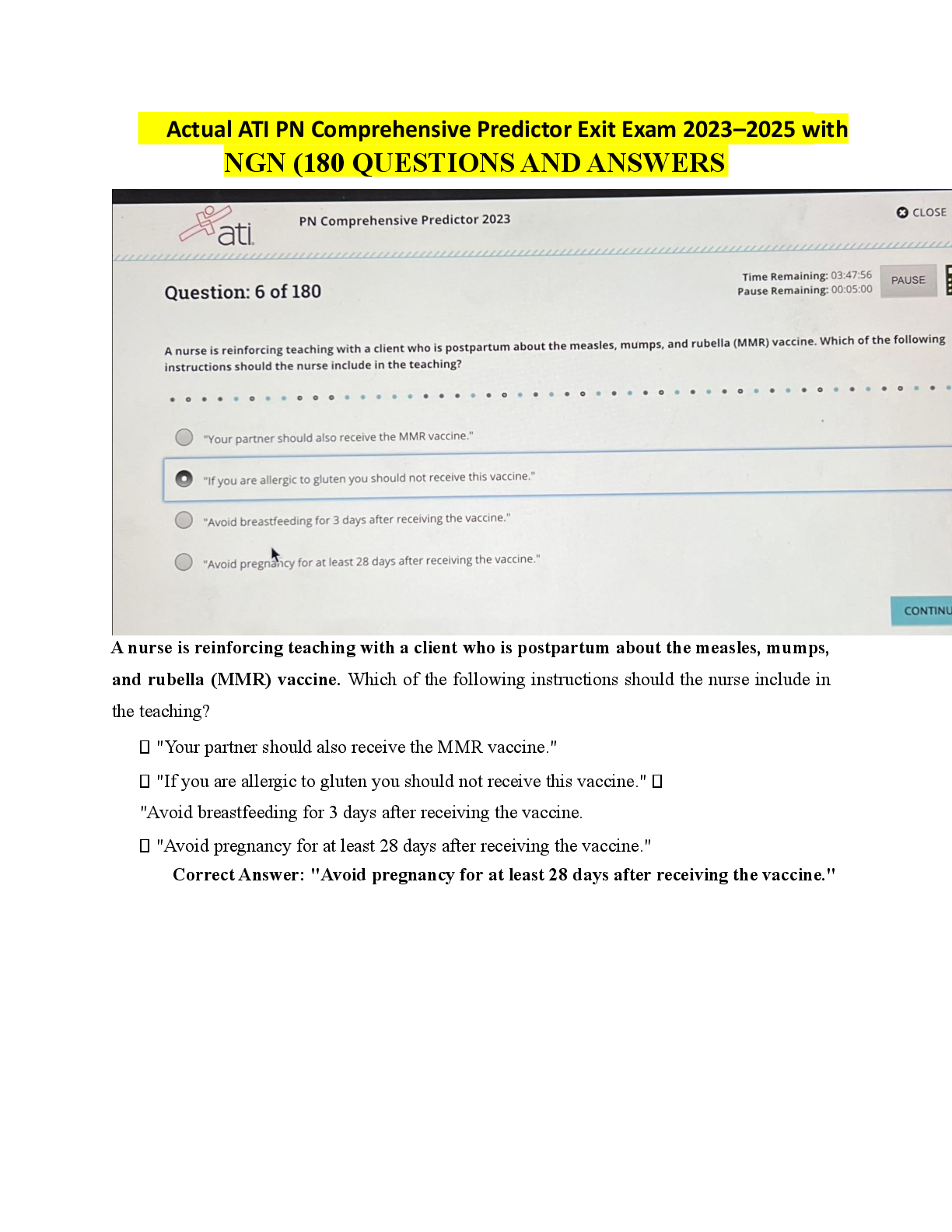
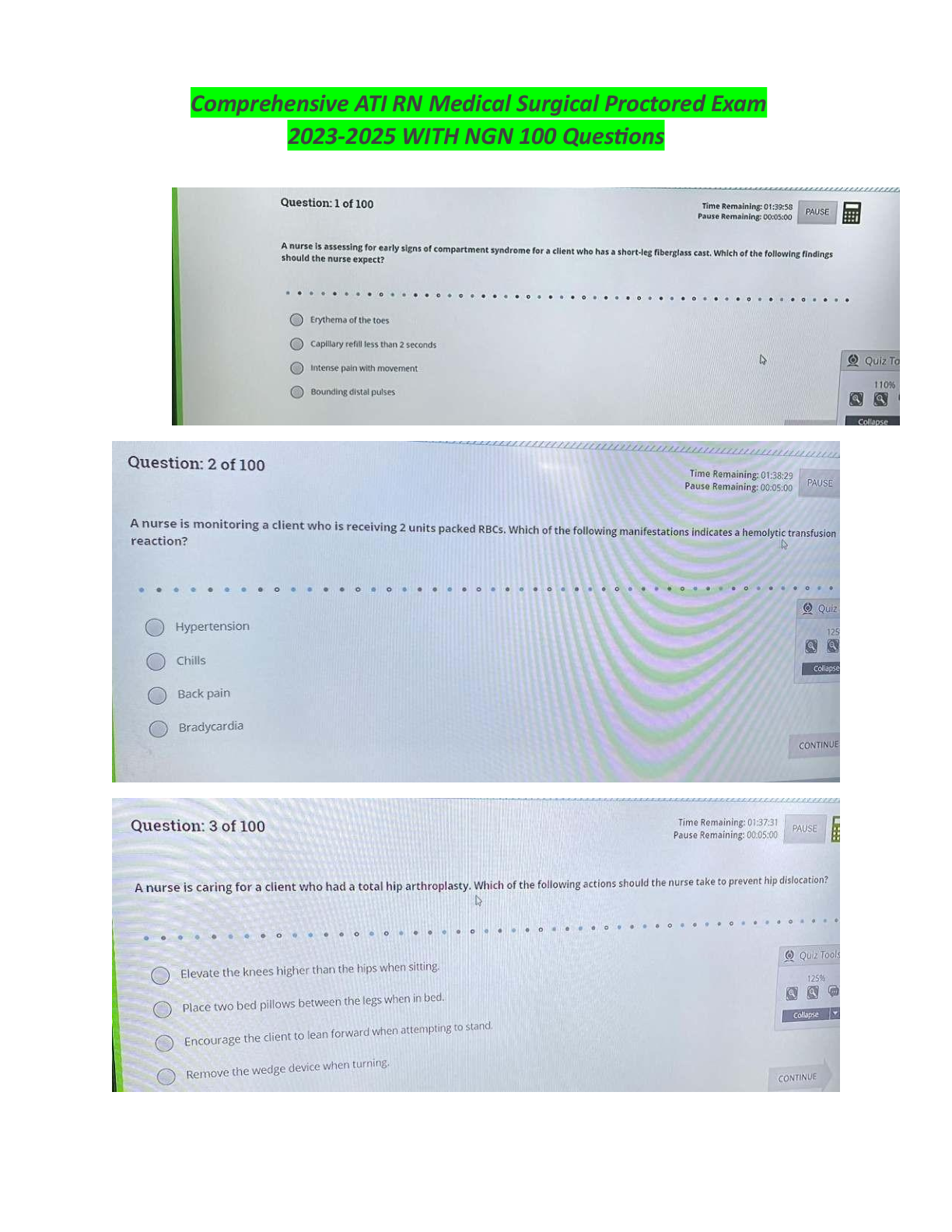
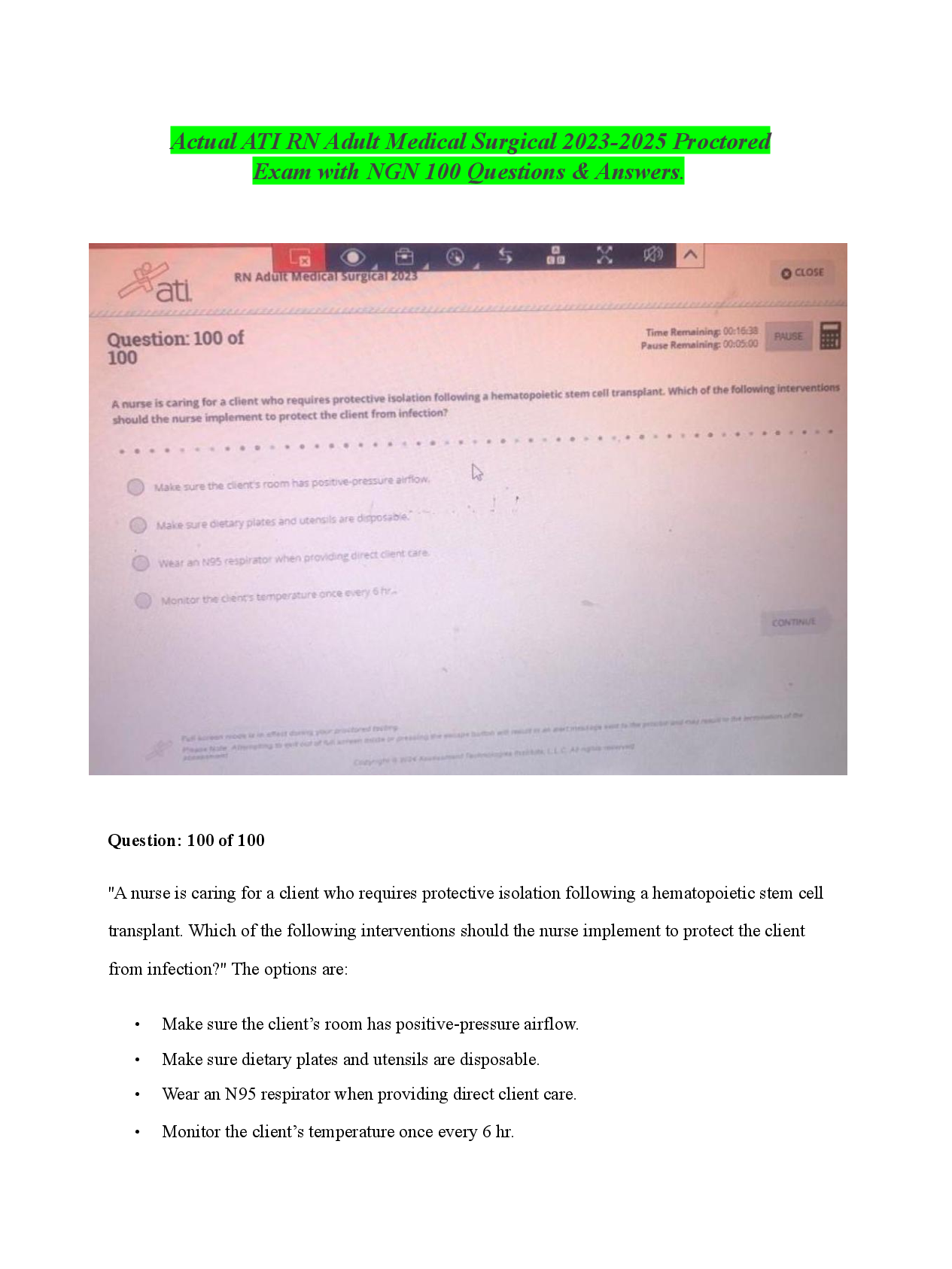
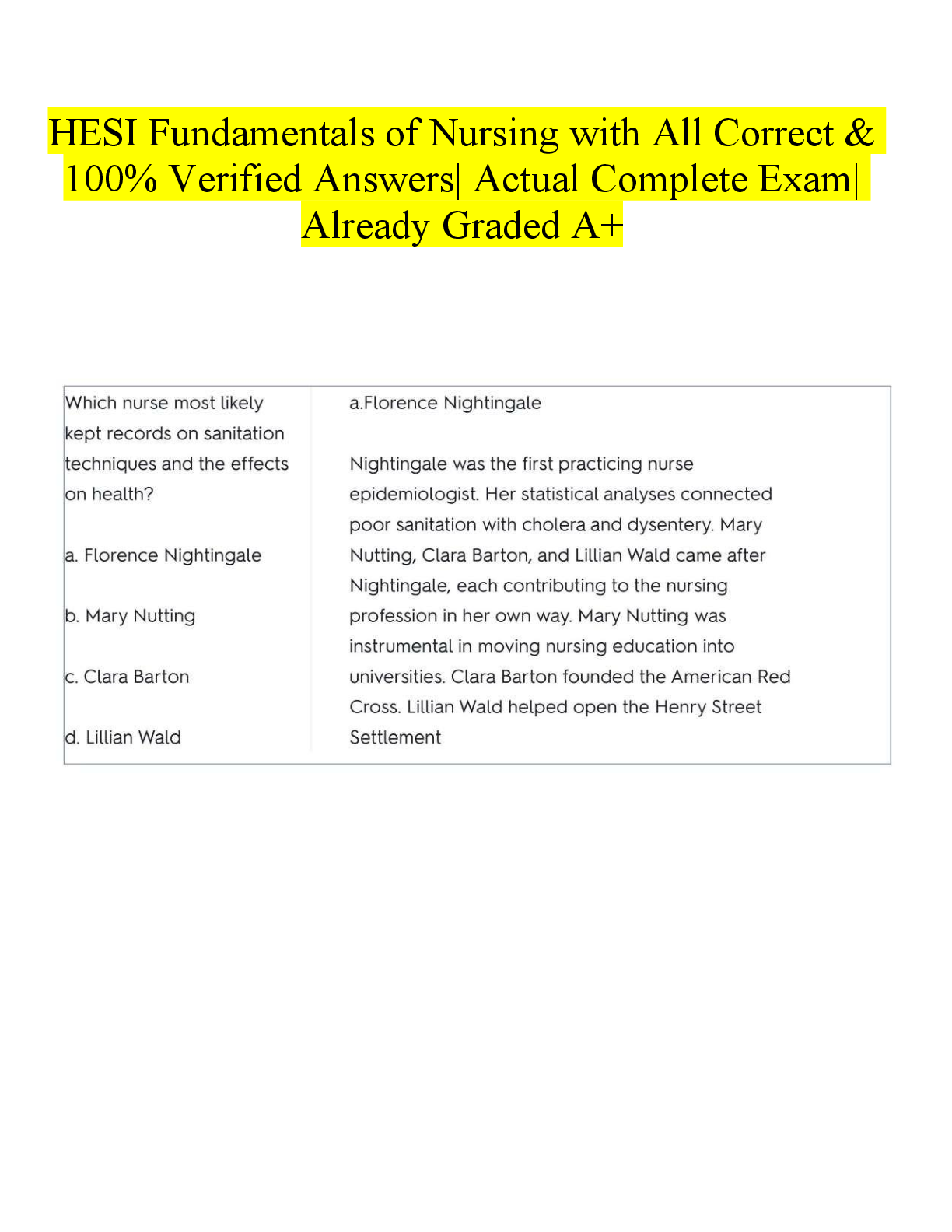
Business > EXAM > PCNSA - Questions 3 & PCNSA Domain 3|103 Questions with Verified Answers,100% CORRECT (All)
PCNSA - Questions 3 & PCNSA Domain 3|103 Questions with Verified Answers,100% CORRECT
Document Content and Description Below
PCNSA - Questions 3 & PCNSA Domain 3|103 Questions with Verified Answers Paloalto networks security operating platform is designed for which 3 purposes? - CORRECT ANSWER consume innovations quick ... ly focus on what matters prevent successful cyberattacks which item is not one of the six primary components of the palo alto networks security operating platform - CORRECT ANSWER WildFire Which cloud delivered security service provides instant access to community based threat data? - CORRECT ANSWER AutoFocus which cloud delivered security services provides security for branches and mobile users? - CORRECT ANSWER GlobalProtect Which palo alto networks security operating platform component perovides access to apps from palo alto networks, third parties, and customers? - CORRECT ANSWER Application Framework Which palo alto networks firewall feature provides all of the following: stops malware, exploits protection while endpoints are online or offline detect threats.... - CORRECT ANSWER Traps Which management features does the control plane provide? - CORRECT ANSWER logging reporting firewall configuration which 3 data processing features does the data plane provide? - CORRECT ANSWER network processing security processing signature matching what are 3 components of the network processing module? - CORRECT ANSWER QoS NAT Flow control which approach most accurately defines that PA SP3 architecture? - CORRECT ANSWER scan it all, scan it once what is the result of using a stream-based design of architecture? - CORRECT ANSWER superior performance which security model does pa networks recommend that you deploy? - CORRECT ANSWER zero trust the zero trust model is implemented to specifically address which type of traffic? - CORRECT ANSWER east-west what are the 3 main concepts of zero trust? - CORRECT ANSWER all resources are accessed in a secure manner access control is on a need-to-know basis all traffic is logged and inspected which 2 statements are true about zero trust - CORRECT ANSWER traffic is inspected laterally traffic is inspected east-west which 3 pa networks products secure your network? - CORRECT ANSWER aperture url filtering wildfire blocking just one stage of the cyber-attack lifecycle is all the is needed to protect a company from attack? - CORRECT ANSWER true what are 2 stages of the cyber-attack lifecycle - CORRECT ANSWER weaponization and delivery command and control command and control can be prevented through which two methods? - CORRECT ANSWER dns sinkholing url filtering exploitation can be mitigated by which 2 actions? - CORRECT ANSWER keeping systems patched blocking known and unknown vuln exploits on the endpoint what are 2 firewall management methods? - CORRECT ANSWER cli xml api which 2 devices are used to connect a computer to the firewall for management purposes? - CORRECT ANSWER serial cable rj-45 ethernet cable what is the default ip address of the mgt interface? - CORRECT ANSWER 192.168.1.1 what are the 2 default services that are available on the mgt interface? - CORRECT ANSWER https ssh service route traffic has security policy rules applied against it? - CORRECT ANSWER true service routes may be used to forward which 2 traffic types out of a data port? - CORRECT ANSWER external dynamic lists palo alto networks updates which plane does the running-config reside on? - CORRECT ANSWER data which plane does the candidate config reside on? - CORRECT ANSWER control candidate config and running config files are saved as which file type? - CORRECT ANSWER xml which command must be performed on the firewall to activate any changes? - CORRECT ANSWER commit which command backs up config files to a remote network device? - CORRECT ANSWER export the command "load named configuration snapshot" overwrites the current candidate config with which 3 items - CORRECT ANSWER custom-named candidate config snapshop custom-named running config that you imported current running config (running-config.xml) what is the shortest time interval that you can configure a pa fw to download wildfire updates? - CORRECT ANSWER 1 minute what is the publishing interval for wildfire updates, with a valid wildfire license? - CORRECT ANSWER 5 minutes a pa fw automatically provides a backup of the config during a software upgrade - CORRECT ANSWER true if you have a threat prevention subscription and not a wildfire subscription, how long must you wait for the wildfire signatures to be added into the antivirus update? - CORRECT ANSWER 12 to 48 hours which 3 actions should you complete before you upgrade to a newer version of the software? - CORRECT ANSWER review release notes ensure fw is connected to a reliable power source create and externally store a backup what are 5 ways to download software? - CORRECT ANSWER over the mgt interface on the control plane over a data interface on the data plane upload from a computer from the pa networks customer portal from panorama what statements are true about that admin profile role - CORRECT ANSWER it can be used for CLI commands it can be used for XML API pan-os software supports which 2 authentication types - CORRECT ANSWER RADIUS TACAS+ which 2 dynamic role types are available in the PAN-OS software? - CORRECT ANSWER Superuser device administrator (read-only) which type of profile does an Authentication Sequence include? - CORRECT ANSWER authentication an authentication profile includes which other type of profile? - CORRECT ANSWER server dynamic roles are called "dynamic" because you can customize them? - CORRECT ANSWER false what is used to override globa minimum password complexity requirements? - CORRECT ANSWER password profile which 2 default zones are included with the pan-os software? - CORRECT ANSWER interzone intrazone which 2 zone types are valid? - CORRECT ANSWER tap virtual wire what is the zone type used to pas traffic between? - CORRECT ANSWER virtual systems which 2 statements are correct? - CORRECT ANSWER interfaces do not have to be configured before you can create a zone an interface can belong to only 1 zone which 3 interface types can belong in a layer 3 zone - CORRECT ANSWER loopback layer 3 tunnel what is used to control traffic through zones? - CORRECT ANSWER security policy rules which 2 actions can be done with a tap interface? - CORRECT ANSWER decrypt traffic log traffic which 2 actions can be done with a virtual wire interface? - CORRECT ANSWER nat log traffic which 2 actions can be done with a layer 3 interface - CORRECT ANSWER nat route layer 3 interfaces support which 2 items? - CORRECT ANSWER nat ipv6 layer3 interfaces support which 3 advance settings? - CORRECT ANSWER ndp configuration link speed configuration link duplex configuration layer 2 interfaces support which 3 items? - CORRECT ANSWER traffic examination forwarding of spanning tree bpdus traffic shaping via qos which 2 interface types support subinterfaces? - CORRECT ANSWER virtual wire layer 2 which 2 statements are true regarding layer 3 interfaces? - CORRECT ANSWER you can configure a layer 3 interface with one or more as a dhcp client you can apply an interface management profile to the interface what is the default administrative distance of a static route within the pan-os software - CORRECT ANSWER 10 which 2 dynamic routing protocols are available in the pan-os software? - CORRECT ANSWER ripv2 ospfv3 which value is used to distinguish the preference of routing protocols - CORRECT ANSWER administrative distance which value is used to distinguish the best route within the same routing protocol - CORRECT ANSWER metric in path monitoring what is used to monitor remote network devices? - CORRECT ANSWER ping what are the 2 default security policy types in pan-os - CORRECT ANSWER interzone intrazone because the first rule that matches the traffic is applied, the more specific rules must follow the more general ones - CORRECT ANSWER false for universal traffic, traffic logging is enabled by default - CORRECT ANSWER true best practice is to enable logging for the two predefined security policy rules? - CORRECT ANSWER true what will the result of one or more occurrences of shadowing? - CORRECT ANSWER a warning which type of security policy rules always exist above the 2 predefined security policies? - CORRECT ANSWER universal what are 2 source nat types - CORRECT ANSWER static dynamic a simple way to remember how to configure security policies where nat was implemented is to memorize the following? - CORRECT ANSWER pre-nat ip, post-nat zone what are 2 types of destination nat? - CORRECT ANSWER dynamic ip static what are 2 possible values for dipp nat oversubscription? - CORRECT ANSWER 1x 4x for static translations, bidirectional nat allows the firewall to create a corresponding translation in the opposite direction of the translation you configure - CORRECT ANSWER true what are 2 application dependencies for icloud-mail? - CORRECT ANSWER ssl icloud-base what does an application filter enable an administrator to do? - CORRECT ANSWER dynamically categorize multiple applications which 2 items can be added to an application group? - CORRECT ANSWER application groups applications filters what does the tcp half close3d setting mean? - CORRECT ANSWER maximum length of time that a session remains in the session table between receiving the first FIN and receiving the second FIN or RST what are 2 application characteristics? - CORRECT ANSWER excessive bandwidth use evasive what column in the applications and threats screen includes the options REVIEW APPS and REVIEW POLICIES? - CORRECT ANSWER Action what can you select to minimize the risk using of installing new app-id updates? - CORRECT ANSWER disable new app in content what are 2 benefits of vulnerability protection security profiles? - CORRECT ANSWER prevent exploitation of system flaws prevent unauthorized access to systems what 2 actions are available for antivirus security profiles? - CORRECT ANSWER allow alert which 2 http header logging options are within a url filtering profile? - CORRECT ANSWER user-agent x-forward-for what are the 2 components of denial-of-service protection? - CORRECT ANSWER zone protection profile dos protection profile and policy rules what 2 types of attacks does the pan-db prevent? - CORRECT ANSWER phishing sites http based command-and-control which 2 valid urls can be used in a custom url category? - CORRECT ANSWER www.youtube.com *.youtube.com What will be the result of one or more occurrences of shadowing? - CORRECT ANSWER A warning Which column in the Applications and Threats screen includes the options Review Apps and Review Policies? - CORRECT ANSWER Action Which link can you select in the web interface to minimize the risk of installing new App-ID updates? - CORRECT ANSWER Disable new apps in content update. Which two protocols are implicitly allowed when you select the facebook-base application? (Choose two.) - CORRECT ANSWER Web-browsing SSL What are the two default (predefined) Security policy rule types in PAN-OS software? (Choose two.) - CORRECT ANSWER Interzone Intrazone Which type of Security policy rules most often exist above the two predefined Security policies? - CORRECT ANSWER Universal What does the TCP Half Closed setting mean? - CORRECT ANSWER Maximum length of time that a session remains in the session table between reception of the first FIN and reception of the second FIN or RST. What are two application characteristics? (Choose two.) - CORRECT ANSWER Excessive bandwidth use Evasive Which two HTTP Header Logging options are within a URL Filtering profile? (Choose two.) - CORRECT ANSWER User-Agent X-Forwarded-For What are two source NAT types? (Choose two.) - CORRECT ANSWER Static Dynamic Which phrase is a simple way to remember how to configure Security policy rules where NAT was implemented? - CORRECT ANSWER Pre-NAT IP, post-NAT zone What are two types of destination NAT? (Choose two.) - CORRECT ANSWER Dynamic IP (with session distribution) Static What are two possible values for DIPP (Dynamic IP and Port NAT) oversubscription? (Choose two.) - CORRECT ANSWER 1x 4x Which statement is true regarding bidirectional NAT? - CORRECT ANSWER Which statement is true regarding bidirectional NAT? a. For static translations, bidirectional NAT enables the firewall to create a corresponding translation in the opposite direction of the translation you configure. The Policy Optimizer does not analyze which statistics? - CORRECT ANSWER Which users matched Security policies. [Show More]
Last updated: 2 years ago
Preview 1 out of 11 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Also available in bundle (1)
Click Below to Access Bundle(s)

ALL PCNSA Exam (21 Sets) Questions with Verified Answers,100% CORRECT
PCNSA Exam 59 Questions with Verified Answers,PCNSA Flash Cards Exam 117 Questions with Verified Answers,PCNSA Exam 84 Questions with Verified Answers,PCNSA Exam 132 Questions with Verified Answers,PC...
By Nolan19 2 years ago
$35
21
Reviews( 0 )
$10.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Oct 09, 2023
Number of pages
11
Written in
All
Additional information
This document has been written for:
Uploaded
Oct 09, 2023
Downloads
0
Views
90