PCNSA Content ID Exam 34 Questions with Verified Answers,100% CORRECT
Document Content and Description Below
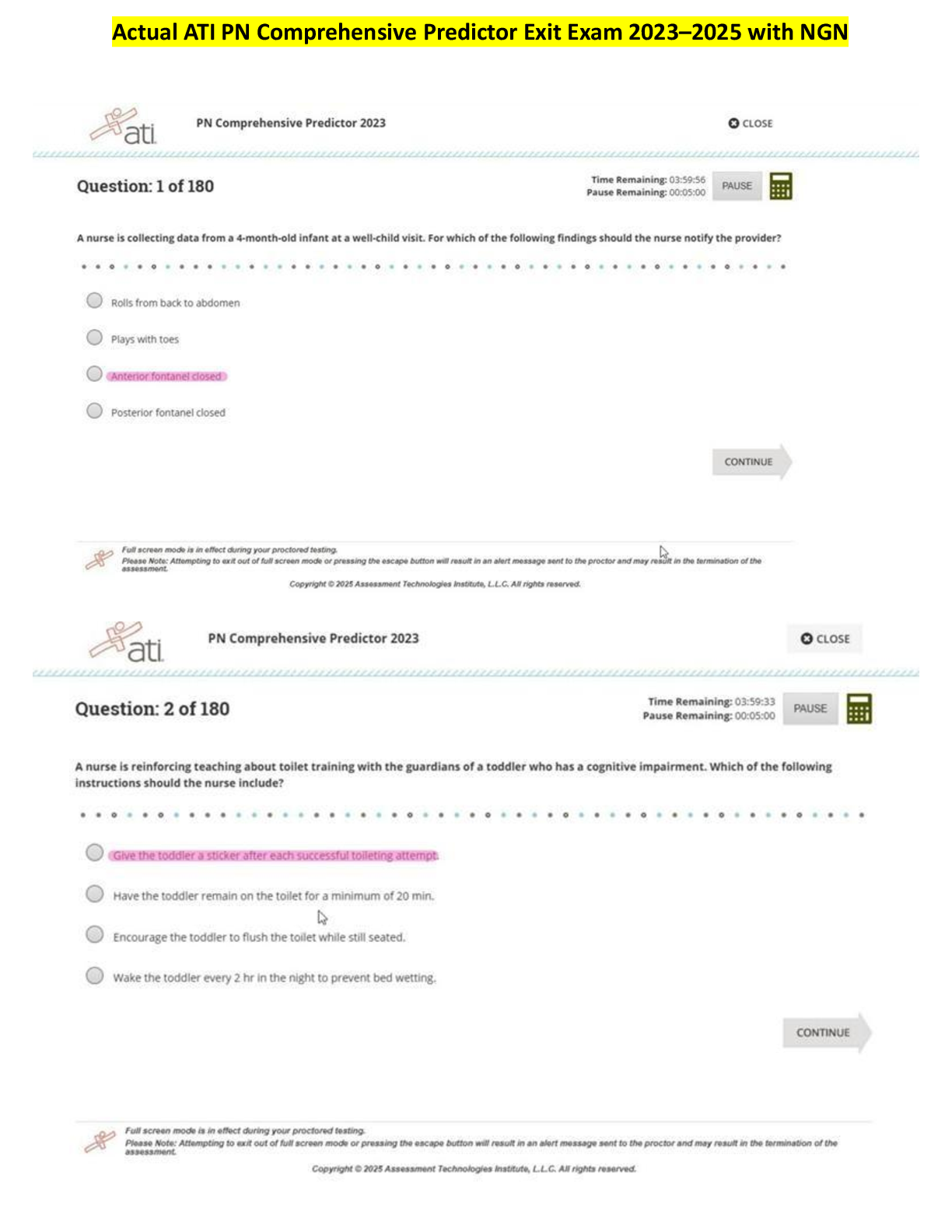
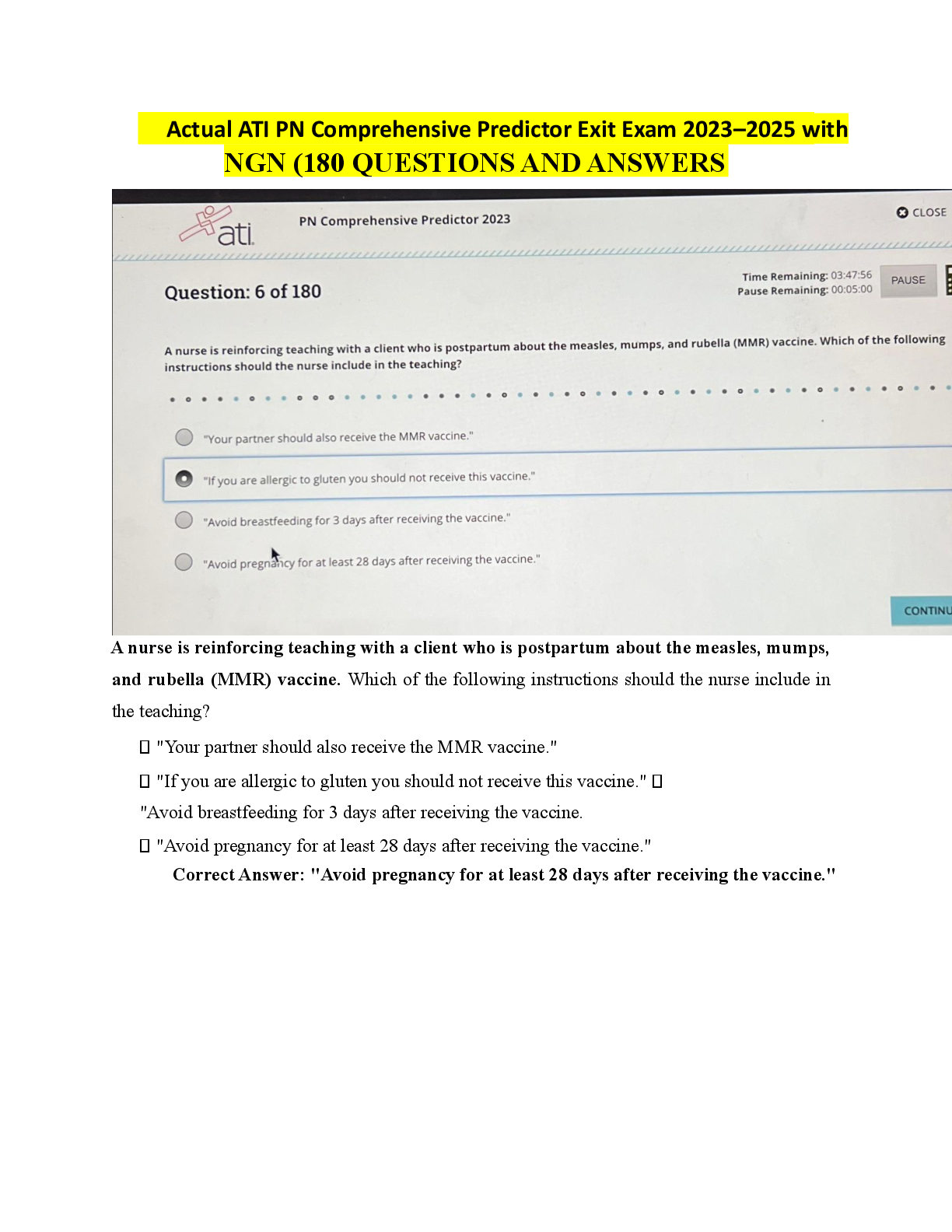
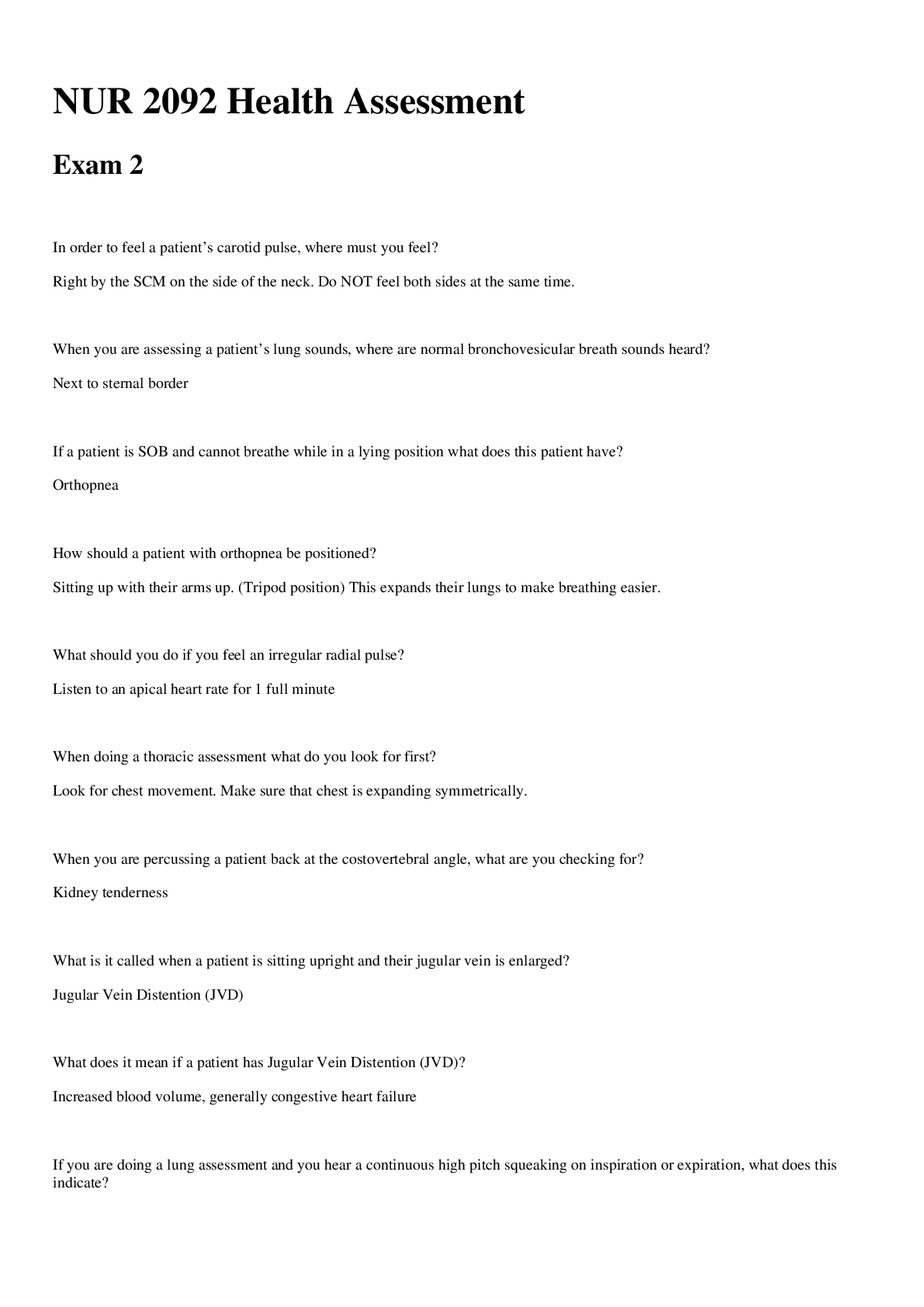
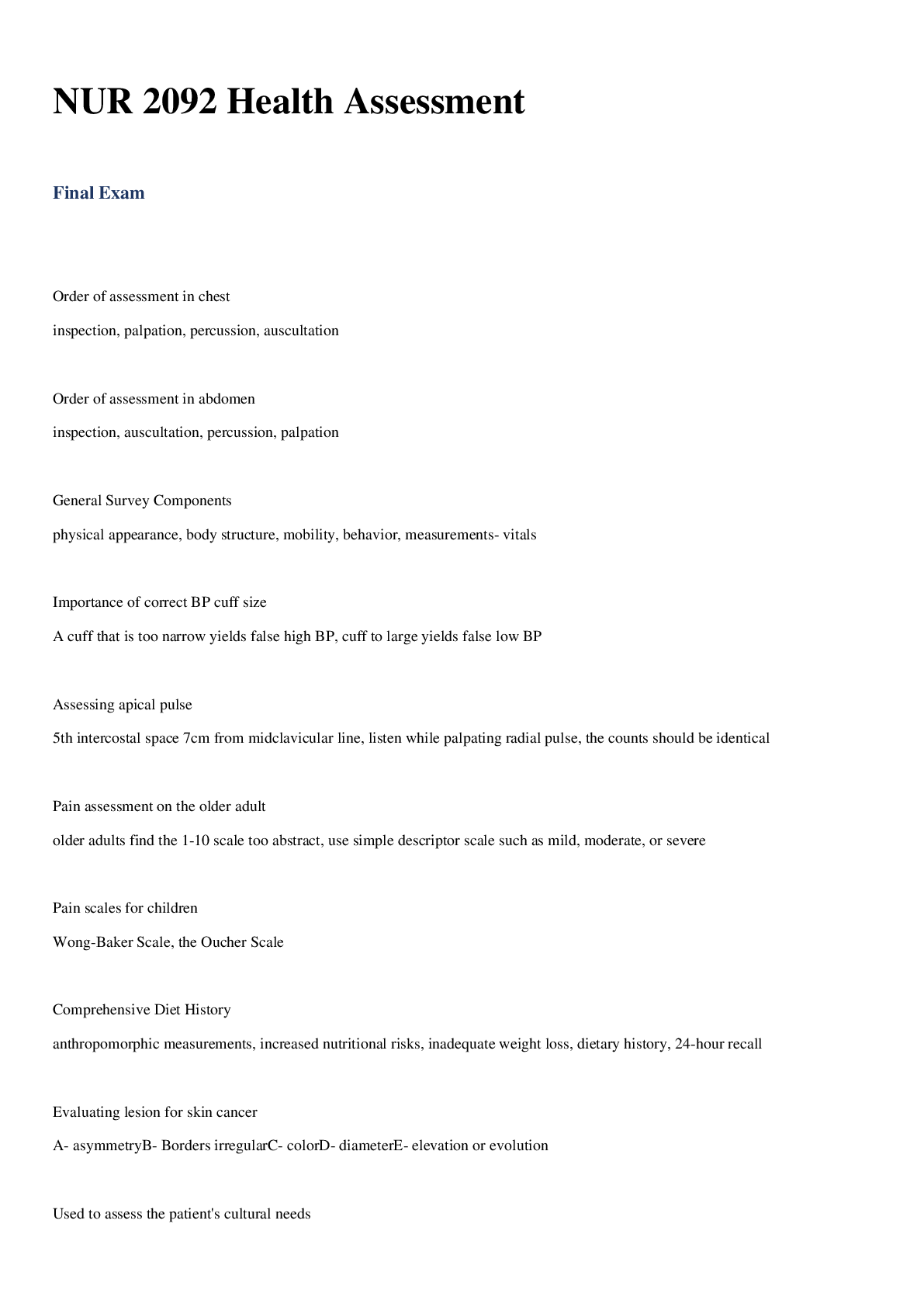
PCNSA Content ID Exam 34 Questions with Verified Answers Content-ID feature - CORRECT ANSWER includes a threat prevention engine and policies to inspect and control content traversing the firewall ... Security Profiles - CORRECT ANSWER objects that are added to security policy rules configured with an action of "allow"... represent additional security checks to be performed on allowed network traffic Antivirus Profile - CORRECT ANSWER Detects infected files being transferred with the application Anti-spyware profile - CORRECT ANSWER detects spyware downloads and traffic from already installed spyware Vulnerability Protection profile - CORRECT ANSWER detects attempts to exploit known software vulnerabilities URL Filtering profile - CORRECT ANSWER classifies and controls web browsing based on content File Blocking profile - CORRECT ANSWER tracks and blocks file uploads and downloads based on file type and application Data Filtering Policy - CORRECT ANSWER identifies and blocks transfer of specific data patterns found in network traffic Wildfire Analysis policy - CORRECT ANSWER forwards unknown files to Wildfire service for malware analysis Security Profile Group - CORRECT ANSWER set of security profiles treated as one unit to simplify adding multiple security profiles to a security policy rule Threat Log - CORRECT ANSWER records antivirus, anti-spyware, and vulnerability threats discovered by Security Profiles Pre-defined Vulnerability Protection Profiles - CORRECT ANSWER default: applies default action to all client and server critical, high-severity, and medium-severity events. Typically used for proof of concept or first-phase deployments strict: applies "reset-both" response to all client and server critical, high-severity, and medium-severity events and uses default action for all client and server informational and low events. Used for out-of-the-box protection with recommended block of critical, high, and medium threats Vulnerability Exceptions - CORRECT ANSWER can override a rule's default action responses for one or more threat signatures, or IP addresses Default Antivirus Security Profile - CORRECT ANSWER out-of-the-box profile, read-only. default action according to different protocols used by applications to transfer files Wildfire action configured based on signatures delivered by WildFire 'Alert' action allows network traffic but creates an entry in the threat log. "reset-both" resets the TCP connection between server and client or drops UDP packets SMTP 541 error message - CORRECT ANSWER sent by firewall as part of the "alert" action when a virus is detected. Tells the mail server not to retry sending the message Virus exceptions - CORRECT ANSWER created to handle false positives. Threat ID added to virus exception tab DNS Signatures - CORRECT ANSWER available through a real-time, on-demand cloud database that can be used to identify potentially malicious domains and unusual DNS query patterns available actions are 'allow', 'alert', 'block', and 'sinkhole', as well as single packet or extended packet captures when a signature is detected in network traffic DNS Sinkhole operation - CORRECT ANSWER used to quickly identify infected hosts on the network, firewall forward DNS queries to a sinkhole IP address where it does not get fowarded any further. Traffic sent to the sinkhole is logged. Infected hosts with sinkhole events are identified in the Threat log, or the use of reports File blocking - CORRECT ANSWER purpose is to prevent the introduction of malicious data, and exfiltration of sensitive data. Actions = alert, continue, and block. an 'alert' action allows the file transfer but logs it in the Data Filtering log Data Filtering Log - CORRECT ANSWER displays list of files blocked by file blocking profiles. Source is the system that sent the file, destination is the system that received the file.. Continue Response Page - CORRECT ANSWER Continue action requires user permission to complete a file transfer. Operates only when paired with 'web-browsing' application Blocking multi-level encoded files - CORRECT ANSWER firewall can decode a max of four levels... file blocking profile can block files encoded more than four times (select multi-level-encoding and set action to 'block') Data Pattern - CORRECT ANSWER used to define information types for Data Filtering profiles... can use predefined pattern (CC#/social security no), regular expression and file properties Telemetry and Threat Intel - CORRECT ANSWER opt-in feature to send sanitized threat information to Palo Alto, such as DNS monitoring for malicious C2 traffic Denial-of-Service Protection - CORRECT ANSWER Mitigates 3 and 4 protocol-based DoS attacks by using packet header info to detect threats rather than a signature. Not linked to a security policy. Zone Protection Profile - CORRECT ANSWER DoS protection applied to the edge of the network. Protects against most common flood attacks (SYN flood, UDP, ICMP flood). Determines packet rates and actions according to a specified threshold. *Enabled on a per-zone basis, each zone can only have one Zone Protection Profile assigned* Alarm rate - determines when an alert should be triggered Activate - threshold where a mitigation response should be triggered (Random Early Drop RED by default) Maximum - threshold where all packets are dropped End host protection - CORRECT ANSWER provides flexible rules and matching criteria to protect destination zones or specific end hosts exposed to the internet (web servers, DNS servers, etc) Zone Protection - Reconnaissance protection - CORRECT ANSWER protects against TCP/UDP port scans and ICMP/TCP/UDP host sweeps. always applied to the ingress interfaces of the protected zone. adjusted using interval and threshold values before an action is triggered Zone protection - Packet-based attack protection - CORRECT ANSWER blocks packets based on protocol options or malformed packets Zone protection - protocol protection - CORRECT ANSWER applies to L2 and virtual wire zones... allows you to control which non-IP protocols are allowed to flow between or within these security zone types DoS Protection Policy - CORRECT ANSWER Defines match criteria and action for blocking DoS attacks. If action is set to "Protect", then matching traffic is controlled by the limits set by the DoS Protection Profile DoS Protection Profile - CORRECT ANSWER Aggregate profile - enables the creation of a maximum session limit for all connections matching a DoS Protection poilcy rule Classified profile - enables creation of a session limit that only applies to a single IP address Flood Protection - CORRECT ANSWER detects and prevents attacks where the network is flooded with packets, resulting in too many half-open sessions or services being unable to respond to every request Resources protection - CORRECT ANSWER detects and prevents session exhaustion attacks... helps prevent attacks where many hosts are used to establish as many fully established sessions as possible to consume system resources (i.e. DDoS attack) [Show More]
Last updated: 2 years ago
Preview 1 out of 5 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Also available in bundle (1)
Click Below to Access Bundle(s)

ALL PCNSA Exam (21 Sets) Questions with Verified Answers,100% CORRECT
PCNSA Exam 59 Questions with Verified Answers,PCNSA Flash Cards Exam 117 Questions with Verified Answers,PCNSA Exam 84 Questions with Verified Answers,PCNSA Exam 132 Questions with Verified Answers,PC...
By Nolan19 2 years ago
$35
21
Reviews( 0 )
$8.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Oct 09, 2023
Number of pages
5
Written in
All
Additional information
This document has been written for:
Uploaded
Oct 09, 2023
Downloads
0
Views
116