PCNSA Study Guide Exam 47 Questions with Verified Answers,100% CORRECT
Document Content and Description Below
PCNSA Study Guide Exam 47 Questions with Verified Answers
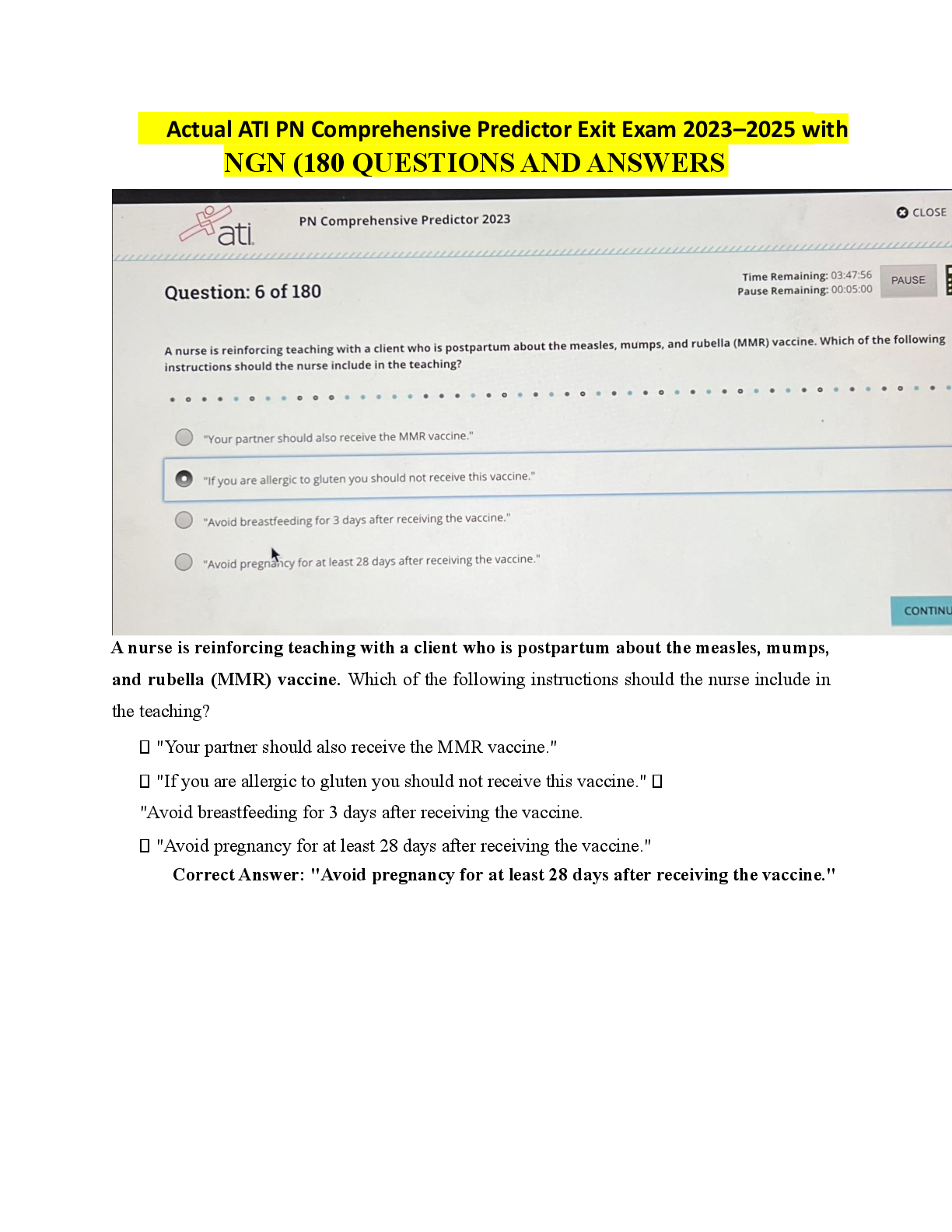
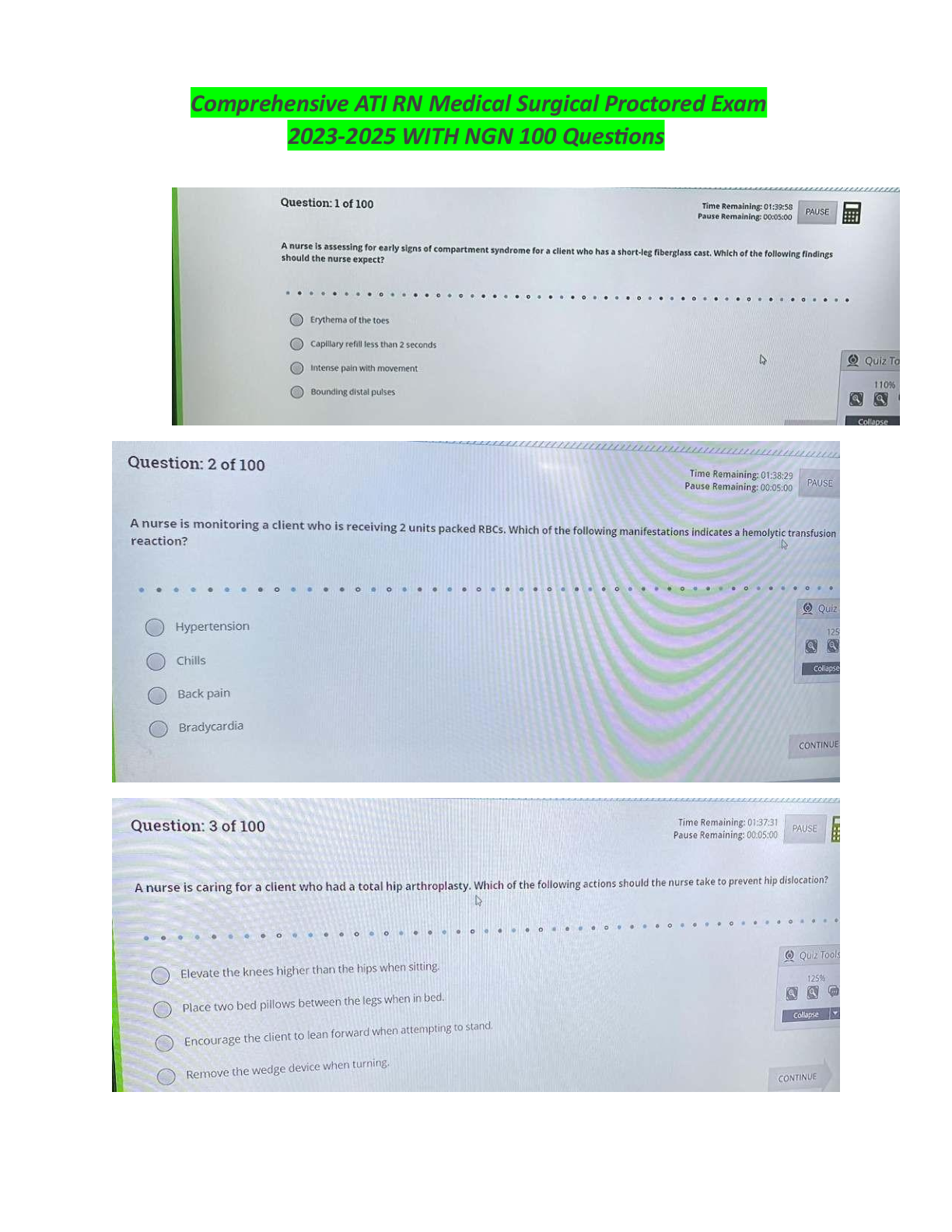
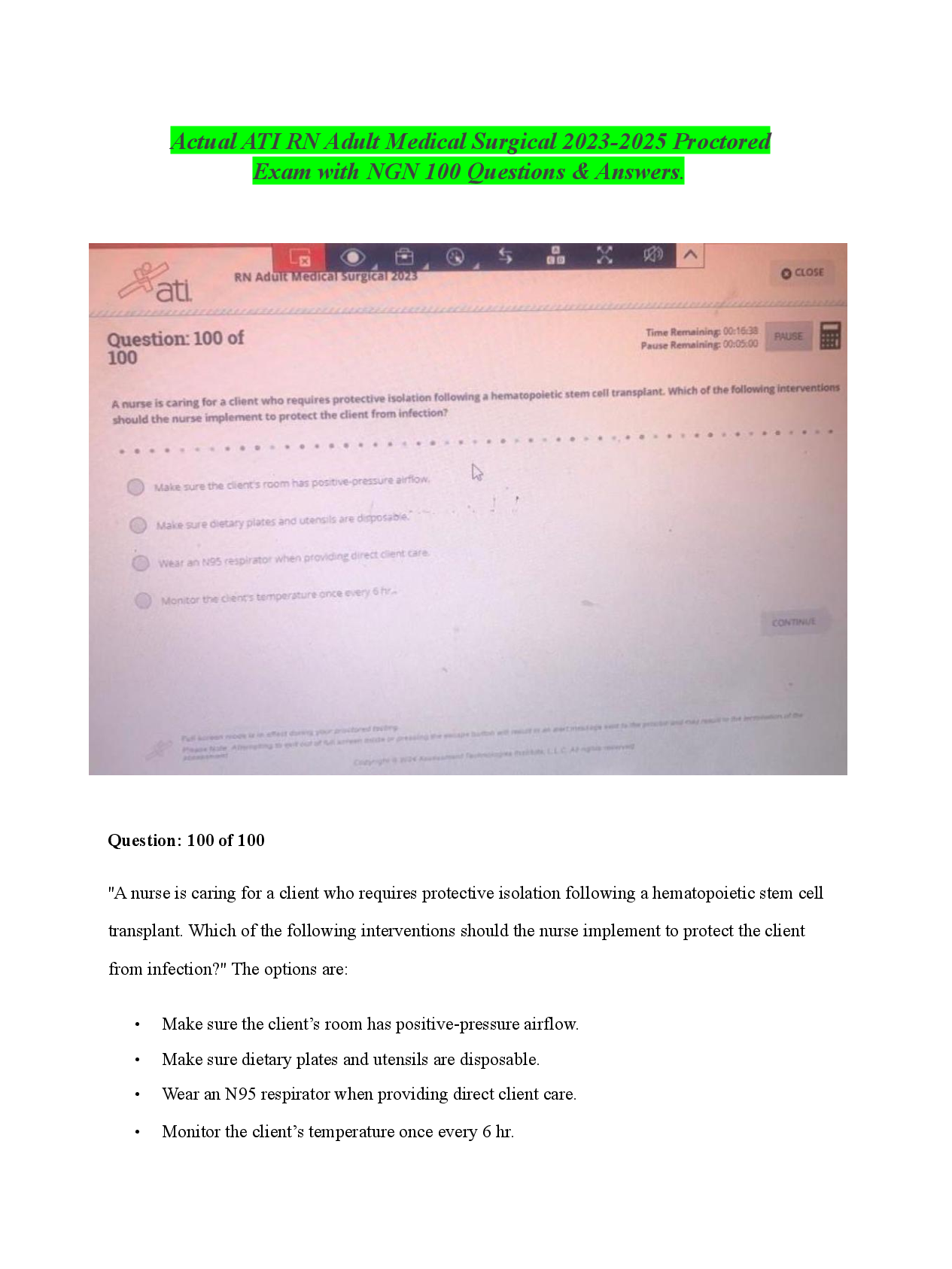
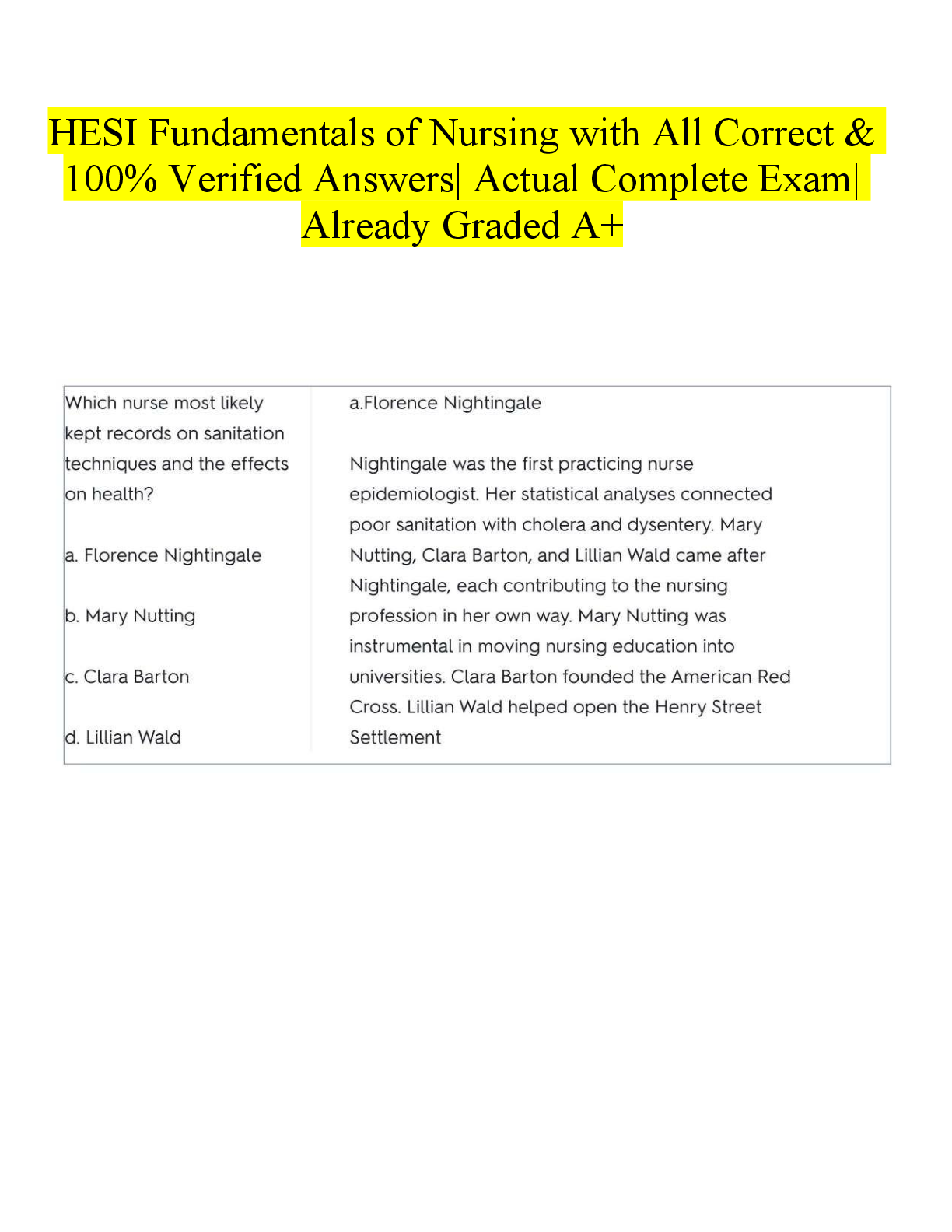
Which steps of the cyberattack lifecycle is used by an attacker to carefully plan their atacks? - CORRECT ANSWER Reconissance
Which ty
...
pical application use can be a gray area on whether the application should be enabled or blocked? - CORRECT ANSWER Tolerated
What is the application database that Palo Alto Networks uses along with App-ID to identify applications? - CORRECT ANSWER applipedia.com
Which tool provides a simple workflow to migrate your legacy or port-based Security policy rulebase to an App-ID-based rulebase? - CORRECT ANSWER Policy Optimizer
Which tool enables you to migrate existing rules from a legacy firewall to a Palo Alto Networks Next-Generation Firewall? - CORRECT ANSWER Expedition
Which phase of the migration process would you use to add application-base rules above the corresponding port-based rules? - CORRECT ANSWER Phase 2
Which VM-Series firewall does *NOT* currently support Device-ID? - CORRECT ANSWER VM-50
T/F. The IoT Security app approach starts by identifying and classifying the devices in your network? - CORRECT ANSWER True
Which Level of Device Classification classifies the device based on the vendor and model? - CORRECT ANSWER Third level
Which Policy Configuration example did the administrator enable policies to allow Cisco VoIP devices to access only the required applications? - CORRECT ANSWER Allow access based on device identity
Which Level of Device Classification identifies the industry in which the device operates? - CORRECT ANSWER First level
Organizations that have not enabled User-ID for visibility create Security policies based on which of the following? - CORRECT ANSWER IP address
T/F. User-ID enables security teams to define policy rules on firewalls to safely enable applications and control access based on users or groups of users - CORRECT ANSWER True
At which step of the User-ID roadmap would you employ a IP-to-user mapping strategy? - CORRECT ANSWER Implement user visibility
What could a SOC analyst use to trigger selective actions on the firewall that will be enforced immediately? - CORRECT ANSWER Dynamic user groups
What is the maximum number of agents that you can add for data redistribution? - CORRECT ANSWER 100
What percentage of malware campaigns are expected to use some type of encryption? - CORRECT ANSWER 70 percent
T/F. Data Loss and Compliance checks stop the loss of sensitive data such as personally identifiable information (PII) and intellectual property (IP). - CORRECT ANSWER True
Which of the following identifies and prevents corporate computer and internet usage policy violations? - CORRECT ANSWER Phishing and Credential Attacks
Which time frame within the decryption rollout is considered the most critical and is the time when you eliminate most problems and move to your user base? - CORRECT ANSWER days 0-30
Which protocol offers improved security, performance, and privacy benefits over the previous versions? - CORRECT ANSWER TLS 1.3
Which of the following are challenges enterprises face in verifying users and enforcing identity-based security? - CORRECT ANSWER -Configuring, maintaining, and synchronizing network security with multiple IdPs can be time-consuming and resource-intensive.
-Set up on-prem IdPs provides the necessary network security capabilities to achieve Zero Trust.
-Fragmentation of identities, and difficulty in ensuring consistent application of identity-based security-controls, has created a significant barrier to adopting Zero Trust.
Which of the following statements about the Cloud Identity Engine are true? - CORRECT ANSWER -It simplifies Zero Trust with easy-to-deploy user identity and access across all locations.
-It is a cloud-native identity synchronization and authentication service-providing a single secure user identity across Palo Alto Networks on-prem and cloud product lines.
Palo Alto Networks was the first next-generation firewall vendor to enable identity-based security by: - CORRECT ANSWER Leveraging user-based policies
T/F. Identity Providers (IdPs) are typically cloud-hosted services and often operate with single sign-on (SSO) providers to authenticate users. - CORRECT ANSWER True
T/F. Authentication policy enables you to authenticate end users before they can access services and applications. - CORRECT ANSWER True
The Cloud Identity Engine empowers organizations to move toward Zero Trust by enabling them to do which two of the following? - CORRECT ANSWER -Accurately enforce security decisions for all their users at all times, with assured synchronization of all identity-related data in the cloud.
-Save time in deployment and management of identity-based controls on their network security infrastructure
Sharing of on-prem Active Directory (AD) groups to other branches via the Cloud offers which benefits? - CORRECT ANSWER -Removes the complexity of managing multiple connections to AD
-Enables customers to download groups and users from their on-prem AD to other branches via cloud
What are three benefits that customers receive with the Cloud Identity Engine? - CORRECT ANSWER -With minimal effort, enable and secure identity irrespective of whether they are using on-prem, cloud hybrid, or multicloud identity sources (IdPs).
-Enable identity across the infrastructure. Configure once and CIE pulls incremental directory information automatically on consistent intervals. No additional charges required for additional IdPs (authentication).
-It is maintenance-free - No need to make changes on your infrastructure as identity providers make changes. All changes by identity providers, e.g., any updates by identity providers or changes in authentication protocols of directories do not require additional configuration on each firewall, management, endpoints.
Which three of the following are Zero Touch approaches? - CORRECT ANSWER -Google BeyondCorp
-Gartner CARTA
-Forrester Zero Trust
Which of the following were authentication challenges faced by customers before the Cloud Identity Engine solution? - CORRECT ANSWER Every identity provider had to be added to all firewalls, management, and endpoints
The Cloud Identity Engine allows you to write Security policy based on which two things? - CORRECT ANSWER Users and Groups
The Cloud Identity Engine provides Palo Alto Networks apps and services with which type of access to your directory information for user visibility and policy enforcement? - CORRECT ANSWER Read-only
To authenticate users, what do Google, Azure and Okta need configured in the Cloud Identity Engine? - CORRECT ANSWER a SAML 2.0 based identity provide (IdP)
When you configure to activate Cloud Identity Engine, what required information do you need to provide? - CORRECT ANSWER -Region
-Company account
-Name
To collect attributes from your Active Directory and synchronize them with the Cloud Identity Engine, which three versions of TLS encryption is supported? - CORRECT ANSWER -TLS 1.1
-TLS 1.2
-TLS 1.3
T/F. You do not need to install or configure a Cloud Identity agent to collect attributes from a cloud-based direcdtory? - CORRECT ANSWER True
To set up the Cloud Identity Engine, which two required tasks will you need to perform? - CORRECT ANSWER -Log in to the Cloud Identity Engine app on the hub to generate a certificate to authenticate the agent and the Cloud Identity Engine
-Associate the Cloud Identity Engine with Palo alto Networks apps to select which apps can use your directory information
The cloud Identity Engine allows you to write security policy based on which two of the following? - CORRECT ANSWER -Groups
-Users
The components of the Cloud Identity Engine deployment vary based on which two of the following factors? - CORRECT ANSWER -Whether the Cloud Identity Engine is accessing an on-premises directory (Active Directory)
-Whether the Cloud Identity Engine is accessing a cloud-based directory (Azure Active Directory)
Which two actions do you need to perform to use the Cloud Identity Engine with an on-premises Active Directory? - CORRECT ANSWER -Access the Cloud Identity Engine app on the hub so you can manage your Cloud Identity Engine instances and Cloud Identity agents
-Install the cloud Identity agent on a Windows server (the agent host) and configure it to connect to your Active Directory and the cloud Identity Engine
Which two planes are found in the Palo Alto Networks single-pass platform architecture? - CORRECT ANSWER -Control
-Data
Which object cannot be segmented using virtual systems on a firewall? - CORRECT ANSWER MGT interface
What are the two attributes of the dedicated out-of-band network management port in Palo Alto Networks Firewalls? - CORRECT ANSWER -Labeled MGT by default
-Cannot be configured as a standard traffic port
T/F. To register a hardware firewall, you will need the firewall's serial number? - CORRECT ANSWER True
In the web interface, what is signified when a text box is highlighted in red? - CORRECT ANSWER The value in the text box is required
T/F. Service routes can be used to configure an in-band port to access external services. - CORRECT ANSWER True
[Show More]
Last updated: 2 years ago
Preview 1 out of 6 pages