GBA 327 Test 1
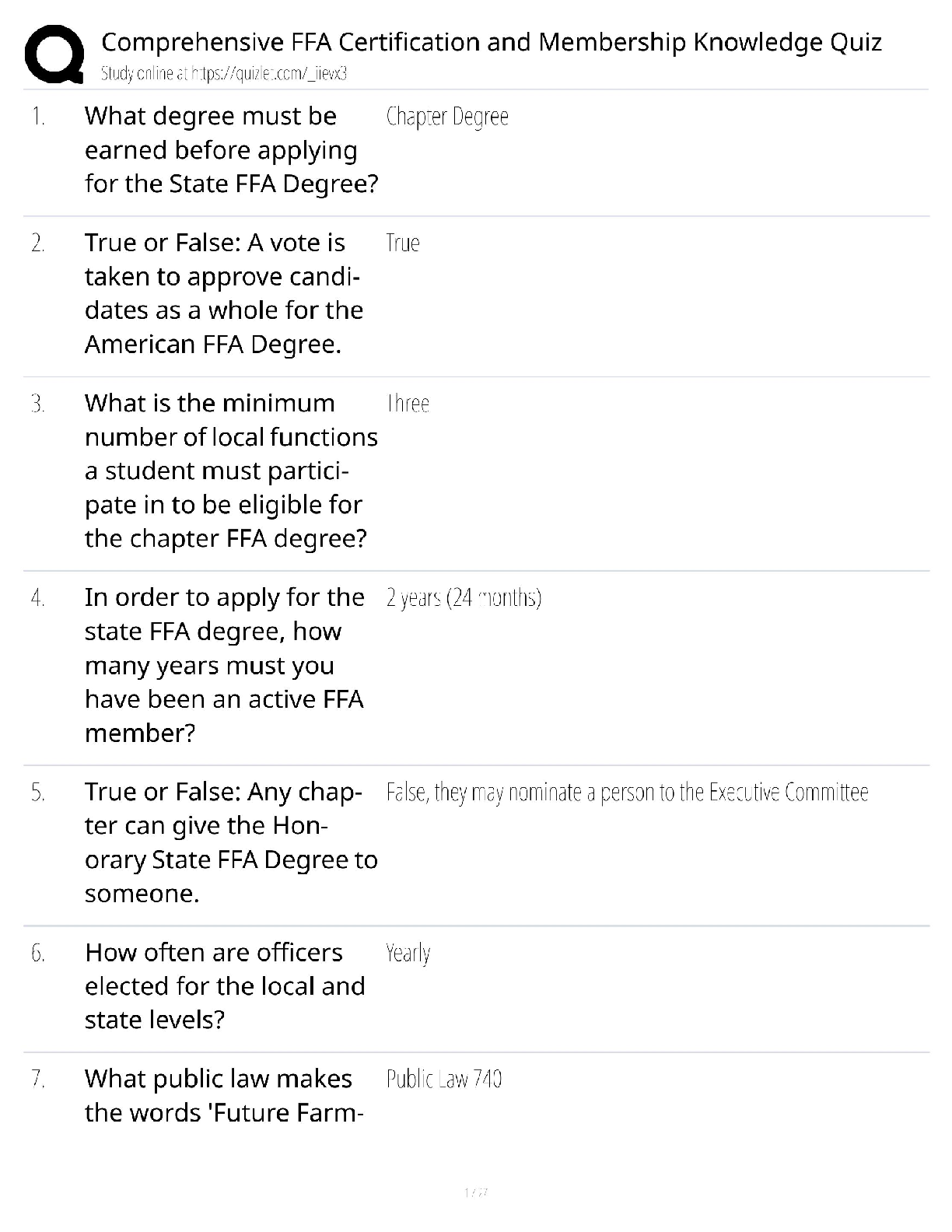
Question 1. ________ states that the number of transistors per square inch on an integrated chip doubles every 18 months.
Nielsen's Law
Faraday's Law
Moore's Law
Newton's
...
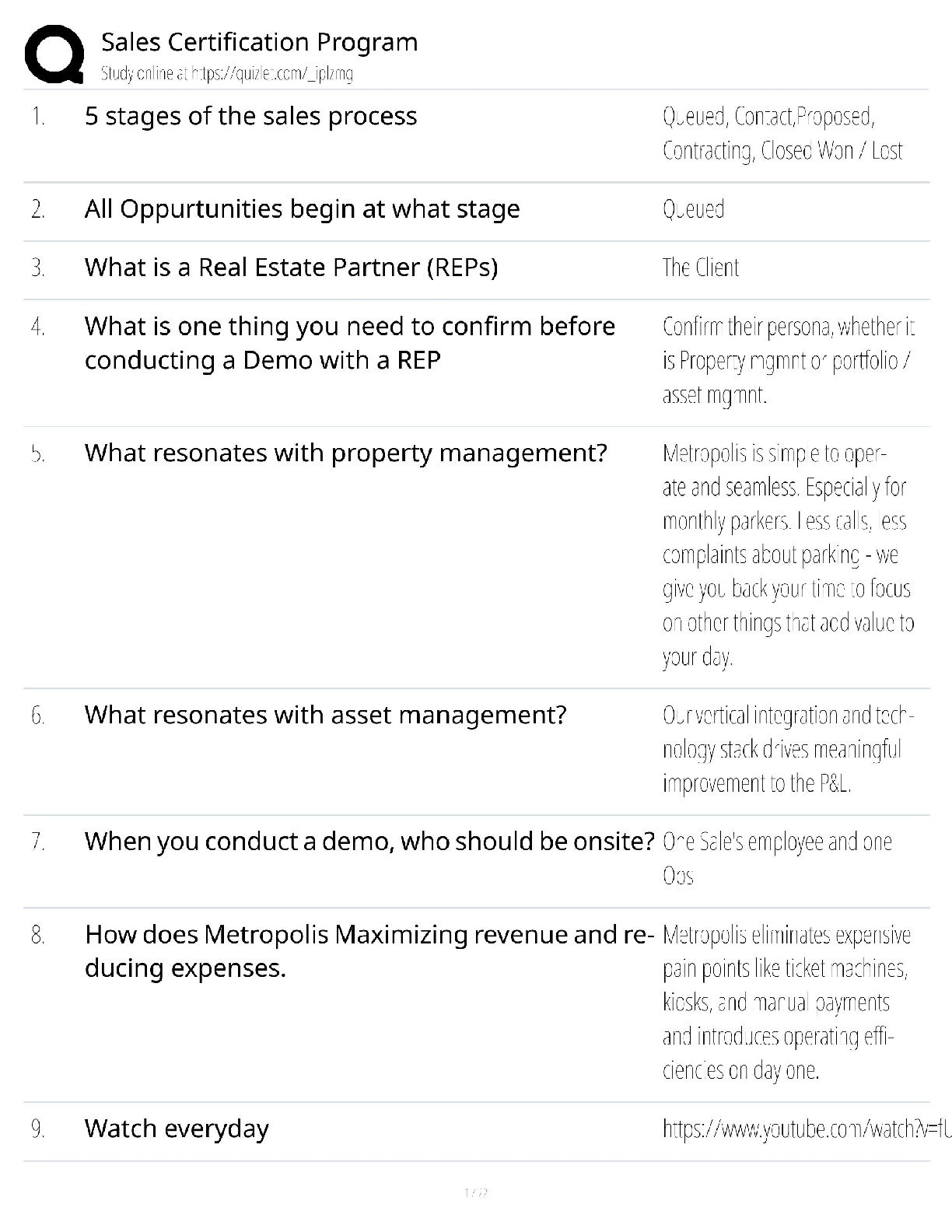
GBA 327 Test 1
Question 1. ________ states that the number of transistors per square inch on an integrated chip doubles every 18 months.
Nielsen's Law
Faraday's Law
Moore's Law
Newton's Law
Question 2. Which of the following types of skills is most likely to be outsourced to the lowest bidder?
ability to experiment
Accounting skills
ability to collaborate
abstract reasoning skills
Question 3. Carlos is a business student doing an internship at Bruno and Venus, a firm specializing in exports of sophisticated equipment to other countries. He finds that he is unable to create a representative chart depicting the relation between processes such as procurement, shipping, and billing. This indicates that he lacks ________ skills.
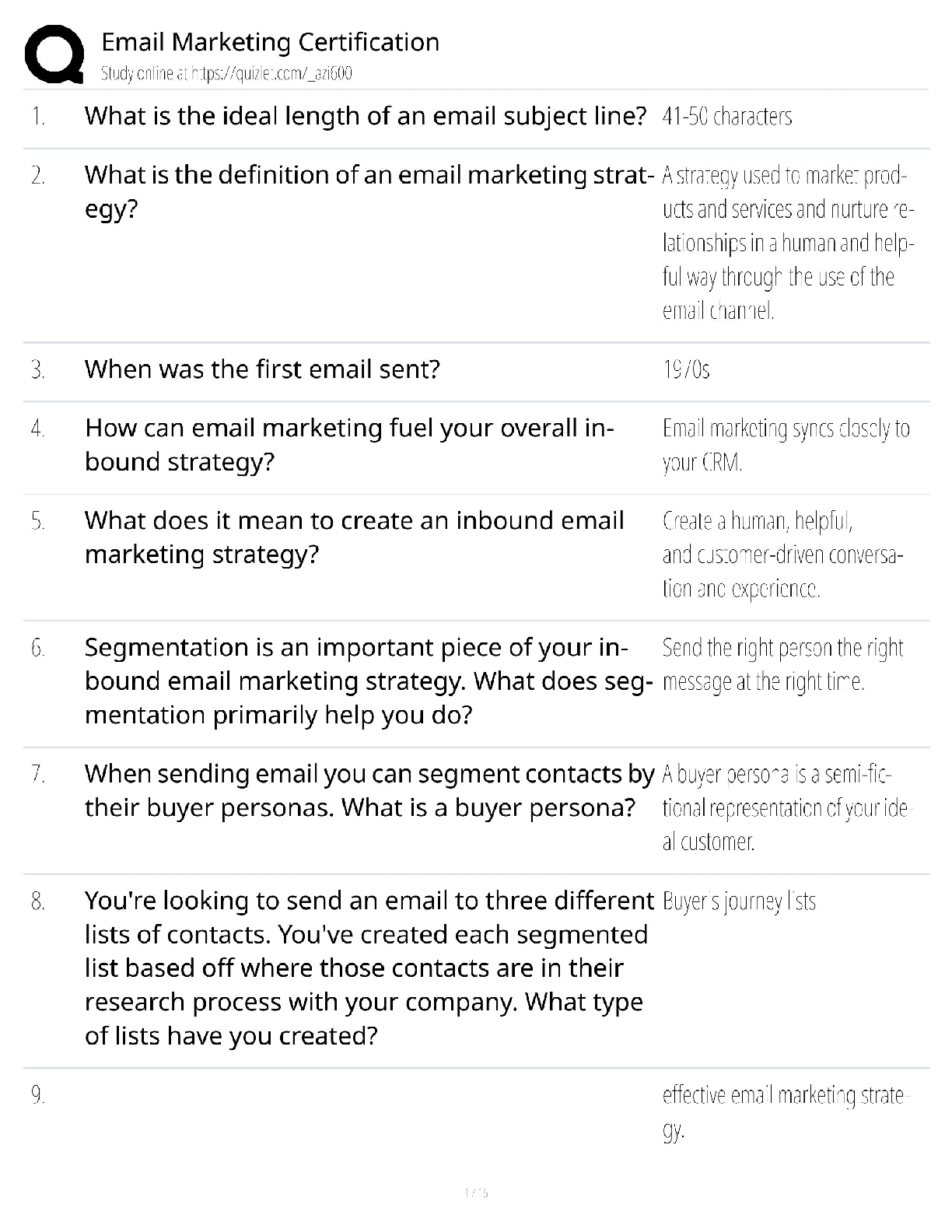
abstract reasoning
collaborative
experimental
systems thinking
Question 4. Meredith constantly analyzes her work in terms of her individual contribution that she makes to the overall output of the organization. This shows her ________ skills.
collaboration
experimentation
systems thinking
problem-solving
Question 5. Erin is a manager for a reputed software firm. She typically monitors and evaluates the existing working procedures of her subordinates. She constantly changes these working procedures so that they are consistent with the company's resources. This shows her ability to ________.
participate in systems thinking
experiment
make abstractions
collaborate
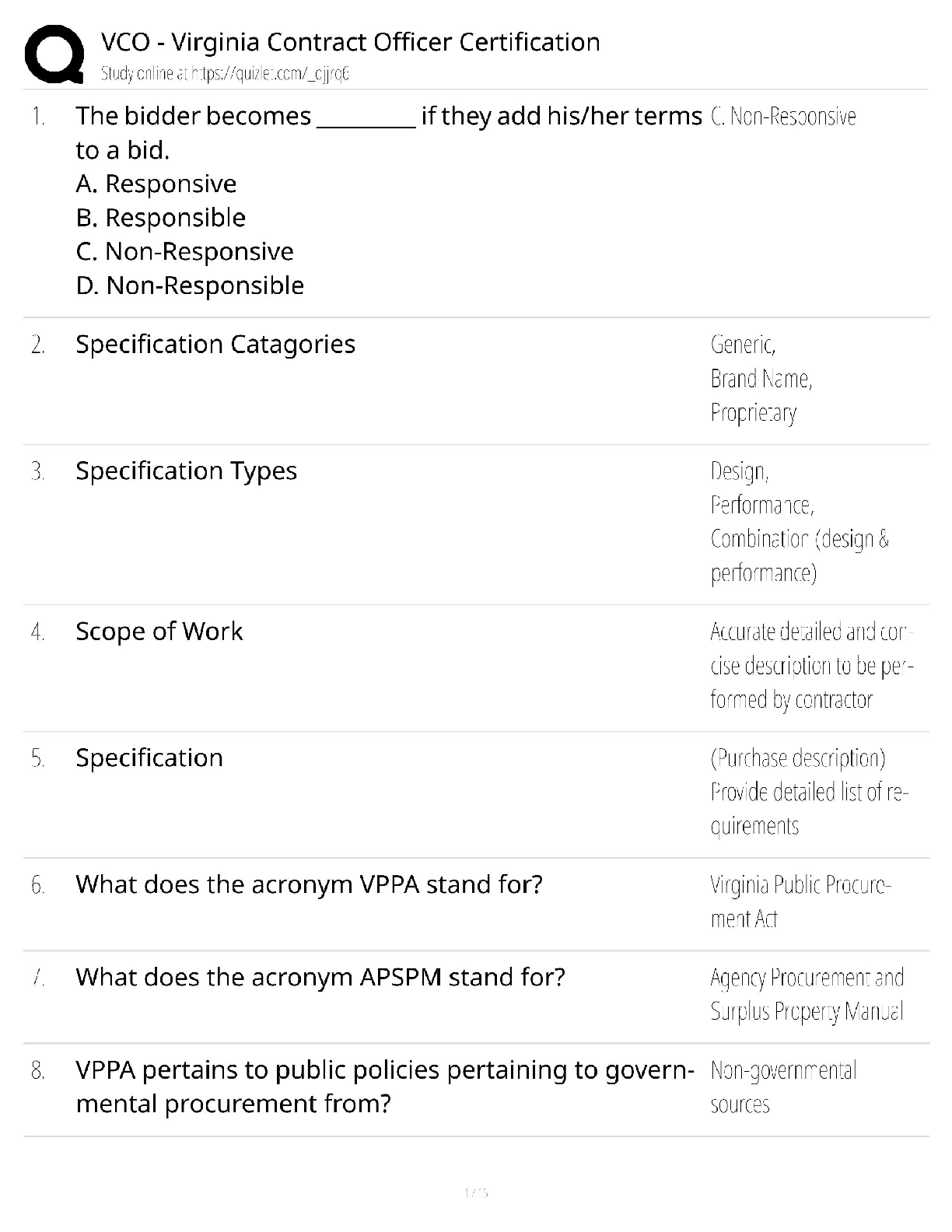
Question 6. The storage disk in a computer is an example of the ________ component of information systems.
hardware
software
database
virtual
Question 7. A customer relationship management (CRM) system contains the names and phone numbers of customers. Such details stored in a CRM system are part of the ________ component.
hardware
data
procedure
people
Question 8. Which of the following is a low-tech information system
an inventory tracking system that produces reports every 24 hours
a file of email addresses stored in an email program
a customer support system that keeps track of product issues
a decision support system that analyzes multiple variables
Question 9. Drudgen Fitness Inc. is a fitness equipment provider that markets its products through a chain of retail outlets in four states. As part of its expansion strategy, the company decides to open outlets in four more states and decides to revise its existing business processes. According to the five-component model of information systems, which of the following processes will be the least disruptive to the organization?
collecting demographic data from the new markets
developing new CRM software for the existing and new outlets
relocating existing employees and hiring new employees
buying and installing new computers in the new outlets
Question 10. It is generally more difficult to make changes to the ________ of an information system than to the database itself.
software
hardware
programs
procedures
Question 11. Which of the following statements is true of information technology (IT)?
Information technology (IT) refers to the products, methods, inventions, and standards that are used for the purpose of producing information.
Information technology is an umbrella term that covers information systems and the products, methods, inventions, and standards used to produce information.
Information technology and information systems are synonymous with each other and can be used interchangeably.
Information technology is an assembly of hardware, software, data, procedures, and people that produces information.
Question 12. Caroline asks her secretary to send information on the meetings that she needs to attend next month. Her secretary, Joanne, provides her with the details immediately, but leaves out certain additional details that are irrelevant to Caroline's requirements. Which of the following statements is true about this scenario?
The information that Joanne provided was partly good as it was timely but insufficient.
Joanne provided adequate and timely information, but the information was of no value to Caroline.
The information that Joanne gave was accurate and sufficient for Caroline's purpose.
The information that Caroline obtained through Joanne was not timely or worth its cost.
Question 13. Which of the following factors determines the structure, features, and functions of an information system used in a company?
the competitive strategy
the value of its brands
the size of the company
the technology used by competitors
Question 14. According to Porter's five forces model, in which of the following situations would a supplier have the highest bargaining power?
a Houston-based vendor is the only supplier of a patented material for many smartphone manufacturers
a fashion brand's outlet catering to a niche market
a restaurant that serves only army veterans
a large retailer buying finished goods from many small suppliers
Question 15. Bargaining power of customers is likely to be the highest for markets involving ________.
limited edition apparel
industrial products
patented drugs
vintage cars
Question 16. Focused differentiation occurs when ________.
a better product is provided within an industry segment
there is limited competition in an industry
the customers are highly price-sensitive
product quality improves across an entire industry
Question 17. Which of the following value chain activities involves collecting, storing, and physically distributing the product to buyers?
inbound logistics
operations
customer service
outbound logistics
Question 18. Which of the following statements is consistent with the central idea of business process design?
Technology should be used to supplement the existing value chain.
Business processes should not focus on the core competencies of organizations.
Organizations should create new business processes rather than improve existing systems.
Technology should be used to modify and improve standard business processes.
Question 19. A database is an example of a ________.
repository
procedure
linkage
value chain
Question 20. Which of the following principles of competitive advantage is related to process implementations?
creating new products
enhancing services
locking in suppliers
differentiating products
Question 21. FunText is a company that owns an app used for text messaging. It recently offered a membership extension of six months without any additional charges to its existing customers who had registered for a three-year membership. By doing this, which competitive strategy did FunText implement?
creation of a new service
product differentiation
locking in customers
locking in suppliers
Question 22. A large software manufacturer attempts to lock in customers by making it difficult for customers to change to another product. The strategy used by the company is referred to as ________.
switching costs strategy
low cost operation strategy
standardization strategy
consumerist strategy
Question 23. Reduction in production cost results in ________.
decreased profitability
lower shareholder value
increased profitability
increased competition
Question 24. Which of the following principles of competitive advantage is associated with product implementations?
locking in customers
enhancing services
locking in suppliers
establishing alliances
Question 25. Which of the following devices is an example of a storage hardware device?
universal serial bus
central processing unit
optical disk
random access memory
Question 26. Bits are grouped into 8-bit chunks called ________.
switches
strings
bytes
nibble
Question 27. Which of the following is an example of an application program?
Microsoft Word
Unix
Linux
Windows
Question 28. Linux is an example of a(n) ________.
open source operating system software
mobile operating system
user community
workstation client
Question 29. Which of the following refers to server virtualization?
a personal computer, such as a desktop or portable computer, that hosts several different operating systems
a server computer that hosts one, or more, other server computers
a storage area that loses its contents when the power is off
a server that hosts many versions of desktop operating systems
Question 30. Programs that perform business functions, such as general ledger and accounting, are examples of ________.
application software
system software
firmware
operating systems
Question 31. DenTimes, a software package installed in hospitals, is used to schedule appointments and bill patients. This is an example of ________.
horizontal-market application software
vertical-market application software
firmware
adware
Question 32. Source code is computer code ________.
that is written by humans
that is not understandable by humans
that is represented as bits and bytes
that cannot be modified
Question 33. Which of the following statements is true of closed source projects?
Only users and developers are allowed to alter the source code in closed source projects.
Anyone can obtain the source code for a closed source project.
Only trusted programmers are allowed to make changes to a closed source project.
Programmers can alter the closed source code based on their interests and goals.
Question 34. Which of the following statements is true of native applications?
They only run on the operating system for which they are programmed
The cost of native applications is low.
They can be developed by less skilled, lesser-paid employees.
The limits on these applications are usually technological, not budget.
Question 35. Thin-client applications are typically limited by the capabilities of the ________.
programming language
browser
hardware
operating system
Question 36. ________ refers to data delivered to the user at the precise moment it is needed.
Asynchronous data
Just-in-time data
Source code
Payload
Question 37. ________ is used to install and update software, back up and restore mobile devices, wipe employer software and data from devices, report usage, and provide other mobile device management data.
MDM software
A key logger
BYOD manager
A UX application
Question 38. A primary key used in a database is a ________.
group of rows that are formed to identify a unique table or file
column or group of columns that identifies a unique row in a table
character or byte that represents fields or columns
group of tables or files formed to identify a unique field or row
Question 39. Which of the following is true of MySQL?
It is offered by Oracle.
It is license-free for most applications.
It is a closed-source database product.
It is yet to be widely adopted.
Question 40. Brenda, the sales manager of a firm, wants to generate a particular report containing sales analyses of the second and third quarter of the year. She should use a ________ to obtain the information that she wants from the database.
report
data model
database administrative
query
Question 41. Which of the following is true of traditional database application programs?
Application forms, reports, and queries are displayed and processed using a browser.
All of the application logic is contained in a program on the database server.
They are written in object-oriented languages such as C++ and VisualBasic.
They are thin-client applications that need not be pre-installed on the users' computers.
Question 42. Which of the following refers to the problem that exists in database applications when two users modify the same data item, but only one of those changes is recorded?
lost-update problem
crow's-foot paradigm
bullwhip effect
update query problem
Question 43. Brad, a project manager, wants to build a database to integrate information about employees and tasks that they handle. Brad wants to track information such as task name, percentage completed, and employee name. These aspects that Brad wants to track are called ________.
identifiers
records
primary keys
entities
Question 44. Which of the following is true of N:M relationships?
They are the same as N:N relationships.
They represent minimum cardinalities in a relationship.
They are also called one-to-many relationships
They can have more than one entity on each side of the relationship.
Question 45. ________ in an E-R diagram refer to the least number of entities required in a relationship.
One-to-one relationships
Primary keys
Foreign keys
Minimum cardinalities
Question 46. When using the relational model to represent two tables, one must ________.
add a foreign key to one of the tables
have more than two identifiers in the model
establish only N:M relationships between the tables
use metadata instead of foreign keys
Question 47. Which of the following is true about the database development process?
The easiest time to change the database structure is during the data modeling stage.
Changing a relationship from 1:N to N:M in an existing database is simply a matter of changing notations.
User review of the data model is avoided as it is not helpful in data modeling.
A database is a model of how the developers view their business world.
Question 48. ________ are the final judges as to what data the database should contain and how the records in that database should be related to one another.
Administrators
Developers
Users
Designers
Question 49. Which of the following is a nonrelational data store developed by Google?
Cassandra
Dynamo
SharePoint
Bigtable
Question 50. ________ is the term used to describe data collections that are characterized by huge volume, rapid velocity, and great variety.
BigData
NoSQL
Dynamo
Hadoop
[Show More]



















.png)