IBWA CPO Study Set - Chapter 8 Already
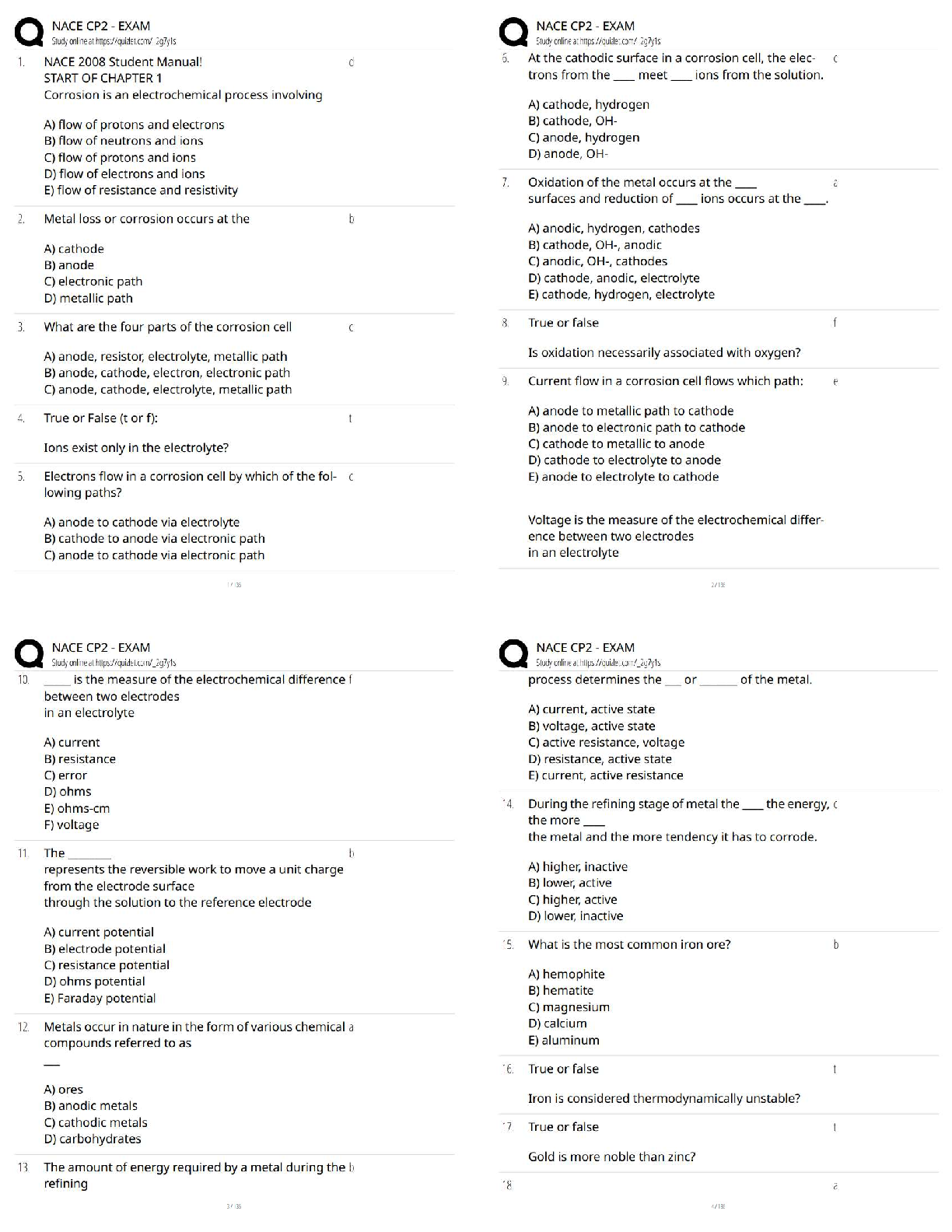
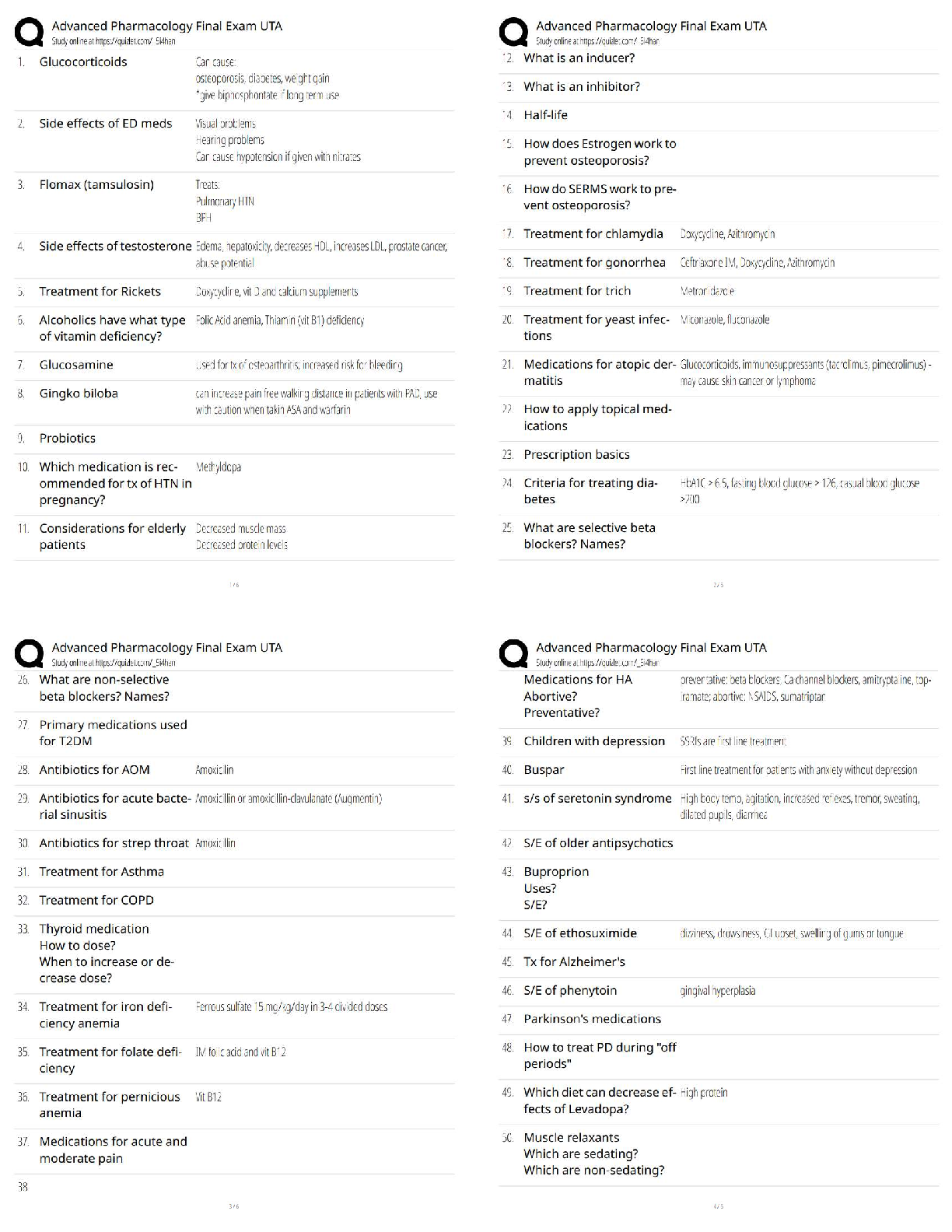
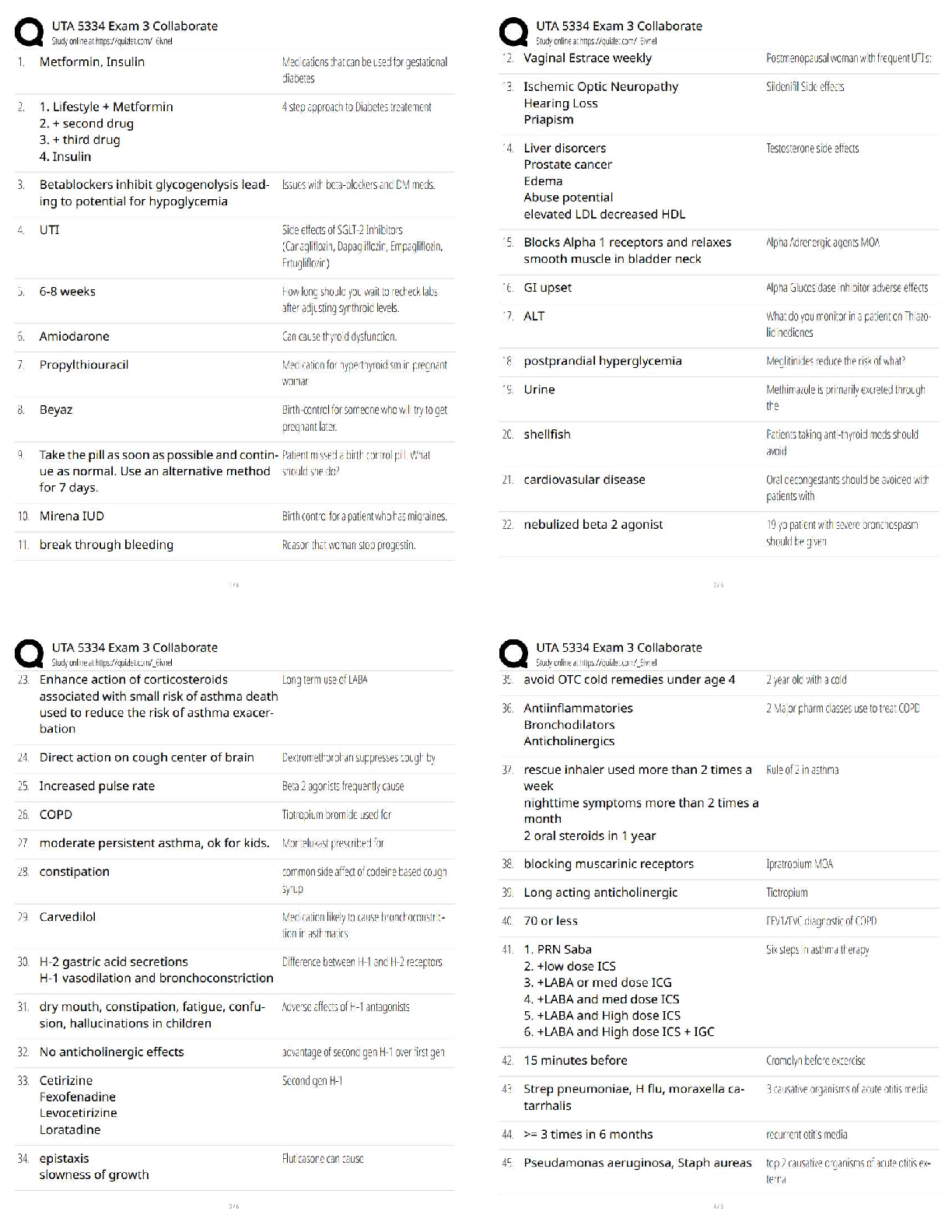
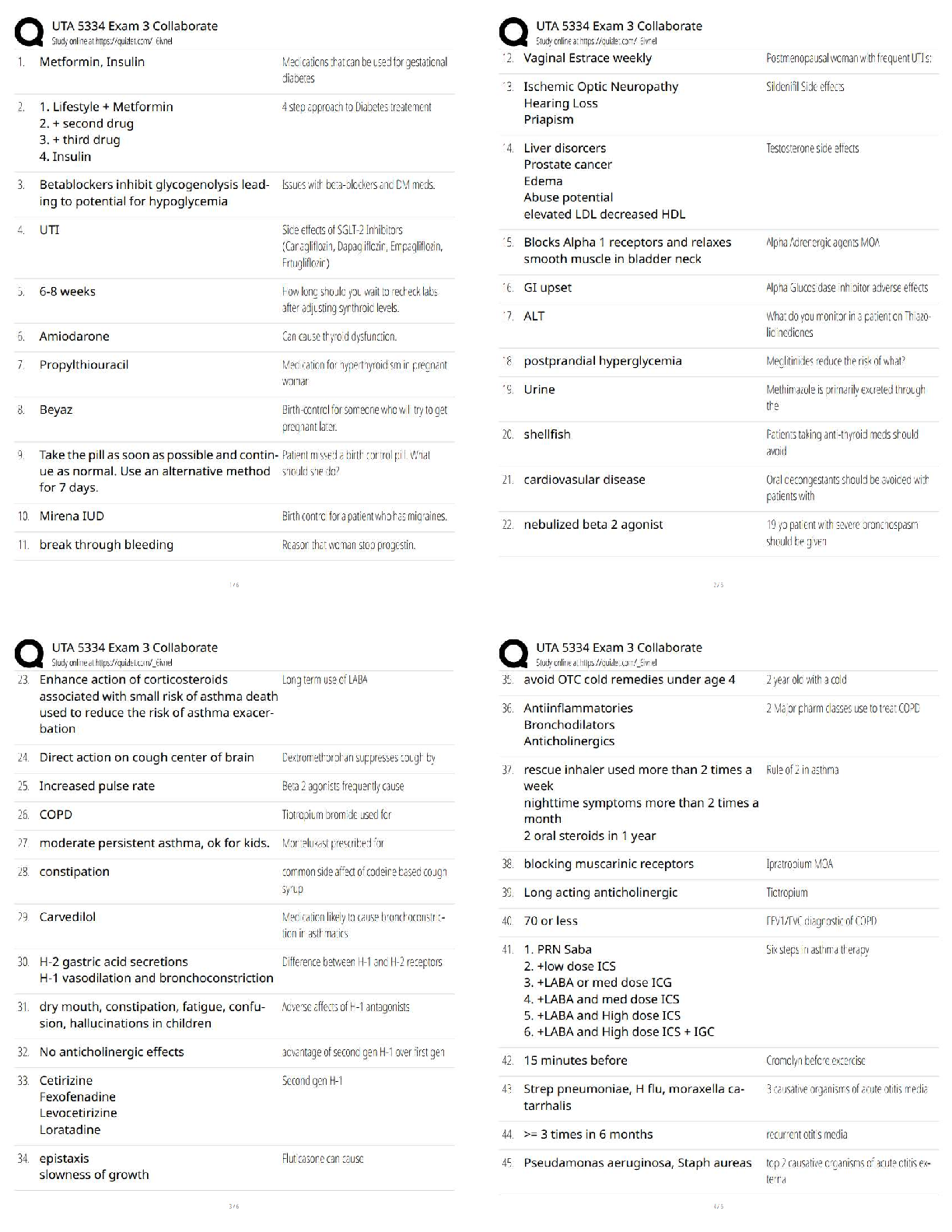
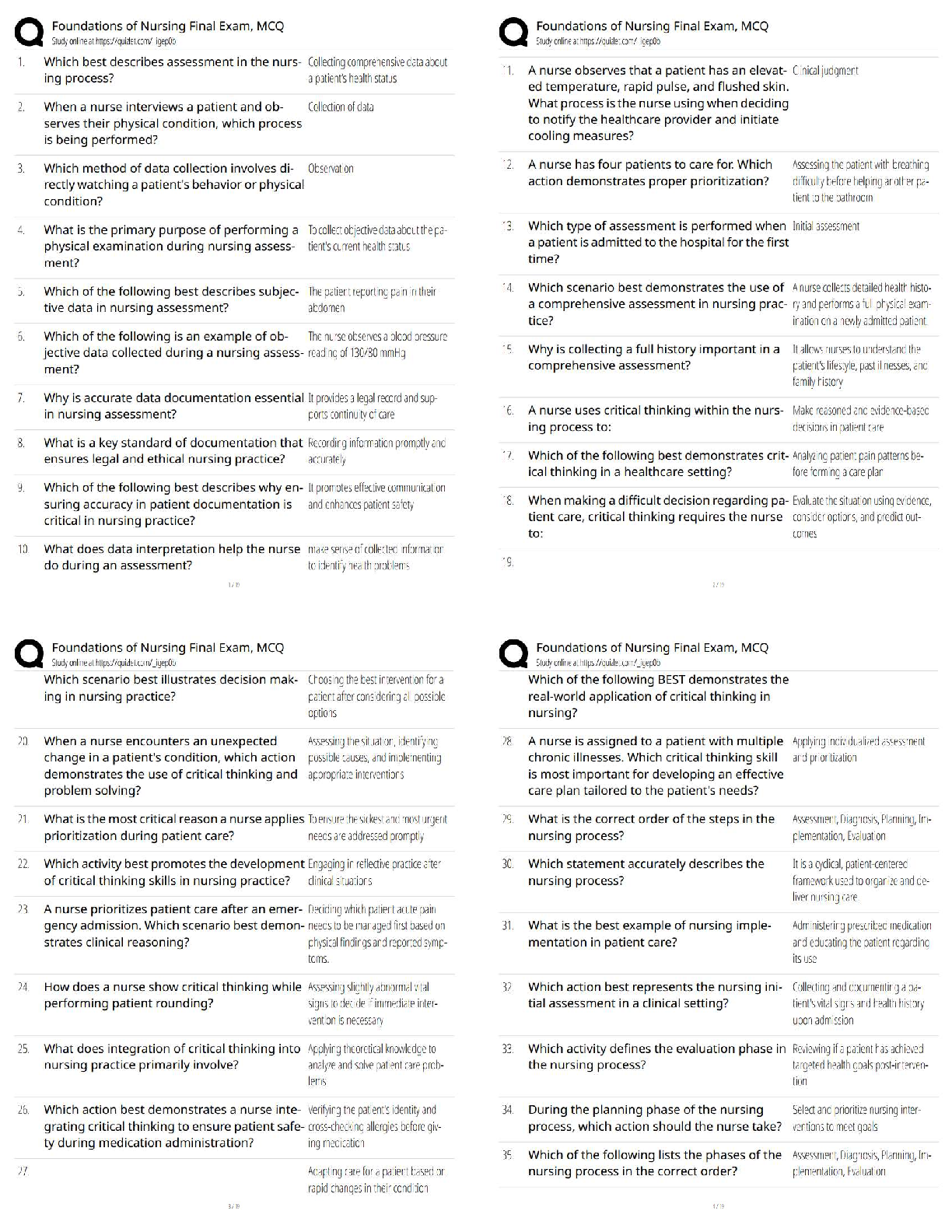
Passed
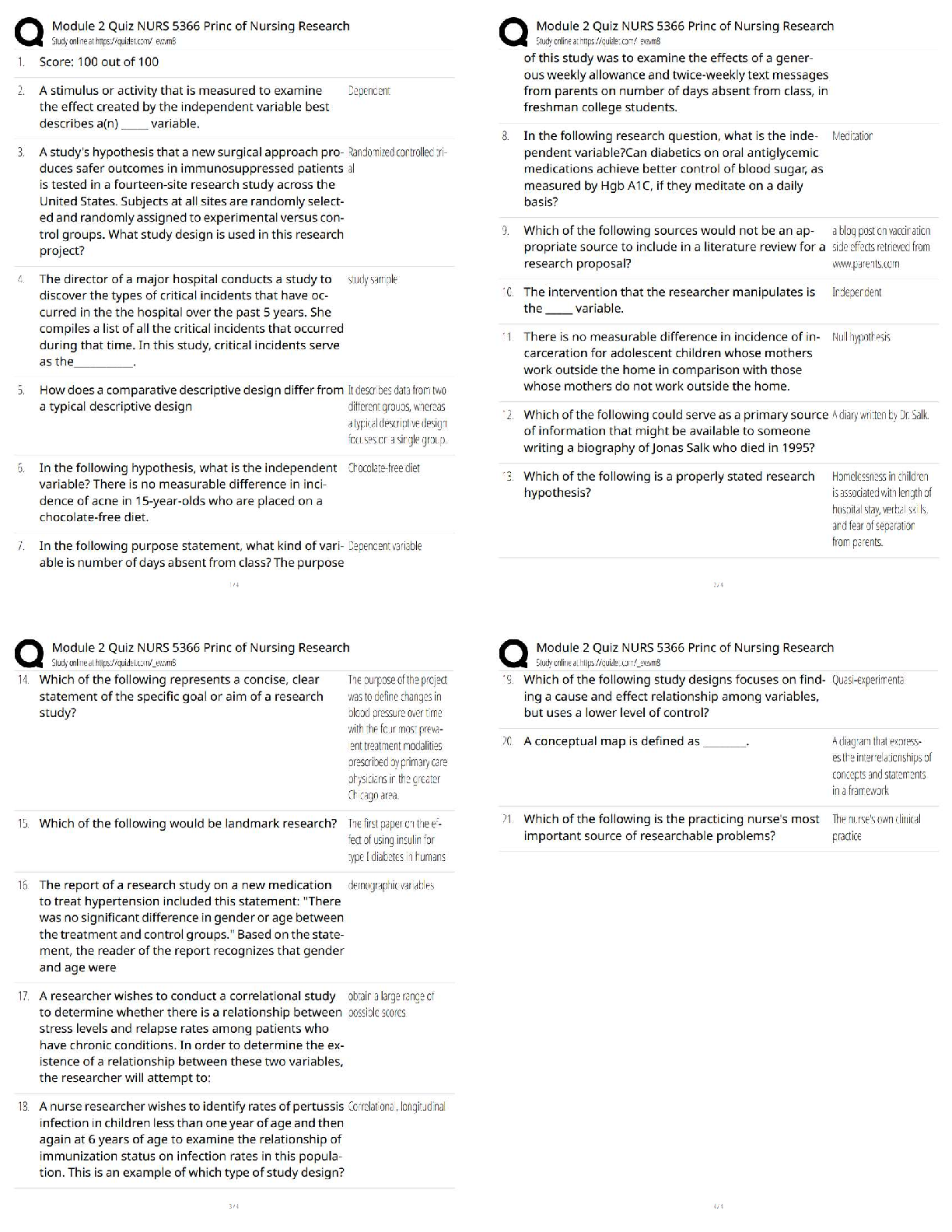
In ____________, the U.S. Congress passed the Public Health Security and Bioterrorism
Preparedness and Response Act ✔✔2002
The Public Health Security and Bioterrorism Pre
...
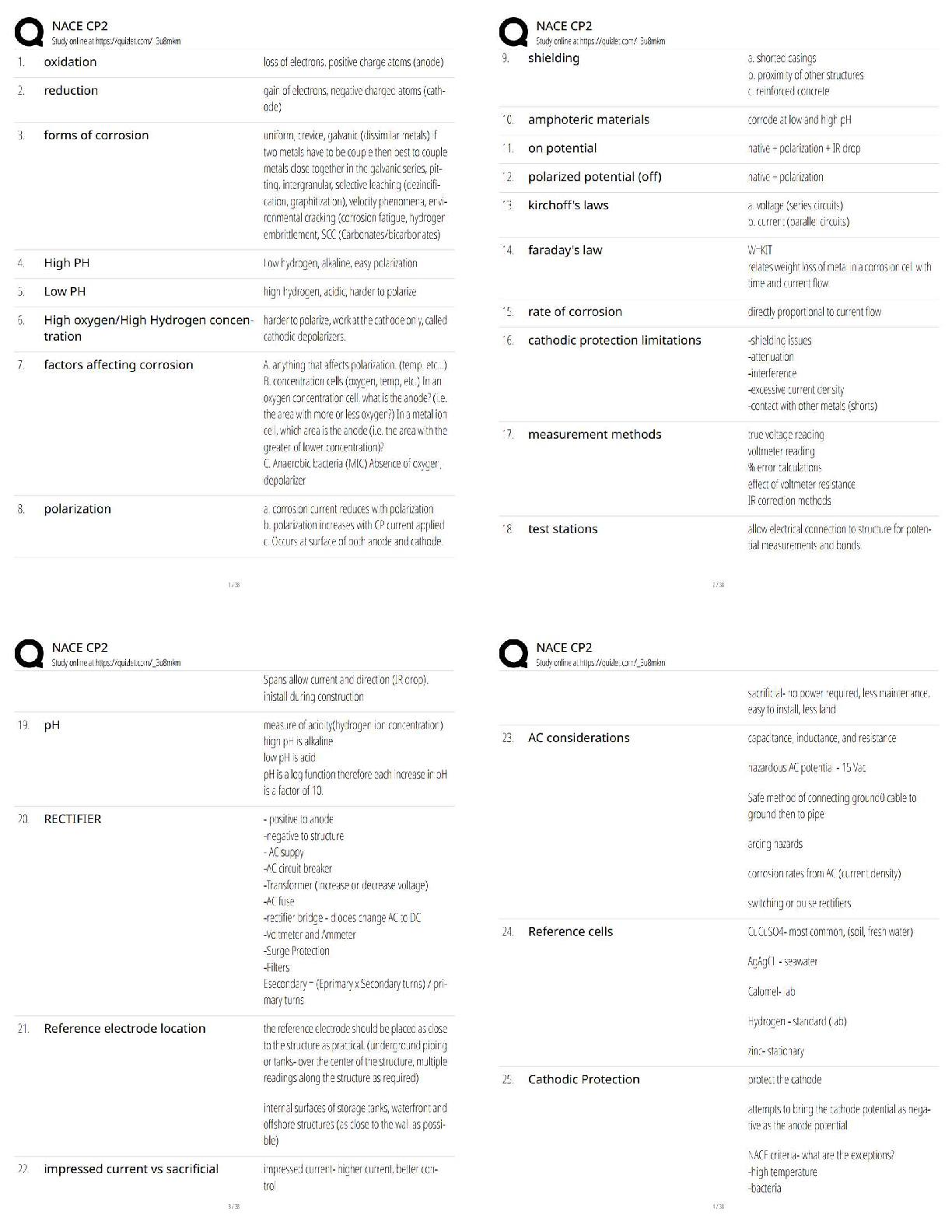
IBWA CPO Study Set - Chapter 8 Already
Passed
In ____________, the U.S. Congress passed the Public Health Security and Bioterrorism
Preparedness and Response Act ✔✔2002
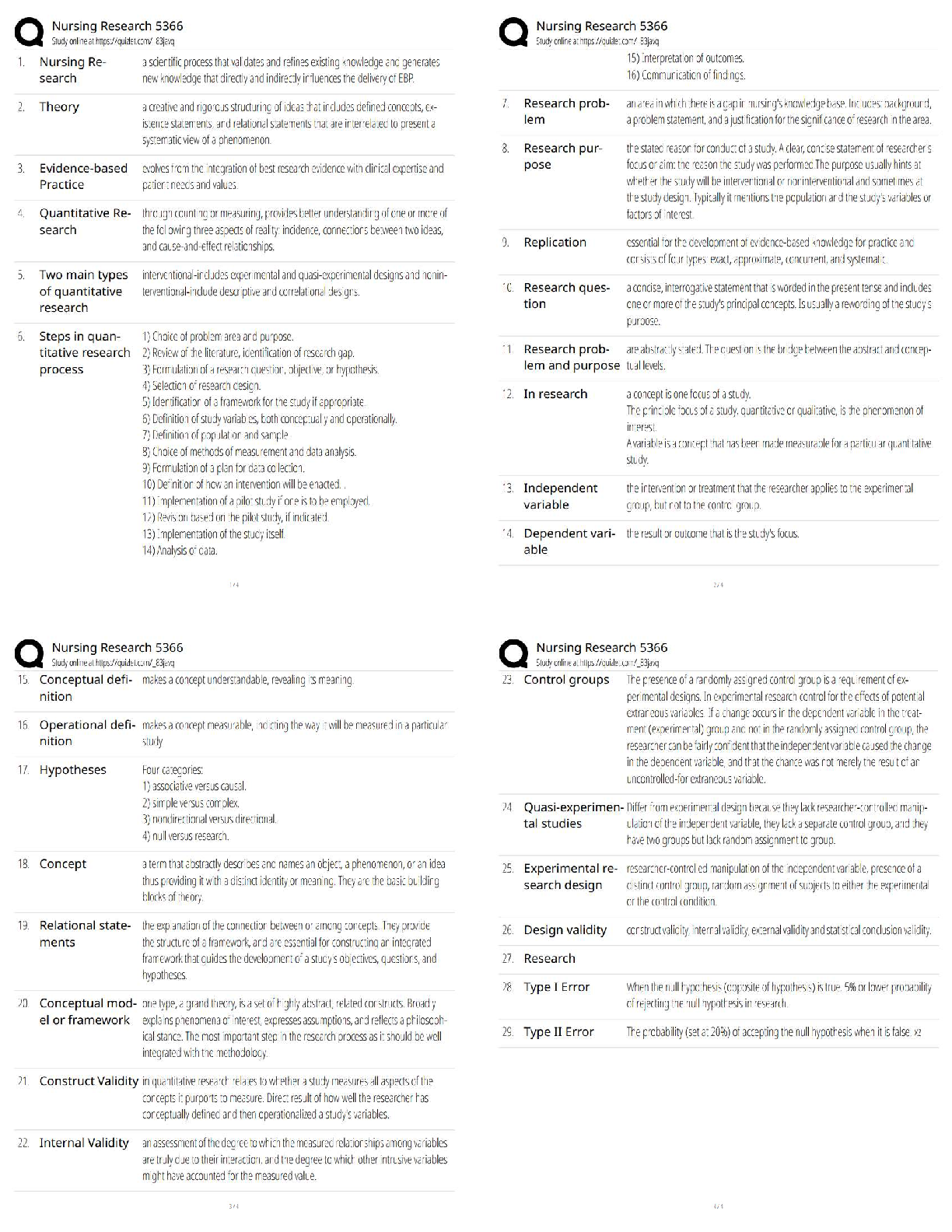
The Public Health Security and Bioterrorism Preparedness and Response Act was part of an
orchestrated government response to the events of ______________ which also included a series
of homeland security presidential directives (HSPDs) ✔✔9/11
HSPDs directed agencies such as the Food and Drug Administration to establish programs and
regulations to assure the protection of the nation's _______________ supply ✔✔food
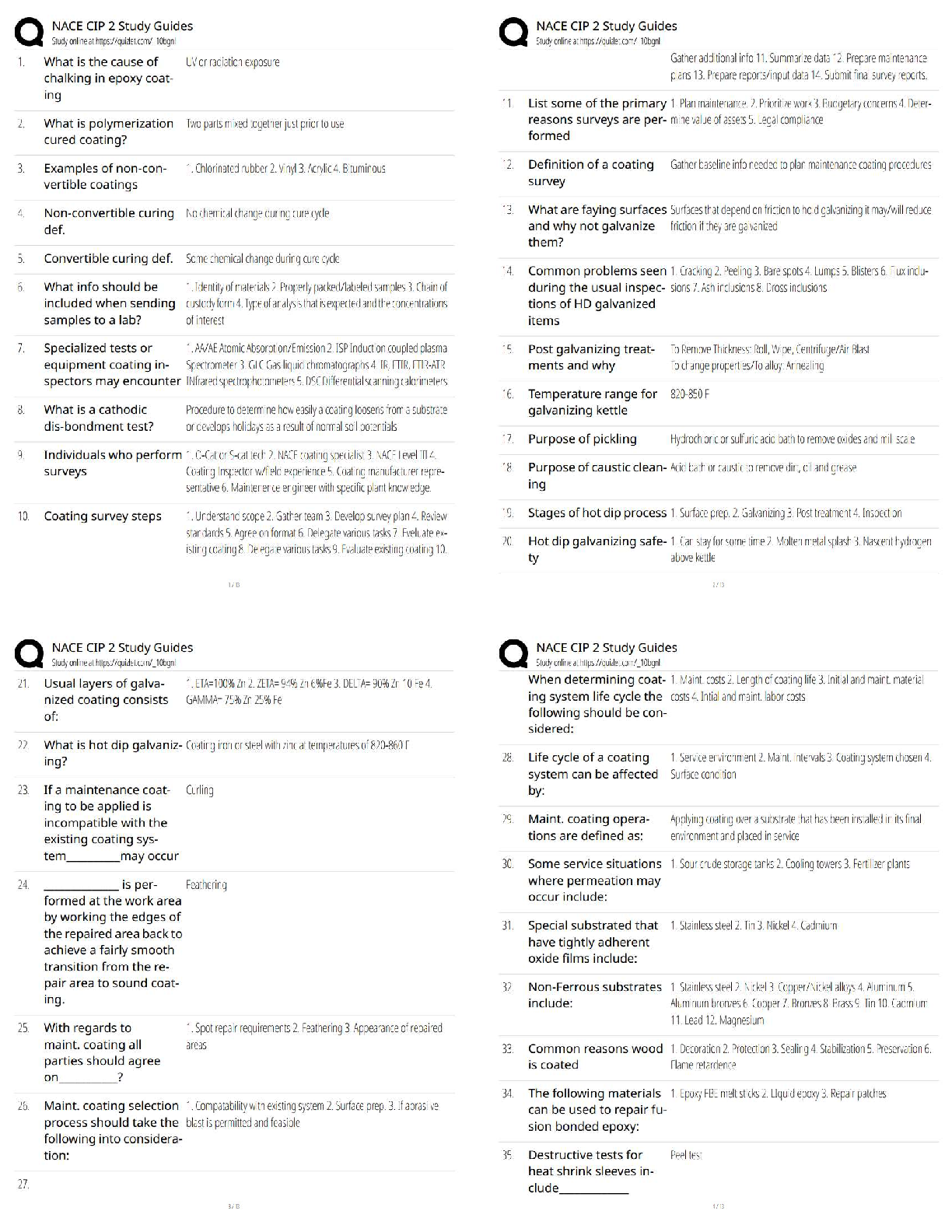
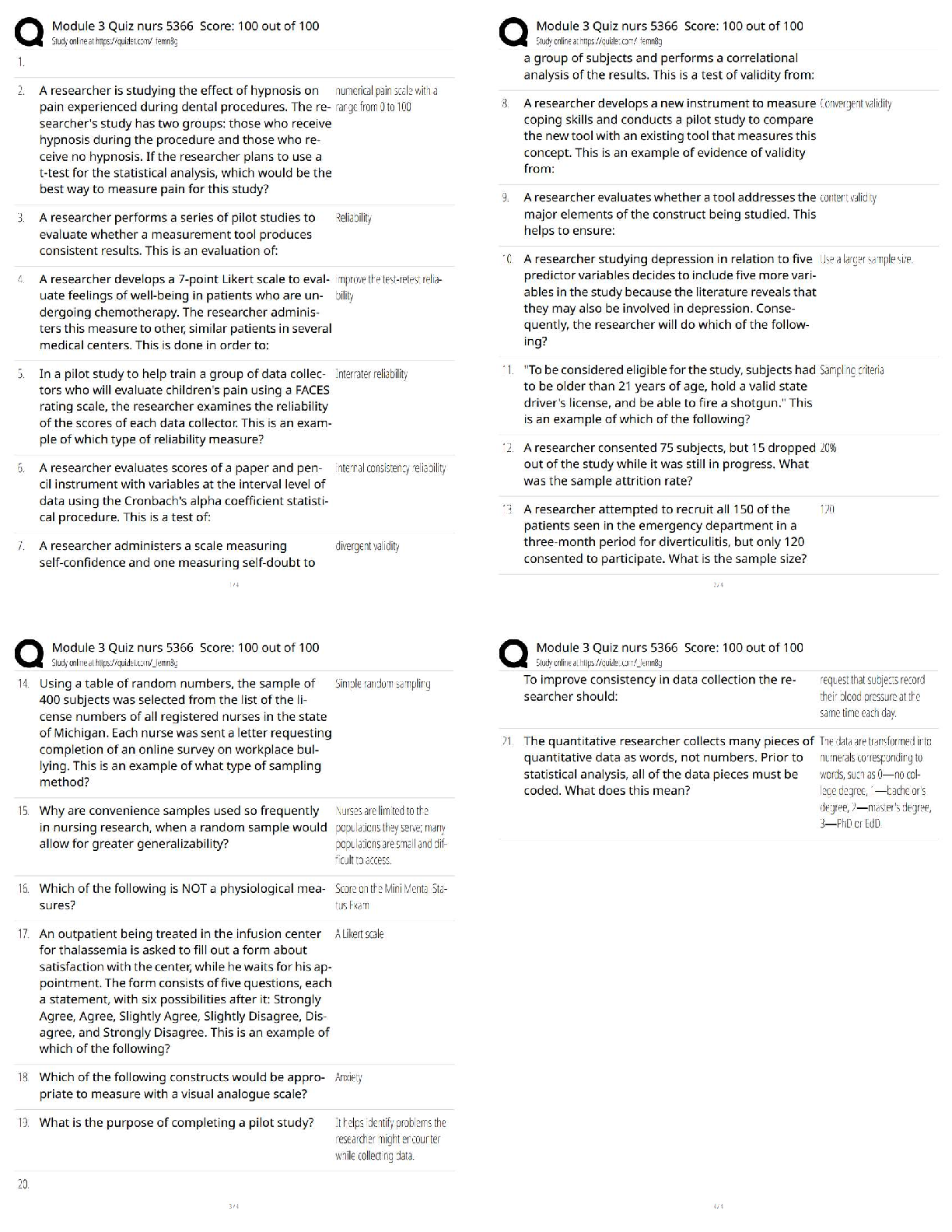
Programs & Regulations to Protect the Nation's Food Supply Include:
-Deterring intentional _____________________ of food by establishing a system of preventive
activities throughout the food chain.
-Periodic testing of the system to determine its _______________ in the event of an attack on the
food supply, and to find and address any gaps in the system. ✔✔contamination, effectiveness
FDA staff worked with representatives of IBWA and the bottled water industry to develop a
threat assessment that would serve to help the industry address any vulnerabilities to a chemical,
biological, or radiological attack, creating the ________________ + ____________________
system ✔✔CARVER + Shock
CARVER + Shock is an acronym for. . . ✔✔- Criticality: Public health and economic impacts to
achieve the attacker's intent.
- Accessibility: Physical access to the target.
- Recuperability: Ability of the system to recover from the attack.
- Vulnerability: Ease of accomplishing the attack.
- Effect: Amount of direct loss from an attack.
- Recognizability: Ease of identifying a target.
- Shock: Combined physical, public health, psychological, and economic effects of an attack.
5 Steps in the CARVER + Shock assessment: ✔✔- Flow chart the system from water source to
processing to distribution
- Identify "critical nodes" that could be the most likely targets for terrorist
- Analyze each "critical node"
- Identify counter-measures to the potential risk
- Develop a terrorist profile
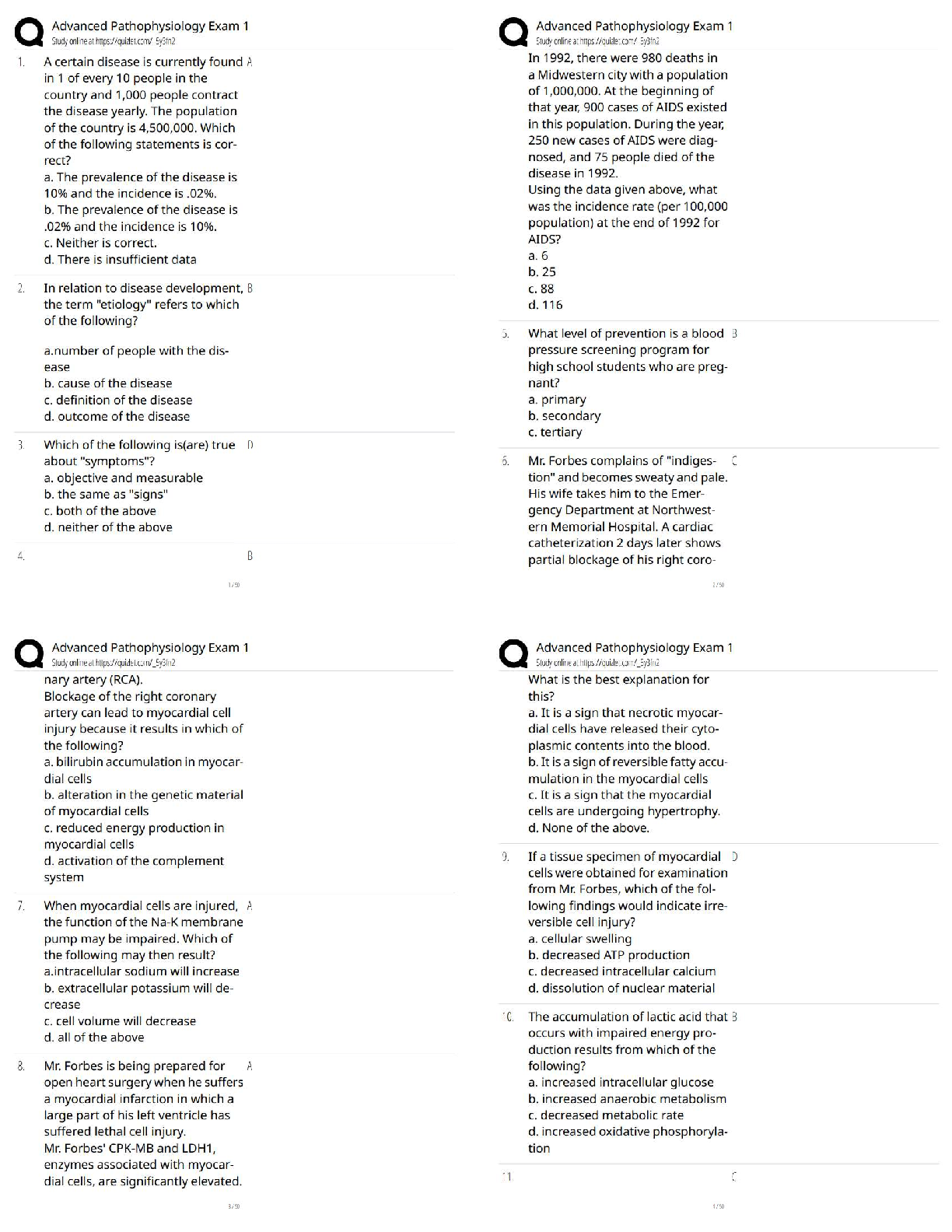
IBWA has promoted the multiple _____________ concept for many years. As they are effective
against many potential contaminants in water, the _____________ play an important part in
assuring the safety of bottled water against intentional tampering or contamination. ✔✔barrier
In 2003, the IBWA Board of Directors approved an amendment to the Model Code requiring
members to develop and maintain bottled water __________________ plans. ✔✔security
4 Principles of Management of Food Safety: ✔✔- Security Procedures
- Investigation of Suspicious activity
- Supervision
- Mail / Packages
2 Components of Security Procedures: ✔✔- Assigning responsibility for security to qualified
individual(s)
- Encouraging all staff to be alert to any signs of tampering with product or equipment, other
unusual situations, or areas that may be vulnerable to tampering, and alerting identified
management about any findings (e.g.1 providing training, instituting a system of rewards,
building into job performance standards)
2 Components of Investigation of Suspicious Activity: ✔✔- Immediately investigating all
information about suspicious activity
- Alerting local law enforcement about all suspected criminal activity
2 Components of Supervision: ✔✔- Providing an appropriate level of supervision to ail
employees, including cleaning and maintenance staff, contract workers, data entry and computer
support staff, and especially new employees.
- Conducting daily security checks of the premises far signs of tampering with product or
equipment, other unusual situations, or areas that may be vulnerable to tampering.
Main Component of Receiving Mail / Packages: ✔✔Implementing procedures to ensure the
security of incoming mail and packages (e,g., securing mailroom, visual or x-ray mail/package
screening)
5 Components of Computer Systems Security: ✔✔- Restricting access to computer process
control systems and critical data systems to those with appropriate clearance (e.g., using
passwords, firewalls).
- Eliminating computer access to past employees immediately upon voluntary or involuntary
termination.
- Establishing a system of traceability of computer transactions.
- Reviewing the adequacy of procedures for backing up critical computer-based data systems.
- Validating the computer security system.
5 Components of Raw Materials and Packaging Security: ✔✔- Using only known, appropriately
licensed or permitted (where applicable) sources for all ingredients, compressed gas, packaging,
and labels.
- Taking steps to ensure that suppliers and transporters practice appropriate food security
measures
- Authenticating labeling and packaging configuration in advance of receipt of shipment
- Inspecting incoming ingredients, compressed gas, packaging, labels, and product returns for
signs of tampering (e.g., abnormal powders, liquids, or odors) or counterfeiting (inappropriate
product identity, labeling, product lot coding or specifications), where appropriate.
- Requesting locked and sealed vehicles/containers/railcars, obtaining the seal number from the
supplier, and verifying upon receipt - make arrangements to maintain the chain of custody when
a seal is broken for inspection by a government agency
Operations security includes the security of _______________ and plant __________ ✔✔water,
air
3 Components of Water Security: ✔✔- Securing water wells, hydrants, storage and handling
facilities
- Ensuring that water systems and trucks are equipped with backflow prevention
- Maintaining contact with the public water provider to be alerted to problems
2 Components of Plant Air Security: ✔✔- Securing access to air intake points for the facility, to
the extent possible (e.g., using fences, sensors, guards, video surveillance).
- Examining air intake points for physical integrity routinely.
Maintain security of finished products by taking ________________ regularly. Investigating
missing or extra stock or other irregularities outside a predetermined normal range of variation
and alerting local law enforcement about unresolved problems, when appropriate. ✔✔inventory
Maintain security of finished products by ensuring that public storage ________________ and
_________________ (vehicles and vessels) practice appropriate security measures (e.g., auditing
for compliance with food security measures that are contained in contracts or letters of
guarantee). ✔✔warehousing, shipping
Maintain security of finished products by performing __________________ inspection of
storage facilities, vehicles, and vessels. ✔✔random
Maintain security of finished products by requesting ____________ and _____________
vehicles/containers/railcars and providing the seal number to the consignee (remember to consult
any relevant federal, state or local fire or occupational safety codes before making any changes).
✔✔locked, sealed
Maintain security of finished products by advising sales staff to be on the lookout for
___________________ products during visits to customers and alerting management if any
problems are detected. ✔✔counterfeit
Maintain security of finished products by evaluating the _______________ of finished product
testing for detecting tampering or criminal or terrorist activity. ✔✔utility
Maintain security of finished products by monitoring closely the _____________ of foods in
open display areas (e.g., salad bars, open bulk containers). ✔✔serving
3 Parts of a Recall Strategy: ✔✔- Identify the person responsible, and a back-up.
- Provide fur proper disposition of recalled product.
- Identify customer contacts, addresses and phone numbers.
Be sure to _______________ the lessons learned from past tampering or terrorist events.
✔✔evaluate
_________________ reviewing and testing the effectiveness of strategies (e.g., conducting mock
criminal, terrorist or tampering event and mock recall, challenging computer security system)
and revising accordingly - using third party or in-house security expert. ✔✔Annually
Performing _____________ and ________________ food security inspections of facility
(including receiving and warehousing areas and intrusion detection system) - using third party or
in-house security expert ✔✔routine, random
___________________ that security contractors are doing an adequate job ✔✔Verify
[Show More]













.png)