Business > EXAM > Service Now Vulnerability Response Implementor me 191 Questions with Verified Answers,100% CORRECT (All)
Service Now Vulnerability Response Implementor me 191 Questions with Verified Answers,100% CORRECT
Document Content and Description Below
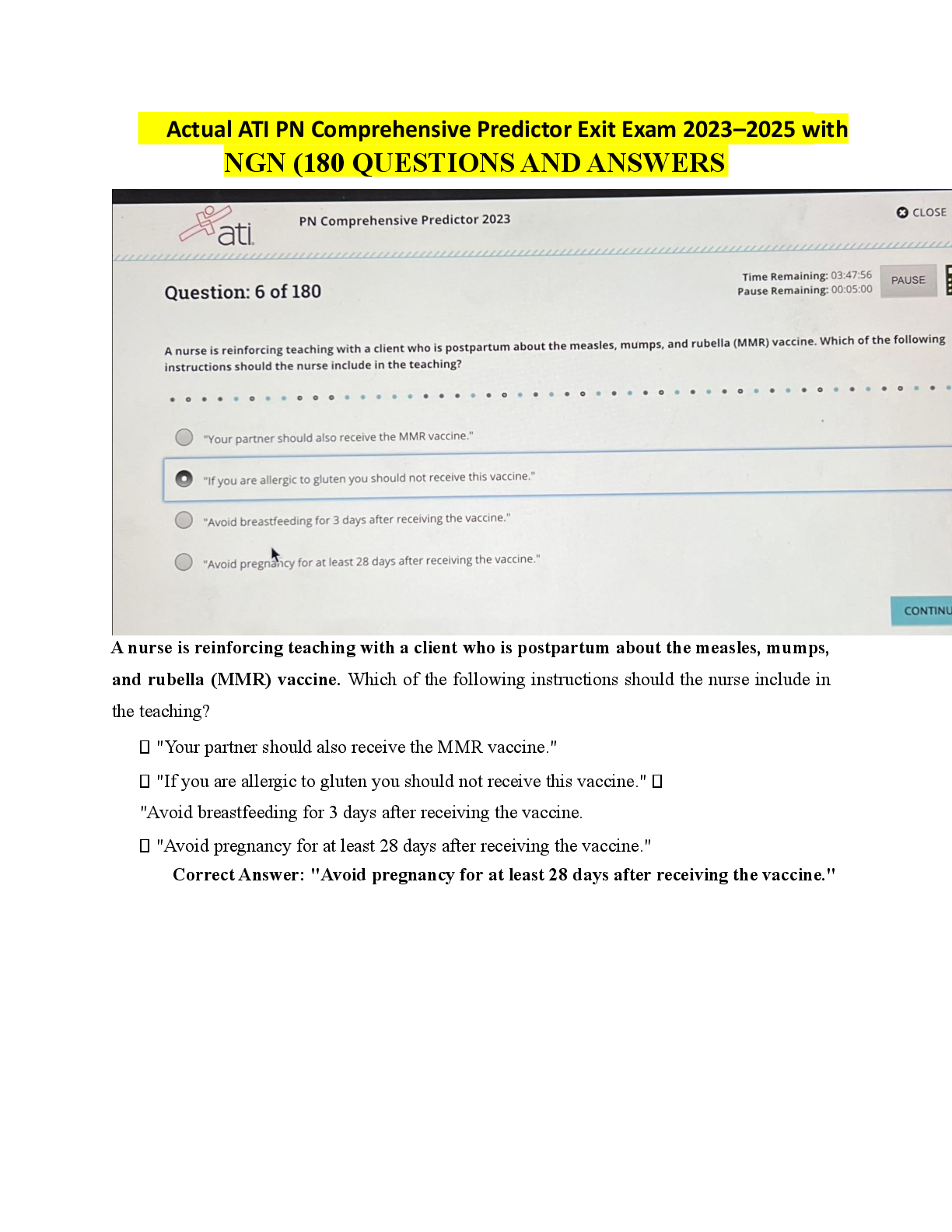
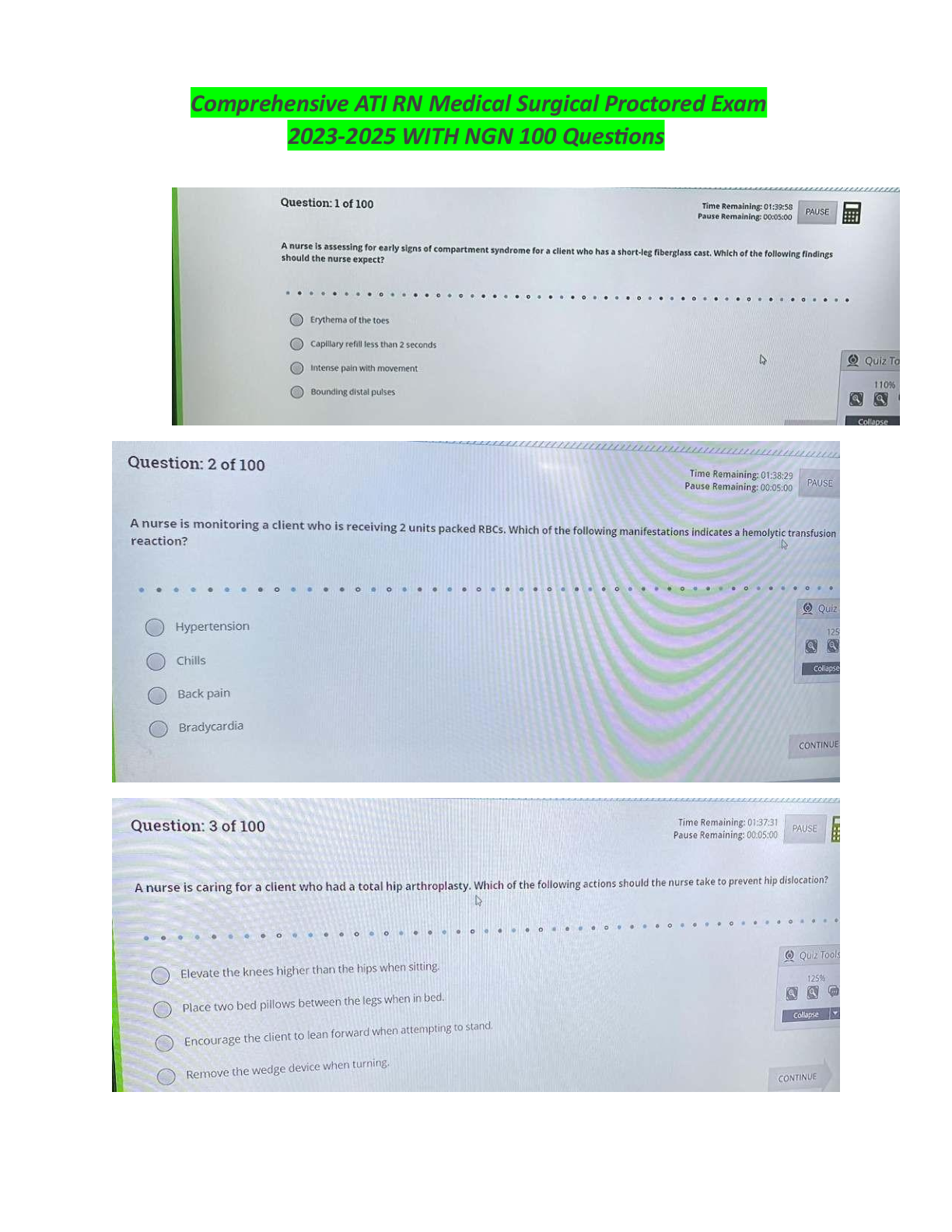
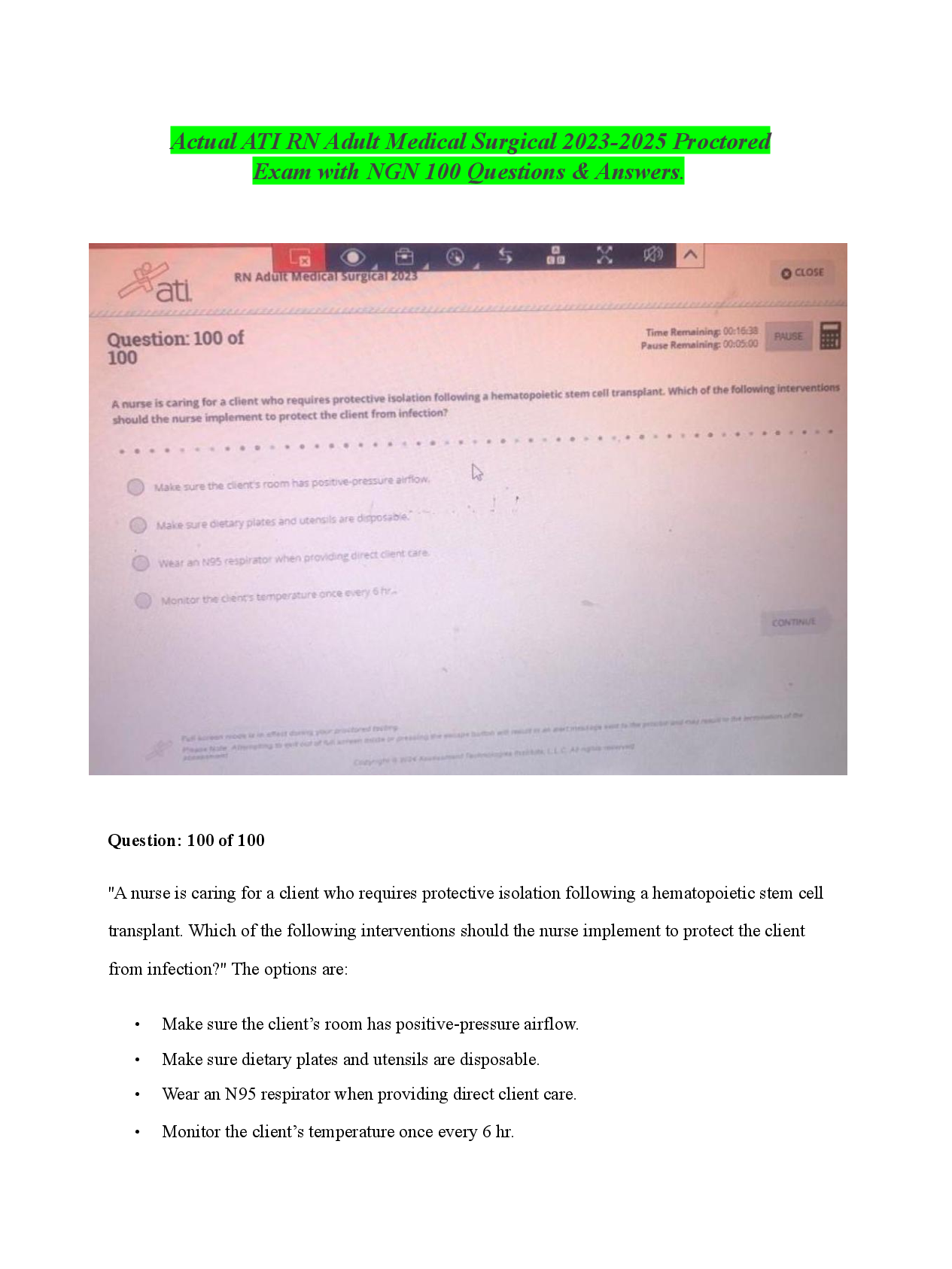
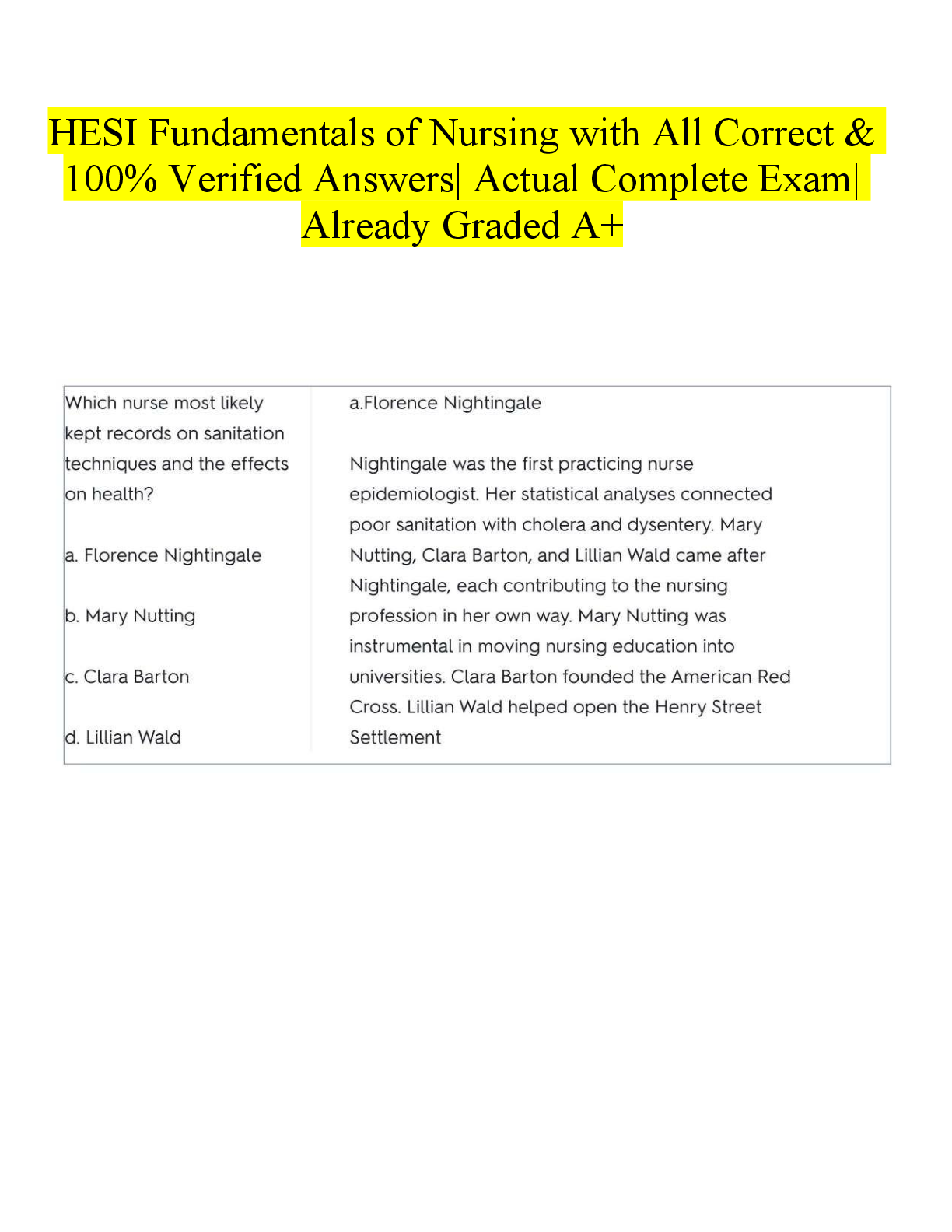
Service Now Vulnerability Response Implementor me 191 Questions with Verified Answers NVD - CORRECT ANSWER National Vulnerability Database CVE - CORRECT ANSWER Common Vulnerability and Exposures ... CWE - CORRECT ANSWER Common Weakness Enumeration CPE - CORRECT ANSWER Common Platform Enumeration Third-Party Vulnerable Entries - CORRECT ANSWER Dictionary of vulns or scan checks based on scanning vendors (Qualys, Tenable, Veracode) What data does a VIT contain? - CORRECT ANSWER Tasks, Attachments, Work Notes, Approvals, Vulnerability Details VR + CMDB allows for the following activities in a single system of record? - CORRECT ANSWER Remediation, Configuration Management/Business Impact, Security Incident Response, Problem Management, Change Management, Orchestrations (Manual response), SLAs IT Remediation Workspace - CORRECT ANSWER Shows all vulnerabilities/RT assigned to me or to a group I belong to Remediation Overview - CORRECT ANSWER Dashboard reporting of all vulns/RT assigned to me or to groups I belong to Vulnerability Manager Workspace - CORRECT ANSWER Breakdown of all vulnerabilities (admin view) Approver Overview - CORRECT ANSWER view of all Exception and FP requests in a dashboard VR Roles: Vulnerability Admin - CORRECT ANSWER complete access to the VR application, Configure VR and rules, Installs all 3rd-party integrations, assigns all VR personas and roles VR Roles: Remediation Owner - CORRECT ANSWER view and update VI's and RT's, view all vulnerabilities and solutions, write access to Notes on the solution record VR Roles: Vulnerability Analyst - CORRECT ANSWER manage VI's and RT's, Assign remediation tasks, monitor remediation Progress VR Roles: CI Manager - CORRECT ANSWER Manages unmatched CIs not in CMDB, Updates discovered items VR Roles: Exception Approver - CORRECT ANSWER approves exceptions, deferrals, and closures of VI's and RT's AVR Roles: Security Champion - CORRECT ANSWER Liaisons between the development group and security managers AVR Roles: App-Sec Manager - CORRECT ANSWER ID and prioritization of vulns, configure integrations, work with security champion and developer to remediate vulns AVR Roles: Developer - CORRECT ANSWER contributor to development of an application, make changes to application to remediate vulns VR Properties: sn_vul.popup - CORRECT ANSWER customization when creating a problem change or security incident in VIT form VR Properties: sn_vul.vulnerable_item.approval_required - CORRECT ANSWER Determines whether an approval process is required to move a vuln item into a terminal state VR Properties: sn_vul.email_to - CORRECT ANSWER specifies the inbox to be used by vulnerability tools (in Security Support Common Scope) VR Properties: sys_properties.list - CORRECT ANSWER complete list of system properties How does VR interact with other SNOW applications: SIEM - CORRECT ANSWER VIT could trigger a SIR How does VR interact with other SNOW applications: Threat Intel - CORRECT ANSWER Threat Intel enriches VIT with threat intel detail How does VR interact with other SNOW applications: GRC - CORRECT ANSWER Track VR activities to demonstrate compliance Vulnerable Item State Approval - CORRECT ANSWER Approvals to change the VIT's state to a terminal state Components to add to Organizations security function: Service Mapping - CORRECT ANSWER correlate SecOps dynamically with key business services so network changes never create security obscurities Components to add to Organizations security function: Event Management and Orchestration - CORRECT ANSWER Improve efficiency and reaction times by automating SecOps activities Components to add to Organizations security function: Performance Analytics - CORRECT ANSWER visualize SecOps data, Cross-referenced with existing data collections Components to add to Organizations security function: GRC - CORRECT ANSWER align security events with organizational risks and controls - automatically appraising other business functions of impact What libraries are the same for IVR and AVR? - CORRECT ANSWER NVD and CWE What libraries are unique for IVR and AVR? - CORRECT ANSWER Third party libraries (Qualys, Veracode, Tenable, etc) What is the table name for the IVR Third-Party Table - CORRECT ANSWER sn_vul_third_party_entry What is the table name for the AVR Third-Party Table - CORRECT ANSWER sn_vul_app_vul_entry When filtering vulnerability feed what does "Recent" display? - CORRECT ANSWER list of recently published vulns When filtering vulnerability feed what does "Modified" display? - CORRECT ANSWER recently published and modified vulns where "recently" = past 8 days What is the governing body for CWE integration? - CORRECT ANSWER MITRE - list of common software security weaknesses for software security tools When is a VIT created? - CORRECT ANSWER when a CVE matches a recorded software for CI What are the key components of the Vulnerable Item (VIT) Table - CORRECT ANSWER does not extend for Task table detections are related and displayed Vuln info from scanner Remediation steps are part of solution management SLA = remediation targets can relate to multiple remediation tasks What is the function of the Remediation Task (RT) Table? - CORRECT ANSWER prioritize VIT and analyze in bulk (automated process) What are the methods for creating a Remediation Task? - CORRECT ANSWER Manually add VITs to task as needed Condition filter (Automation) Filter Group (Automation) What are the key components of the Remediation Task (RT) Table - CORRECT ANSWER Extends from Tasks created from rules or manually platform SLAs can be defined change requests can be initiated/related can be split includes VIT rollups What does the "RollupCalculatorUtil" script do? - CORRECT ANSWER Aggregates the below values: Active VIs Risk Score Risk Rating Max Risk Score Remediation Target Remediation Status How is Risk Score calculated? RT - CORRECT ANSWER rollup calculator How is Risk Rating calculated? RT - CORRECT ANSWER Based on weights and configuration of Risk Score What is the Max Risk Score? RT - CORRECT ANSWER Highest risk score of any active vuln in the selected remediation task What is the remediation target? RT - CORRECT ANSWER soonest remediation target date for all active non-deferred VIs in RT What is the Remediation Status when open? RT - CORRECT ANSWER uses remediation status of the VI used for the target if open What is the Remediation Status when closed? RT - CORRECT ANSWER Target Met = all closed VIs met their target Target Missed = Some VIs missed their target No Target = if no closed items had a target When does the script "RollupCalculatorUtil" run? - CORRECT ANSWER Every 15 Min when change to following VIT State Remediation Target Date membership in a RT When does the severity calculator run after vuln entry? - CORRECT ANSWER every 30min When does the associated vulnerable items refresh? - CORRECT ANSWER every hour Where can you configure NVD integrations? - CORRECT ANSWER Vulnerability Response -> Administration -> Integrations Where can you access the NVD library? - CORRECT ANSWER Vulnerability Response -> Libraries -> NVD In AVR, what kind of scanning does SNOW focus on? - CORRECT ANSWER DAST Scanning What is DAST scanning? - CORRECT ANSWER Dynamic Application Security Testing - detects vulns by performing actual attacks What is SAST Scanning? - CORRECT ANSWER Static Application Security Testing - scans an application's source code directly What is the Application Vulnerability Table name? - CORRECT ANSWER sn_vul_app_vulnerable_item What are the key components of the Application Vulnerability Table (AVIT) Table - CORRECT ANSWER Not connected to VIT table Business rules are separate from VIT no RTs vulnerability state is managed by source app (Veracode) Deep-link back to source Editable Fields: Assignment Group, Assigned to Fields, and Notes How do the scanned applications in AVR integrate? - CORRECT ANSWER Scanned apps correspond to Mapped Application Services in CMDB How do you access the list of scanned applications? - CORRECT ANSWER Application Vulnerability Response -> Administration -> Applications What can you update in the list of scanned applications? - CORRECT ANSWER Department Business Unit Support Group Relationships to technical service add appropriate Security Champions What is the name of the Scanned Application Table? - CORRECT ANSWER (sn_vul_app_scanned_application) is a CMDB table. It extends from (cmdb_ci_appl) What is the name of the Application Vulnerability Entry Table? - CORRECT ANSWER sn_vul_entry What is the name of the Application Vulnerability Integration Table? - CORRECT ANSWER sn_vul_integration What is an Application Vulnerability Item? - CORRECT ANSWER Contains details of each scan detection What is an Application Vulnerability Entry? - CORRECT ANSWER Represents a detection category/CWE from the scanner What does Application Release Details contain and where does it come from? - CORRECT ANSWER App Name, Version, Assigned Teams (Source from scanner) What does Scanned Application represent? - CORRECT ANSWER extends CI and represents and application in CMDB What does the Application Vulnerability Scan Summary Contain? - CORRECT ANSWER scan data, total detections by scan type, policy status What will you need to replicate if building a custom integration in AVR? - CORRECT ANSWER Integration script integration factor script report processor strategy Where can you download plugins for scanners like Qualys and Tenable? - CORRECT ANSWER store.servicenow.com What is the name of the Qualys Plugin? - CORRECT ANSWER Qualys Integration for Security Operations What action should you take after installing the Qualys Plugin? - CORRECT ANSWER Schedule job to query and load Qualys data How does the Qualys integration sync CMDB data? - CORRECT ANSWER Plugin will automatically update SNOW CMDB and add assets discovered by Qualys Will also add asset in SNOW CMDB to Qualys What are the two tasks to perform before integrating the Veracode integration? - CORRECT ANSWER Populate the NVD and CWE table obtain the Veracode API What is the first integration to run for Veracode integration? - CORRECT ANSWER Veracode Application List Integration - populates the scanned application table What will the customer need to update after running the "Veracode Application List Integration" ? - CORRECT ANSWER Department Business Unit Supported Fields Create any Triage rules Where can you access the Qualys integrations to import the vulnerability details once installed? - CORRECT ANSWER Qualys Vulnerability Integration -> Administration -> Primary Integrations Where can you access the Qualys scan to configure how often Qualys data is imported? - CORRECT ANSWER Vulnerability Response-> Vulnerability Scanning -> Rate Limit Definitions What are the key data fields that are pulled from the Qualys integration? - CORRECT ANSWER Host List Host Detection Details KB Ticket List What data does the Host Detection Details contain from the Qualys import? - CORRECT ANSWER Class Name CI Name DNS FQDN IP What Qualys specific host information is imported with the Vulnerability Management Plugin? - CORRECT ANSWER Qualys ID Qualys Host ID adds field "Created by Qualys" What scripts does Qualys use to transform and update the CI? - CORRECT ANSWER QualysUtil QualysSimpleCITransform What is the name of the base table for CMDB that the Qualys transform targets? - CORRECT ANSWER cmdb_ci What happens when the CI lookup flow finds an asset in Qualys it does not have CI details for? - CORRECT ANSWER Placeholder CI is created and designated as unmatched CI What is the IRE API? - CORRECT ANSWER Identification and Reconciliation Engine What does the IRE do? - CORRECT ANSWER Prevents duplicate CIs from being created reconcile CI attributes by allowing only authoritative data sourced to write to CMDB Where can I access the logic SNOW is using when integrating Qualys with CIs? - CORRECT ANSWER CMDB -> CI Lookup RUles What is the SAM? - CORRECT ANSWER Software Asset Management What does the SAM do? - CORRECT ANSWER - Provides information about where the most recent vulnerabilities exist in the infrastructure - leveraged to quickly identify what systems are running that software and address risk Where can I access the Exposure Assessment tool? - CORRECT ANSWER Vulnerability Response -> Vulnerability Scanning -> Exposure Assessment What can the Exposure assessment tool do? - CORRECT ANSWER Create VITs based on specific software Automatically group to RTs Where can I access the Assignment Rules for automated Triage? - CORRECT ANSWER Vulnerability Response -> Administration -> Assignment Rules What do the Assignment rule configurations do? - CORRECT ANSWER Automatically Assign Remediation Tasks to an Assignment group, or Group field when a VIT record is created What can Predictive Intelligence do? - CORRECT ANSWER "Train" the system to automatically assign VITs Where can I access Predictive Intelligence Classification record for VR? - CORRECT ANSWER Predictive Intelligence -> Classification -> Solution Definitions - Record "Vulnerability Item Assignment" ***Requires extensive testing in dev/test before pushing to production What level should assignment of vulnerabilities always be managed - CORRECT ANSWER Remediation Task Level How does SNOW standardize the various scoring systems from vendors or CVSS? - CORRECT ANSWER Normalized Severity Maps module Where can I access the Normalized Severity Maps - CORRECT ANSWER Vulnerability Response-> Administration-> Normalized Severity Maps Where can I go and what can I use to combine severity scores from multiple sources to assist with prioritization of vulnerabilities? - CORRECT ANSWER Vulnerability Calculator Where can I access the Vulnerability Calculator? - CORRECT ANSWER Vulnerability Response -> Administration -> Vulnerability Calculator What are the default Risk Rule Calculator settings? - CORRECT ANSWER Vulnerability Severity (80%) Exploit exists (20%) What are the default risk rules that can be adjusted? - CORRECT ANSWER Normalized CVSS score Exploitability exists Exploitability skill level Exploitability Vector Business Criticality CI exposure (Internal vs external) What are some example fields used in vulnerability calculators and what can vuln calcs do? - CORRECT ANSWER Prioritize and rate impact of VITs based on condition filters Business impact Class of CI Age of VIT Custom fields in VIT When does a calculator rule apply a condition in its list? - CORRECT ANSWER applies first matching rule How should notification rules be applied? - CORRECT ANSWER applied in platform email runs risk of bombarding users What are Remdiation Target Rules for set VITs? - CORRECT ANSWER define the expected timeframe to remediate a VIT (Much like an SLA) What can a vulnerability manager configure for a Remediation Target Rule? - CORRECT ANSWER Remediation target Reminder Targe Reminder and notification recipients How can someone close a VIT? - CORRECT ANSWER Manually When scanner detects remediation Set up auto-close parameter to handle stale detections What is the name of Assignment Rules table? - CORRECT ANSWER sn_vul_assignment_rule What is the name of Remediation Target Rules table? - CORRECT ANSWER sn_vul_ttr_rule What is the name of Vulnerability Calculator table? - CORRECT ANSWER sn_vul_calculator_group What are the calculator weights for AVR? - CORRECT ANSWER Vulnerability severity OAWSP top 10 SANS top 25 (software errors) Where can you configure SLAs? - CORRECT ANSWER Service Level Management -> SLA -> SLA Definitions What are the 3 manual methods for vulnerability grouping strategires - CORRECT ANSWER Manually Grouping by Condition Using Filter Groups What are the three advantages of vulnerability grouping when remediating VITs in bulk using Tasks? - CORRECT ANSWER Create tasks using default rule (specific Vuln) organize by department/assignment group create more monitoring tasks comprised of other tasks Can VITs belong to more than one RT? T/F - CORRECT ANSWER True What do Remediation Task Rules apply to VITs when grouping? - CORRECT ANSWER - Identify which VITs to include in the task - Determine how to group them based on select key values - Determine the Assignment Group for the Remediation Task What two main options can be used for grouping? - CORRECT ANSWER - CI identified on VIT - Fields in the VIT (QID, CVE, etc) What role provides admin access in VR? - CORRECT ANSWER sn_vul.admin What are the fields used in condition builder? - CORRECT ANSWER -Field (based on table) - Operator (based on field type) - Value (can be text field, T/F, or Choice List) What is the name of the Vulnerable Items Table - CORRECT ANSWER sn_vul_vulnerable_item What benefits does the Vulnerability Solution Management module provide? - CORRECT ANSWER -Identify the Highest-impact solutions to active vulns -track solution deployment progress -prioritize remediation efforts What does the Vulnerability Solution Management module provide? - CORRECT ANSWER - identifies top solutions by risk reduction and superseded solutions - tracks deployment progress across SLAs provides reporting metrics for dashboards What does the "Unified navigation ->Solution" page allow you to do? - CORRECT ANSWER - automatically correlate MS and Red Hat solutions to vulns - identify remediation actions and prioritize them by greatest reduction in vuln risk What two teams should collaborate on the "Vulnerability Solution Management" module? - CORRECT ANSWER - Vulnerability Assessment (Security) - Patching Management (IT) What happens when an object is marked as a FP? - CORRECT ANSWER - State changes to closed - substate changes to FP Can you bulk edit Remediation Tasks as FPs? (T/F) - CORRECT ANSWER True What actions can be performed when the Vulnerable Item State approval Workflow is triggered? - CORRECT ANSWER - Reopen - Delete - Update "Date Until" field which marks when FP expires What is the best way to leverage the exception approval process in VR? - CORRECT ANSWER Leverage GRC policy exception management capability for increased visibility and audit purposes What happens when an exception request is raised in Exception Management Workflow? - CORRECT ANSWER Status changes to in review and two exception approvers will review the request What benefits does combining GRC+VR provide? - CORRECT ANSWER - Performance assessment can be done based on request - exceptions requested based on policy or control - Configure approvals to be triggered automatically based on risk rating, policy, or control When are Exception Rules allowed in VR - CORRECT ANSWER Only when non-GRC is enabled What factors can you configure about Exception rules? - CORRECT ANSWER - set dates - set conditions - set approval groups What benefits does combining VR + Change Management provide? - CORRECT ANSWER - easier to create change request for remediating vulns - Help It automate remediation tasks What are the use cases for combining VR + Change Management? - CORRECT ANSWER - Create comprehensive CRs to RTs - Associate RT to existing CR - Split Groups (RT carve-out) - State-Sync (automatically resolve RT when CR implemented) Where to access Change Requests? - CORRECT ANSWER Remediation Task -> Change Request button What functionality can you perform with a Change Request? - CORRECT ANSWER - Change Scope (all or based on VIT conditions) - Type of Change (Standard, Normal, Emergency) - Add CIs to Change What happens when a Change Request is created from a subset of VITs in an RT? - CORRECT ANSWER - Items will be moved to new RT - Note is created in the activity log What state will the vulnerabilities change to when a Change Request is created? - CORRECT ANSWER Awaiting Implementation (or Deferred) What state will the vulnerabilities change to when a Change Request is implemented? - CORRECT ANSWER Resolved What state will be used when multiple Change Requests are associated with the RT? - CORRECT ANSWER System will use Change Request in earliest state to determine RT State What is the table used for Vulnerability Group Change Requests? - CORRECT ANSWER sn_vul_m2m_vg_change_request What is Flow designer used for? - CORRECT ANSWER Creates automation for specific vulnerabilities when conditions are met What is the name of the Remediation Task Table? - CORRECT ANSWER sn_vul_vulnerability Who are the three audiences to consider when building dashboards? - CORRECT ANSWER - CIO/CISO - Managers - Analysts What are the dashboard requirements for CIO/CISO? - CORRECT ANSWER - High-level Overviews - Single, clear indicators of organizational health and function What are the dashboard requirements for Managers? - CORRECT ANSWER - Aggregations for priority and workload - Drill-down to granularity - time period views What are the dashboard requirements for Analysts? - CORRECT ANSWER - up-to-the-minute views - Clear prioritizations - Granularity How to enable Performance Analytics in VR? - CORRECT ANSWER Download plugin - Performance Analytics - Content Pack - Vulnerability Response What should you use when PA is not enabled at client? - CORRECT ANSWER Vulnerability Response -> Remediation Overview Where can you access the baseline reports for VR - CORRECT ANSWER - sys_metadata.list - Filter results by Application = VR and Class = Report What are the benefits of Performance Analytics vs Reporting? - CORRECT ANSWER - trending information - can act on performance degradation - take action in real time - allows analysis to enable timely decision making - provide insights into leading indicators that influence health What benefits does basic reporting (Non-PA) provide? - CORRECT ANSWER - analysis of what happened - measures lagging indicators (output from process) What is the table for "Vulnerability Item Task"? - CORRECT ANSWER sn_vul_m2m_item_task What is the table for "Remediation Task"? - CORRECT ANSWER sn_vul_vulnerability What is the table for "Vulnerable Item"? - CORRECT ANSWER sn_vul_vulnerable_item What is the table for "Related Business Services"? - CORRECT ANSWER sn_vul_m2m_ci_services What is the table for "Vulnerability Entry"? - CORRECT ANSWER sn_vul_entry What are "Vulnerability Performance Analytic Indicators"? - CORRECT ANSWER statistics that businesses track to measure current conditions and forecasts (KPIs) What is a "Leading Indicator"? - CORRECT ANSWER focus on input that is required to achieve an objective (Hard to measure but easier to influence) What is a "Lagging Indicator"? - CORRECT ANSWER Measure the output of your activities (most commonly used) What is the name of the admin role for Performance Analytics? - CORRECT ANSWER pa_admin What is a Vulnerability Item Task? - CORRECT ANSWER steps to contain/work through process to close out vulnerability What are Remediation Tasks? - CORRECT ANSWER Grouping of vulnerabilities What role allows one to create and update VITs and Vulnerability Groups? - CORRECT ANSWER sn_vul.vulnerability_write What role allows one to view vuln app menu and modules, vuln software and VITs? - CORRECT ANSWER sn_vul.vulnerability_read What role allows you to run scheduled jobs, role given to system user for integrations? - CORRECT ANSWER sn_vul.vr_import_admin What role allows you to manage specific remediation items assigned to you? - CORRECT ANSWER sn_vul.remediation_owner What role allows you to access CISO dashboards and all vulnerability details regardless of roles? - CORRECT ANSWER sn_vul.vulnerability_ciso What are Discovery Models? - CORRECT ANSWER software models used to help normalize the software you own by analyzing and classifying models to reduce duplication What role is required to define a VR email template - CORRECT ANSWER sn_vul.vulnerability_admin What does the Asset Management Model enable? - CORRECT ANSWER allows you to compare vulnerability data to CIs and software identified as VRs Where are change request created? - CORRECT ANSWER Vulnerability Group Record What are the application scopes in Vulnerability Response (2)? - CORRECT ANSWER - Vulnerability Response (sn_vul) - Security Support Common (sn_sec_cmn) What workflow implements VIT and Vuln Group approvals? - CORRECT ANSWER Vulnerable Item State Approval Which script includes controls that require Vulnerable Item/Group approval - CORRECT ANSWER VulnerabilityStateChangeManager Which script implements Vulnerability State Change Approval? - CORRECT ANSWER VulnerabilityChangeApproval What roles come with Qualys Plugin? - CORRECT ANSWER - sn_vul_qualys.admin - sn_vul_qualys.read - sn_vuln_qualys.user What does the Configuration Compliance Plugin enable? - CORRECT ANSWER uses results from 3rd-party Secure Configuration Assessment (SCA) Scanner integrations to verify CI compliance with security or corporate policies (default passwords, remote access, etc) What are the roles assigned with Configuration Compliance (4)? - CORRECT ANSWER - sn_vulc.admin - sn_vulc.read - sn_vulc.write - sn_vulc.remediation_owner What are the VIT and Vuln Group States? - CORRECT ANSWER -Open - Under investigation - Awaiting implementation - In Review - Resolved - Deferred - Closed What are severity maps used for? - CORRECT ANSWER converting 3rd-party severity into SNOW severity (Normalized Severity Maps) What ways can Vulnerability Group assignment occur? - CORRECT ANSWER - Assignment rules - vulnerability calculator - vulnerability group Which role is required to manage security tags? - CORRECT ANSWER Security Support Common admin (sn_sec_cmn.admin) What are security tags? - CORRECT ANSWER metadata and/or controls to define who should have access to specific types of security WHat system property that defines CI classes to ignore when running security operations CMDB CI lookup rules? - CORRECT ANSWER cn_sec_cmn.ignoreCIClass What are the three SecOps tiers? - CORRECT ANSWER - Standard - Professional - Enterprise What is the application release table? - CORRECT ANSWER sn_vul_app_release [Show More]
Last updated: 2 years ago
Preview 1 out of 22 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$11.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Oct 09, 2023
Number of pages
22
Written in
All
Additional information
This document has been written for:
Uploaded
Oct 09, 2023
Downloads
0
Views
59