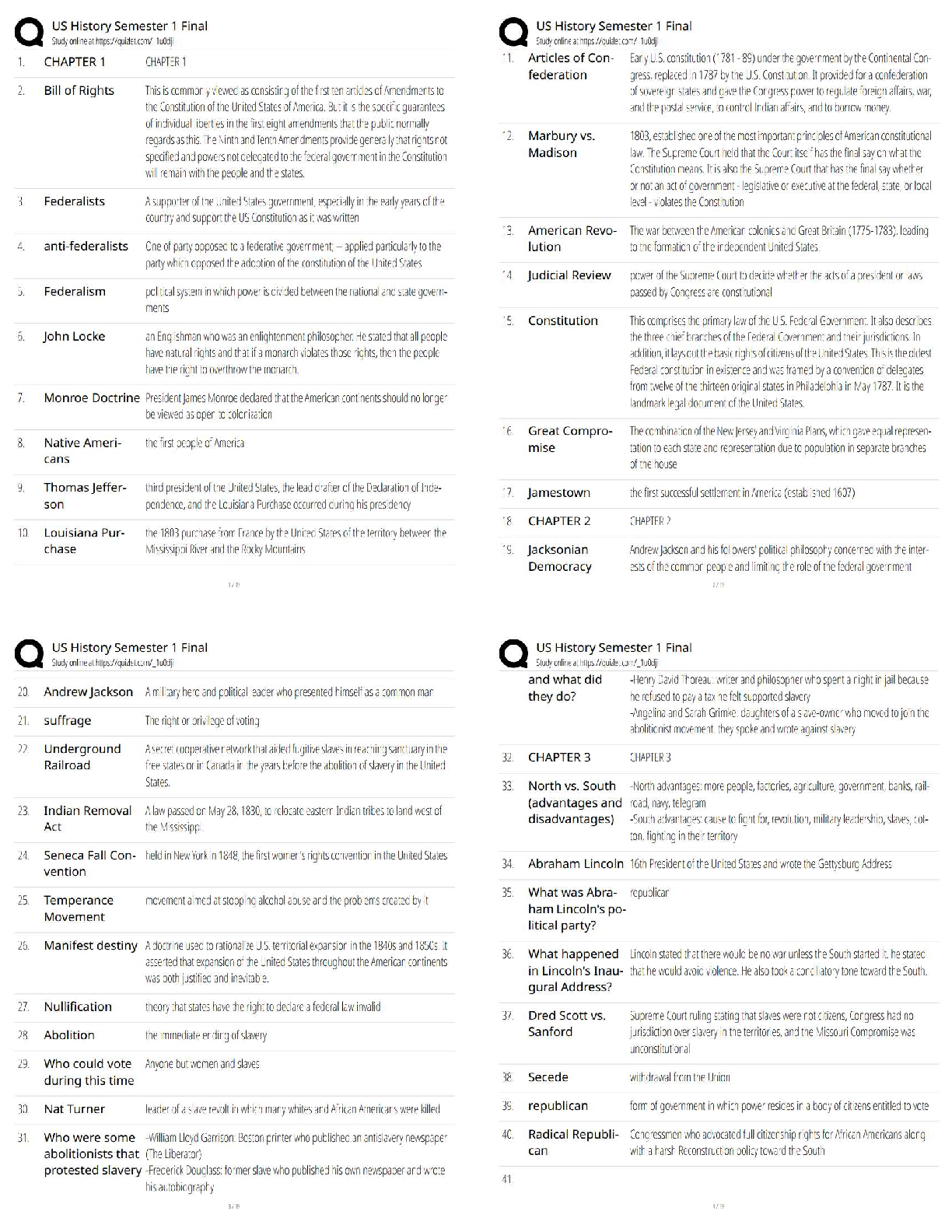
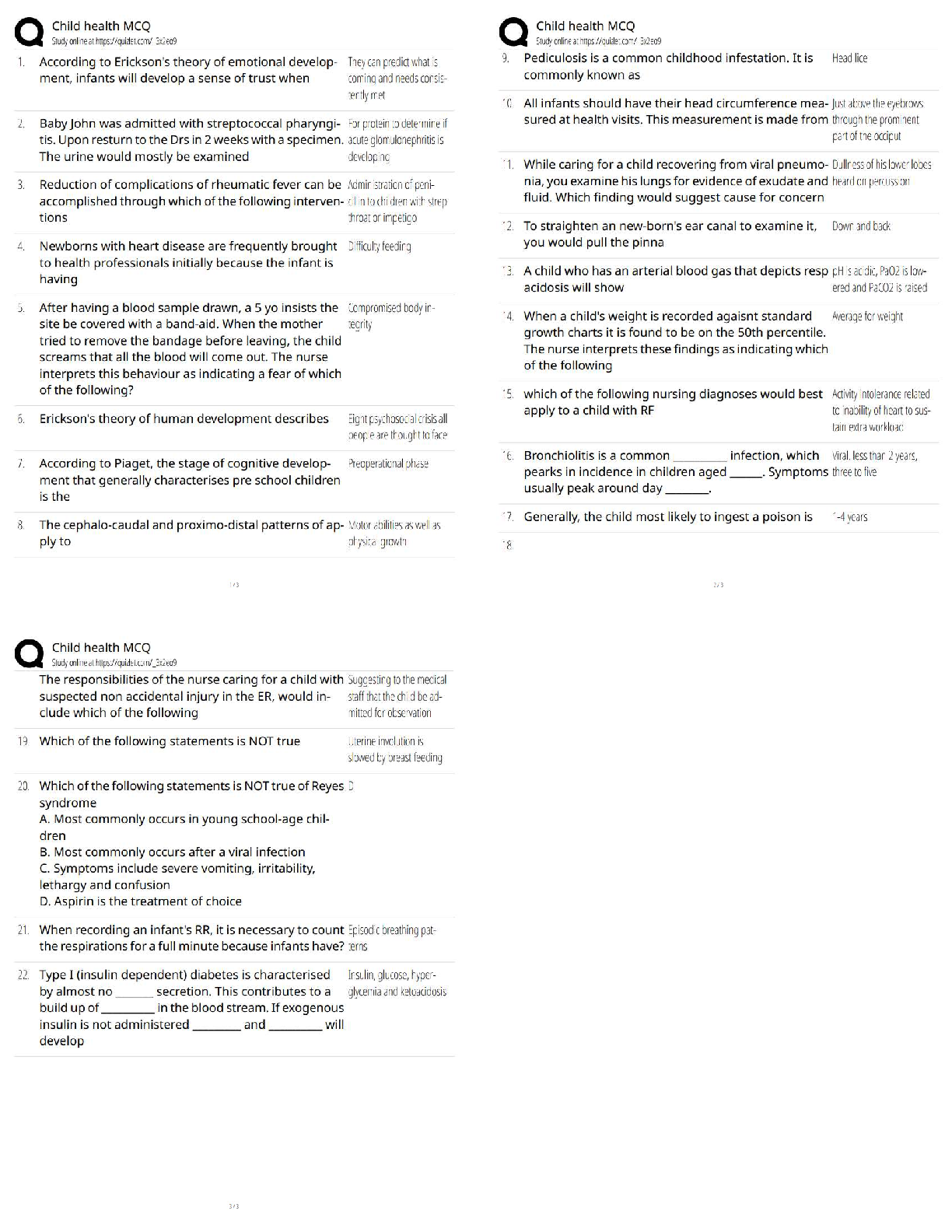
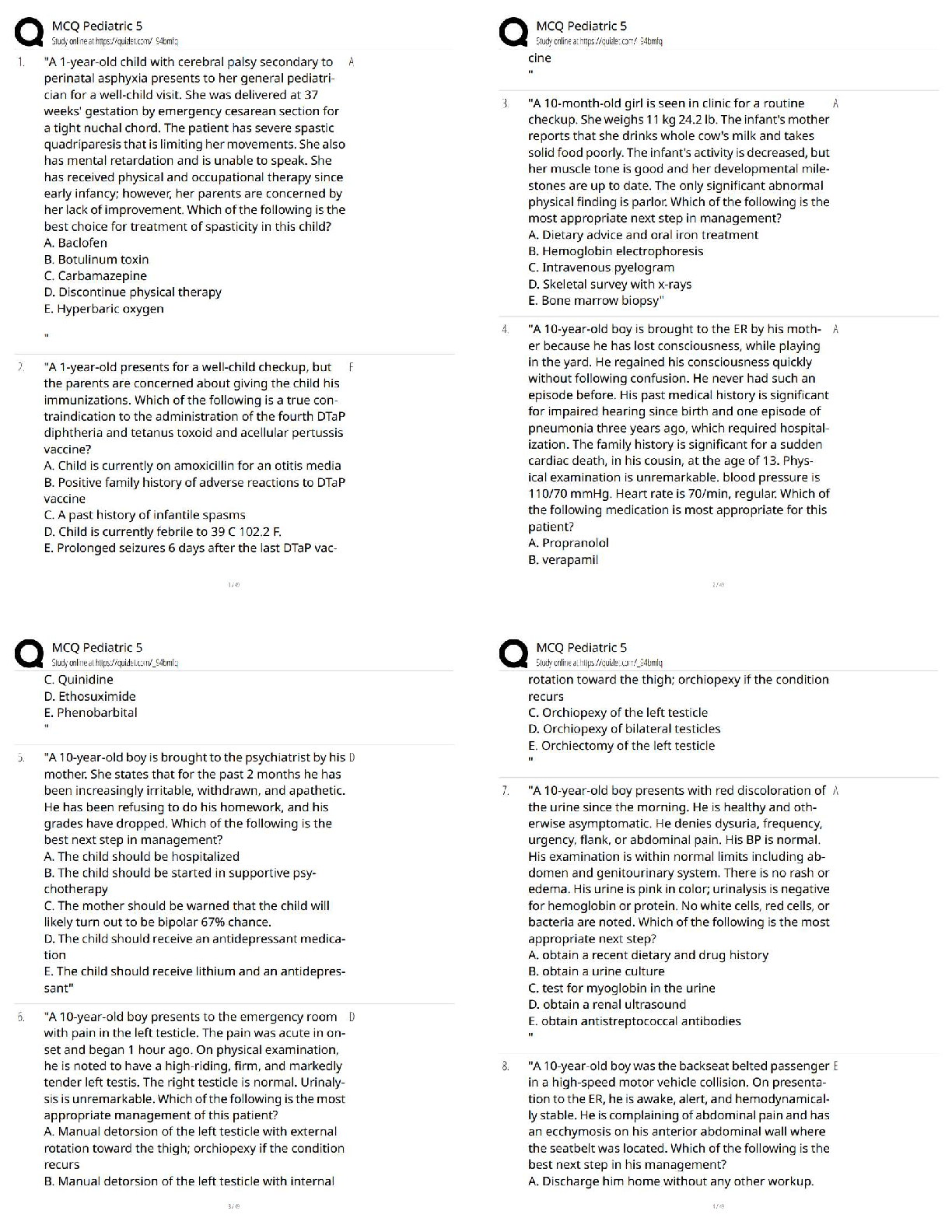
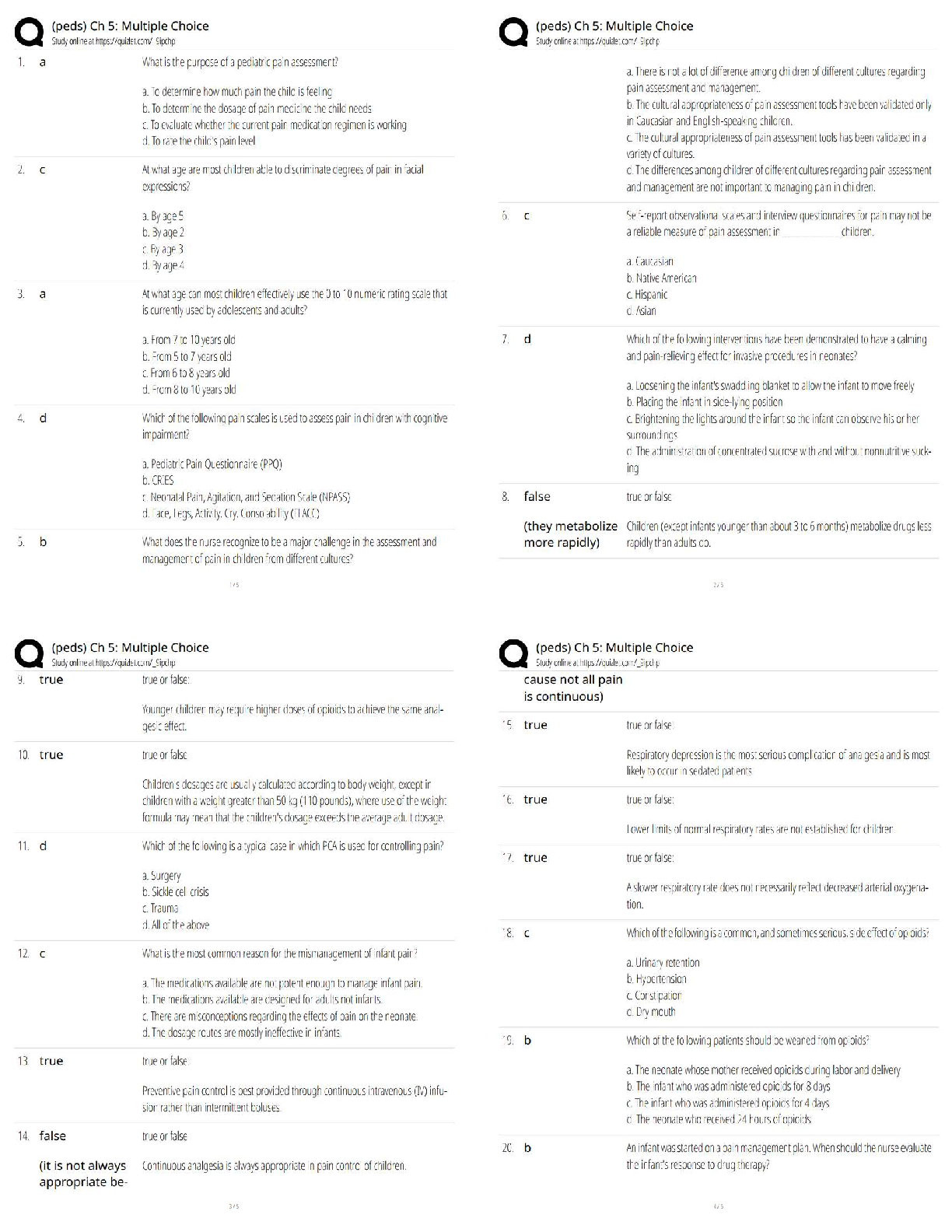
SPēD SFPC: General Questions and Answers Graded A Principle incident/events required to be reported to DoD counterintelligence (CI) organizations ✔✔espionage, sabotage, terrorism, cyber Indic ... ators of insider threats ✔✔1. Failure to report overseas travel or contact with foreign nationals 2. Seeking to gain higher clearance or expand access outside the job scope 3. Engaging in classified conversations without a need to know 4. Working hours inconsistent with job assignment or insistence on working in private 5. Exploitable behavior traits 6. Repeated security violations 7. Attempting to enter areas not granted access to 8. Unexplainable affluence/living above one's means 9. Anomalies (adversary taking actions which indicate they are knowledgeable to information) 10. Illegal downloads of information/files Elements that should be considered in identifying Critical Program Information ✔✔Elements which if compromised could: 1. cause significant degradation in mission effectiveness 2. shorten the expected combat-effective life of the system 3. reduce technological advantage 4. significantly alter program direction or 5. enable an adversary to defeat, counter, copy, or reverseengineer the technology or capability Asset, threat, vulnerability, risk, countermeasures ✔✔Elements that a security professional should consider when assessing and managing risks to DoD assets The three categories of Special Access Programs ✔✔acquisition, intelligence, and operations and support Three different types of threats to classified information ✔✔Insider Threat, Foreign Intelligence Entities (FIE) and Cybersecurity Threat The concept of an insider threat ✔✔An employee who may represent a threat to national security. These threats encompass potential espionage, violent acts against the Government or the nation, and unauthorized disclosure of classified information, including the vast amounts of classified data available on interconnected United States Government computer networks and systems. The purpose of the Foreign Visitor Program ✔✔To track and approve access by a foreign entity to information that is classified; and to approve access by a foreign entity to information that is unclassified, related to a U.S. Government contract, or plant visits covered by ITAR. Special Access Program ✔✔A program established for a specific class of classified information that imposes safeguarding and access requirements that exceed those normally required for information at the same classification level. Enhanced security requirements for protecting Special Access Program (SAP) information ✔✔1. Within Personnel Security: • Access Rosters • Billet Structures (if required) • Indoctrination Agreement • Clearance based on an appropriate investigation completed within the last 5 years • Individual must materially contribute to the program in addition to having the need to know • All individuals with access to SAP are subject to a random counterintelligence scope polygraph examination • Polygraph examination, if approved by the DepSecDef, may be used as a mandatory access determination • Tier review process • Personnel must have a Secret or Top Secret clearance • SF-86 must be current within one year; • Limited Access • Waivers required for foreign cohabitants, spouses, and immediate family members. 2. Within Industrial Security: The SecDef or DepSecDef can approve a carve-out provision to relieve Defense Security Service of industrial security oversight responsibilities. 3. Within Physical Security: • Access Control • Maintain a SAP Facility • Access Roster • All SAPs must have an unclassified nickname/ Codeword (optional). 4. Within Information Security: • The use of HVSACO; • Transmission requirements (order of precedence). True ✔✔True or False: Special access requirements are designed to provide an additional layer of security to some of our nation's most valuable assets. False. Threats and vulnerabilities are related but distinct. Threats to national security exploit vulnerabilities. ✔✔True or False: There is no difference between a threat and a vulnerability. What SAPs aim to achieve ✔✔1. Protect technological breakthroughs 2. Cover exploitation of adversary vulnerabilities 3. Protect sensitive operational plans 4. Reduce intelligence on U.S. capabilities Protection Level ✔✔This communicates how the SAP is acknowledged and protected. Acknowledged ✔✔This protection level describes a SAP whose existence may be openly recognized. Its purpose may be identified. However, the details of the program (including its technologies, materials, and techniques) are classified as dictated by their vulnerability to exploitation and the risk of compromise. The funding is generally unclassified. Unacknowledged ✔✔This protection level describes a SAP whose existence and purpose are protected. The details, technologies, materials, and techniques are classified as dictated by their vulnerability to exploitation and the risk of compromise. The program funding is often classified, unacknowledged, or not directly linked to the program. SAP Lifecycle ✔✔1. Establishment (is extra protection warranted?) 2. Management and Administration (continued need? processed followed?) 3. Apportionment (proper measures in place? approval received) 4. Disestablishment (program no longer needed?) Component-level SAP Central Offices ✔✔Exist for each military component, the Joint Chiefs of Staff, Defense Advanced Research Projects Agency (DARPA), and Missile Defense Agency (MDA) Special Access Program Oversight Committee (SAPOC) ✔✔The final SAP approving body chaired by the Deputy Secretary of Defense Senior Review Group (SRG) ✔✔This group ensures there are no duplicative efforts across SAPs DoD Special Access Central Office (SAPCO) ✔✔DoD SAP legislative liaison that notifies Congress of SAP approval Authorization, Appropriations, and Intelligence Congressional ✔✔Congressional committees granted SAP access OSD-level SAP Central Offices ✔✔Exercise oversight authority for the specific SAP category under their purview. PIE-FAO ✔✔People, information, equipment, facilities, activities, and operations Antiterrorism Officer ✔✔This person is responsible for the installation's antiterrorism program CI Support ✔✔Responsible for providing valuable information on the capabilities, intentions, and threats of adversaries OPSEC Officer ✔✔This person analyzes threats to assets and their vulnerabilities [Show More]
Last updated: 2 years ago
Preview 1 out of 8 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Also available in bundle (1)
Click Below to Access Bundle(s)

SPēD SFPC BUNDLED EXAMS QUESTIONS AND ANSWERS WITH VERIFIED SOLUTIONS
SPēD SFPC BUNDLED EXAMS QUESTIONS AND ANSWERS WITH VERIFIED SOLUTIONS
By Nutmegs 2 years ago
$22
13
Reviews( 0 )
$10.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
May 25, 2023
Number of pages
8
Written in
All
Additional information
This document has been written for:
Uploaded
May 25, 2023
Downloads
0
Views
142








.png)