Education > EXAM > University of Maryland CMIT FINAL TEST Exam Report Microsoft 70-411 Certification Practice Exam (All)
University of Maryland CMIT FINAL TEST Exam Report Microsoft 70-411 Certification Practice Exam
Document Content and Description Below
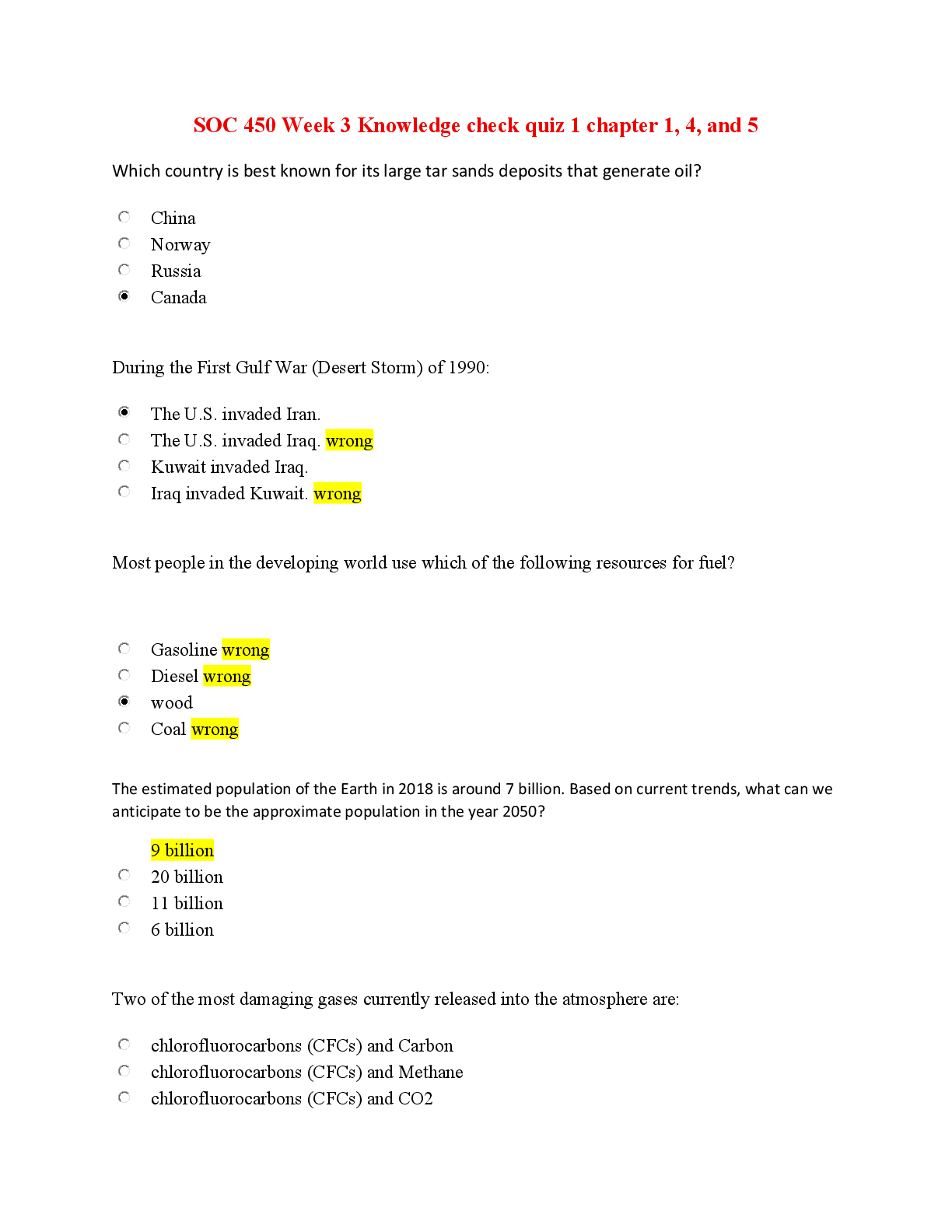
University of Maryland, University College CMIT 321 Final Exam University of Maryland, University College CMIT 321 Final Exam Final Exam Question 1 1 / 1 point __________ is a worm f... or Windows XP that downloads and executes malicious files on the compromised computer and spreads through removable storage devices. a. HTTP W32.Drom b. W32/VBAut-B c. W32/QQRob-ADN d. W32/SillyFDC-BK View Feedback Question 2 1 / 1 point __________ monitors and audits databases for security issues in real time. a. Selective Audit b. AppDetective c. AppRadar d. FlexTracer View Feedback Question 3 1 / 1 point Which of the following attacks would you choose to seize control of a legitimate user’s web application session while the session is still in progress? a. session hijacking b. DOS attack c. password sniffing d. spoofing View Feedback Question 4 1 / 1 point __________ viruses search all drives and connected network shares to locate files with an EXE or SCR extension. a. W32/Madang-Fam b. W32/Hasnot-A c. W32/Fujacks-AK d. W32/Fujacks-E View Feedback Question 5 1 / 1 point In order for traffic to get back to the attacker during session hijacking, a process called __________ is used that allows the sender to specify a particular route for the IP packet to take to the destination. a. desynchronization b. source routing c. spoofing d. TCP routing View Feedback Question 6 1 / 1 point A __________ attack occurs when an attacker sends an oversized ping packet to a victim’s device. a. BlueSmacking b. Blueprinting c. BTVoiceBugging d. Bluesnarfing View Feedback Question 7 1 / 1 point __________ can monitor a Simple Mail Transfer Protocol (SMTP) server regularly after connecting to it. a. CheckOK b. SMTPCheck c. SMTPMon d. SLCheck View Feedback Question 8 1 / 1 point Which of the following definitions best describes a wrapper? a. A wrapper is a packet-crafting technique used to perform stealthy port scans. b. A wrapper is an encryption tool used to hide messages inside image files. c. A wrapper is a method of hiding a virus inside an executable file. d. A wrapper is a tool used to bind a Trojan to a legitimate file. View Feedback Question 9 1 / 1 point _________ hijacking is a hacking technique that uses spoofed packets to take over a connection between a victim and a target machine. a. ACK b. Blind c. TCP/IP d. Network-level View Feedback Question 10 1 / 1 point Which of the following is not a Microsoft Internet Information Services vulnerability? a. ::$DATA vulnerability b. UFS integer overflow vulnerability c. Showcode.asp vulnerability d. WebDAV/RPC exploits View Feedback Question 11 1 / 1 point The __________ script allows a remote user to view the code of server-side scripts. a. Showlogin.asp b. Showcode.asp c. RemoteAccess.asp d. Remotelogin.asp View Feedback Question 12 1 / 1 point __________ automatically scans a computer, looking for cookies created by Internet Explorer, Mozilla Firefox, and Netscape Navigator, and then displays the data stored in each one. a. Cookie Viewer b. Cookie Explorer c. Cookie Browser d. Cookie Manager View Feedback Question 13 1 / 1 point __________ is an application that identifies all Bluetooth-enabled devices, their communications, and their connectivity within a given area. a. BlueSweep b. BlueWatch c. BlueKey d. BlueFire Mobile View Feedback Question 14 1 / 1 point __________ is a command-line TCP/IP packet assembler/analyzer. a. Hping2 b. Firewalk c. WUPS d. Blaster Scan View Feedback Question 15 1 / 1 point Bluetooth-enabled devices communicate via short-range, ad hoc networks known as __________. a. piconets b. uninets c. btnets d. pans View Feedback Question 16 1 / 1 point Redirections for URLs are handled with the __________ URL handler, which can cause errors in older versions of Internet Explorer. a. goto: b. mdir: c. mhtml: d. redir: View Feedback Question 17 1 / 1 point __________ is a short-range wireless communication technology intended to replace the cables connecting portable or fixed devices while maintaining high levels of security. a. Wi-Fi b. HID c. Bluetooth d. Piconet View Feedback Question 18 1 / 1 point Which of the following types of tools would be most effective in cracking UNIX passwords? a. Ophcrack b. KerbCrack c. John the Ripper d. RainbowCrack View Feedback Question 19 1 / 1 point __________ is a nonvoice service available with most GSM networks. a. CDMA b. EDO c. EDVA d. GPRS View Feedback Question 20 1 / 1 point Web applications have a three-layered architecture consisting of presentation, logic, and __________. a. application b. data layers c. transport d. HTTP View Feedback Question 21 1 / 1 point After gaining access, what is the attacker’s next goal? a. Cover their tracks. b. Start denial-of-service attacks. c. Find ways to maintain access. d. None of the above. View Feedback Question 22 1 / 1 point __________ hackers are information security professionals who specialize in evaluating, and defending against, threats from attackers. a. Gray-hat b. Black-hat c. Consulting d. Ethical View Feedback Question 23 1 / 1 point The Network News Transport Protocol service uses port __________. a. 110 b. 119 c. 135 d. 139 View Feedback Question 24 1 / 1 point Which of the following selections lists the four phases of a penetration test? a. planning, recon, hack, cleanup b. recon, exploit, payload, loot c. planning, preattack, attack, postattack d. planning, recon, attack, cleanup View Feedback Question 25 1 / 1 point __________ URLs, or intranets, are private links that only a company’s employees use. a. Internal b. Private c. Organizational d. Domain Question 26 1 / 1 point This type of port scanning technique splits a TCP header into several packets so that the packet filters cannot detect what the packets intend to do. a. UDP scanning b. IP fragment scanning c. inverse TCP flag scanning d. ACK flag scanning View Feedback Question 27 1 / 1 point __________ is a simple form of attack aimed directly at the application’s business logic. a. Authentication hijacking b. Parameter tampering c. Cookie poisoning d. Session poisoning View Feedback Question 28 1 / 1 point The __________ command displays the ARP table and is used to modify it. a. ifconfig -arp b. arp-table c. netstat -arp d. arp View Feedback Question 29 1 / 1 point A good countermeasure against hijacking includes which of the following? a. application of non-Internet protocols like http to secure sessions against hijacking b. use of biometrics and access tokens c. enforcement of a stronger password policy d. unpredictable sequence numbers View Feedback Question 30 1 / 1 point A __________, also called a packet analyzer, is a software program that can capture, log, and analyze protocol traffic over the network and decode its contents. a. sniffer b. recorder c. logger d. tapper View Feedback Question 31 1 / 1 point The Java-based __________ worm spreads through Bluetooth and affects unprotected Mac OS X 10.4 systems. a. OSX/Leap-A b. AppHook.B c. Inqtana.A d. BTHook-A View Feedback Question 32 1 / 1 point __________ is a method of gaining access to sensitive data in a Bluetooth-enabled device. a. Bluebugging b. Bluesnarfing c. BTKeylogging d. Blueprinting View Feedback Question 33 1 / 1 point __________ is an advanced version of More and provides key commands from the Vi text editor to enhance file viewing. a. Fileview b. More-x c. Less d. Head View Feedback Question 34 1 / 1 point __________ is a lightweight Knoppix version cut to 50 MB for a business-card-sized CD. a. Gnoppix b. GeeXboX c. Morphix d. Damn Small Linux View Feedback Question 35 1 / 1 point ____ is the use of Bluetooth to send messages to users without the recipients’ consent—similar to e-mail spamming. a. Bluesnarfing b. Bluebugging c. Blueprinting d. Bluejacking View Feedback Question 36 1 / 1 point The easiest way to find a Cisco router is to run __________ from a command shell. a. Nessus b. Netcat c. Traceroute d. Nmap View Feedback Question 37 1 / 1 point __________ is a common and easy form of SQL injection. The technique involves evading the logon forms. a. Command injection b. SELECT bypass c. INSERT injection d. Authorization bypass View Feedback Question 38 1 / 1 point __________ is a lightweight substitute for telnet that enables the execution of processes on other systems, eliminating the need for manual installation of client software. a. PsExec b. Alchemy Remote Executor c. EmsaFlexInfo Pro d. RemoteApp View Feedback Question 39 1 / 1 point __________ is a small utility that lists all USB devices currently connected to a computer, as well as all previously used USB devices. a. MyUSBOnly b. USB Blocker c. USB CopyNotify! d. USBDeview View Feedback Question 40 1 / 1 point A(n) __________ is a specific way to breach the security of an IT system through a vulnerability. a. hole b. exposure c. exploit d. threat View Feedback Question 41 1 / 1 point Private data stored by Firefox can be quickly deleted by selecting __________ in the Tools menu. a. Clear History b. Clear Private Data c. Delete Private Data d. Delete History View Feedback Question 42 1 / 1 point When an ethical hacker uses nslookup, which protocol are they querying? a. DNS b. HTTPS c. SMB d. NTP View Feedback Question 43 1 / 1 point There are several aspects to security, and the owner of a system should have confidence that the system will behave according to its specifications. This is called __________. a. confidentiality b. reusability c. accountability d. assurance View Feedback Question 44 1 / 1 point Information on all Linux accounts is stored in the __________ and /etc/shadow files. a. /etc/conf b. /etc/passwd c. /etc/password d. /conf/passwd View Feedback Question 45 1 / 1 point __________ gathering is the process of accumulating information from resources like the Internet that can later be analyzed as business intelligence. a. Competitive intelligence b. Tracerouting c. Passive information d. Footprinting View Feedback Question 46 1 / 1 point __________ is a tool that administrators can use to test the reliability of their critical systems and determine what actions they must take to fix any problems. a. DbEncrypt b. AppDetective c. Selective Audit d. AppRadar View Feedback Question 47 1 / 1 point A common technique used to hide data within image files uses the __________ technique. a. hex dump b. injection c. least-significant-bit d. big endian View Feedback Question 48 1 / 1 point __________ is the act of gathering information about the security profile of a computer system or organization, undertaken in a methodological manner. a. Tracerouting b. Passive information gathering c. Footprinting d. Competitive intelligence gathering View Feedback Question 49 1 / 1 point A __________ is a device that cannot function in any capacity. a. block b. brick c. rock d. cage View Feedback Question 50 1 / 1 point IT __________ are designed to evaluate an organization’s security policies and procedures. a. ping sweeps b. vulnerability assessments c. penetration tests d. security audits View Feedback Question 51 1 / 1 point What phase of attack uses social engineering and dumpster diving to find information about the target? a. scanning b. gaining access c. reporting d. reconnaissance View Feedback Question 52 1 / 1 point __________ is the exploitation of an organization’s telephone, dial, and private branch exchange (PBX) system to infiltrate the internal network in order to abuse computing resources. a. War driving b. Line dialing c. PBX driving d. War dialing View Feedback Question 53 1 / 1 point __________ allow attackers to pass malicious code to different systems via a web application. a. SQL injection attacks b. XSS vulnerabilities c. Authentication hijacking attacks d. Command injection flaws View Feedback Question 54 1 / 1 point Which website can an ethical hacker visit to see web pages from 2002? a. www.symantec.com b. www.archive.org c. www.oldwebsites.net d. www.historyoftheinternet.com View Feedback Question 55 1 / 1 point How do you defend against privilege escalation? a. Use encryption to protect sensitive data. b. Restrict the interactive logon privileges. c. Run services as unprivileged accounts. d. Run users and applications on the least privileges. View Feedback Question 56 1 / 1 point __________ is a tool for performing automated attacks against web-enabled applications. a. cURL b. dotDefender c. Burp Intruder d. AppScan View Feedback Question 57 1 / 1 point __________ is a secure method of posting data to the database. a. URL b. SQL c. GET d. POST View Feedback Question 58 1 / 1 point __________ record the parts of the website visited and can contain identifying information. a. Logs b. Records c. Cookies d. Certificates View Feedback Question 59 1 / 1 point RFID __________ collision occurs when an RFID tag reader energizes numerous tags and the tags’ respective signals are reflected back to the reader simultaneously. a. tag b. reader c. token d. signal View Feedback Question 60 1 / 1 point In a hit-and-run attack, __________. a. the attacker constantly injects bad packets into the router b. the attacker mistreats packets, resulting in traffic congestion c. the attacker injects a few bad packets into the router d. the attacker alters a single packet, resulting in denial of service View Feedback Question 61 1 / 1 point Which of the following statements best describes the rules of engagement for a penetration test? a. The rules of engagement are the systems that a tester can knock offline during a penetration test. b. The rules of engagement are the agreed-upon guidelines for a penetration test, including desired code of conduct and procedures. c. The rules of engagement define the service-level agreement and scope of a penetration test. d. The rules of engagement include the insurance and risk management associated with third-party testing. View Feedback Question 62 1 / 1 point __________ is an HTTP authentication brute-force program. It attempts to guess passwords for basic HTTP authentication by logging in to a web server. a. Authforce b. ObiWaN c. Hydra d. Cain & Abel View Feedback Question 63 1 / 1 point __________ is a unique 15- or 17-digit code used to identify a mobile station to a GSM network. a. IMEI b. SIMID c. SIM d. PhoneID View Feedback Question 64 1 / 1 point The __________ vulnerability is a vulnerability present in some servers that can be exploited by hackers in the browser address window and cause commands to be run on the server. a. malformed URL b. URL injection c. Unicode directory traversal d. folder browsing View Feedback Question 65 1 / 1 point The information resource or asset that is being protected from attacks is usually called the __________. a. key value b. target of evaluation c. main asset d. target asset View Feedback Question 66 1 / 1 point What privileges does an attacker have when running a shell after executing a successful buffer overflow against a default IIS installation on a Windows 2000 server? a. LOCAL_SYSTEM b. IUSR_COMPUTERNAME c. root d. remote-access account View Feedback Question 67 1 / 1 point An __________ share is a hidden share that allows communication between two processes on the same system. a. SMC b. IPC c. EPC d. SMB View Feedback Question 68 1 / 1 point __________ are software applications that run automated tasks over the Internet. a. Zombies b. Spiders c. Bots d. Crawlers View Feedback Question 69 1 / 1 point __________ cryptography is the most common method on the Internet for authenticating a message sender or encrypting a message. a. Symmetric b. Hash-based c. Private-key d. Public-key View Feedback Question 70 1 / 1 point __________ is a tool that combines web crawling with the capability of a personal proxy. a. WebSleuth b. BlackWidow c. SiteScope d. WSDigger View Feedback Question 71 1 / 1 point __________ occurs when hackers break into government or corporate computer systems as an act of protest. a. Hacktivism b. Cyber terrorism c. Cybercrime d. Suicide hacking View Feedback Question 72 1 / 1 point A(n) __________ is a custom command in Linux that is a substitute for a formal command string. a. user string b. system link c. alias d. link View Feedback Question 73 1/ 1 point Which of the following is not a category of security assessment? a. security audit b. rootkit detection c. vulnerability assessment d. penetration testing View Feedback Question 74 1 / 1 point __________ is a Microsoft-proprietary protocol that authenticates users and computers based on an authentication challenge and response. a. LMLAN b. Kerberos c. NTLM d. NTLAN View Feedback Question 75 1 / 1 point •Which of the following types of password attacks is not an online attack? a. sniffing b. man-in-the-middle c. hybrid d. replay View Feedback Question 76 1 / 1 point __________ is a portable, battery-powered device that mediates interactions between RFID readers and RFID tags. a. RSA blocker tag b. RFID Firewall c. RFID Guardian d. Kill switch View Feedback Question 77 1 / 1 point In Internet Explorer, the __________ zone is a security zone for sites that the user has designated as safe to visit. a. user sites b. legal sites c. white list d. trusted sites View Feedback Question 78 1 / 1 point The __________ is due to a canonicalization error in IIS 4.0 and 5.0 that allows an attacker to use malformed URLs to access files and folders located on the logical drive that includes web folders. a. canonicalization vulnerability b. ::$DATA vulnerability c. Unicode directory traversal vulnerability d. Msw3prt IPP vulnerability View Feedback Question 79 1/ 1 point The RFID __________ policy establishes the framework for many other security controls. It provides a vehicle for management to communicate its expectations regarding the RFID system and its security. a. security b. physical access c. secure disposal d. usage View Feedback Question 80 1 / 1 point The __________ file is used to determine which TTY devices the root user is allowed to log in to. a. /usr/securetty b. /etc/securetty c. /var/securetty d. /home/securetty View Feedback Question 81 1 / 1 point A __________ is a program that produces its own source code as its output. a. query b. script c. bot d. quine View Feedback Question 82 1 / 1 point Kaspersky is used as __________. a. a hacking tool against PDAs b. a hacking tool against IPHONEs c. a hacking tool against IPODs d. an antivirus for Windows Mobile View Feedback Question 83 1 / 1 point __________ is a parallelized login cracker that supports numerous protocols for attack. a. ADMsnmp b. SING c. Hydra d. John the Ripper View Feedback Question 84 1 / 1 point The contract agreement that describes the terms of service an outsourcer provides is known as a __________. a. service-level agreement (SLA) b. rule of engagement c. due contract d. project scope statement View Feedback Question 85 1 / 1 point __________ is a collection of tools for network auditing and penetration testing. a. Dsniff b. Nmap c. Hping2 d. Nemesis View Feedback Question 86 1 / 1 point __________ is usually employed when the attacker discerns that there is a low probability that these reconnaissance activities will be detected. a. Social engineering b. Direct information gathering c. Active reconnaissance d. Inactive reconnaissance View Feedback Question 87 1 / 1 point A __________ occurs when a connection between the target and host is in the established state, or in a stable state with no data transmission, or the server’s sequence number is not equal to the client’s acknowledgment number, or the client’s sequence number is not equal to the server’s acknowledgment number. a. synchronization state b. blind hijacking c. source routing d. desynchronization state View Feedback Question 88 1 / 1 point __________ gathering is performed by obtaining details that are freely available on the Internet and using various other techniques, without coming into direct contact with the organization’s internal servers. a. Competitive intelligence b. Footprinting c. Resource record d. Passive information View Feedback Question 89 1 / 1 point Ethical hackers use their knowledge and skills to __________. a. learn the details of computer systems and enhance their capabilities b. attack government and commercial businesses c. develop new programs or reverse-engineer existing software to make it more efficient d. defend networks from malicious attackers View Feedback Question 90 1 / 1 point __________ is a cable modem hacking program. It performs the task of uncapping by incorporating all the uncapping steps into one program. a. Yersinia b. OneStep: ZUP c. Zebra d. Solar Winds MIB Browser View Feedback Question 91 1 / 1 point __________ is an application that, when installed on a system, runs a background process that silently copies files from any USB flash drive connected to it. a. USB Switchblade b. USBDumper c. USB Hacksaw d. USB Copy ’em all View Feedback Question 92 1 / 1 point Firefox 2.0.0.11 cannot correctly interpret single quotation marks and spaces during authentication. This is called the __________ value of an authentication header. a. registration b. site c. domain d. realm View Feedback Question 93 1 / 1 point Tripwire protects against Trojan horse attacks by __________. a. blocking the port that the Trojan program is listening on b. removing any Trojan horse programs found on the system c. detecting unexpected changes to a system utility file that may indicate it had been replaced by a Trojan horse d. quarantining any Trojan horse programs discovered on the system View Feedback Question 94 1 / 1 point Which type of penetration test is conducted with absolutely no prior knowledge of the target environment? a. white-box testing b. gray-box testing c. red-hat testing d. black-box testing View Feedback Question 95 1 / 1 point __________ is a virus targeted against mobile personal digital assistant devices. a. Skulls b. Brador c. Doomboot.A d. Podloso View Feedback Question 96 1 / 1 point __________ provides a complete view for monitoring and analyzing activity within USB host controllers, USB hubs, and USB devices. a. USB PC Lock b. USBlyzer c. Advanced USB Monitor d. Virus Chaser USB View Feedback Question 97 1 / 1 point __________ is a method in which a sniffer is used to track down a conversation between two users. a. A man-in-the-middle (MITM) attack b. Session hijacking c. IP spoofing d. Network tapping View Feedback Question 98 1 / 1 point __________ allows applications to read and write various image file formats, including GIF. a. ImageCore b. CoreText c. ImageIO d. CoreImage View Feedback Question 99 1 / 1 point Once the Oracle database server has been traced, the first port of call is made to the __________ listener. a. SQL b. TNS c. TCP d. PL/SQL View Feedback Question 100 1 / 1 point Mac OS X includes __________, a collection of frameworks, APIs, and accompanying runtimes that allows for a host of open-source web, database, scripting, and development technologies. a. Cocoa b. Coffee c. Bean d. Xcode View Feedback Question 101 1 / 1 point __________ is an application-layer protocol that runs on UDP and is used to maintain and manage routers, hubs, and switches on an IP network. a. SMMP b. SNMP c. SMTP d. SNTP View Feedback Question 102 1 / 1 point __________ is a protocol used to create, modify, and terminate sessions such as VOIP. a. SMS b. SIP c. GSMA d. GPRS View Feedback Question 103 1 / 1 point A __________ attack adds numbers or symbols to a dictionary file’s contents to crack a password successfully. a. brute-force b. dictionary c. hybrid d. parameter manipulation View Feedback Question 104 1 / 1 point A hacker has successfully used a tool to intercept communications between two entities and establish credentials with both sides of the connection. The two remote ends of the communication never notice that the attacker is relaying the information between the two. This is called a(n) __________ attack. a. man-in-the-middle b. interceptoring c. MAC poisoning attack d. firewalking View Feedback Question 105 1 / 1 point Attackers use a technique called __________ to exploit the system by pretending to be legitimate users or different systems. a. identity theft b. impersonation c. spoofing d. flooding View Feedback Question 106 1 / 1 point Only __________ scan is valid while scanning a Windows system. a. SYN b. Null c. FIN d. Xmas View Feedback Question 107 1 / 1 point __________ reconnaissance is a hacker’s attempt to scout for or survey potential targets and then investigate the target using publicly available information. a. Active b. Passive c. Public d. Open View Feedback Question 108 1 / 1 point __________ is a command-line utility provided by Microsoft with SQL Server 2000 (and Microsoft SQL Server 2000 Desktop Engine) that allows users to issue queries to the server. a. ODBC b. SQLP c. OSQL d. SSRS View Feedback Question 109 1 / 1 point A __________ is a device that receives digital signals and converts them into analog signals, and vice versa. a. firewall b. proxy c. hub d. modem View Feedback Question 110 1 / 1 point __________, formerly called AppTapp, is a tool for jailbreaking and installing nonsanctioned third-party applications on the iPhone. a. iFuntastic b. iNdependence c. iActivator d. AppSnapp View Feedback Question 111 1 / 1 point Traceroute uses the __________ field in an IP packet to determine how long it takes to reach a target host and whether that host is reachable and active. a. IHL b. flags c. TOS d. TTL View Feedback Question 112 1 / 1 point While conducting an ethical penetration test in Europe, which Regional Internet Registry (RIR) would you use? a. APNIC b. RIPE NCC c. ARIN d. LACNIR View Feedback Question 113 1 / 1 point Which of the following password attacks is conducted using nontechnical means? a. hybrid b. brute force c. social engineering d. rainbow tables View Feedback Question 114 1 / 1 point The __________ method appends data in the URL field. a. POST b. GET c. APPEND d. URL View Feedback Question 115 1 / 1 point __________ is a programming language that permits website designers to run applications on the user’s computer. a. Java b. Ruby c. Python d. Smalltalk View Feedback Question 116 1 / 1 point __________ is an automatic identification method that uses radio waves to identify an object. a. BTID b. Wi-Fi c. Bluetooth d. RFID View Feedback Question 117 1 / 1 point In __________-level hijacking, the attacker obtains the session IDs to get control of an existing session or to create a new, unauthorized session. a. network b. data link c. transport d. application View Feedback Question 118 1 / 1 point __________ is, simply enough, looking through an organization’s trash for any discarded sensitive information. a. Trash diving b. Trash carving c. Dumpster searching d. Dumpster diving View Feedback Question 119 1 / 1 point Null sessions require access to TCP port __________. a. 139 b. 141 c. 345 d. 349 View Feedback Question 120 1 / 1 point __________ is a type of computer architecture in which multiple processors share the same memory and are each assigned different tasks to perform. a. Xcode b. Multitasking c. Cocoa d. Symmetric multiprocessing View Feedback Question 121 1 / 1 point Attackers can use a simple test to find out if an application is vulnerable to an OLE DB error. They can fill in the username and password fields with __________. a. a pound sign b. two dashes c. a single quotation mark d. double quotes View Feedback Question 122 1 / 1 point Which of the following Microsoft authentication protocols is the least secure? a. LAN Manager b. SMB c. NTLM v2 d. SQL View Feedback Question 123 1 / 1 point Which one of the following vulnerabilities is associated with Cisco routers? a. SQL injection b. HTTP Configuration Arbitrary Administrative Access c. buffer overflow d. Cisco overflow injection View Feedback Question 124 1 / 1 point The __________ are the agreed-on guidelines for a penetration test. a. rules of engagement b. project scope statements c. test requirements d. service-level agreements (SLAs) View Feedback Question 125 1 / 1 point In the TCP/IP stack, the __________ layer is where applications and protocols, such as HTTP and Telnet, operate. a. Internet b. network c. transport d. application [Show More]
Last updated: 2 years ago
Preview 1 out of 41 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$8.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Mar 08, 2021
Number of pages
41
Written in
Additional information
This document has been written for:
Uploaded
Mar 08, 2021
Downloads
0
Views
63