Data Systems > QUESTIONS & ANSWERS > SEC-360 Week 3 Quiz (Q & A) - 100% Correct Answers (All)
SEC-360 Week 3 Quiz (Q & A) - 100% Correct Answers
Document Content and Description Below
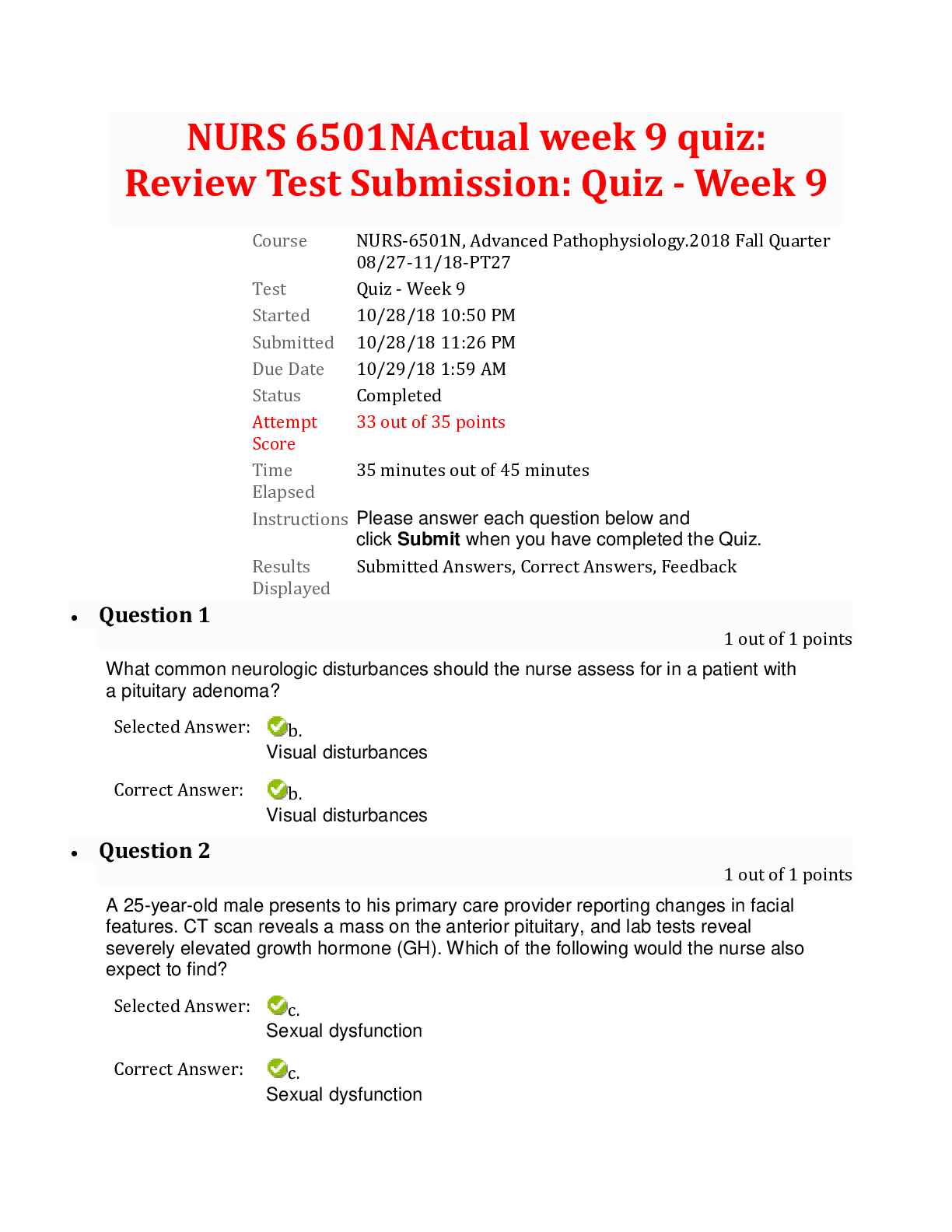
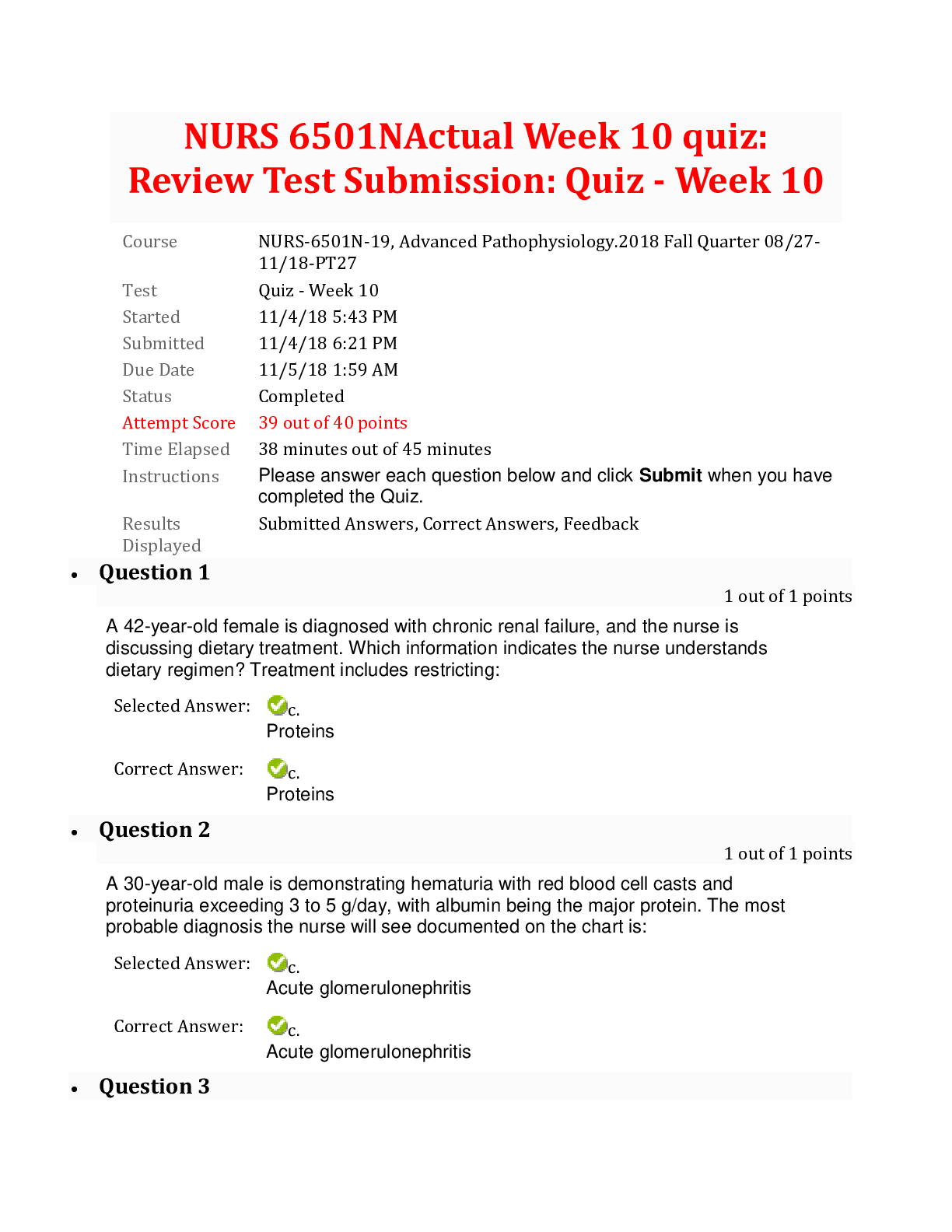
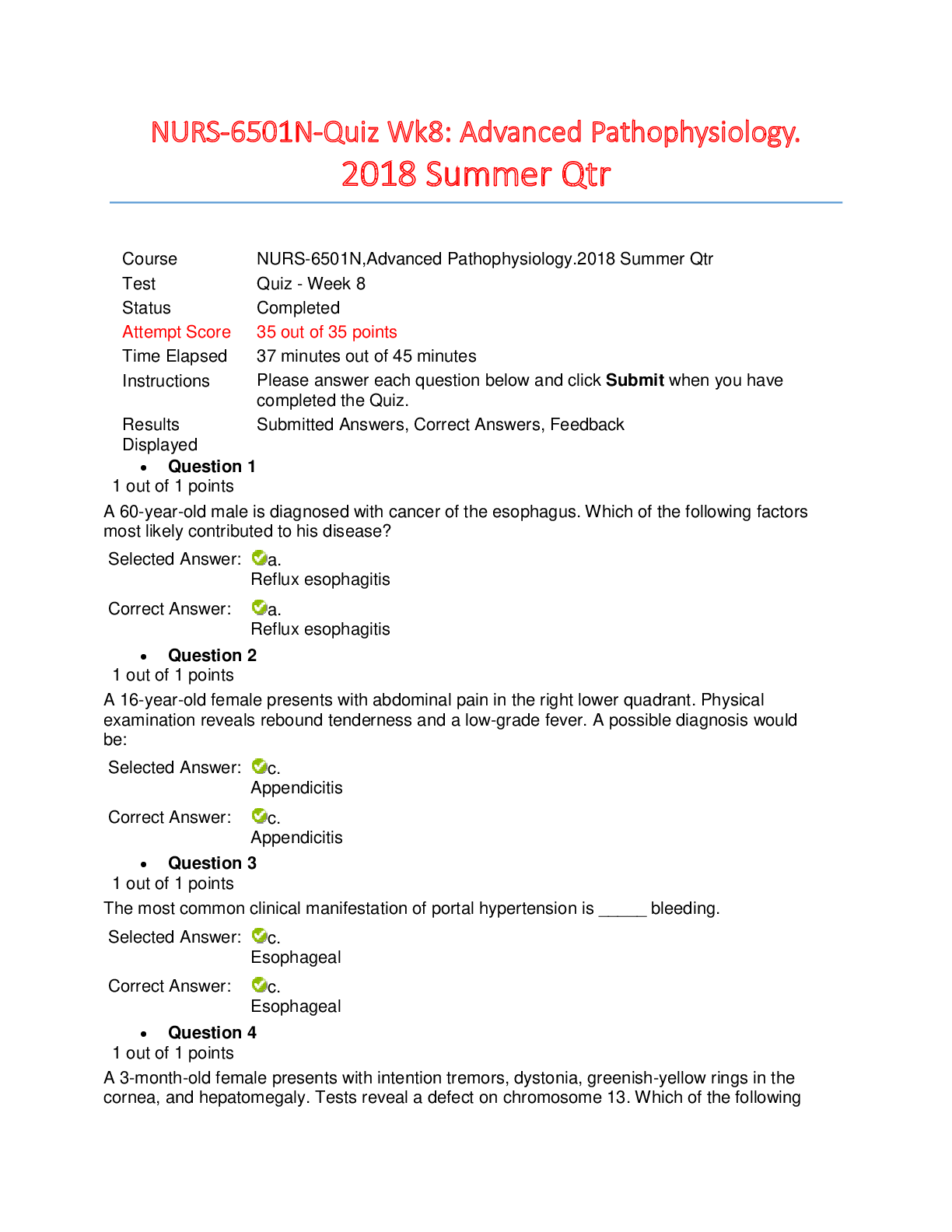
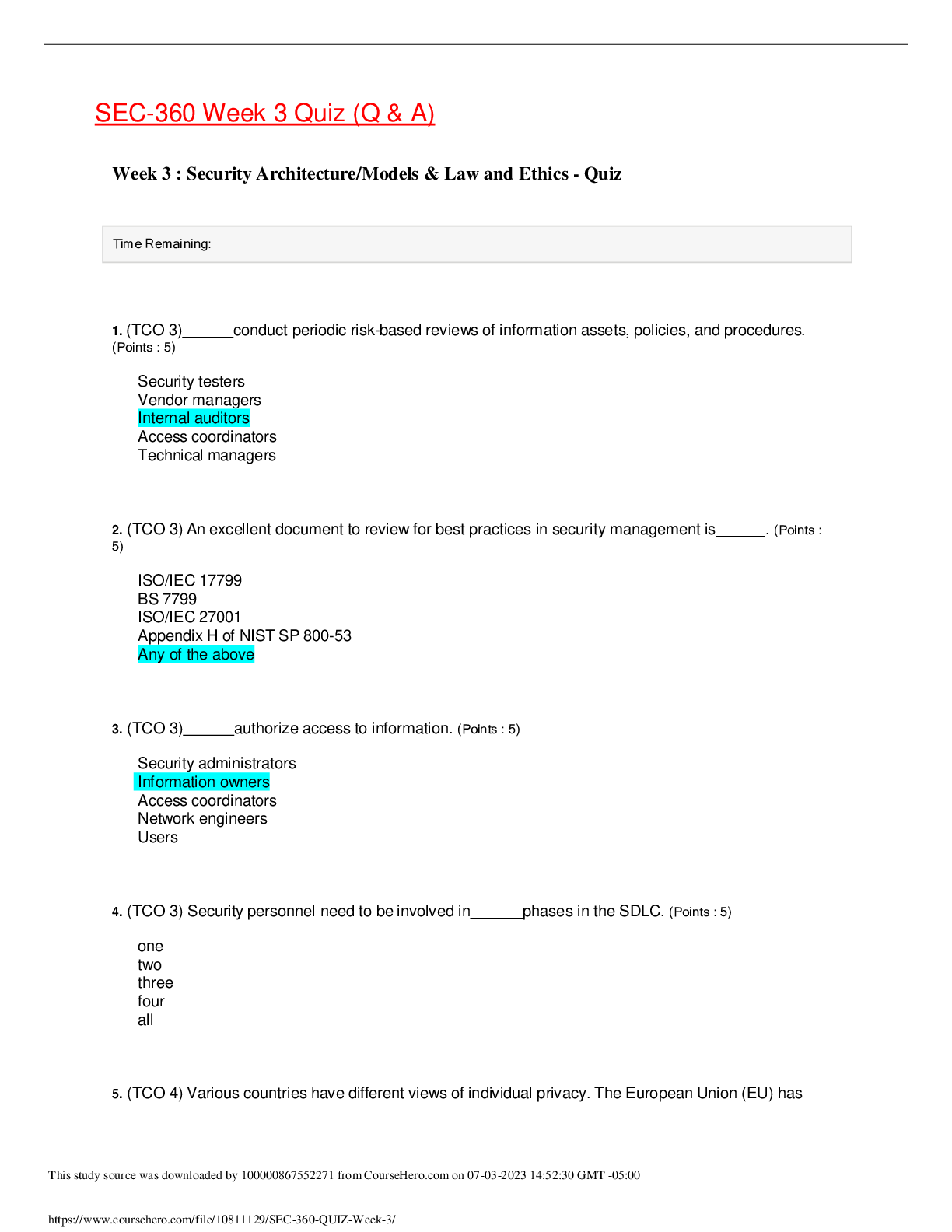
SEC-360 Week 3 Quiz (Q & A) Week 3 : Security Architecture/Models & Law and Ethics - Quiz 1. (TCO 3) conduct periodic risk-based reviews of information assets, policies, and procedures... . (Points : 5) Security testers Vendor managers Internal auditors Access coordinators Technical managers 2. (TCO 3) An excellent document to review for best practices in security management is . (Points : 5) ISO/IEC 17799 BS 7799 ISO/IEC 27001 Appendix H of NIST SP 800-53 Any of the above 3. (TCO 3) authorize access to information. (Points : 5) Security administrators Information owners Access coordinators Network engineers Users 4. (TCO 3) Security personnel need to be involved in phases in the SDLC. (Points : 5) one two three four all 5. (TCO 4) Various countries have different views of individual privacy. The European Union (EU) has very different privacy laws than the United States has. To allow U.S. companies better ease of operation in the European Union, the Department of Commerce negotiated the with the EU. (Points : 5) privacy treaty Memorandum of Agreement regarding privacy Privacy Reciprocity Act of 1993 international safe harbor principles Privacy Act of 198z3 6. (TCO 4) Which of the following "commandments" should be part of the information security professional's code of ethics? (Points : 5) I will abide by the Constitution of the United States. I will dress appropriately for the company environment. I will protect the equities of senior management. I will act honorably, honestly, justly, responsibly, and legally. 7. (TCO 5) prevents data leakage and modification of the data while it is in memory. (Points : 5) Process isolation Data hiding Layering Abstraction Information hiding 8. (TCO 5) The Common Criteria is used to evaluate . (Points : 5) the security assurance of commercial products security products the vendor's life cycle security methods the cost of security in commercial products the security features and assurance of commercial products 9. (TCO 4) The program has created the need for companies that create protective equipment to help prevent spies from detecting stray computer signals. (Points : 5) information warfare qualitative risk analysis information assurance TEMPEST None of the above 10. (TCO 5) What does a product or system have enforced over it by one or more components of the trusted computing base (TCB)? (Points : 5) Tools and methodologies Unified security policy Kernel monitoring Driver signing [Show More]
Last updated: 1 year ago
Preview 1 out of 3 pages
Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$10.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Jul 03, 2023
Number of pages
3
Written in
Additional information
This document has been written for:
Uploaded
Jul 03, 2023
Downloads
0
Views
60