Computer Science > QUESTIONS & ANSWERS > B.4 CompTIA IT Fundamentals FC0-U61 Certification Practice Exam (All)
B.4 CompTIA IT Fundamentals FC0-U61 Certification Practice Exam
Document Content and Description Below
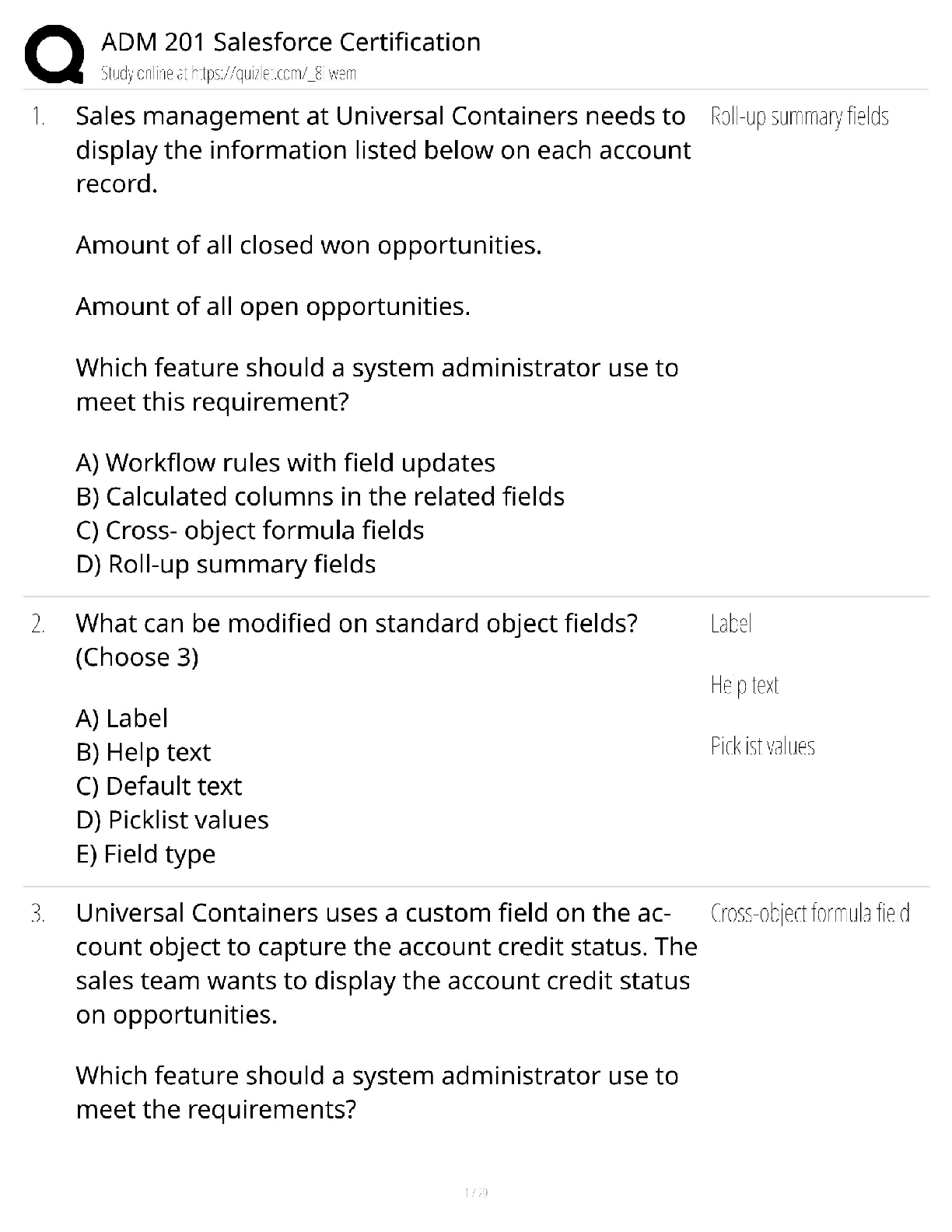
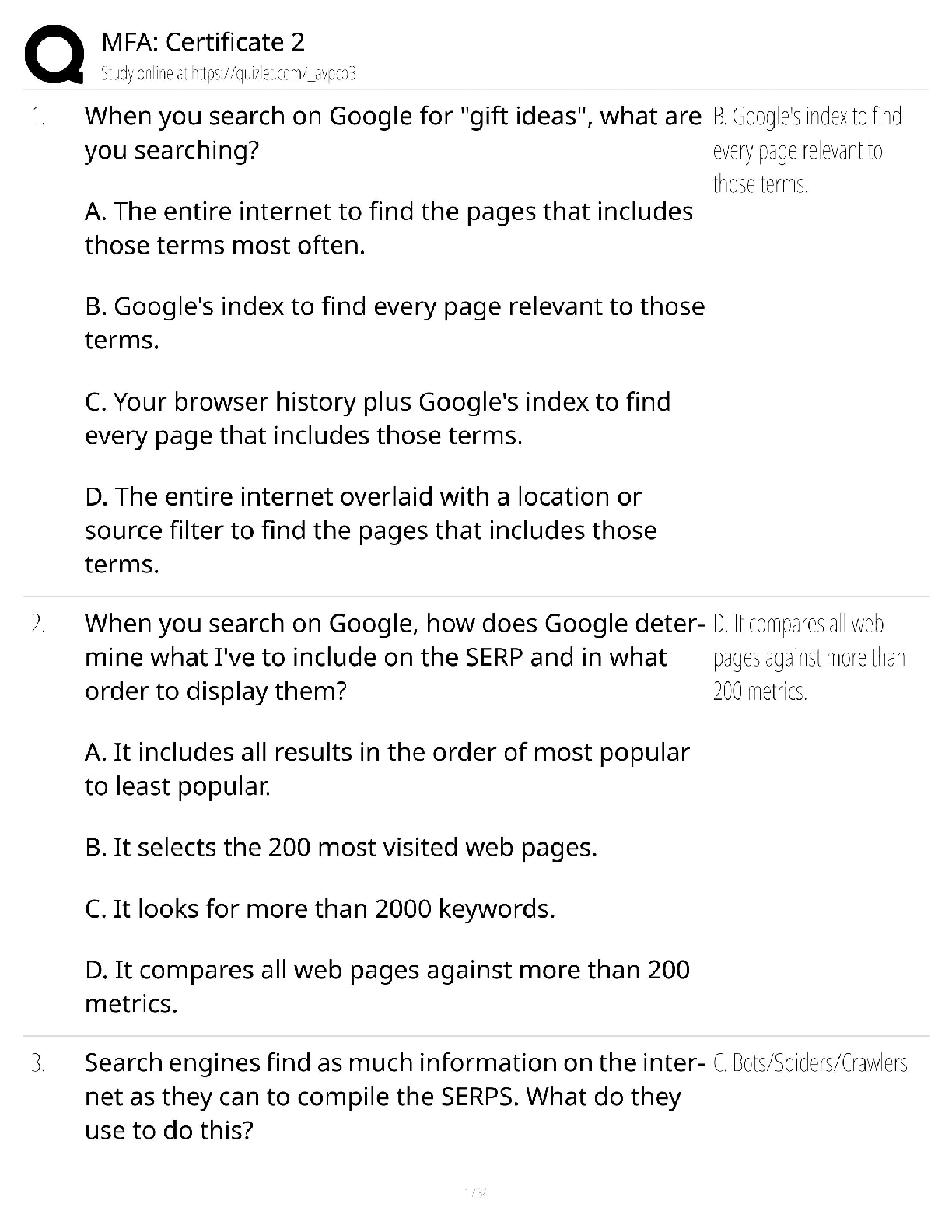
B.4 CompTIA IT Fundamentals FC0-U61 Certification Practice Exam Which connector is used with an unshielded twisted pair (UTP) cable? - ✔✔RJ-45 A business is requesting confidential information ... from a customer to complete an online transaction. Which of the following is the MOST important action the business should take as part of their information request? - ✔✔Obtain permission from the customer to process and store the confidential information. Brandon is a member of an online gaming community that makes files available to each other from their local hard drives. Which of the following BEST describes this file system feature? - ✔✔P2P (peer-to-peer) sharing What do you call the software that can communicate with a computer's hardware, provides a user interface to accept commands, maintains a filing system, and has built-in security features? - ✔✔Operating system Which of the following terms describes the set of SQL commands that change the structure or schema of a database, such as the DROP command? - ✔✔Data Definition Language (DDL) Martin just purchased a new computer and wants to surf the web. He is afraid his new computer may get infected by automatically installing viruses. What should he do to protect his computer? - ✔✔Change browser settings to notify before downloading. A consumer wants to add a hard drive to their computer to store video from their camera. Which of the following is the storage capacity of a modern hard disk drive (HDD) purchased from a computer store? - ✔✔3 terabytes Ben wants to format his flash drive so it can be read on many types of devices, such as game consoles and different desktop computers running different operating systems. Which file system should he format his flash drive to so it can be used this way? - ✔✔FAT32 Which of the following colored jacks on an audio card would you connect a microphone to? - ✔✔Pink Abby wants a high-end computer system for her home office that can be upgraded. Which of the following should she choose? - ✔✔Desktop Hans is programming a device driver that will interact directly with hardware. The language he's using is considered the most difficult human-readable language. Which of the following languages is he utilizing? - ✔✔Assembly Gloria is concerned that her online banking transactions could be intercepted if she uses public WiFi. Which of the following could she use to prevent access to her online transactions? - ✔✔VPN Which of the following authentication types include security questions as a factor for providing security? - ✔✔Type 1 authentication Gary has finished installing a wireless router for his neighbor's small business. Which wireless standard should Gary use to support up to 150 Mbps on the 5 GHz band? - ✔✔802.11n Firewalls, data encryption, backups, and passwords are designed to protect computing devices. These technologies are all examples of what? - ✔✔Security controls Which of the following connectors are used to terminate a Cat 5e and Cat 6a network cable? - ✔✔RJ-45 Greg is a network administrator for a medical supply company and has identified a problem with an access control list (ACL) failing to filter out data packets that have been restricted. What is the next step Greg should take to troubleshoot the ACL problem? - ✔✔Research knowledge bases and the internet for information related to the problem. Modern smartphones are amazing devices. They have more computing power than the computers that put a man on the moon in 1969. Which type of operating system do they run? - ✔✔Mobile OS A system administrator has completed the entire troubleshooting process. Some employees at the office were plugging their Ethernet cable into the wrong port and not getting access to network resources. Although the administrator tested the solution, a couple weeks later other employees begin help tickets for the same issue. Which of the following BEST describe what the administrator might have missed doing during the troubleshooting process? - ✔✔Taking preventative actions. What group of database commands is used to define and modify metadata? - ✔✔Data definition A programmer is developing an application that will store names and addresses (street, city, state, and zip code). The zip code must be able to accommodate alphanumeric characters to accommodate international zip codes, such as Canada. Which data type should be used for the variable that will hold the zip code? - ✔✔String Which of the following provides the ability to control which websites can run client-side scripting in your web browser? - ✔✔Script blocker add-on When Jacob first starts his computer, he hears several warning beeps and nothing else happens. Which of the following is sending out the beeps? - ✔✔Power-On Self-Test (POST) A programmer is developing a program that will list the order history for a customer. Which of the following data structures is the BEST one to use? - ✔✔Array Which option should you use to respond to every single person included on an email? - ✔✔Reply All In the decimal number system, you can think of each digit representing a place (or column) in the number. For example, in the decimal number 652, the two, the five, and the six are all in different places and each place can be expressed as 10 to a specific power. Which power of 10 does 6 in the above example represent? - ✔✔10 to the second power Which of the following CPU types does Nvidia's Tegra fall under? - ✔✔ARM Which of the following is an advantage of using a relational database over a key/value pair database? - ✔✔Relational databases use SQL to retrieve data from the database. You need a storage device that has very large storage capacity, is fast, and is relatively inexpensive. Which storage device will best suit your needs? - ✔✔Hard disk Justin has purchased a new laptop but is having problems connecting to his home Wi-Fi network. Which of the following is the MOST likely issue that is preventing the laptop from connecting to the Wi-Fi network? - ✔✔The external Wi-Fi button or switch on the laptop case needs to be turned on. Which of the following is a common form of social engineering attack? - ✔✔Hoax virus information emails. Diana, a developer, needs to program a logic component that will allow the user to enter a series of values. Which of the following would BEST provide that functionality? - ✔✔Looping Which of the following disaster recovery concepts applies when a server needs to be online and accessible at all times? - ✔✔Redundancy Which of the following BEST describes what a kilobyte is a measurement of? - ✔✔Storage space Gina is a database user and her supervisor has asked her to generate a report from the structured database. Gina does not know how to write SQL commands and no forms have been created. Which of the following would be her BEST option to generate the report? - ✔✔Query builder Katy has uninstalled a photo editing application, but an icon still appears on her web browser for the application. Which of the following is the BEST solution for getting rid of the icon? - ✔✔Remove the application add-on in the web browser. Which of the following is the basic difference between a password and a passphrase? - ✔✔Passphrases are longer than passwords and can include spaces. You are working on a program that needs to keep track of many values at the same time. Which of the following would you use? - ✔✔An array You sign up for an online class at the local community college. The course is all web based. You open your favorite browser to enter the class portal, and you get a message "Use one of these browsers." What is the problem? - ✔✔Browser compatibility. Which of the following should be done to protect your identity when creating a social media profile? - ✔✔Always review and set privacy settings. Dana is an IT administrator who is working on a company-wide initiative to address confidentiality concerns about secure information being revealed to unauthorized individuals. Which of the following would be topics on the team agenda? (Select two.) - ✔✔Snooping, Social engineering The legal protection of rights to ideas and discoveries is called a copyright. What are the other ways that intellectual property can be legally protected? (Select two.) - ✔✔Trademarks, Patents Which option should you use to respond to the sender of an email but not all the recipients? - ✔✔Reply Lynda, a programmer, is developing a Linux device driver in assembly language. Many device drivers are written in the C language. Which of the following is the BEST reason for using assembly language instead of C? - ✔✔Code written in assembly is more efficient and allows direct access to hardware. Linda has just purchased a Tesla electric car with online navigation software and the ability to automatically drive itself. Which of the following BEST describes this type of technology? - ✔✔IoT (Internet of Things) A software developer is working on a website and has been tasked with adding interactive elements to it. Which of the following programming languages would work BEST for this task? - ✔✔JavaScript As a system administrator, you are modifying access control lists to make sure that company employees are only given access to company resources that they need to do specific tasks. Which of the following BEST describes this process of limiting access rights? - ✔✔Principle of least privilege What is the name of the large background area of the Windows environment that holds icons for files, folders, and applications? - ✔✔Desktop Adam is a marketing manager for a financial advisory firm and is sitting in an airport terminal waiting for a connecting flight. Adam is connected from his laptop to the free Wi-Fi service available in the terminal, has just finished a client's financial statement, and wants to upload it to a cloud-based company document storage server. Which of the following is the BEST solution for Adam to securely upload the file? - ✔✔Wait until he has access to a secured network service before uploading the financial statement. A user has entered a search string into an application and clicked on the search icon. Which of the following is the NEXT step in the computing process? - ✔✔Processing Your organization has 20 employees who need an accounting software update installed. Due to a miscommunication, the purchaser only paid to update 10 licenses. The software company issued a paper license and a single key for updating 10 users. This is an enterprise paper license and there is no mechanism that enforces a limit to the number of times the key can be used. You decide to update all 20 users. Which of the following are possible consequences of this decision? (Select two.) - ✔✔You risk losing your job. The basic (and smallest) unit of computer information is the bit (binary digit). Memory and file sizes are commonly measured in multiples of bits. What is the first multiple of a bit called? - ✔✔Byte Which of the following do cybercriminals frequently use to alter or compromise data integrity? - ✔✔Malware attack Which of the following are wired components that allow a computer to connect to an internal company network? (Select two.) - ✔✔RJ-45 cable, Network interface port A developer is creating a program that will store a customer's latest order number. The value will change each time a customer creates a new order. Which of the following would MOST likely be used to store the value? - ✔✔Variable Pam is working with a database that contains all the product and customer orders for her company. Pam is using SQL to access the database to retrieve a customer's order. Which of the following BEST describes SQL? - ✔✔Query language A business wants to set up a database to store customer and order information. They have decided to use a relational database. Which of the following is the main benefit of using a relational database? - ✔✔The data can be organized into separate tables that are related to each other. Patricia, a database system manager for a large hotel chain, is setting up a relational database to track customer hotel registrations for each hotel. The table in the database currently includes fields (columns) for First Name, Last Name, Phone, Email, License Plate #, and Check-in Date. What can Patricia do to make sure that each record (row) in the database is unique? - ✔✔Create an additional Check-in ID field. Which of the following is a firewall function? - ✔✔Packet filtering Emily is using Search on her web browser to try and find a recipe for pecan pie. However, she wants to make sure it's a recipe from her home state of Mississippi. Which of the following search phrases will help her find exactly what she needs? - ✔✔"Mississippi pecan pie" A pop-up blocker is a web browser feature that _________________. - ✔✔prevents unwanted advertisements Which of the following stores data using microscopic light and dark spots? - ✔✔Compact disc A medical supply company is using a spreadsheet to keep track of inventory. The company is rapidly expanding, and several employees now need to access the spreadsheet securely at the same time (concurrent use). However, each time one employee opens the spreadsheet, it's locked for use by any other employees. Which of the following provides the BEST solution to resolve this issue? - ✔✔Switch to a database that allows for concurrent users and can support thousands of users accessing the data at the same time. A user was working on a spreadsheet when the application became unresponsive. After waiting several minutes, the application is still unresponsive. Which of the following is the BEST action for the user to take? - ✔✔Use Task Manager to end task Which of the following is a significant difference between a patent and a trademark? - ✔✔Patents exist to protect creators, while trademarks exist to protect consumers. Which of the following statements BEST describes a firewall? - ✔✔A firewall restricts the flow of data between hosts and networks by checking data packets to make sure they are safe. In a networking environment, which of the following describes a 32-bit binary number in four octets with each octet separated by a period? - ✔✔IP address Which of the following BEST describes the use of a database by the application? - ✔✔Data persistence A systems engineer wants to encrypt a hard drive that contains critical data. Which type of data encryption can be used to protect the data on the hard drive? - ✔✔Whole disk encryption You have recently issued new mobile phones to the sales team in your company. Each phone has the ability to store and transmit encrypted information for such things as making payments at a checkout counter. Which of the following is the technology being used in these phones? - ✔✔NFC chips Your company is having issues with employees who write down their passwords on sticky notes, paper notepads, and other types of paper. Even though they're often hidden in drawers or behind computer equipment, it is still a high security risk for the company. As the managing IT administrator for your company, what is the BEST solution to reduce or eliminate this issue? - ✔✔Work with Human Resources to provide security training. You are using your new scanner to scan a text document so you can edit it on the computer. Which type of software would you use to do this? - ✔✔OCR Personnel management policies provided by Human Resources contribute significantly to security in a company. Which of the following is the personnel management policy type that communicates the importance of security to employees? - ✔✔Operation Stewart's friend gave him an old server. He decides to install a second NIC card and some extra hard drives. He puts the computer on his network and shares all the storage space for clients to use. What did Stewart just create? - ✔✔A file server What is the term for software that is exclusively controlled by a company and cannot be used or modified without permission? - ✔✔Proprietary Software [Show More]
Last updated: 2 years ago
Preview 1 out of 14 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$10.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Jul 30, 2023
Number of pages
14
Written in
All
Additional information
This document has been written for:
Uploaded
Jul 30, 2023
Downloads
0
Views
150








.png)