Data Systems > Quiz > SEC-360 Week 1 Quiz (Q & A) - 100% Correct Answers (All)
SEC-360 Week 1 Quiz (Q & A) - 100% Correct Answers
Document Content and Description Below
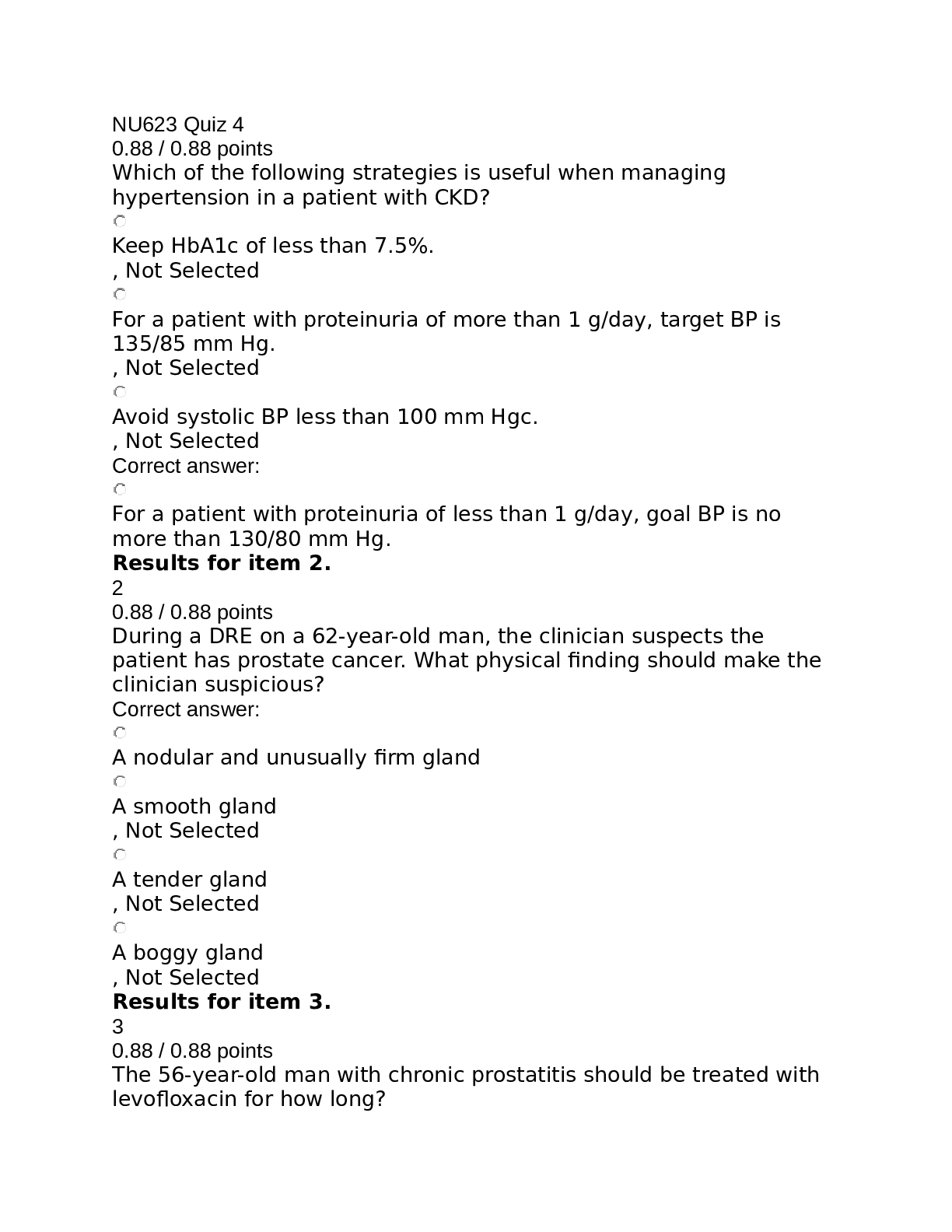
SEC360 - Week 1: Quiz (TCO 1) Defense-in-depth is a . security requirement security model security strategy security policy security control Defense-in-depth is a strategy (text, p. ... 23). (TCO 1) Information security is the process of protecting all of the following except . confidentiality of data data integrity availability of data data configuration information system availability Week 1 Lecture; and text, page 21 Question 3 5 / 5 pts (TCO 1) An organization’s security posture is defined and documented in _ _ that must exist before any computers are installed. standards guidelines procedures tolerance for risk All of the above Text, page 9 (TCO 1) Layered security is also referred to as _ _. computing rings defense in depth multilevel security physical security reference monitor Text, page 23 (TCO 2) The umbrella of information security includes all of the following, except _. incident response key management business readiness security testing training and awareness Text, page 9 (TCO 2) The two kinds of requirements that must be satisfied to ensure verification and validation of information security are called _ _. audit and accountability functional and assurance testing and evaluation analysis and assessment functional and performance Text, page 26 (TCO 2) What is the enemy of security? Industry Foreign nations Competitors Complexity People Text, page 30 (TCO 2) The functions of the ISC2 do NOT include which of the following? Ensure maintenance of credentials Administer examinations Refute working knowledge of information security Maintain CBK for information security Administer recertification Text, page 41 (TCO 1) Policies and procedures are often referred to as . models a necessary evil guidelines documentation Text, page 21 (TCO 2) The Application Development Security domain focuses on . sound and secure application development techniques who may access a system single sign-on technologies and their risks specific attacks and countermeasures Text, pages 46-47 [Show More]
Last updated: 2 years ago
Preview 1 out of 5 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$10.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Jul 03, 2023
Number of pages
5
Written in
All
Additional information
This document has been written for:
Uploaded
Jul 03, 2023
Downloads
0
Views
104