PCNSA Exam 40 Questions with Verified Answers,100% CORRECT
Document Content and Description Below
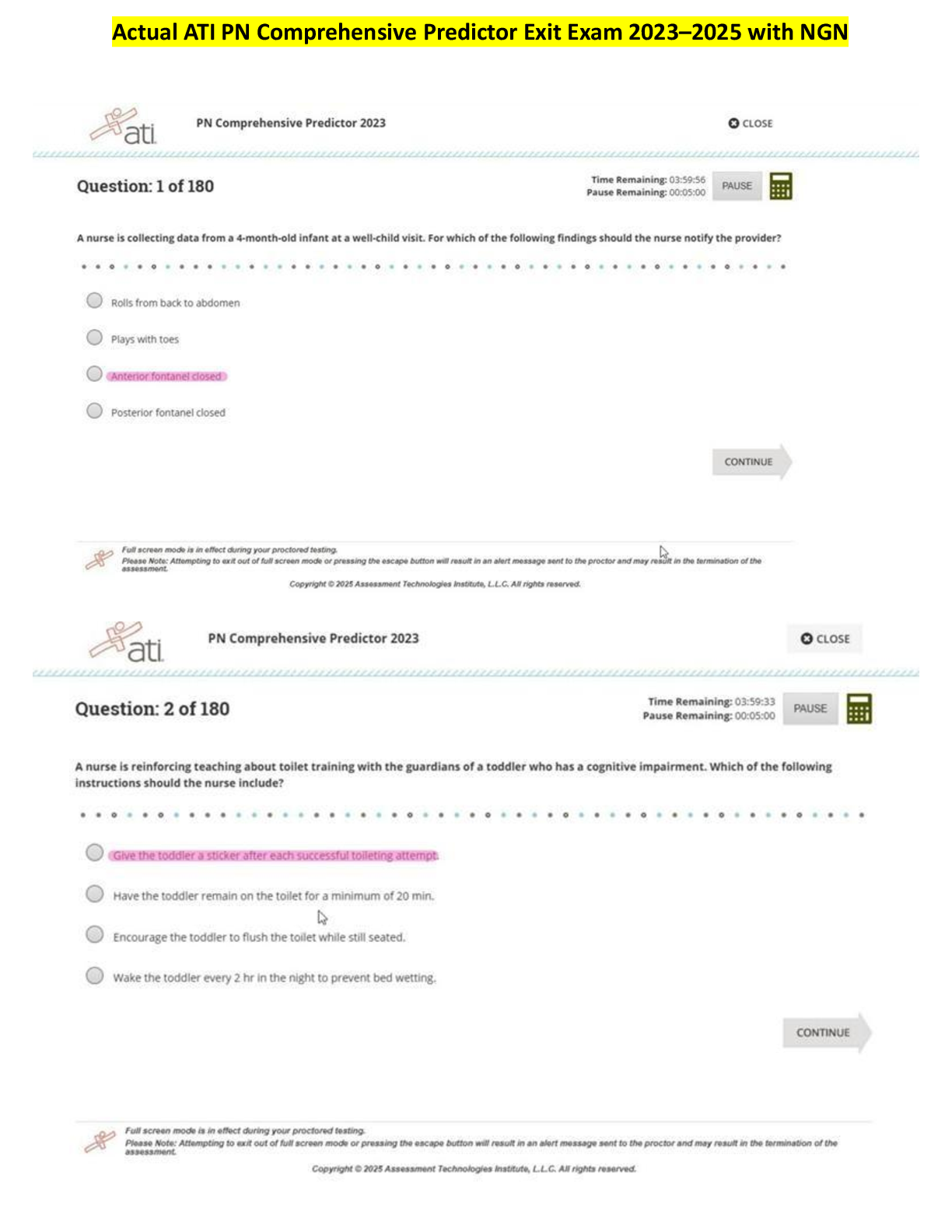
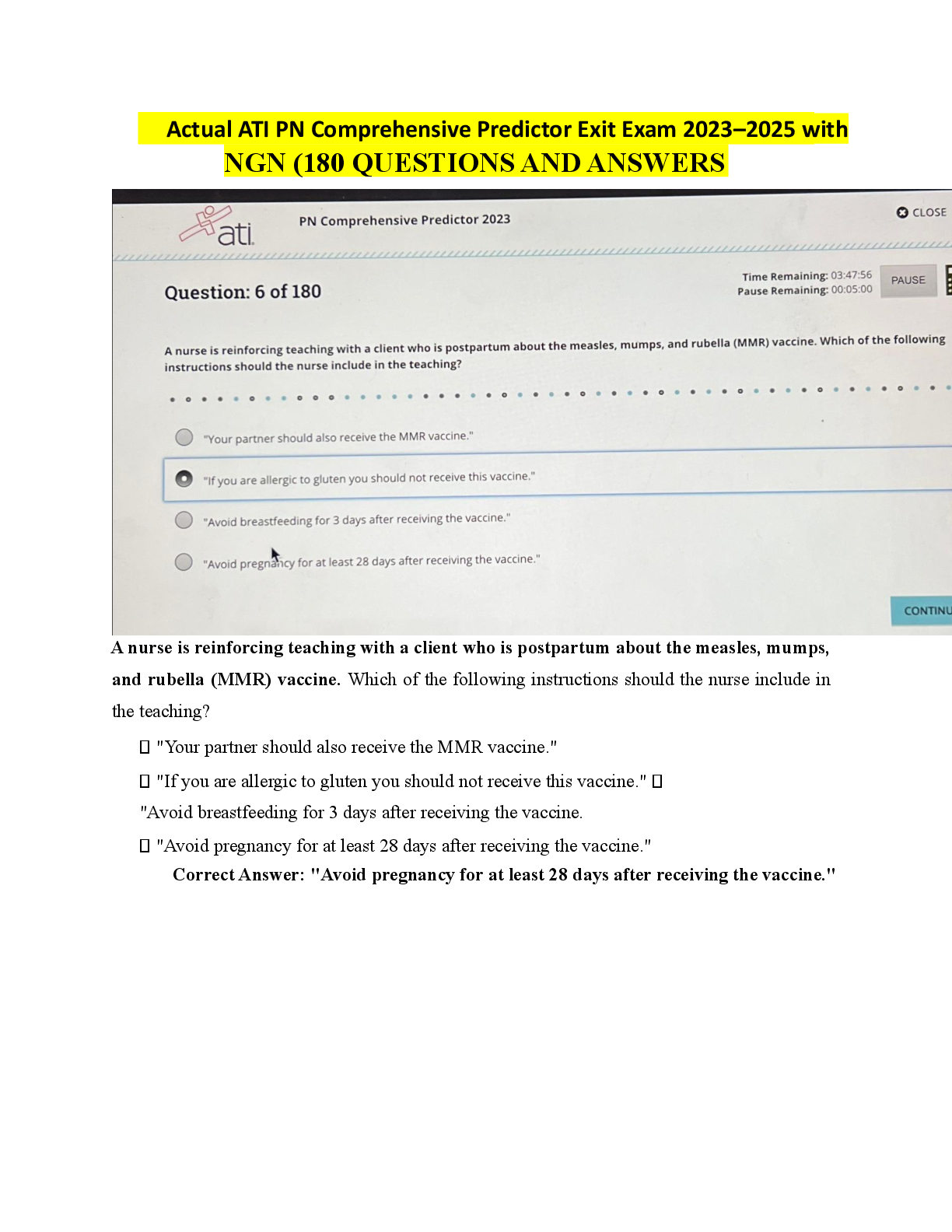
PCNSA Exam 40 Questions with Verified Answers Default Antivirus Profile protocols - CORRECT ANSWER -smtp -smb -ftp -imap -pop3 -http/2 Antivirus profile actions - CORRECT ANSWER -allow -al ... lert (Default) -drop -reset client -reset server -reset both Rule Usage tab in Security Policy Rule displays the rule's usage, what four important information you will find in Rule Usage tab? - CORRECT ANSWER -Basics -Applications -Activity -Traffic A Virtual Wire object is capable of blocking or allowing traffic based on? - CORRECT ANSWER 802.1Q VLAN tag values When new applications are added to the App-ID database, application groups are always automatically updated ? - CORRECT ANSWER No! After updating an application group, you need to issue a firewall commit. Application groups allow you to create a logical group of applications that can be added to the policy rules of Security and QoS. When you want to treat a set of applications similarly in a policy, an application group is used. Ultimately, application groups simplify the administration of the rule bases. Instead of applying multiple rules to the same list of applications, you can create an application group and apply multiple rules to that group. In a TCP exchange how many packets does it take to identify the application? - CORRECT ANSWER Four or five What are the methods of managing the Palo Alto firewall ? - CORRECT ANSWER -Web interface -Panorama -SSH/Console CLI -Rest XML API The first classification of network traffic is based on its IP and port address. The Security Policy is consulted by the firewall to decide whether to allow or block traffic based on the IP address and port. What is application set to during this initial Security Policy check? - CORRECT ANSWER ANY . The application is set to "any" during this initial Security Policy check. If traffic is allowed, a session is generated and the App-ID then looks for a signature for the application. Which are all the security profiles ? - CORRECT ANSWER ▪ Antivirus: Detects infected files being transferred with the application ▪ Anti-Spyware: Detect downloads of spyware and traffic from spyware already installed ▪ Vulnerability Protection: Detects attempts at exploiting known vulnerabilities in applications ▪ URL Filtering: Classifies and controls content-based web browsing ▪ File Blocking: Based on file type tracks and blocks file uploads and downloads ▪ Data Filtering: Identifies and blocks the transfer of specific patterns of data found in network traffic ▪ WildFire Analysis: Forward unknown files for malware analysis to the WildFire service -DoS protection What is telemetry ? - CORRECT ANSWER Enables the firewall to collect and exchange information regularly with Palo Alto Networks about applications, threats and system health. What are two approaches to mitigate DoS attacks? - CORRECT ANSWER 1.Zone-Based Protection - A broad-based comprehensive DoS template at the edge to prevent the enterprise network from DoS attacks. It acts as a first line of defense for the network. 2.End Host Protection (DoS Rule base and DoS Profiles) - is a flexible policy rule base that provides protection of specific end hosts (web servers, DNS servers, user subnets), which are critical and prone to DoS attacks. In which Security Policy rule type you can not define destination zone? - CORRECT ANSWER Intrazone rule. Three types of rules can be specified in the Security Policy. Whether a rule applies to traffic within a zone, between zones, or both is defined by each rule form. For all matching traffic within the defined source zones, the Intrazone rule applies. A destination zone for an intrazone rule can not be specified. For all matching traffic between the specified source and destination zones, an interzone rule applies. A universal rule applies in the defined source and destination zones to all matching interzone and intrazone traffic. Protection is also required for traffic inside the network, as this is where the malicious lateral movement techniques can take place. This traffic is referred to as? - CORRECT ANSWER Protection is required from traffic entering the network from external locations where the egress point is the perimeter (known as "north-south" traffic). Protection is also required for traffic inside the network, as this is where the malicious lateral movement techniques can take place. This traffic is referred to as "east-west" traffic. What are three methods of replacing a Port-Based Rule to Application-based rule? - CORRECT ANSWER The Create Cloned Rule method is the safest way to migrate rules. Create Cloned Rule - New Cloned application-based rule is placed directly above the port-based rule. Add to Rule - Firewall replaces port-based rule with application-based rule. Must manually configure as application-default. Match Usage - Copies all applications under Apps Seen to Apps on Rule. To which item you apply Zone Protection Profiles? - CORRECT ANSWER Ingress Interface The firewall provides Denial-of-Service (DoS) protection that mitigates protocol-based attacks on Layer 3 and 4. DoS protections are packet-based instead of signature-based. Zone protection always is applied to the ingress interfaces in the protected zone, regardless of the zone where the destination hosts are located. Rather than a signature DoS protection uses packet header information to detect threats. DoS protection is not linked to Security policy. Is DoS protection linked to Security Policy ? - CORRECT ANSWER No In Source NAT configuration Security policy rule matches the packet based on the original pre-NAT source and pre-NAT destination addresses, and which zone? - CORRECT ANSWER The post NAT destinazion zone. Security policy rule is enforced after the NAT policy rule is evaluated but before the NAT translation is applied. A Security policy rule matches the packet based on the original pre-NAT source and destination addresses, but matches the post-NAT destination zone. How you can configure a Layer 3 interface ? - CORRECT ANSWER A Layer 3 interface may be configured with one or more static IP addresses or as a DHCP client. The firewall can be configured to be a Point-to-Point Protocol over Ethernet (PPPoE) termination point to support a DSL modem connection. In which format traffic logs can be exported? - CORRECT ANSWER CSV An administrator needs to make sure that no other administrators are able to make any changes while implementing very important modification. Which commit the administrator needs to activate? - CORRECT ANSWER -Commit lock The PAN firewall can be accessed at the same time by multiple administrators. An administrator can choose to take either a Commit lock that prevents another administrator from committing, or a Config lock that prevents changes to candidate configuration. Instead of taking commit locks, you can use admin-level commit. In which Next Generation Firewall plane is CPU and RAM located? - CORRECT ANSWER Control plane Telemetry is an opt‐out feature ? - CORRECT ANSWER False Telemetry enables your firewall to periodically collect and share information about applications, threats, and device health with Palo Alto Networks. Opt-in feature; nothing selected by default Globally enhances threat protection Can preview data sent to Palo Alto Networks Destination NAT is mostly used to enable hosts on the public (external) network access to private (internal) servers ? - CORRECT ANSWER True Configuring NAT can take two forms: source NAT and destination NAT. Source NAT is translation of traffic originating on a private network and being forwarded to the Internet. Destination NAT is translation of traffic coming from the internet to the local private network The default logging behavior is to log only at the end of the session. Why would an administrator enable logging at the start of the session? - CORRECT ANSWER Troubleshooting Logging at the start of the session, is used for troubleshooting purposes only in the short term. The main disadvantage with logging session start and session end, is the additional load on the CPUs of the management plane and the additional storage space needed for the log entries. What is NOT available actions for traffic that matches an Antivirus Profile rule? - CORRECT ANSWER Block IP In Antivirus Profiles other than the default profile, you can modify the Action and WildFire Action: ▪ Allow: Permits the traffic without logging ▪ Alert: Generates a log entry and permits the traffic ▪ Drop: Discards the traffic and generates a log entry ▪ Reset Client: For TCP, resets the client-side connection. For UDP, drops the connection. ▪ Reset Server: For TCP, resets the server-side connection. For UDP, drops the connection. ▪ Reset Both: For TCP, resets the connection on both the client and server. For UDP, drops the connection. ▪ Block IP: Blocks is not Antivirus Profile rule action. File blocking activity is logged to the Threat log ? - CORRECT ANSWER File blocking activity is logged to the Data Filtering log. A File Blocking Profile allows you to block the downloading or uploading of prohibited, malicious, and suspect files from your network. The goal is to prevent malicious data from being introduced and confidential data from being exfiltrated. By default, inter-zone traffic is allowed by the PAN-OS security policy, allowing devices in the same zone to communicate freely with each other. Intra-zone traffic, is denied by default. - CORRECT ANSWER False Intra-zone traffic (Intra-zone=Same zone) is allowed by the PAN-OS security policy, allowing devices in the same zone to communicate freely with each other. Interzone (Inter-zone=Different zone) traffic, is denied by default. Zone names have no predefined meaning or association with security policy. Descriptive zone names should be used. A zone is a logical grouping based on your network's common type of traffic. There is no relation to the physical location of a zone and its traffic. In reality, throughout your company, a single zone can reside at various locations. If you know the admin account password, what command can be used to reset a firewall to its default factory settings? - CORRECT ANSWER request system private-data-reset Use the request system private-data-reset command in the PAN-OS CLI to remove all logs and restore the default configuration. When this command is performed, all logs will be deleted and the configuration will return to the default factory state. It will restart the system and then reset the data. In a single physical Palo Alto Networks firewall, Virtual Systems, or vsys, are separate logical firewall instances. In which firewall series, virtual systems (vsys) are NOT supported? - CORRECT ANSWER PA 800 SERIES Each virtual system is an isolated, separately managed firewall whose traffic is completely isolated from other virtual systems' traffic. Virtual systems are supported on the PA‐3x00, PA‐5x00, and PA‐7x00 Series firewalls. Network traffic during a session will shift from one application to another ? - CORRECT ANSWER True During a session's lifetime, network traffic will shift from one application to another. App-ID cannot identify the traffic from only a TCP handshake. Even after completing the TCP three-way handshake, the firewall would report insufficient data. However, App-ID will report the application as web-browsing when an HTTP GET is detected. There are six Dynamic Profiles with predefined privileges labeled superuser, superuser (read only), and device administrator, device administrator (read only). What's the other two dynamic profiles ? - CORRECT ANSWER -Virtual System Administrator - Virtual System Administrator (read only) There are six Dynamic Profiles with predefined privileges labeled superuser, superuser (read only), and device administrator, device administrator (read only), and if your firewall is capable of running virtual systems, virtual system administrator, virtual system administrator (read only). Apart from some roles being read-only, the key differences are device administrator cannot manage administrator accounts or create new virtual systems, and a virtual system administrator can manage only virtual systems assigned to them. A brief overview of the predefined functions is given below: ▪ superuser: All access to all options of the firewall ▪ superuser (read only): Read-only access to all options of the firewall ▪ device administrator: Full access to the firewall except for creation of virtual systems and administrative accounts ▪ device administrator (read only): Read-only access to the firewall except for viewing other administrative accounts ▪ virtual system administrator: Full access to a specific virtual system ▪ virtual system administrator (read only): Read-only access to a specific virtual system What two predefined read-only Vulnerability Protection Security Profiles are included on Palo Alto Networks firewalls? - CORRECT ANSWER -Default -Strict Palo Alto Networks firewalls include two predefined, read-only Vulnerability Protection Security Profiles. These profiles contain rules that configure the actions taken by a firewall when it detects malware known to exploit system vulnerabilities of different severity levels and types. Vulnerability Protection Profiles: default: This profile applies the "default" behavior to all critical, high-severity, and medium-severity events for the client and server. The default profile is usually used for first-phase of deployments. strict: This profile applies the "reset-both" response to all critical, high-severity, and medium-severity spyware events of the client and server. What feature does the security policy set for the application to be allowed on the standard ports associated with the application? - CORRECT ANSWER Application-default Traditional firewalls categorize traffic by port and protocol, which was a satisfactory mechanism at one point to protect the perimeter of the network. However, by hopping ports, using SSL and SSH encrypted traffic, hopping through port 80, or using non-standard ports, today's applications can easily bypass a port-based firewall. PCNSA Exam 40 Questions with Verified Answers The firewall by default implicitly permits intra-zone traffic and implicitly denies inter-zone traffic ? - CORRECT ANSWER True The firewall implicitly permits intra-zone traffic by default and implicitly denies inter-zone traffic. By default, after all explicit administrator-defined firewall rules are examined and there is no match for traffic, the two implicit rules are processed. The interzone-default rule removes the need to create a rule that blocks all traffic that the Security Policy does not explicitly allow. When managing security risks and using the Cyber-attack Lifecycle model, in which stage attackers will try to create privileged operations, such as retaining access, persistence, and escalating privileges? - CORRECT ANSWER Installation The cyber-attack lifecycle is a set of events that an attacker goes through to penetrate and exfiltrate information from a network. In this lifecycle, a block of only one phase will protect the network from attack. Reconnaissance (Attackers carefully plan their attacks. They research, identify, and select targets. Also scan for network vulnerabilities and services or applications that they can exploit.) Weaponization (Use the information from the earlier reconnaissance to develop a weapon against specific targeted. Use the vulnerabilities of the assets that were discovered and build them into a tool that can be deployed) Delivery (Weapon is transmitted to the target using a delivery vector. Through the use of a website, removable USB media, or an email attachment Exploitation (Deploys an exploit against a vulnerable application or system. Deploying an exploit allows the attack to gain an initial entry point into the organization. Installation (Threat actor establishes a back door into the system. Must survive through antimalware scans and rebooting of the computer to be effective. Seek to establish privileged operations and escalating privileges) Command and Control (Establish command and control (CnC or C2) with the target system. Pass data back and forth between infected devices and their own infrastructure. Malware requires manual interaction in order to exfiltrate data from the network.) Actions on Objectives (Persistence and ongoing communication. Goal achieved. Data exfiltration. Destruction of critical infrastructure. Encrypt and Ransom.) The PAN-OS DIPP NAT implementation supports oversubscription on some platforms. What is DIPP NAT Oversubscription? - CORRECT ANSWER Reuse of port numbers TCP protocol recognizes up to approximately 64,000 port numbers. A limit of approximately 64,000 concurrent sessions on each IP address configured within the NAT will be supported by DIPP source NAT pool. Oversubscription enables the reuse of port numbers as an alternative NAT session identifier by using the destination IP address. Which Next Generation Firewall feature is part of the Threat Intelligence Cloud and provides direct access to security operations and analysis teams to all of the threat intelligence Palo Alto Networks gathers from clients, open source feeds, and the Unit 42 threat research team? - CORRECT ANSWER AutoFocus The Palo Alto Networks Security Operating Platform is a prevention-focused architecture that offers visibility into all traffic and protects all users on any device from known and unknown cyber threats. Panorama (Consolidated policy creation and centralized management). Aperture (SaaS-based service that protects cloud-based applications such as Box, Salesforce, and Dropbox. Focused on Data loss prevention (DLP) for Personally Identifiable Information (PII), payment card industry (PCI) information). GlobalProtect (Network security for endpoints. Inspecting all traffic. Using internet gateways next-generation firewalls). AutoFocus (Service that is part of the Threat Intelligence Cloud. Direct access to all of the threat intelligence Palo Alto Networks gathers from customers and the Unit 42 threat research team). MineMeld (Allows you to aggregate threat intelligence. MineMeld can filter, unduplicate, and consolidate metadata across all sources). Application Framework and Logging Service (Application Framework - Apps can be created and developed on a common application framework. Logging Service - Central cloud-based repository for all application data and logs. No additional processing power and storage). Network Security (Can identify all network traffic based on applications, users, content, and devices Business policies in security rules). Advanced Endpoint Protection (Provides multi-method prevention both known and unknown threats directly on an endpoint). Cloud Security (VM-Series firewalls are designed for use in a virtualized or cloud environment). Applications and Threats updated content is made available by Palo Alto Networks on the following schedule? - CORRECT ANSWER Weekly Updated content is available on the following schedule by Palo Alto Networks: ▪ Antivirus: daily ▪ Applications and Threats: weekly updates, new applications added monthly ▪ WildFire: approximately every five minutes. You customize how often the firewall checks for the updates. Antivirus updates can be checked by the firewall as frequently as every hour, updates to Applications and Threats as frequently as every 30 minutes, and updates to WildFire as frequently as every minute. When configuring a File Blocking Profile, what action you can set? - CORRECT ANSWER -Alert -Block -Continue File Blocking Profiles identify and control the flow of various file types. The file type is identified by the extension of the filename and by examining the file content. You can configure a File Blocking Profile with three actions: "alert," "continue," and "block." An "alert" action allows file transfer, however generates a log entry in the Data Filter Log. A "continue" action logs the event but also allows a file to be transferred only with the user's permission The "block" action logs the activity and blocks the transfer of the file. Source NAT is used to enable hosts on the public (external) network access to private (internal) servers. ? - CORRECT ANSWER Configuring NAT can take two forms: source NAT and destination NAT. Source NAT is translation of traffic originating on a private network and being forwarded to the Internet. Destination NAT is translation of traffic coming from the internet to the local private network [Show More]
Last updated: 2 years ago
Preview 1 out of 12 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Also available in bundle (1)
Click Below to Access Bundle(s)

ALL PCNSA Exam (21 Sets) Questions with Verified Answers,100% CORRECT
PCNSA Exam 59 Questions with Verified Answers,PCNSA Flash Cards Exam 117 Questions with Verified Answers,PCNSA Exam 84 Questions with Verified Answers,PCNSA Exam 132 Questions with Verified Answers,PC...
By Nolan19 2 years ago
$35
21
Reviews( 0 )
$8.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Oct 09, 2023
Number of pages
12
Written in
All
Additional information
This document has been written for:
Uploaded
Oct 09, 2023
Downloads
0
Views
126