PCNSA Exam 147 Questions with Verified Answers,100% CORRECT
Document Content and Description Below
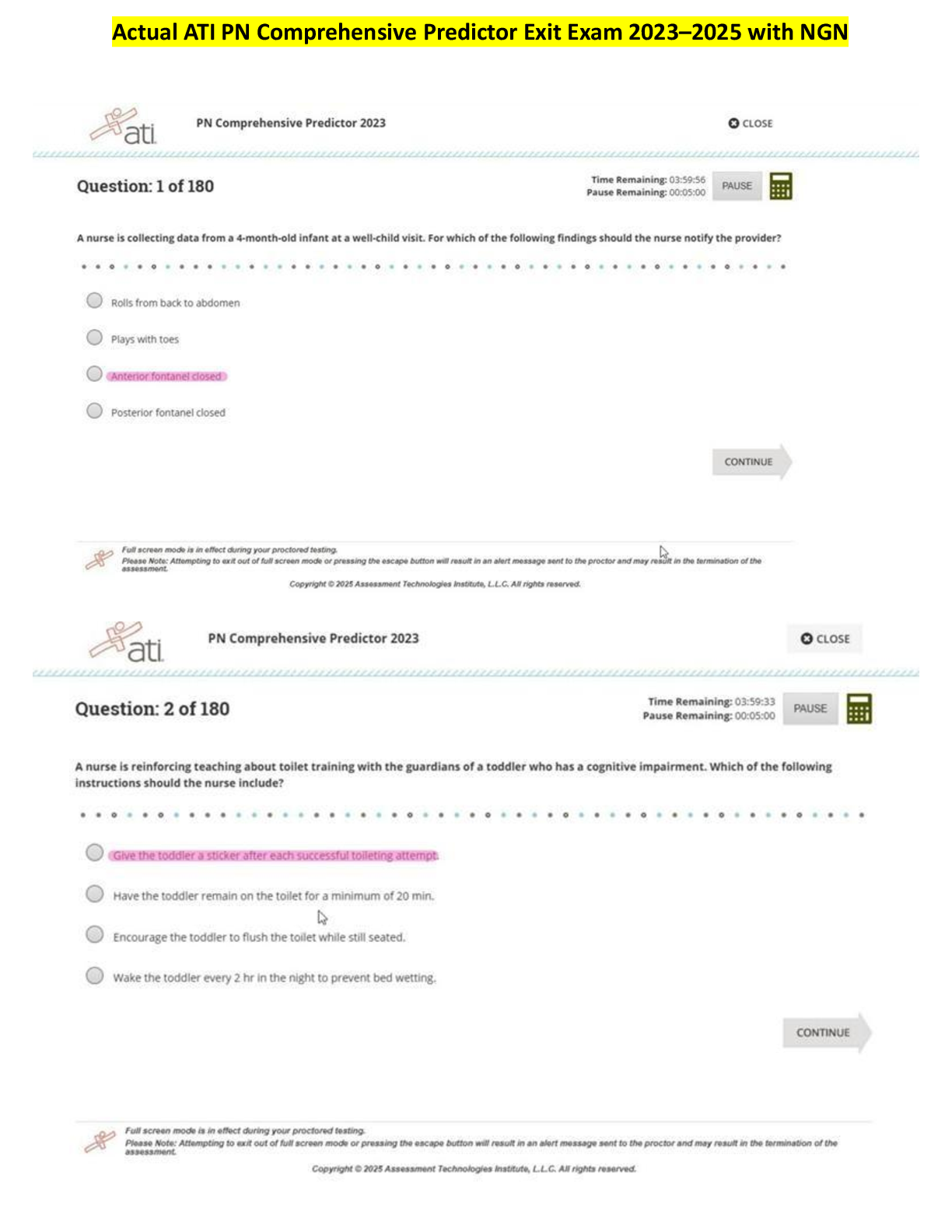
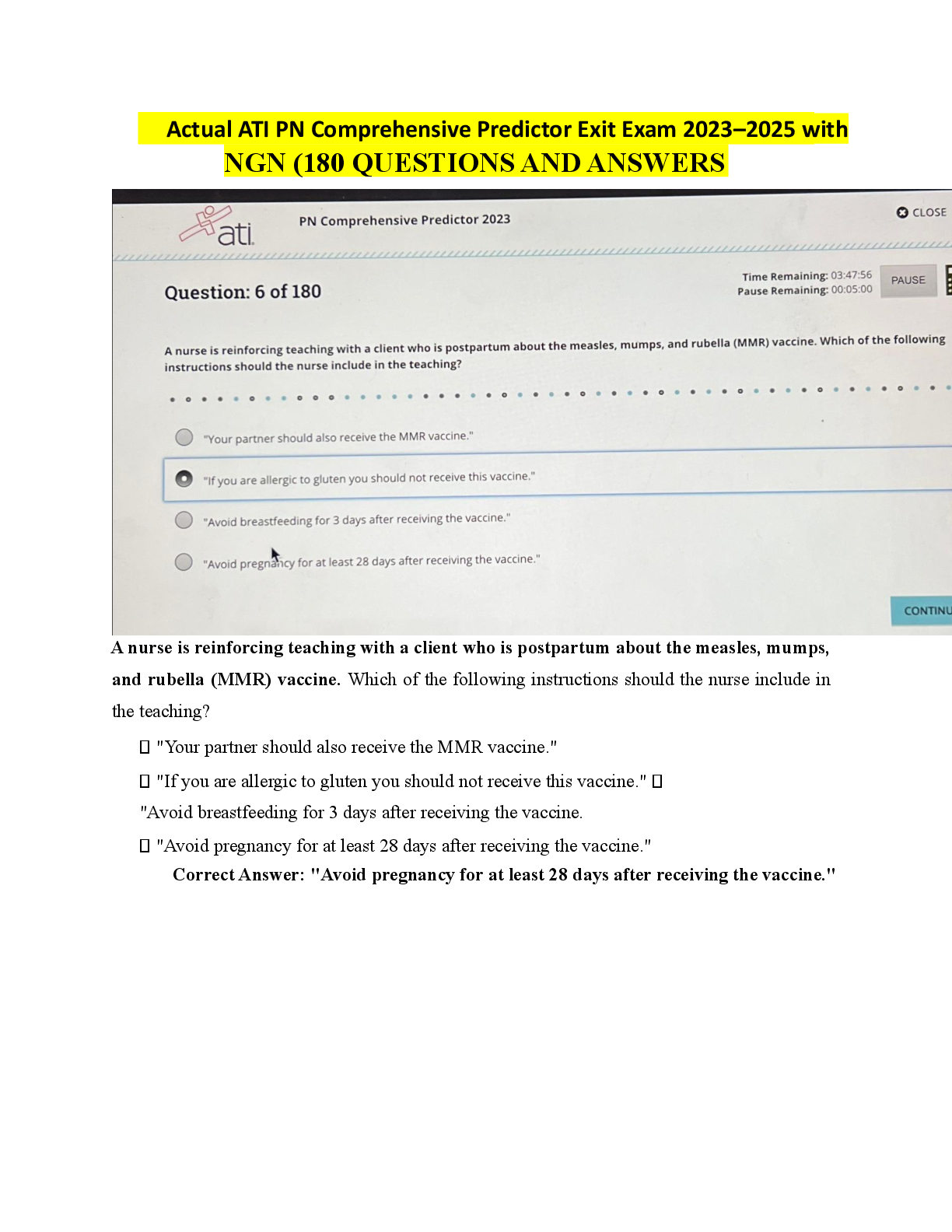
PCNSA Exam 147 Questions with Verified Answers Threat Intelligence Cloud - CORRECT ANSWER Gather, analyzes, correlates, and disseminates threats to and from the network and endpoints located within ... the network Next-generation Firewall - CORRECT ANSWER Identifies and inspects all traffic to block know threats. Advanced Endpoint Protection - CORRECT ANSWER Inspects all Processes and files to prevents known and unknown exploits Which plane on a Palo Alto Networks Firewall provide configuration, logging, and reporting functions on a separate processor. - CORRECT ANSWER Management A security administrator has configured App-ID updates to be automatically downloaded and installed. The company is currently using an application identified byApp-ID as SuperApp_base. On a content update notice, Palo Alto Networks is adding new app signatures labeled SuperApp_chat and SuperApp_download, which will be deployed in 30 days.Based on the information, how is the SuperApp traffic affected after the 30 days have passed? - CORRECT ANSWER No impact because the firewall automatically adds the rules to the App-ID interface How many zones can an interface be assigned with a Palo Alto Networks firewall? - CORRECT ANSWER One Which two configuration settings shown are not the default? - CORRECT ANSWER Server Log Monitor Frequency (sec) Enable Session Which data plane layer of the graphic shown provides pattern protection for spyware and vulnerability exploits on a Palo Alto Networks Firewall? - CORRECT ANSWER Signature Matching Which option shows the attributes that are selectable when setting up application filters? - CORRECT ANSWER Category, Subcategory, Technology, Risk, and Characteristic Actions can be set for which two items in a URL filtering security profile? - CORRECT ANSWER Block List Allow List reconnaissance - CORRECT ANSWER Stage where the attacker scans for network vulnerabilities and services that can exploited installation - CORRECT ANSWER stage where the attacker will explore methods such as a root kit to establish persistence. Command and Control - CORRECT ANSWER stage where the attacker has access to a specific server so they can communicate and pass data to and from infected devices within an network Act on the Objective - CORRECT ANSWER stage where the attacker has motivation for attacking a network to deface web property Which two statements are correct about App-ID content updates? - CORRECT ANSWER Existing security policy rules are not affected by application content updates. After an application content update, new applications are automatically identified and classified. Which User-ID mapping method should be used for an environment with users that do not authenticate to Active Directory? - CORRECT ANSWER Captive Portal An administrator needs to allow users to use their own office applications. How should the administrator configure the firewall to allow multiple applications in a dynamic environment? - CORRECT ANSWER Create an Application Filter and name it Office Programs, then filter it on the business-systems category, office-programs subcategory Which statement is true regarding a Best Practice Assessment? - CORRECT ANSWER It provides a percentage of adoption for each assessment area Employees are shown an application block page when they try to access YouTube. Which security policy is blocking the YouTube application? - CORRECT ANSWER interzone-default Choose the option that correctly completes this statement. A Security Profile can block or allow traffic ____________. - CORRECT ANSWER after it is matched by a security policy rule that allows traffic. When creating a Source NAT policy, which entry in the Translated Packet tab will display the options Dynamic IP and Port, Dynamic, Static IP, and None? - CORRECT ANSWER Translation Type Which interface does not require a MAC or IP address? - CORRECT ANSWER Virtual Wire A company moved its old port-based firewall to a new Palo Alto Networks NGFW 60 days ago. Which utility should the company use to identify out-of-date or unused rules on the firewall? - CORRECT ANSWER Rule Usage Filter > Hit Count > Unused in 90 days Step 1 for creating a new security zone with a Palo Alto Networks firewall. - CORRECT ANSWER Select Zone from List Step 2 for creating a new security zone with a Palo Alto Networks firewall. - CORRECT ANSWER Assign Interface as needed Step 3 for creating a new security zone with a Palo Alto Networks firewall. - CORRECT ANSWER Select Network Tab Step 4 for creating a new security zone with a Palo Alto Networks firewall. - CORRECT ANSWER Select Zone Name Step 5 for creating a new security zone with a Palo Alto Networks firewall. - CORRECT ANSWER Select Add Step 6 for creating a new security zone with a Palo Alto Networks firewall. - CORRECT ANSWER Specify Zone type What are two differences between an implicit dependency and an explicit dependency in App-ID? (Choose two.) - CORRECT ANSWER An implicit dependency does not require the dependent application to be added in the security policy An explicit dependency requires the dependent application to be added in the security policy Recently changes were made to the firewall to optimize the policies and the security team wants to see if those changes are helping.What is the quickest way to reset the hit counter to zero in all the security policy rules? - CORRECT ANSWER Use the Reset Rule Hit Counter > All Rules option Which two App-ID applications will you need to allow in your Security policy to use facebook-chat? (Choose two.) - CORRECT ANSWER facebook-chat facebook-base Which User-ID agent would be appropriate in a network with multiple WAN links, limited network bandwidth, and limited firewall management plane resources? - CORRECT ANSWER Windows-based agent deployed on the internal network Your company requires positive username attribution of every IP address used by wireless devices to support a new compliance requirement. You must collect IPג€"to-user mappings as soon as possible with minimal downtime and minimal configuration changes to the wireless devices themselves. The wireless devices are from various manufactures.Given the scenario, choose the option for sending IP-to-user mappings to the NGFW. - CORRECT ANSWER syslog An administrator receives a global notification for a new malware that infects hosts. The infection will result in the infected host attempting to contact a command- and-control (C2) server.Which two security profile components will detect and prevent this threat after the firewall signature database has been updated? (Choose two.) - CORRECT ANSWER anti-spyware profile applied to outbound security policies URL filtering profile applied to outbound security policies At which stage of the Cyber-Attack Lifecycle would the attacker attach an infected PDF file to an email? - CORRECT ANSWER Delivery Identify the correct order to configure the PAN-OS integrated USER-ID agent. 3. add the service account to monitor the server(s) 2. define the address of the servers to be monitored on the firewall 4. commit the configuration, and verify agent connection status 1. create a service account on the Domain Controller with sufficient permissions to execute the User- ID agent - CORRECT ANSWER 1-3-2-4 Users from the internal zone need to be allowed to Telnet into a server in the DMZ zone.Complete the security policy to ensure only Telnet is allowed.Security Policy: Source Zone: Internal to DMZ Zone __________services ג€Application defaultsג€, and action = Allow - CORRECT ANSWER Application = "Telnet" Based on the security policy rules shown, ssh will be allowed on which port? - CORRECT ANSWER 22 Which license must an Administrator acquire prior to downloading Antivirus Updates for use with the firewall? - CORRECT ANSWER Threat Prevention An administrator notices that protection is needed for traffic within the network due to malicious lateral movement activity. Based on the image shown, which traffic would the administrator need to monitor and block to mitigate the malicious activity? - CORRECT ANSWER east-west traffic Given the topology, which zone type should zone A and zone B to be configured with? - CORRECT ANSWER Layer3 To use Active Directory to authenticate administrators, which server profile is required in the authentication profile? - CORRECT ANSWER LDAP Which interface type is used to monitor traffic and cannot be used to perform traffic shaping? - CORRECT ANSWER Tap Which administrator type provides more granular options to determine what the administrator can view and modify when creating an administrator account? - CORRECT ANSWER Role-based Which administrator type utilizes predefined roles for a local administrator account? - CORRECT ANSWER Dynamic Which two security profile types can be attached to a security policy? (Choose two.) - CORRECT ANSWER antivirus vulnerability The CFO found a USB drive in the parking lot and decide to plug it into their corporate laptop. The USB drive had malware on it that loaded onto their computer and then contacted a known command and control (CnC) server, which ordered the infected machine to begin Exfiltrating data from the laptop.Which security profile feature could have been used to prevent the communication with the CnC server? - CORRECT ANSWER Create an anti-spyware profile and enable DNS Sinkhole Which user mapping method could be used to discover user IDs in an environment with multiple Windows domain controllers? - CORRECT ANSWER domain controller monitoring Which three statements describe the operation of Security policy rules and Security Profiles? (Choose three.) - CORRECT ANSWER Security Profiles are attached to Security policy rules. Security Profiles should be used only on allowed traffic. Security policy rules can block or allow traffic. Given the image, which two options are true about the Security policy rules. (Choose two.) - CORRECT ANSWER The Allow Office Programs rule is using an Application Filter In the Allow Social Networking rule, allows all of Facebookג€™s functions Which type of Security policy rule would match traffic flowing between the Inside zone and Outside zone, within the Inside zone, and within the Outside zone? - CORRECT ANSWER universal Which Palo Alto Networks firewall security platform provides network security for mobile endpoints by inspecting traffic deployed as internet gateways? - CORRECT ANSWER GlobalProtect Which two statements are correct regarding multiple static default routes when they are configured as shown in the image? (Choose two.) - CORRECT ANSWER Path monitoring determines if route is useable. Route with lowest metric is actively used. Given the Cyber-Attack Lifecycle diagram, identify the stage in which the attacker can run malicious code against a targeted machine. - CORRECT ANSWER Exploitation Which file is used to save the running configuration with a Palo Alto Networks firewall? - CORRECT ANSWER running-config.xml In the example security policy shown, which two websites would be blocked? (Choose two.) - CORRECT ANSWER LinkedIn Facebook Which Palo Alto Networks component provides consolidated policy creation and centralized management? - CORRECT ANSWER Panorama Which statement is true regarding a Prevention Posture Assessment? - CORRECT ANSWER It provides a set of questionnaires that help uncover security risk prevention gaps across all areas of network and security architecture Which five Zero Trust concepts does a Palo Alto Networks firewall apply to achieve an integrated approach to prevent threats? (Choose five.) - CORRECT ANSWER User identification Vulnerability protection Antivirus Application identification Anti-spyware The PowerBall Lottery has reached a high payout amount and a company has decided to help employee morale by allowing employees to check the number, but doesnג€™t want to unblock the gambling URL category.Which two methods will allow the employees to get to the PowerBall Lottery site without the company unlocking the gambling URL category? (Choose two.) - CORRECT ANSWER Add *.powerball.com to the allow list Create a custom URL category called PowerBall and add *.powerball.com to the category and set the action to allow. Which service protects cloud-based applications such as Dropbox and Salesforce by administering permissions and scanning files for sensitive information? - CORRECT ANSWER Aperture (Prisma Saas) An administrator receives a global notification for a new malware that infects hosts. The infection will result in the infected host attempting to contact and command-and-control (C2) server.Which security profile components will detect and prevent this threat after the firewallג€™s signature database has been updated? - CORRECT ANSWER Antivirus profile applied to outbound security policies Which update option is not available to administrators? - CORRECT ANSWER New URLs A server-admin in the USERS-zone requires SSH-access to all possible servers in all current and future Public Cloud environments. All other required connections have already been enabled between the USERS- and the OUTSIDE-zone. What configuration-changes should the Firewall-admin make? - CORRECT ANSWER Create a security-rule that allows traffic from zone USERS to OUTSIDE to allow traffic from any source IP-address to any destination IP-address for application SSH How often does WildFire release dynamic updates? - CORRECT ANSWER every 5 minutes What is the minimum frequency for which you can configure the firewall to check for new WildFire antivirus signatures? - CORRECT ANSWER every 1 minute Your company has 10 Active Directory domain controllers spread across multiple WAN links. All users authenticate to Active Directory. Each link has substantial network bandwidth to support all mission-critical applications. The firewallג€™s management plane is highly utilized.Given the scenario, which type of User-ID agent is considered a best practice by Palo Alto Networks? - CORRECT ANSWER Windows-based agent on a domain controller What must you configure to enable the firewall to access multiple Authentication Profiles to authenticate a non-local account? - CORRECT ANSWER authentication sequence Which Security Profile mitigates attacks based on packet count? - CORRECT ANSWER zone protection profile Which interface type uses virtual routers and routing protocols? - CORRECT ANSWER Layer3 Which URL Filtering Profile action does not generate a log entry when a user attempts to access a URL? - CORRECT ANSWER Allow An internal host needs to connect through the firewall using source NAT to servers of the internet.Which policy is required to enable source NAT on the firewall? - CORRECT ANSWER NAT policy with internal zone and internet zone specified Which Security Profile can provide protection against ICMP floods, based on individual combinations of a packetג€™s source and destination IP addresses? - CORRECT ANSWER DoS protection Which path in PAN-OS 9.0 displays the list of port-based security policy rules? - CORRECT ANSWER Policies> Security> Rule Usage> No App Specified Which two components are utilized within the Single-Pass Parallel Processing architecture on a Palo Alto Networks Firewall? (Choose two.) - CORRECT ANSWER App-ID User-ID Which path is used to save and load a configuration with a Palo Alto Networks firewall? - CORRECT ANSWER Device>Setup>Operations Which action related to App-ID updates will enable a security administrator to view the existing security policy rule that matches new application signatures? - CORRECT ANSWER Review Policies How do you reset the hit count on a Security policy rule? - CORRECT ANSWER Select a Security policy rule, and then select Hit Count > Reset. Given the topology, which zone type should you configure for firewall interface E1/1? - CORRECT ANSWER Tap Which interface type is part of a Layer 3 zone with a Palo Alto Networks firewall? - CORRECT ANSWER Aggregate Which security policy rule would be needed to match traffic that passes between the Outside zone and Inside zone, but does not match traffic that passes within the zones? - CORRECT ANSWER interzone Four configuration choices are listed, and each could be used to block access to a specific URL. If you configured each choice to block the same URL then which choice would be the last to block access to the URL? - CORRECT ANSWER PAN-DB URL category in URL Filtering Profile Which data flow direction is protected in a zero-trust firewall deployment that is not protected in a perimeter-only firewall deployment? - CORRECT ANSWER east-west Which protocol is used to map usernames to user groups when User-ID is configured? - CORRECT ANSWER LDAP Which definition describes the guiding principle of the zero-trust architecture? - CORRECT ANSWER never trust, always verify All users from the internal zone must be allowed only Telnet access to a server in the DMZ zone.Complete the two empty fields in the Security policy rules that permits only this type of access. Source Zone: Internal - Destination Zone: DMZ Zone - Application: _________? Service: ____________? Action: allow- (Choose two.) - CORRECT ANSWER Service = ג€application-defaultג€ Application = ג€Telnetג€ In which profile should you configure the DNS Security feature? - CORRECT ANSWER Anti-Spyware Profile Which two statements are true for the DNS Security service introduced in PAN-OS version 9.0? (Choose two.) - CORRECT ANSWER It removes the 100K limit for DNS entries for the downloaded DNS updates. It eliminates the need for dynamic DNS updates. Which two features can be used to tag a username so that it is included in a dynamic user group? (Choose two.) - CORRECT ANSWER XML API User-ID Windows-based agent The CFO found a malware infected USB drive in the parking lot, which when inserted infected their corporate laptop. The malware contacted a known command- and-control server, which caused the infected laptop to begin exfiltrating corporate data.Which security profile feature could have been used to prevent the communication with the command-and-control server? - CORRECT ANSWER Create an anti-spyware profile and enable DNS Sinkhole feature. You must configure which firewall feature to enable a data-plane interface to submit DNS queries on behalf of the control plane? - CORRECT ANSWER service route Which component provides network security for mobile endpoints by inspecting traffic routed through gateways? - CORRECT ANSWER GlobalProtect For the firewall to use Active Directory to authenticate users, which Server Profile is required in the Authentication Profile? - CORRECT ANSWER LDAP Which operations are allowed when working with App-ID application tags? - CORRECT ANSWER Predefined tags may be augmented by custom tags. Your company occupies one floor in a single building. You have two Active Directory domain controllers on a single network. The firewallג€™s management plane is only slightly utilized.Which User-ID agent is sufficient in your network? - CORRECT ANSWER PAN-OS integrated agent deployed on the firewall Which type of administrative role must you assign to a firewall administrator account, if the account must include a custom set of firewall permissions? - CORRECT ANSWER Role-based Which statement is true regarding a Heatmap report? - CORRECT ANSWER It provides a set of questionnaires that help uncover security risk prevention gaps across all areas of network and security architecture. Based on the screenshot presented, which column contains the link that when clicked, opens a window to display all applications matched to the policy rule? - CORRECT ANSWER Apps Seen Access to which feature requires the PAN-OS Filtering license? - CORRECT ANSWER PAN-DB database Based on the screenshot, what is the purpose of the Included Groups? - CORRECT ANSWER They are used to map users to groups. Based on the graphic, which statement accurately describes the output shown in the Server Monitoring panel? - CORRECT ANSWER The User-ID agent is connected to a domain controller labeled lab-client. Which action results in the firewall blocking network traffic without notifying the sender? - CORRECT ANSWER Drop What do Dynamic User Groups help you to do? - CORRECT ANSWER create a policy that provides auto-remediation for anomalous user behavior and malicious activity Which type of security policy rule will match traffic that flows between the Outside zone and inside zone, but would not match traffic that flows within the zones? - CORRECT ANSWER interzone You notice that protection is needed for traffic within the network due to malicious lateral movement activity. Based on the image shown, which traffic would you need to monitor and block to mitigate the malicious activity? - CORRECT ANSWER east-west traffic Which type of administrator account cannot be used to authenticate user traffic flowing through the firewall's data plane? - CORRECT ANSWER local user How frequently can WildFire updates be made available to firewalls? - CORRECT ANSWER every 5 minutes Starting with PAN-OS version 9.1, which new type of object is supported for use within the User field of a Security policy rule? - CORRECT ANSWER dynamic user group Which link in the web interface enables a security administrator to view the Security policy rules that match new application signatures? - CORRECT ANSWER Review Policies Based on the shown security policy, which Security policy rule would match all FTP traffic from the inside zone to the outside zone? - CORRECT ANSWER egress-outside Which type of firewall configuration contains in-progress configuration changes? - CORRECT ANSWER candidate Which three configuration settings are required on a Palo Alto Network firewall management interface? - CORRECT ANSWER Netmask, default gateway, IP address What is an advantage for using application tags? - CORRECT ANSWER They help content updates automate policy updates. At which point in the App-ID update process can you determine if an existing policy rule is affected by an App-ID update? - CORRECT ANSWER after downloading the update You receive notification about a new malware that infects hosts. An infection results in the infected host attempting to contact a command-and-control server.Which Security Profile detects and prevents this threat from establishing a command-and-control connection? - CORRECT ANSWER Anti-Spyware Profile applied to outbound security policies. The PowerBall Lottery has reached an unusually high value this week. Your company has decided to raise morale by allowing employees to access the PowerBallLottery website (www.powerball.com) for just this week. However, the company does not want employees to access any other websites also listed in the URL filtering `gambling` category.Which method allows the employees to access the PowerBall Lottery website but without unblocking access to the `gambling` URL category? - CORRECT ANSWER Add *.powerball.com to the URL Filtering allow list. Create a custom URL category, add *.powerball.com to it and allow it in the Security Profile. Which Palo Alto Networks service protects cloud-based applications such as Dropbox and Salesforce by monitoring permissions and shares and scanning files for sensitive information? - CORRECT ANSWER Prisma SaaS In a Security policy, what is the quickest way to reset all policy rule hit counters to zero? - CORRECT ANSWER Use the Reset Rule Hit Counter > All Rules option Based on the Security policy rules shown, SSH will be allowed on which port? - CORRECT ANSWER the default port You receive notification about new malware that is being used to attack hosts. The malware exploits a software bug in common application.Which Security Profile detects and blocks access to this threat after you update the firewall's threat signature database? - CORRECT ANSWER Antivirus Profile applied to outbound Security policy rules Palo Alto Networks firewall architecture accelerates content inspection performance while minimizing latency using which two components? (Choose two.) - CORRECT ANSWER Parallel Processing Hardware Single Stream-based Engine An administrator is reviewing another administrator's Security policy log settings.Which log setting configuration is consistent with best practices for normal traffic? - CORRECT ANSWER Log at Session Start disabled, Log at Session End enabled Which Security profile would you apply to identify infected hosts on the protected network using DNS traffic? - CORRECT ANSWER anti-spyware Assume a custom URL Category Object of `NO-FILES` has been created to identify a specific website?How can file uploading/downloading be restricted for the website while permitting general browsing access to that website? - CORRECT ANSWER Create a Security policy with a URL Filtering profile that references the site access setting of block to NO-FILES. Which URL Filtering profile action would you set to allow users the option to access a site only if they provide a URL admin password? - CORRECT ANSWER override How are Application Filters or Application Groups used in firewall policy? - CORRECT ANSWER Which tab would an administrator click to create an address object? - CORRECT ANSWER Objects An administrator wishes to follow best practices for logging traffic that traverses the firewall.Which log setting is correct? - CORRECT ANSWER Enable Log at Session End Which two firewall components enable you to configure SYN flood protection thresholds? (Choose two.) - CORRECT ANSWER DoS Protection profile Zone Protection profile An administrator would like to see the traffic that matches the interzone-default rule in the traffic logs.What is the correct process to enable this logging? - CORRECT ANSWER Select the interzone-default rule and edit the rule; on the Actions tab, select Log at Session End and click OK. The Palo Alto Networks NGFW was configured with a single virtual router named VR-1.What changes are required on VR-1 to route traffic between two interfaces on the NGFW? - CORRECT ANSWER Add interfaces to the virtual router An administrator wants to prevent users from submitting corporate credentials in a phishing attack.Which Security profile should be applied? - CORRECT ANSWER URL-filtering Which two rule types allow the administrator to modify the destination zone? (Choose two.) - CORRECT ANSWER interzone, universal What is the main function of Policy Optimizer? - CORRECT ANSWER convert port-based security rules to application-based security rules Based on the screenshot, what is the purpose of the group in User labelled `it`? - CORRECT ANSWER Allow users in group "It" to access IT applications. Assume that traffic matches a Security policy rule but the attached Security Profiles is configured to block matching traffic.Which statement accurately describes how the firewall will apply an action to matching traffic? - CORRECT ANSWER If it is an allowed rule, then the Security Profile action is applied last. Which Security profile can you apply to protect against malware such as worms and Trojans? - CORRECT ANSWER antivirus Which license is required to use the Palo Alto Networks built-in IP address EDLs? - CORRECT ANSWER Threat Prevention Which statement is true about Panorama managed devices? - CORRECT ANSWER Panorama automatically removes local configuration locks after a commit from Panorama. A Security Profile can block or allow traffic at which point? - CORRECT ANSWER after it is matched to a Security policy rule that allows traffic Packet processing order of operations first - CORRECT ANSWER Dos Protection Packet processing order of operations second - CORRECT ANSWER Security Policy Lookup Packet processing order of operations third - CORRECT ANSWER content inspection Packet processing order of operations fourth - CORRECT ANSWER QOS shaping applied Which type of address object is `10.5.1.1/0.127.248.2`? - CORRECT ANSWER IP wildcard mask Which component is a building block in a Security policy rule? - CORRECT ANSWER application [Show More]
Last updated: 2 years ago
Preview 1 out of 17 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Also available in bundle (1)
Click Below to Access Bundle(s)

ALL PCNSA Exam (21 Sets) Questions with Verified Answers,100% CORRECT
PCNSA Exam 59 Questions with Verified Answers,PCNSA Flash Cards Exam 117 Questions with Verified Answers,PCNSA Exam 84 Questions with Verified Answers,PCNSA Exam 132 Questions with Verified Answers,PC...
By Nolan19 2 years ago
$35
21
Reviews( 0 )
$10.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Oct 09, 2023
Number of pages
17
Written in
All
Additional information
This document has been written for:
Uploaded
Oct 09, 2023
Downloads
0
Views
140