University of Maryland, University College CMIT 321 Final exam
Document Content and Description Below
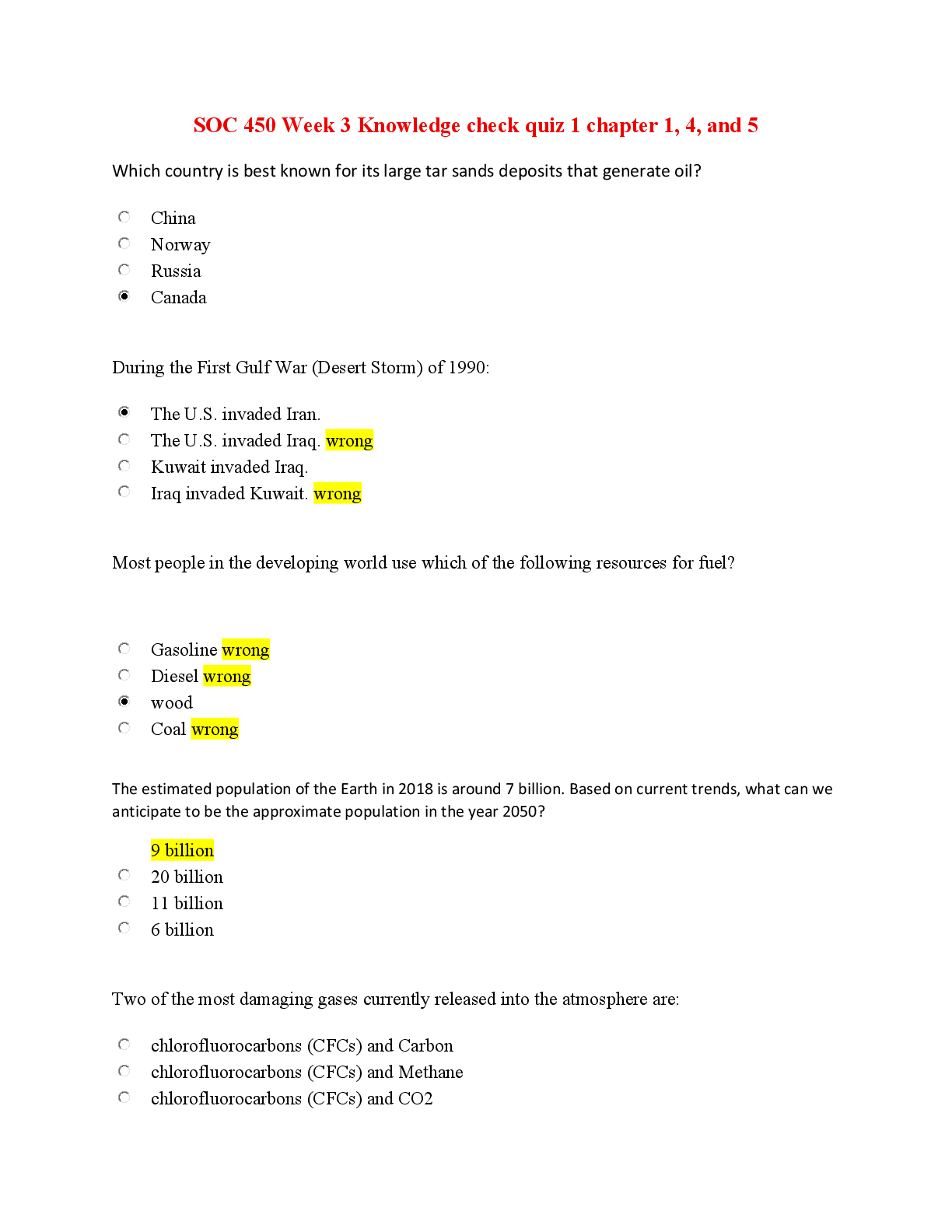
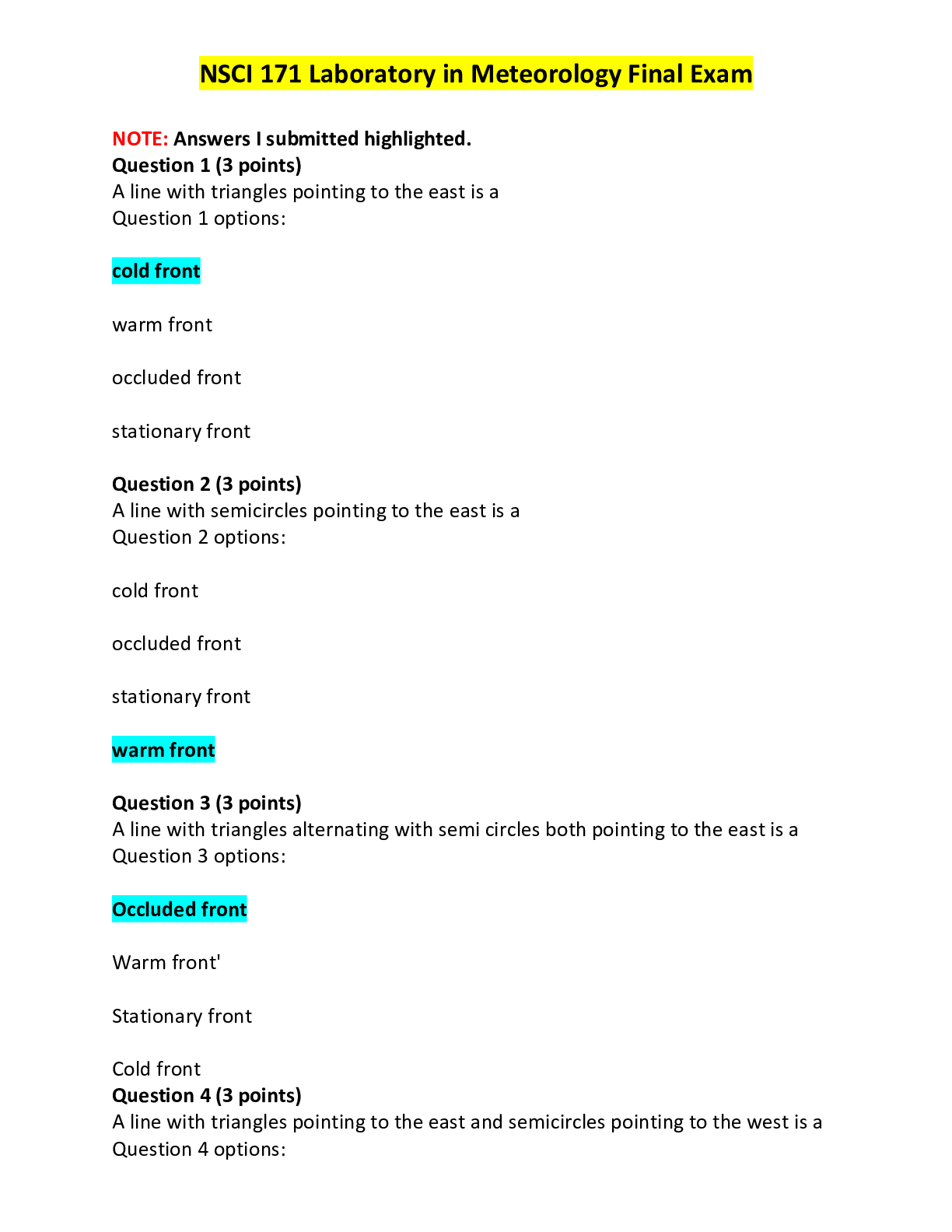
University of Maryland, University College CMIT 321 Final University of Maryland, University College CMIT 321 Final Exam Question 1 (5 points) Question 1 Unsaved The TCP 3 way handshake ... terminates after which of the following? (choose all that apply) Question 1 options: FIN RESET ACK SYN Question 2 (5 points) Question 2 Unsaved Which of the following is one of the most reliable forms of TCP scanning? Question 2 options: XMAS Scan Connect Scan Inverse TCP Flag Scan Half-open Scan Question 3 (5 points) Question 3 Unsaved Which of the following can be utilized as traceroute tool? Question 3 options: nslookup Path Analyzer Pro pingpath TTL (Time to Live) Question 4 (5 points) Question 4 Unsaved FTP uses which of the following ports? (choose all that apply) Question 4 options: 443 20 80 21 Which of the following are command line tools? (choose all that apply) Question 5 options: zenmap nmap hping3 hping2 Question 6 (5 points) Question 6 Unsaved ICMP and Port Scanning are the same. Question 6 options: True False Question 7 (5 points) Question 7 Unsaved A ping scan is also a(n) ___. Question 7 options: UDP Scan ICMP Scan Stealth Scan ACK Flag Probe Scan Question 8 (5 points) Question 8 Unsaved How many bytes of the TCP/IP Packet are for the data? Question 8 options: 32 8 16 56 Question 9 (5 points) Question 9 Unsaved Which three of the following are tools used for footprinting? Question 9 options: Maltego FOCA Aircrack-ng Recong-ng Question 10 (5 points) Question 10 Unsaved What does the Simple Service Discovery Protocol (SSDP) do? (choose all that apply) Question 10 options: Can be vulnerable to denial of service Uses multicast addresses Controls Communication for the Universal Plug and Play Service Not work behind a firewall Question 11 (5 points) Question 11 Unsaved After an ICMP scan, if a host is live it will send back: Question 11 options: ICMP Echo Reply ICMP Echo Request SYN-ACK ACK Which of the following is NOT a TCP flag? Question 12 options: RESET SYN ACK ICMP Question 13 (5 points) Question 13 Unsaved What is the first part of the TCP 3 way handshake? Question 13 options: FIN SYN SYN-ACK ACK Question 14 (5 points) Question 14 Unsaved Which of the following flags will indicate that there is a new sequence number? Question 14 options: ACK SYN URG PSH Question 15 (5 points) Question 15 Unsaved Binging is an example of a footprinting tool which uses __________ to perform queries. Question 15 options: .Net Framework Bing API DNS Reverse Lookups Question 16 (5 points) Question 16 Unsaved What is the second part of the TCP 3 way handshake? Question 16 options: SYN ACK FIN SYN-ACK Question 17 (5 points) Question 17 Unsaved Footprinting tools will help gather which three of the following pieces of information about a target? Question 17 options: Host Names Process Lists IP Addresses DNS Records Question 18 (5 points) Question 18 Unsaved According to the text, what is the first step in scanning? Question 18 options: Look for vulnerabilities Launch a buffer Overflow Identify live systems Create a custom packet Question 19 (5 points) Question 19 Unsaved This vulnerability scanner is from Microsoft. Question 19 options: Nessus Core Impact Cloud Scan MBSA Question 20 (5 points) Question 20 Unsaved How many bits is an IPv6 address? Question 20 options: 128 bits 32 bits 64 bits 16 bits Question 2 (5 points) Question 2 Unsaved SNMP uses which of the following ports? (choose all that apply) Question 2 options: 162 161 22 445 Question 3 (5 points) Question 3 Unsaved How many bits is an IPv4 address? Question 3 options: 64 bits 32 bits 16 bits 128 bits Question 4 (5 points) Question 4 Unsaved Tracert counts the number of __________ to a destination IP Address. Question 4 options: Lookup Requests Pings Hops ICMP Echo Replies If you want to mask (or spoof) your IP Address, use this type of scan: Question 5 options: IDLE, IPID Scan Stealth Scan UDP Scan ACK Flag Probe Scan Angry IP Scanner allows you to send the output to which of the following? (choose all that apply) Question 6 options: TXT XML IP-Port List file CSV Question 7 (5 points) Question 7 Unsaved Netbios uses which of the following ports? (choose all that apply) Question 7 options: 137 139 138 140 Types of scanning include which of the following? (Choose all that apply) Question 8 options: Port Vulnerability Buffer Overflows Network Question 9 (5 points) Question 9 Unsaved This tool will allow you to create a custom network packet: Question 9 options: Wireshark Snort ColaSoft TCPDUMP Question 10 (5 points) Question 10 Unsaved The website zabasearch provides what type of information to users? Question 10 options: Webserver software Version IP Addresses Operating System Phone Numbers and Addresses Question 1 (5 points) Question 1 Unsaved Which of the following Windows Utilities can be utilized to enumerate hosts? Question 1 options: net view net Use net stop net start Question 2 (5 points) Question 2 Unsaved The NETBIOS Name can be up to how many characters? Question 2 options: 24 characters 15 characters 16 characters 128 characters Question 3 (5 points) Question 3 Unsaved Commonly used SNMP enumeration tools include which of the following? Question 3 options: hping3 nmap Angry IP Scanner IP Network Browser Question 4 (5 points) Question 4 Unsaved SMTP uses which port? Question 4 options: TCP Port 110 TCP Port 25 UDP Port 993 UDP Port 161 Question 5 (5 points) Question 5 Unsaved User DataGram Protocol can be used for which three of the following? Question 5 options: Video Reliable Communication Teleconferencing Streaming Audio Question 6 (5 points) Question 6 Unsaved The SNMP agent receives requests on which port? Question 6 options: TCP Port 162 UDP Port 162 UDP Port 161 TCP Port 161 Question 7 (5 points) Question 7 Unsaved The Management Information Base (MIB) includes which of the following? (choose all that apply) Question 7 options: Scalar and Tabular Objects File and Folder Permissions OID Numbers User Accounts Question 8 (5 points) Question 8 Unsaved Typically SMB over TCP uses this port for transmission: Question 8 options: 161 137 445 139 Which of the following accurately describes Transmission Control Protocol? (choose all that apply) Question 9 options: Can terminate a connection Connection-less oriented protocol Provides acknowledgment Supports Retransmission of lost Data Question 10 (5 points) Question 10 Unsaved SNMP protocol responds to managers on which port? Question 10 options: UDP Port 161 TCP Port 161 TCP Port 162 UDP Port 162 Question 11 (5 points) Question 11 Unsaved According to the text, having several organizational units makes a company vulnerable to attack. Question 11 options: True False Question 12 (5 points) Question 12 Unsaved Which of the following are SNMP enumeration tools? (choose all that apply) Question 12 options: Getif Softperfect Spiceworks Nmap Question 13 (5 points) Question 13 Unsaved Which of the following are LDAP enumeration tools? (choose all that apply) Question 13 options: SnScan Active Directory Explorer JXplorer LEX Question 14 (5 points) Question 14 Unsaved NETBIOS uses which of the following? (choose all that apply) Question 14 options: TCP Port 139 TCP Port 22 UDP Port 138 UDP Port 137 Typically SNMP uses this port for transmission: Question 15 options: 161 137 139 445 Question 16 (5 points) Question 16 Unsaved The SMTP Protocol provides 3 built in commands. What are they? Question 16 options: VRFY RCPT TO FINGER EXPN Question 17 (5 points) Question 17 Unsaved Typically NBNS uses this port for transmission: Question 17 options: UDP Port 139 UDP Port 137 TCP Port 139 TCP Port 137 Question 18 (5 points) Question 18 Unsaved Which port is used for the Global catalog Service? Question 18 options: 25 3389 389 3268 Question 19 (5 points) Question 19 Unsaved Which of the following Management Information Base (MIB) files contains information about server services? Question 19 options: DCHP.MIB WINS.MIB HOSTMIB.MIB LNMIB2.MIB The psexec utility can be utilized to perform which of the following actions? Question 20 options: Show open files Launch an Interactive Command Session Get System Information List Processes Question 1 (5 points) Question 1 Unsaved IP Network Browser can determine this on a Cisco Device (select all that apply): Question 1 options: ARP Tables Passwords IOS Version Cards Installed Question 2 (5 points) Question 2 Unsaved Which of the following are Network Time Protocol (NTP) enumeration commands? (choose all that apply) Question 2 options: ntpq Net time ntpdate ntptrace Question 3 (5 points) Question 3 Unsaved SMTP commands include which of the following? (choose all that apply) Question 3 options: RESET MGET DATA HELO Question 4 (5 points) Question 4 Unsaved NETBIOS Name Resolution is supported in IPv6: Question 4 options: False True Question 5 (5 points) Question 5 Unsaved The pstools include which of the following? (choose all that apply) Question 5 options: psloglist pslists psexec psdumpram Question 6 (5 points) Question 6 Unsaved NTP uses: Question 6 options: UDP Port 123 UDP Port 139 TCP Port 123 TCP Port 139 Question 7 (5 points) Question 7 Unsaved Which of the following is NOT a Social Engineering technique? Question 7 options: Exploiting the Victim Selecting a Victim Research on a Target Company Developing a Relationship Question 8 (5 points) Question 8 Unsaved What are three ways that an attacker can perform human-based social engineering? Question 8 options: Posing as someone important Posing as an legitimate end user Deploying Malware Posing a s Technical Support Question 9 (5 points) Question 9 Unsaved Where, in Windows, are the password hashes of the user account stored? Question 9 options: Passwd File Encrypted File Shadow File SAM Question 10 (5 points) Question 10 Unsaved This command provides you with netbios statistics: Question 10 options: netbtstat netstat nbtstat net use The characteristics of these Trojans include the ability to open and close the CD-ROM tray (check all that apply): Question 1 options: Poison Ivy Dark Comet SubSeven NetBus Question 2 (1 point) Question 2 Unsaved According to the text, a Denial of Service Attack caused major problems for: Question 2 options: Target The Department of Defense DALnet IRC Network 780th Military Intelligence Brigade Which of the following uses direct client to client (DCC)? Question 3 options: File Sharing with Mapped Drives Email Clients such as Outlook Express Internet Browser Internet Relay Chat Question 4 (1 point) Question 4 Unsaved What are the three phases used to carry out a session fixation attack? Question 4 options: fixation phrase tear-down phrase entrance phrase set up phrase Your Supervisor is concerned about the use of port 139 in your environment. What measure do you recommend? Question 5 options: Use TCP Wrappers Disable File and Print Sharing Turn on the Windows Firewall Block ICMP so the host cannot be detected Which of the following is an example of a wrapper program that can be used to hide a Trojan? Question 6 options: Kriptomatic Obfuscator Binder Trojan Warrior Malware Toolbox Question 7 (1 point) Question 7 Unsaved This is an example of a Trojan that can be utilized for Website Defacement: Question 7 options: WGET CrimePack HTTrack Restorator MAC spoofing is also referred to as: Question 8 options: MAC attack MAC intercept MAC hijacking MAC duplicating Session hijacking refers to an attack where an attacker: Question 9 options: takes over a valid TCP session takes over a valid ICMP session takes over a valid TCP or UDP session takes over a valid UDP session According to your text, examples of malware include which of the following? (choose all that apply) Question 10 options: Botnet Crypter Metasploit Ransomware Question 11 (1 point) Question 11 Unsaved With a session fixation attack, the attacker uses a: Question 11 options: cookie valid SID legitmate packet corrupt packet Question 12 (1 point) Question 12 Unsaved Network level hijacking includes (choose all that apply): Question 12 options: packet capturing of TCP traffic session ID's being obtained packet capturing of UDP traffic taking over of an HTTP session This will help prevent DNS spoofing attacks (choose all that apply): Question 13 options: primary zones SSH secondary zones SSL Session hijacking types include: Question 14 options: stateful passive stateless active Question 15 (1 point) Question 15 Unsaved An attacker may use packet sniffing tools such as these to intercept traffic, (choose all that apply): Question 15 options: nmap hping3 wireshark smartsnif Question 16 (1 point) Question 16 Unsaved This tool can help detect arp spoofing: Question 16 options: inverse arp smac rarp xarp Question 17 (1 point) Question 17 Unsaved Cross-site Request Forgery is also known as: Question 17 options: XXS SQL injection a one click attack Buffer Overflow Question 18 (1 point) Question 18 Unsaved A hijacking attack includes (choose all that apply): Question 18 options: relies on the legitimate user takes over of an HTTP session uses stolen credentials pretends to be another user Question 19 (1 point) Question 19 Saved A spoofing attack includes (choose all that apply): Question 19 options: pretends to be another user relies on the legitimate user takes over of an HTTP session uses stolen credentials Question 20 (1 point) Question 20 Saved Session hijacking takes advantage of: Question 20 options: flaws in encryptions flaws in HTTPS inexperienced end users flaws in TCP/IP Application level hijacking includes (choose all that apply): Question 1 options: taking over of an HTTP session packet capturing of TCP traffic session ID's being obtained packet capturing of UDP traffic Question 2 (1 point) Question 2 Unsaved There are many purposes of malware, including which of the following? (choose all that apply) Question 2 options: Obtaining Passwords Disable Networking Functions Remove the Default LAN Route Making a Computer Useless What is the best course of action to remove Autorun for Removable Disks and CD Drives in Windows? Question 3 options: Tape the USB ports Provide Users without Administrative Rights Remove the CD-ROM Drive from the System Use Group Policy Question 4 (1 point) Question 4 Saved This tool will allow you to spoof a MAC address: Question 4 options: inverse arp rarp xarp smac Question 5 (1 point) Question 5 Unsaved What were the two dominant attack strategies identified in Symantec's Threat Report? Question 5 options: Advanced Persistent Threats Distributed Denial of Service Broader Strokes Focused Attack Question 8 (1 point) Question 8 Unsaved You can filter for an IP Address in Wireshark by typing: Question 8 options: IP.ADDR == IP.Address == IP == IP = Question 1 (5 points) Question 1 Unsaved This DOS tool works from a mobile platform Question 1 options: AnDOSid LOIC HULK DOSSIM Question 2 (5 points) Question 2 Unsaved Which of the following are true when referring to the term phalshing? (choose all that apply) Question 2 options: Something that can cause a device to render hardware inoperable An email attack in which the user is enticed to click on links A type of permanent Denial of Service Can be known as bricking Question 3 (5 points) Question 3 Unsaved Tor's hammer will run behind the TOR network. Question 3 options: True False Question 4 (5 points) Question 4 Unsaved Which of the following are password cracking techniques? (choose all that apply) Question 4 options: Brute Force Attacks Guessing Dictionary Attacks Hybrid Attack Question 5 (5 points) Question 5 Unsaved BlackShades Net can best be described as a: Question 5 options: Bot Wrapper RAT DDoS Tool Question 6 (5 points) Question 6 Unsaved DDoS Sim features include which of the following? (choose all that apply) Question 6 options: zombies simulation Application Layer attacks TCP Based Attacks random source IP Address Question 7 (5 points) Question 7 Unsaved Tor's hammer will kill Apache 2X with less than: Question 7 options: 128 threads 16 threads 64 threads 256 threads Question 8 (5 points) Question 8 Unsaved Password cracking tools include (choose all that apply): Question 8 options: Cain Brutus Wireshark Hydra Question 9 (5 points) Question 9 Unsaved According to your text, most of the webservers run which of the following? Question 9 options: Apache Google NGINX Microsoft IIS Question 10 (5 points) Question 10 Unsaved Central Source propagation commonly utilized which of the following protocols? (choose all that apply) Question 10 options: FTP RDP TFTP RPC Question 11 (5 points) Question 11 Unsaved To crash a webserver, what should an attacker target? (Select all that apply) Question 11 options: Network Bandwidth Server Memory Database CPU Question 12 (5 points) Question 12 Unsaved What are the 3 techniques that can be utilized to propagate malicious code? Question 12 options: Central Source Back Dating Back Chaining Autonomous Question 13 (5 points) Question 13 Unsaved The two types of honeypots include: Question 13 options: IPS high interaction low interaction IDS Question 14 (5 points) Question 14 Unsaved SYN flooding takes advantage of which of the following? (choose all that apply) Question 14 options: A flaw in some firewalls which do not restrict ICMP traffic by default Not replying to SYN/ACKs A flaw in how the three-way handshake can be implemented Holding the incomplete connection for a period up to one second Question 15 (5 points) Question 15 Unsaved A hotfix is a small piece of software used to fix a bug or problems. Question 15 options: True False Question 16 (5 points) Question 16 Unsaved Permutation Scanning involves which of the following? Question 16 options: Looking for new vulnerable machines on the local subnet Collecting a list of possibly vulnerable machines Using a pseudorandom function Using information from infected machines Question 17 (5 points) Question 17 Unsaved Which of the following steps can be used to help secure Web Servers? Question 17 options: Use a DMZ Disconnect from the WAN Switch from Linux from Microsoft Switch from Microsoft from Linux Question 18 (5 points) Question 18 Unsaved A patch is a package used to address a critical defect in a live environment. Question 18 options: True False Using wget is one way to get a robots.txt file. Question 19 options: True False Question 20 (5 points) Question 20 Unsaved IIS for Microsoft supports (choose all that apply): Question 20 options: NNTP HTTP HTTPS RDP Question 1 (5 points) Question 1 Unsaved When an attacker is performing a denial of service and a SYN attack is initiated which of the following things happens? (choose all that apply) Question 1 options: A large number SYN requests is sent to the target A large number of ACK packets is sent to the target The actual source address is used A fake source address is used Question 2 (5 points) Question 2 Unsaved Tor's hammer will kill Apache 1X with less than: Question 2 options: 16 threads 128 threads 256 threads 64 threads Question 3 (5 points) Question 3 Unsaved Webserver footprinting can be down with (choose all that apply): Question 3 options: ID Serve Telnet Netcraft Httprecon Question 4 (5 points) Question 4 Unsaved SSH uses which of the following? Question 4 options: UDP Port 22 UDP Port 23 TCP port 23 TCP Port 22 Question 5 (5 points) Question 5 Unsaved Which of the following can be used to identify DoS Attacks? Question 5 options: MD5 SHA-256 Cusum SHA-1 Question 6 (5 points) Question 6 Unsaved Egress filtering includes (choose all that apply): Question 6 options: scanning packet headers of IP packets leaving the network scanning packet headers of IP packets entering the network not allowing unauthorized packets entering the network not allowing unauthorized packets to leave the network Question 7 (5 points) Question 7 Unsaved What two things happen when a distributed reflective denial of service attack (DRDoS) is used? Question 7 options: Traffic will be directed to intermediate hosts Traffic to the secondary hosts will originate from the intermediate hosts Traffic will be directed to secondary victims The source Address will be spoofed Question 8 (5 points) Question 8 Unsaved Which of the following is an Internet Relay Chat bot? Question 8 options: Dark Comet Netbus SubSeven EnergyMech Question 9 (5 points) Question 9 Unsaved LOIC will kill the server with (choose all that apply): Question 9 options: UDP Requests TCP Requests ICMP Requests HTTP Requests Question 10 (5 points) Question 10 Unsaved It was well publicized that BlackShades Net was used as an attack tool against: Question 10 options: Syrian Political Activists RSA Target Sony Pictures Question 1 (5 points) Question 1 Unsaved Which of the following are part of the aircrack-ng suite? (Choose all that apply) Question 1 options: Airodump-ng Aircrack-ng Airdecap-ng Packetforge-ng Question 2 (5 points) Question 2 Unsaved In this Blue tooth attack, the attacker takes control of the device: Question 2 options: Blue Bugging Blue Cracking Bluesmacking Blue Snarfing Question 3 (5 points) Question 3 Unsaved Best Wireless Security Practices include (Choose all that apply): Question 3 options: Change the Default SSID Disable SSID Broadcast Use WEP Change the Router Access Password Question 4 (5 points) Question 4 Unsaved SQL Databases include (Choose all that apply): Question 4 options: Microsoft SQL MS Access My SQL Oracle Question 5 (5 points) Question 5 Unsaved Which of the following uses Orthogonal Frequency Division Multiplexing? (choose all that apply) Question 5 options: 802.11n 802.11g 802.11a 802.11b Question 6 (5 points) Question 6 Unsaved According to the text, by 2018, what percent of enterprises will specify Wi-Fi as the default connection? Question 6 options: 75% 40% 25% 60% This Blue tooth attack tries to get sensitive data: Question 7 options: Bluesmacking Blue Bugging Blue Cracking Blue Snarfing Question 8 (5 points) Question 8 Unsaved Which of the following are types of wireless attacks? (Choose all that apply) Question 8 options: ARP Poisoning Denial of Service Attacks Fragmentation Attacks MAC Spoofing Attacks Question 9 (5 points) Question 9 Unsaved The MAC Address of an access point is referred to as the ____. Question 9 options: ESSID SSID BSSID OFDM This antenna is based on the principal of a satellite dish and can pick up Wi-Fi signals from 10 miles away: Question 10 options: Parabolic Dipole Omni Directional Yagi Question 11 (5 points) Question 11 Unsaved Blue Tooth modes include (Choose all that apply): Question 11 options: Non-pairable Airplane Pairable Hotspot Question 12 (5 points) Question 12 Unsaved Wi-Fi Chalking includes which of the following? (choose all that apply) Question 12 options: War Flying War Chalking War Driving War Walking Question 13 (5 points) Question 13 Unsaved Which of the following tools will allow you crack WPA Passphrases and WEP keys? (Choose one) Question 13 options: Airdecap-ng Airodump-ng Aircrack-ng Packetforge-ng Question 14 (5 points) Question 14 Unsaved An SSID (select all that apply): Question 14 options: Is part of the frame header Will be encrypted in WEP or WPA/WPA2 is utilized Is Case Sensitive Can be up to 32 characters Question 15 (5 points) Question 15 Unsaved Blue sniff is a Bluetooth wardriving tool that works on Windows. Question 15 options: False True Question 16 (5 points) Question 16 Unsaved Blue Tooth attacks include (Choose all that apply): Question 16 options: Bluesmacking Blue Cracking Blue Bugging Blue Snarfing Wired Equivalent Privacy (WEP) keys can be (Choose all that apply): Question 17 options: 512 bits 40 bits 104 bits 256 bits Which version of Wired Equivalent Privacy (WEP) uses a 104-bit key size? Question 18 options: 152 bit WEP 128 bit WEP 256 bit WEP 64 bit WEP An SSID is NOT (Choose one )? Question 19 options: part of the frame header Case Sensitive encrypted in WEP or WPA/WPA2 is utilized up to 32 characters Which of the following is true about the 802.11i standard? Question 20 options: It operates at both 2.4 GHZ and 5 GHZ It defines WPA-2 Enterprise and Personal It operates at 5 GHZ only It operates at 2.4 GHZ only Question 1 (5 points) Question 1 Unsaved Which of the following is a Cloud Consumer model that includes storage, service management, and content delivery? Question 1 options: IaaS PaaS SaaS SAN Question 2 (5 points) Question 2 Unsaved An Intrusion Detection System (IDS) (choose all that apply) Question 2 options: Signals an alarm Monitors inbound traffic Monitors outbound traffic Will perform actions to stop the attacker in their tracks Question 3 (5 points) Question 3 Unsaved This Cloud Deployment model is a multi-tenant infrastructure shared among organizations with common characteristics: Question 3 options: Private Cloud Public Cloud Community Cloud Hybrid Cloud Question 4 (5 points) Question 4 Unsaved Which of the following are signs of network intrusions? (choose all that apply) Question 4 options: Sudden Influx of Data Missing Files File Size Modifications Repeated Service Probes Question 5 (5 points) Question 5 Unsaved According to your text, which of the following are Cloud Deployment Models? (choose all that apply) Question 5 options: Private Cloud Public Cloud Hybrid Cloud Community Cloud Question 6 (5 points) Question 6 Unsaved According to your text, ways to detect an Intrusion with an (IDS) include (choose all that apply): Question 6 options: Protocol Anomaly Detection Signature Detection Anti-Virus Alerts Anomaly Detection Question 7 (5 points) Question 7 Unsaved According to the text, the three different types of Virtualization include which of the following? Question 7 options: Network Virtualization Server Virtualization Storage Virtualization SAN Virtualization Question 8 (5 points) Question 8 Unsaved Some of the Characteristics of Cloud Computing services include (select all that apply) Question 8 options: Measured Services Distributed Storage Resource Pooling Virtualization Technology Question 9 (5 points) Question 9 Unsaved Some of the Limitations of Cloud Computing services include (select all that apply): Question 9 options: Contracts Control Limits Storage Limits Inflexible Question 10 (5 points) Question 10 Unsaved The Major 5 actors of the NIST Cloud Computing Reference Architecture include which of the following? (choose two) Question 10 options: Cloud Database Cloud Broker Cloud Auditor CloudShareOne Question 11 (5 points) Question 11 Unsaved Which of the following are signs of file system intrusion? (choose all that apply) Question 11 options: Double Extensions Connection Requests Reduced Bandwidth Rogue SUID Entries Question 12 (5 points) Question 12 Unsaved Select the three IP Protocols that Snort Supports for Suspicions behavior according to your text. Question 12 options: ICMP ARP TCP UDP Question 13 (5 points) Question 13 Unsaved What are the advantages of Software as a Service (SaaS)? (choose all that apply) Question 13 options: Easy Administration Security Low Cost Internet Dependency Question 14 (5 points) Question 14 Unsaved Examples of companies that offer Cloud Computing services include (select all that apply): Question 14 options: Facebook Dropbox Google Salesforce Question 15 (5 points) Question 15 Unsaved In this Cloud Deployment model, the provider makes services such as applications, servers, and data storage available. Question 15 options: Private Cloud Hybrid Cloud Community Cloud Public Cloud Question 16 (5 points) Question 16 Unsaved According to your text, these are the 3 types of cloud services. Question 16 options: Software as a Service Platform as a Service Virtualization as a Service Infrastructure as a Service Question 17 (5 points) Question 17 Unsaved Some of the main functions of an Intrusion Detection System (IDS) include (choose all that apply): Question 17 options: Blocks rule-based traffic Performs packet sniffing Performs packet analysis Gathers and analyses information from a network Question 18 (5 points) Question 18 Unsaved Which of the following is a Cloud Consumer model that includes database, business intelligence, and application deployment? Question 18 options: IaaS SAN PaaS SaaS Question 19 (5 points) Question 19 Unsaved You should place your Intrusion Detection System (IDS) in this location on the network (choose all that apply): Question 19 options: At the ISP Location DMZ Inside the Firewall Outside the Firewall Question 20 (5 points) Question 20 Unsaved Services models available to Cloud Consumers include which of the following models? (choose all that apply) Question 20 options: PaaS SaaS SAN IaaS Question 1 (5 points) Question 1 Unsaved According to OWASP, these two should be applied to transport channels. Question 1 options: WPA TLS SSL WPA2 with AES Question 2 (5 points) Question 2 Unsaved SPAM can include which of the following? (choose all that apply) Question 2 options: TLS SMS IM MMS Question 3 (5 points) Question 3 Unsaved Mobile Network Based Attacks include (choose all that apply): Question 3 options: Man-in-the-Middle Attacks Packet Sniffing Rogue Access Points SSL Strip Question 4 (5 points) Question 4 Unsaved According to OWASP, strong encryption channels, such as which of the following, should be used. (choose all that apply) Question 4 options: DES RC4 AES 3DES Question 5 (5 points) Question 5 Unsaved Which of the following can a hacker can use this to gain control of a device? Question 5 options: Blue Snarfing Blue Bugging SMS Intercept IM Takeover Question 6 (5 points) Question 6 Unsaved Fake Defender deleted apk files from which of the following locations? (choose all that apply) Question 6 options: /mnt/external_sd/Download /home/Download /users/Download /mnt/extSdCard/Download Question 7 (5 points) Question 7 Unsaved Which of the following are app stores? (choose all that apply) Question 7 options: Fanddago ITunes Store Google Play BlackBerry App World Question 8 (5 points) Question 8 Unsaved According to the text, which of the following is a form of MITM Attack? Question 8 options: Checksum Evasion API Hooking Packet Sniffing SSL Strip Question 9 (5 points) Question 9 Unsaved A lack of vetting of apps can lead to which of the following? (choose all that apply) Question 9 options: fake apps jail-breaking Malicious apps Rooting Question 10 (5 points) Question 10 Unsaved Mobile Devices are replacing which of the following? (choose all that apply) Question 10 options: PDA desktop GPS Labtop Android includes media support for which the following? (choose all that apply) Question 11 options: H.323 AAC ARM H.264 Question 12 (5 points) Question 12 Unsaved Which of the following are Sophos mobile security features (choose all that apply)? Question 12 options: Loss and Theft Protection Privacy Protection and security antivirus anti-malware Spam Protection Which of the following is the 3D Graphics Library of Android? Question 13 options: Media Framework OpenGL SSL SGL Question 14 (5 points) Question 14 Unsaved Rooting enables which of the following? (choose all that apply) Question 14 options: deleting system files Low level access to hardware removing bloatware tethering Question 15 (5 points) Question 15 Unsaved Database Attacks include which of the following? (choose all that apply) Question 15 options: SQL Injection Data Dumping HOS Command Execution Privilege Escalation Question 16 (5 points) Question 16 Unsaved Rooting risks include which of the following? (choose all that apply) Question 16 options: malware bricking voiding the warranty poor performance Question 17 (5 points) Question 17 Unsaved Among all smartphones, which is most likely to be hacked? Question 17 options: iPhone Android Blackberry Windows Phone Question 18 (5 points) Question 18 Unsaved Which of the following are methods to connect smartphones to a network? (choose all that apply) Question 18 options: Bluetooth Wired Connection Wi-Fi 3G/4G Question 19 (5 points) Question 19 Unsaved Bluetooth devices in these modes are at greater risk (choose all that apply): Question 19 options: monitor discovery open promiscuous Question 20 (5 points) Question 20 Unsaved Which of the following are Android options to save persistent data? (choose all that apply) Question 20 options: Network Connection External Storage Internal Storage SQLite Databases [Show More]
Last updated: 2 years ago
Preview 1 out of 42 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$8.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Mar 08, 2021
Number of pages
42
Written in
Additional information
This document has been written for:
Uploaded
Mar 08, 2021
Downloads
0
Views
59