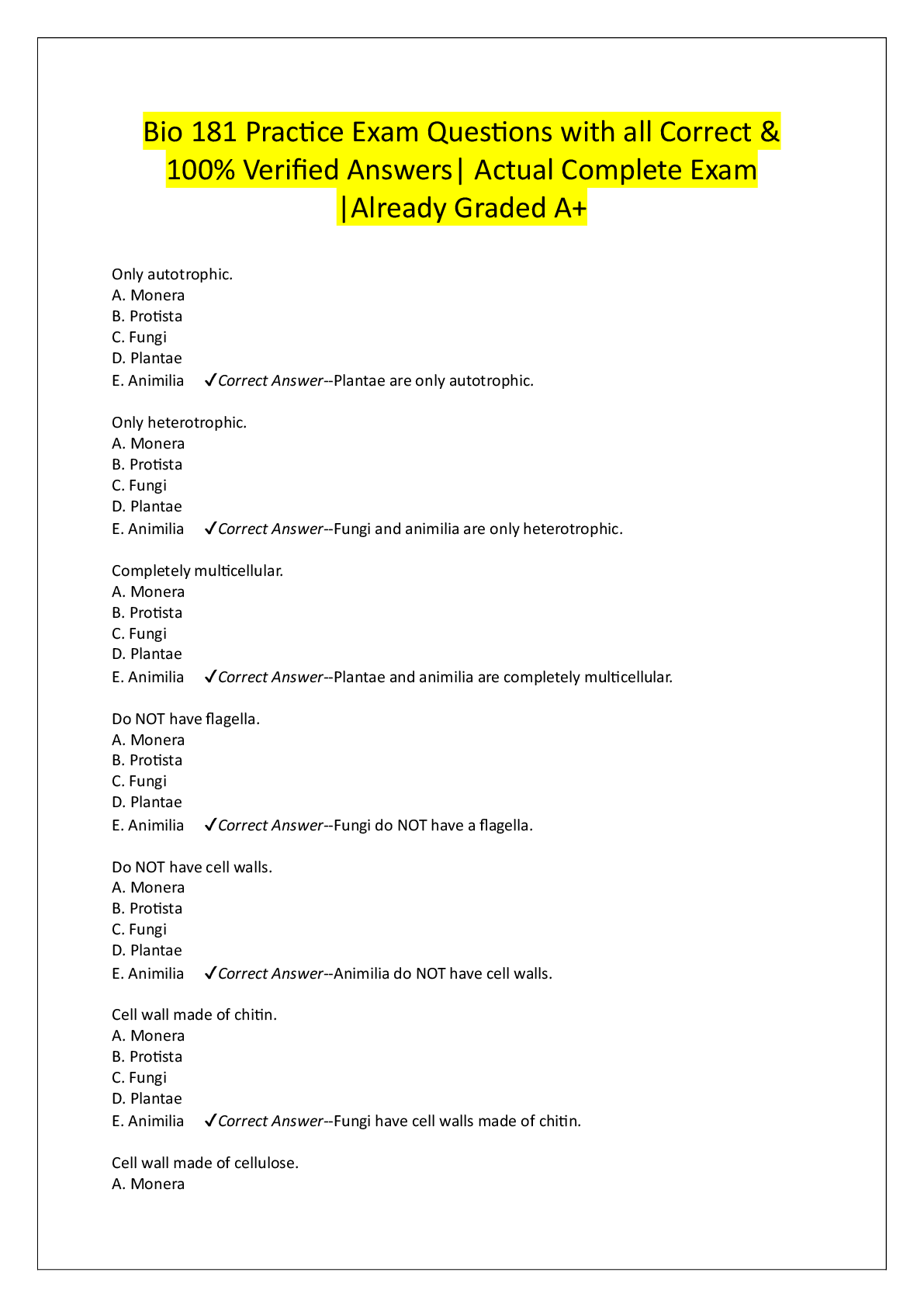
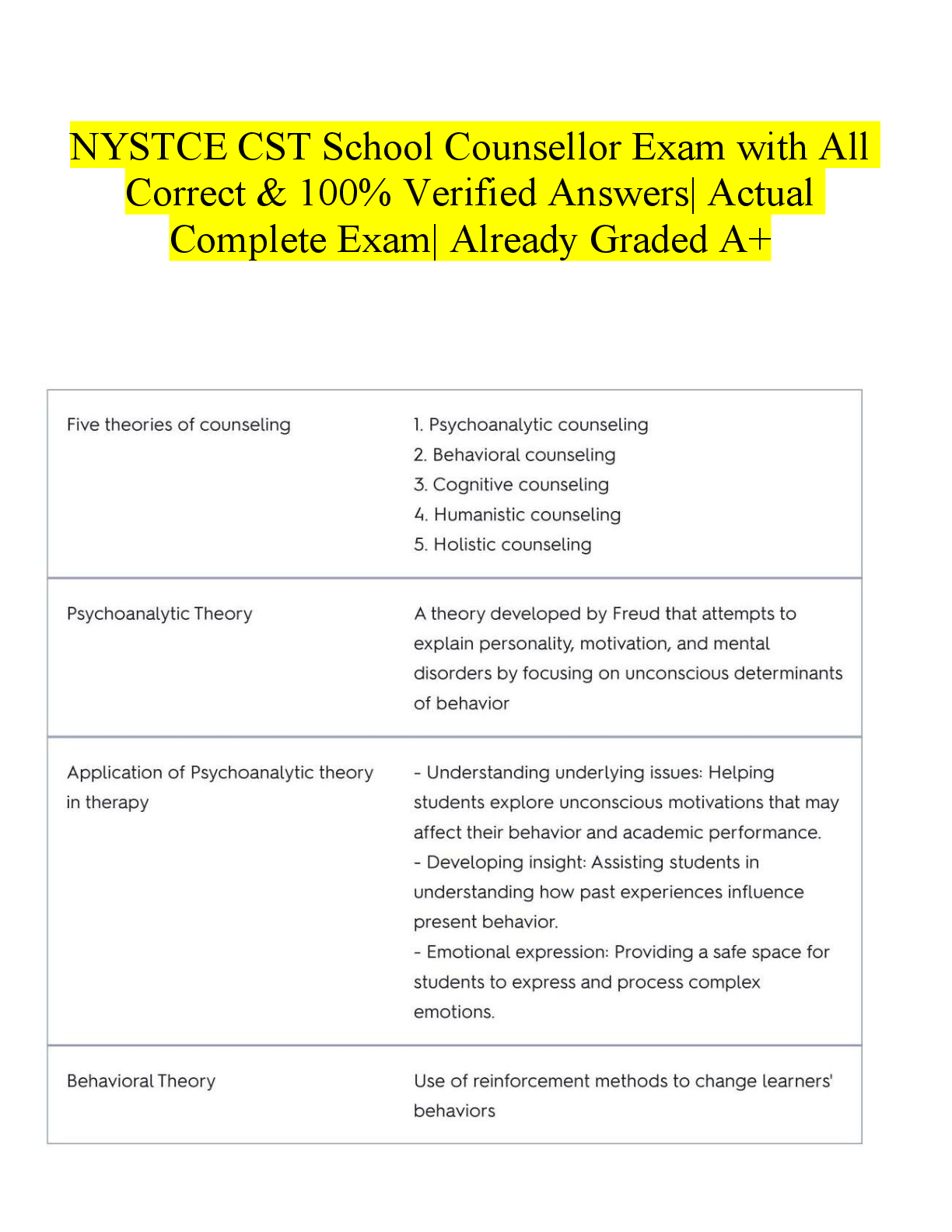
Business > EXAM > Qualys Vulnerability Management v1|30 Questions with Verified Answers,100% CORRECT (All)
Qualys Vulnerability Management v1|30 Questions with Verified Answers,100% CORRECT
Document Content and Description Below
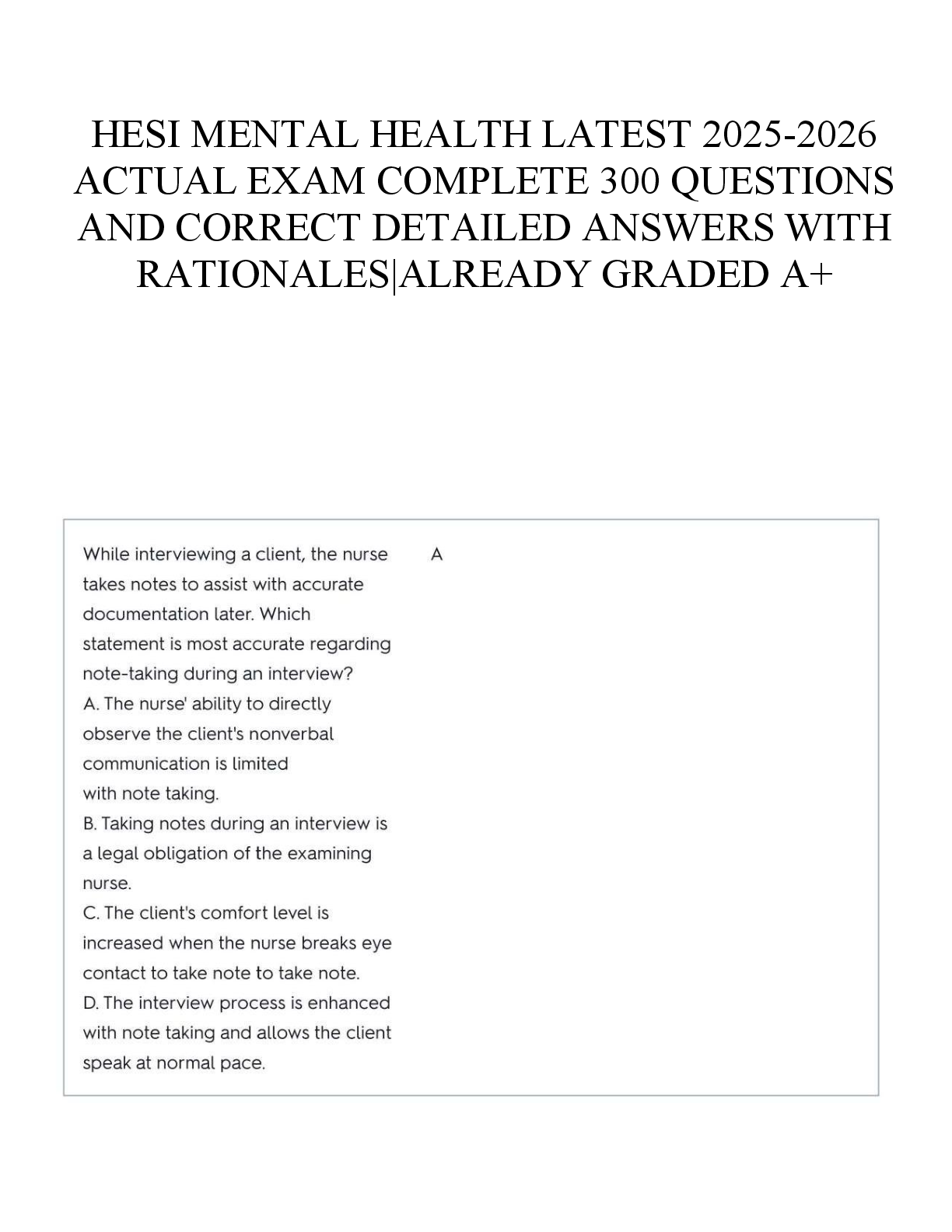
Qualys Vulnerability Management v1|30 Questions with Verified Answers Which of the following are benefits of scanning in authenticated mode? (choose 2) - Fewer confirmed vulnerabilities - Mor ... e vulnerabilities are detected - Time saved from manually investigating potential vulnerabilities - More accurate scan details - CORRECT ANSWER - More vulnerabilities are detected - Time saved from manually investigating potential vulnerabilities Which of the following are valid options for scanning targets? (choose 3). - Asset Groups - Domain Name - IP addressing - Asset Tags - Search Lists - MAC Address - CORRECT ANSWER - Asset Group - IP Addressing - Asset Tags What type of scanner appliance (already provisioned within the Qualys Cloud Platform) is ideal for scanning public facing assets? - Offline Scanner - Virtual Scanner - External Scanner - Internal Scanner - CORRECT ANSWER External Scanner 4. Which of the following is NOT a component of a vulnerability scan? - Host Discovery - OS Detection - Port Scanning - Business Impact - CORRECT ANSWER Host Discovery Which of the following will have the greatest impact on a half red, half yellow QID? - Share Enumeration - Scan Dead Hosts - Authentication - Authoritative Option - CORRECT ANSWER Authentication What is the maximum number of TCP ports that can participate in the Host Discovery process? - 10 - 65535 - 1900 - 20 - CORRECT ANSWER 20 Which of the following items are used to calculate the Business Risk score for a particular asset group? (choose 2) - Business Impact - Security Risk - CVSS Base - CVE ID - CORRECT ANSWER - Business Impact - Security Risk In order to successfully perform an authenticated (trusted) scan, you must create a(n): - Authentication Record - Search List - Asset Map - Report Template - CORRECT ANSWER Authentication Record Multiple Remediation Policies are evaluated: - From top to bottom - From bottom to top - Based on the rule creation date - In no specific order - CORRECT ANSWER From top to bottom A search list contains a list of QIDs Host Assets Applications Asset Groups - CORRECT ANSWER QIDs Dynamic Asset Tags are updated every time you. - Run a scan - Create a remediation policy - Run a report - Search the KnowledgeBase - CORRECT ANSWER Run a scan As a Manager in Qualys, which activities can be scheduled? - Asset Searches - Updates to the KnowledgeBase - Maps - Reports - Scans - CORRECT ANSWER - Asset Searches - Updates to the KnowledgeBase - Maps - Reports - Scans What does it mean when a "pencil" icon is associated with a QID in the Qualys KnowledgeBase? - There is malware associated with the QID - The QID has a known exploit - The QID has been edited - A patch is available for the QID - CORRECT ANSWER The QID has been edited Which item is not mandatory for launching a vulnerability scan? - Target Hosts - Option Profile - Authentication Record - Scanner Appliance - CORRECT ANSWER Authentication Record About how many services can Qualys detect via the Service Detection Module? - 13 - 512 - 20 - 600 - CORRECT ANSWER 600 By default, the first user added to a new Business Unit becomes a ____________ for that unit. - Auditor - Administrator - Reader - Scanner - Unit Manager - CORRECT ANSWER Unit Manager In a new Option Profile, which authentication options are enabled by default? - All - Unix - Windows - None - CORRECT ANSWER None Which of the following vulnerability scanning options requires the use of a "dissolvable agent"? - Windows Share Enumeration - TCP port scanning - Scan Dead Hosts - UDP port scanning - CORRECT ANSWER Windows Share Enumeration To produce a scan report that includes the results from a specific scan that occurred at a specific point in time, you should select the _______________ option in the Report Template. - Scan Based Findings - Dynamic Findings - Static Findings - Host Based Findings - CORRECT ANSWER Host Based Findings About how many TCP ports are scanned when using Standard Scan option? - 1900 - 10 - 20 - 65535 - CORRECT ANSWER 1900 Asset Groups and Asset Tags can be used to effectively customize or fine tune ... (choose all that apply) - Reports - Vulnerability Scans - Remediation Policies - Search Lists - CORRECT ANSWER Reports Vulnerability Scans Remediation Policies What is required in order for Qualys to generate remediation tickets? (choose all that apply) - Scan Results need to be processed by Qualys - A Policy needs to be created - A Map needs to be run - A Remediation Report needs to be run - CORRECT ANSWER - Scan Results need to be processed by Qualys - A Policy needs to be created Before you can scan an IP address for vulnerabilities, the IP address must first be added to the. - Host Assets tab - Business Units tab - Domains tab - Search List tab - CORRECT ANSWER Host Assets tab What is the 6-step lifecycle of Qualys Vulnerability Management? - Mapping, Scanning, Reporting, Remediation, Simplification, Authentication - Learning, Listening, Permitting, Forwarding, Marking, Queuing - Bandwidth, Delay, Reliability, Loading, MTU, Up Time - Discover, Organize Assets, Assess, Report, Remediate, Verify - CORRECT ANSWER Discover, Organize Assets, Assess, Report, Remediate, Verify To exclude a specific QID/vulnerability from a vulnerability scan you would: - Disable the QID in the Qualys KnowledgeBase. - Ignore the vulnerability from within a report. - Place the QID in a search list, and exclude that search list from within the Option Profile. - You cannot exclude QID/Vulnerabilities from vulnerability scans. - CORRECT ANSWER Place the QID in a search list, and exclude that search list from within the Option Profile. Which of the following components are included in the raw scan results, assuming you do not apply a Search List to your Option Profile? (choose all that apply) - Host IP - Option Profile Settings - Potential Vulnerabilities - Information Gathered - Vulnerabilities - CORRECT ANSWER - Potential Vulnerabilities - Information Gathered - Vulnerabilities Which of the following types of items can be found in the Qualys KnowledgeBase? (choose all that apply) - Potential Vulnerabilities - Configuration data (Information Gathered) - Confirmed Vulnerabilities - Asset Groups - Remediation Tickets - CORRECT ANSWER - Potential Vulnerabilities - Configuration data (Information Gathered) - Confirmed Vulnerabilities Which three features of the Vulnerability Management application can be customized using a KnowledgeBase "Search List"? - Authentication Records - Report Templates - Remediation Policies - Option Profiles - CORRECT ANSWER - Report Templates - Remediation Policies - Option Profiles What type of Search List adds new QIDs to the list when the Qualys KnowledgeBase is updated? - Active - Static - Dynamic - Passive - CORRECT ANSWER - Dynamic When a host is removed from your subscription, the Host Based Findings for that host are. - Ranked - Purged - Ignored - Archived - CORRECT ANSWER - Purged [Show More]
Last updated: 2 years ago
Preview 1 out of 9 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$8.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Oct 09, 2023
Number of pages
9
Written in
All
Additional information
This document has been written for:
Uploaded
Oct 09, 2023
Downloads
0
Views
67