CRY 303c Final Exam | Questions with complete solutions Which of the following violate Kerckhoff's principle? Select all that are applicable. A. A company states that its system is "secure" because it uses confidential
...
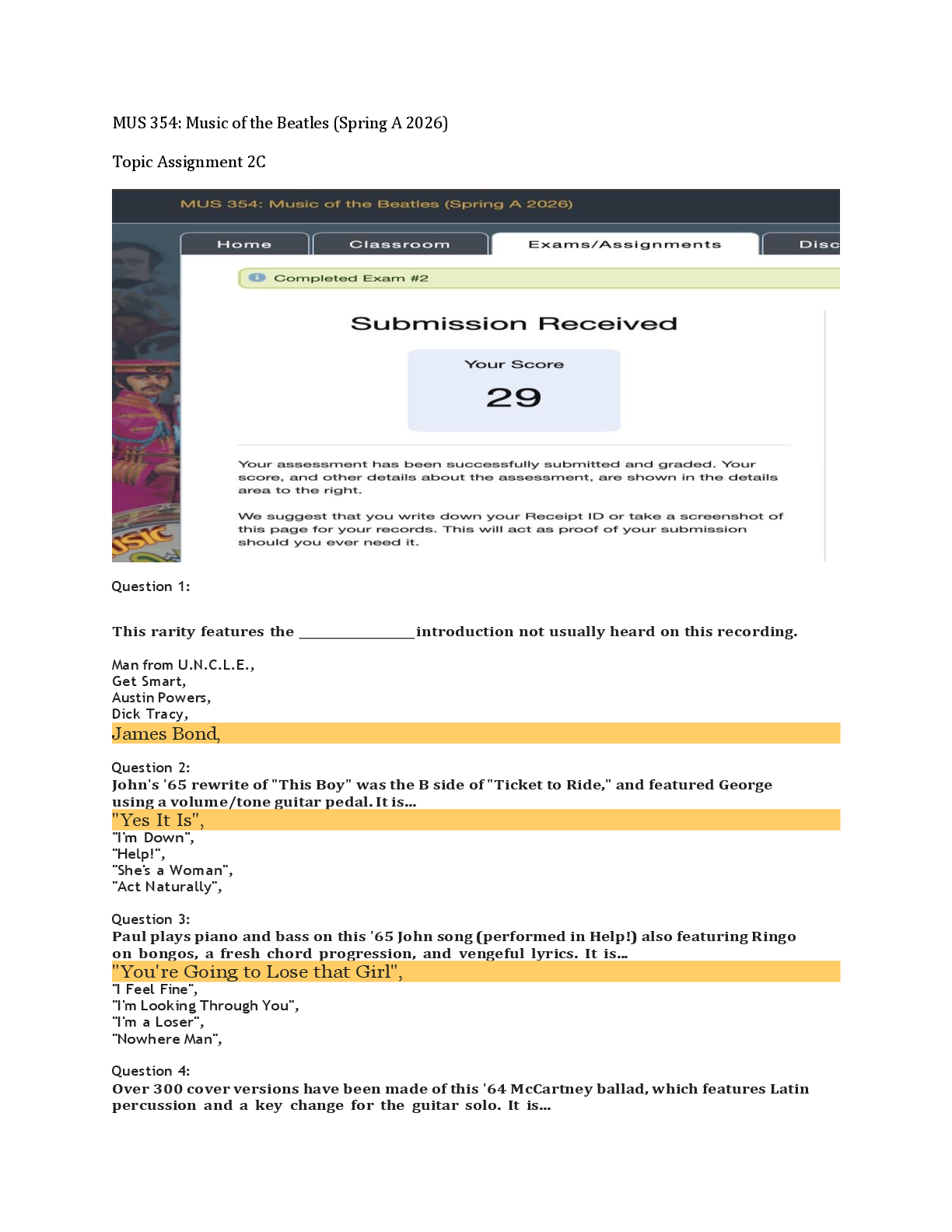
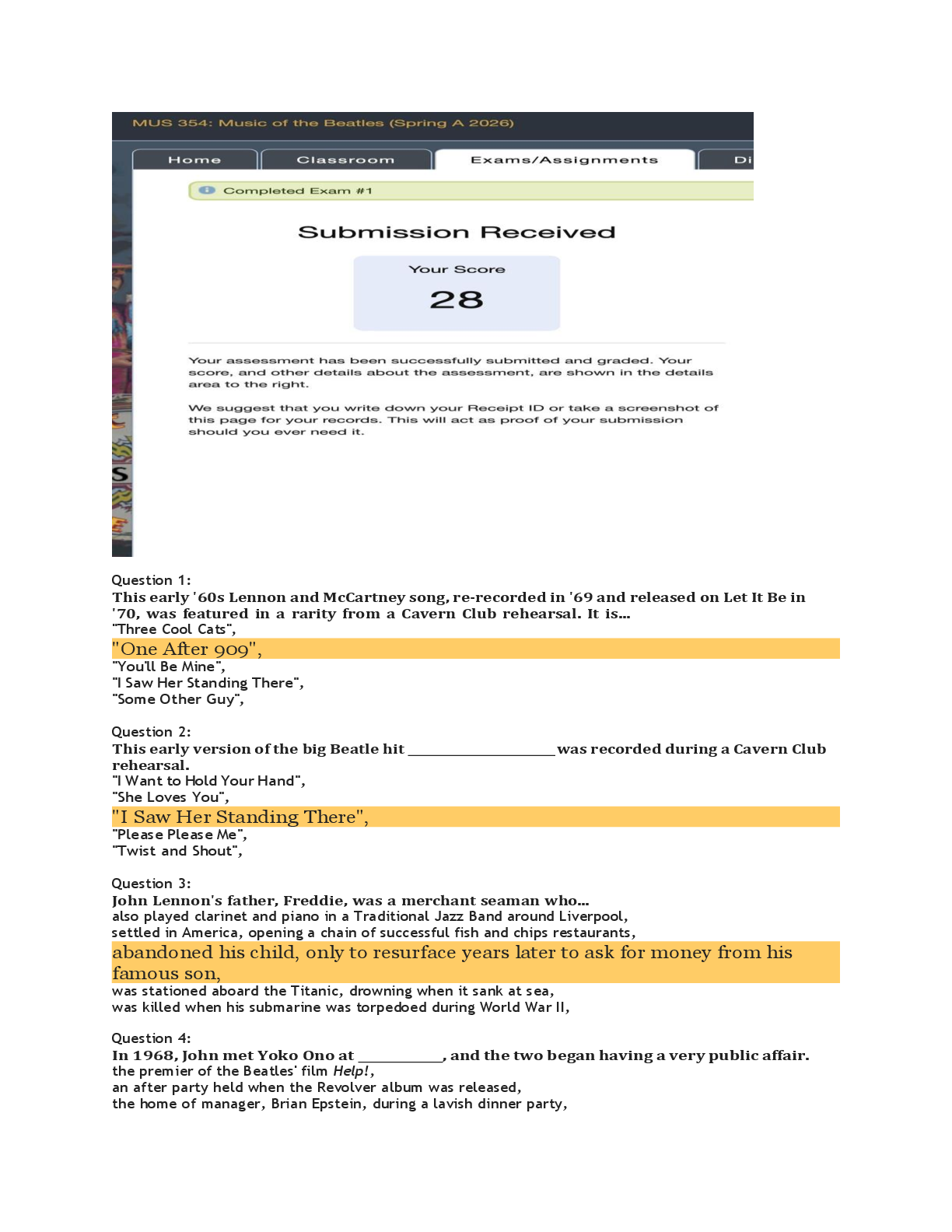
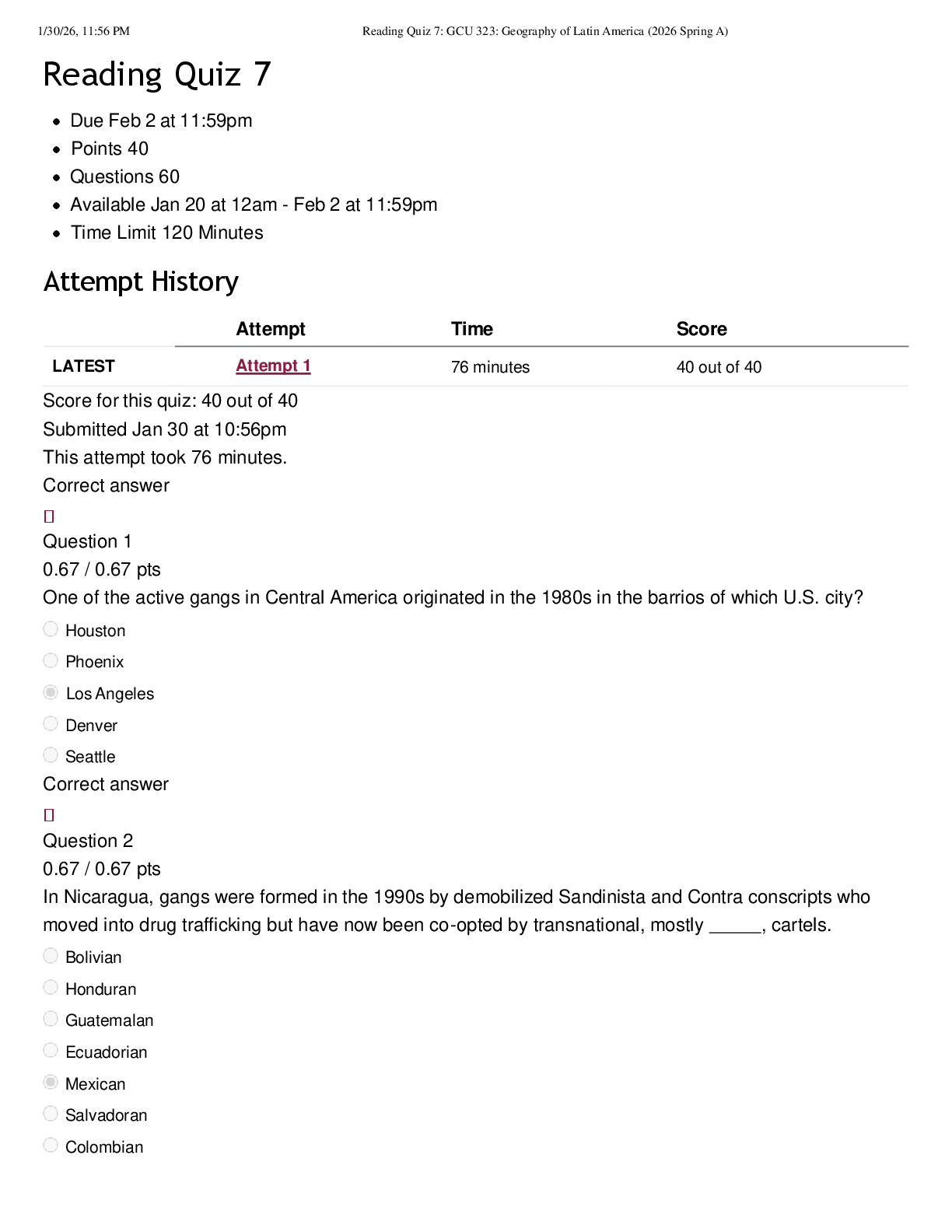
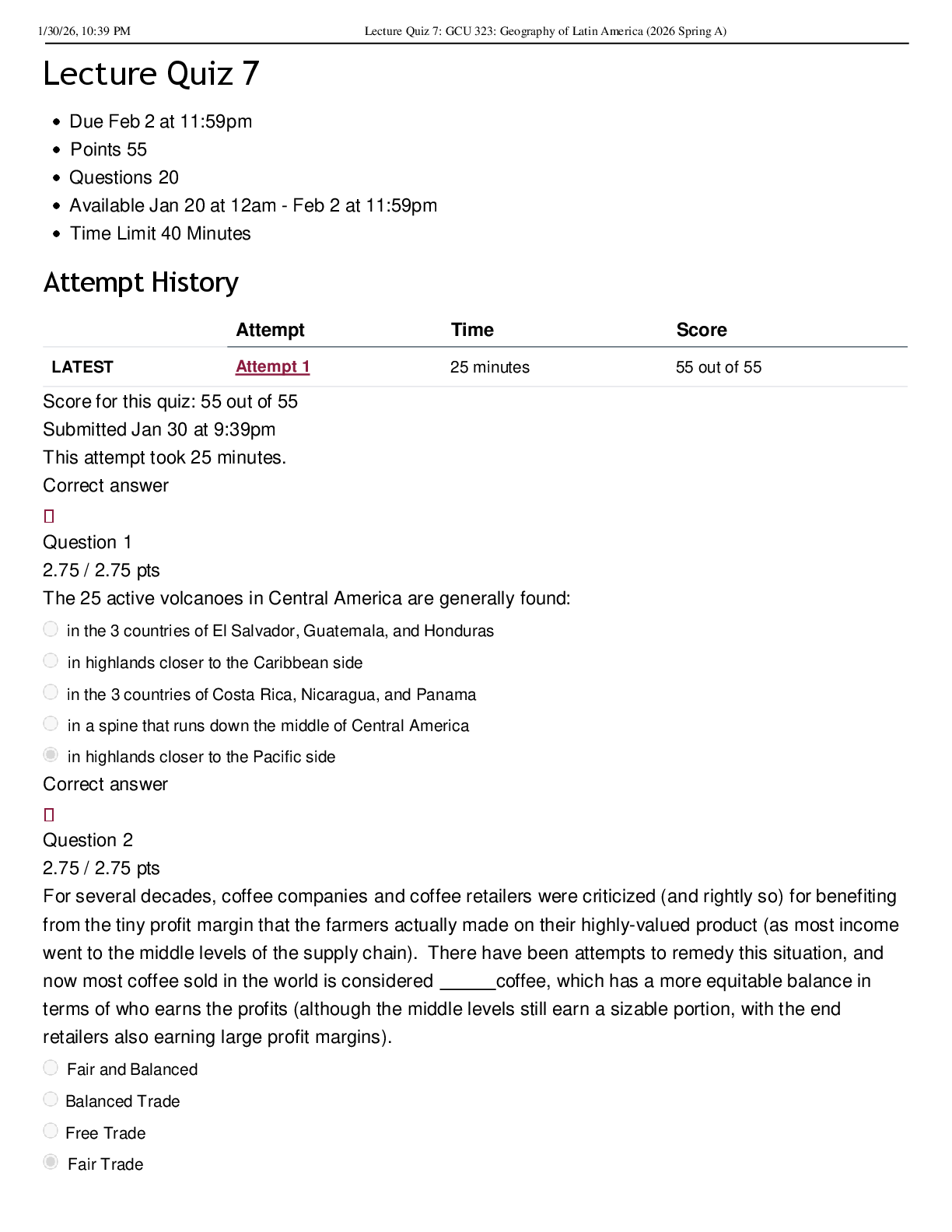
CRY 303c Final Exam | Questions with complete solutions Which of the following violate Kerckhoff's principle? Select all that are applicable. A. A company states that its system is "secure" because it uses confidential and proprietary protocols. B. The company password is written using an invisible ink, and only the people within the company know the fact that invisible ink is used. C. The algorithms for popular symmetric ciphers such as DES and AES are publicly known. D. The attacker has the copy of the system. Using the cryptography jargon, when Alice wants to communicate to Bob, who holds the key among Alice, Bob, and Eve? Select all that are applicable. A. Eve B. Alice C. Bob Which of the following is the least similar to Kerckhoff's Principle? A. Open design B. "Attacker knows the system" C. Security by Obscurity D. Shannon Maxim Solve the following steganographic message. The grading is space- and case-sensitive so, in your answer, use all lower case letters and skip all punctuation marks, i.e., your answer should only be comprised only of spaces, numbers, and lower-case letters. your package ready Friday 21st room three please destroy this immediately Which of the followings are examples of steganography? A. Broadcasting your password to another person and hoping that the person forgot of your password by now B. Blinking based on Morse code while saying something else C. Touching different parts of your faces (where different parts indicate different messages) while being engaged in another activity D. Using passwords for authentication E. Invisible ink F. Embedding another message on the least significant bits on images (so that they are indistinguishable in human eyes) There is a typical dice (with each side showing distinct numbers between 1 and 6). In each event, you throw the dice and observe the number. What is the information entropy for one event in bits? 2.585 ( log26 ) There is a typical dice (with each side showing distinct numbers between 1 and 6). In each event, you throw the dice and observe the number. What is the information entropy for five event in bits? 12.925 ( 5 x log26 ) Now suppose you modify the dice so that the side which originally showed the number 6 becomes a 5 (i.e., the numbers 1, 2, 3, 4 occupy one side each, and 5 occupies two sides). What is the information entropy for one event? 2.251 (1/6) x log2(6) x 4 + (1/3) x log2(3) There are five red balls, three yellow balls, and four green balls in a bin. In each event, you pick one ball from the bin and observe the color of the ball. The balls are only distinguishable by their colors. After observation, you put the ball back into the bin. What is the probability of choosing a red ball in an event? 0.416 ( 5/12 ) As was in the previous question (the same setup with the previous question), there are five red balls, three yellow balls, and four green balls in a bin. In each event, you pick one ball from the bin and observe the color of the ball. The balls are only distinguishable with their colors. After observation, you put the ball back into the bin. What is the information entropy for one event (pick ball once) in bits? 1.555 (5/12) x log2(12/5) + (3/12) x log2(12/3) + (4/12) x log2(12/4) As was in the previous question (the same setup with the previous question), there are five red balls, three yellow balls, and four green balls in a bin. In each event, you pick one ball from the bin and observe the color of the ball. The balls are only distinguishable with their colors. After observation, you put the ball back into the bin. What is the information entropy for five events in bits? 7.773 ( 1.555 x 5 ) As was in the previous question (the same setup with the previous question), there are five red balls, three yellow balls, and four green balls in a bin. In each event, you pick one ball from the bin and observe the color of the ball. The balls are only distinguishable with their colors. After observation, you put the ball back into the bin. You can re-color or re-paint one ball of your choice to any of the three colors (red, yellow, green). Which ball would you re-color and to which color in order to maximize the entropy? A. Re-color a red ball to green B. Re-color a yellow ball to red C. Re-color a green ball to yellow D. Re-color a yellow ball to green E. Re-color a green ball to red F. Re-color a red ball to yellow Now, the bin contains 12 green balls. In each event, you pick one ball from the bin and observe the color of the ball. The balls are only distinguishable with their colors. After observation, you put the ball back into the bin. What is the entropy value for five events in bits? 0 ( vì tất cả ball đều là màu xanh ) True or False: Brute-force attack assumes that the attacker can distinguish between the correct and the incorrect key after the decryption trial. For example, the incorrect key can yield gibberish while the correct key yields a meaningful message. A. True B. False When the key is 10-bits long, how many decryptions do the brute-force attacker try in the worst case (this is the worst case in the Alice-Bob perspective and corresponds to the case when the attacker gets lucky)? a. 1 b. 512 c. 1024 d. 2048 When the key is 64-bits long, how long does it take in days for an attacker to brute-force search/attack for the key on average? The attacker can perform 10 trillion (10^13) decryptions per second, given the attacker processor and the encryption/decryption algorithm. a. 42.701 b. 4.971 c. 21.350 d. 10.675 (2^64-1) / (10^13) / 60 / 60 / 24 True or False: Known-plaintext attack is a stronger threat than ciphertext-only attack because the attacker uses the known plaintext-ciphertext pairs to more efficiently find the key that is being used by Alice and Bob. A. True B. False Is the following claim (that your friend generated a true one-time pad for perfect secrecy) true or false? A friend wants to use a one-time pad to encrypt a data of size 1 kilobyte/KB and ensure perfect secrecy. He generates a key that is of size 1KB by taking an 1B-long seed and using a deterministic algorithm to produce a 1KB-long key. The friend uses a secret algorithm, which he does not tell anybody, and the output key passes the pseudo-random test published by US NIST. A. True B. False True or False: One-time pad is popularly used for systems that require secure data protection. A. True B. False You agreed to use a Caesar cipher with a key of k=5 with a friend. While sitting in a group, the friend hands you over a message that says "QNGWFWD". a. WEEKEND b. BELIEVE c. LIBRARY d. COUNTRY Suppose you actually forgot the key. How many decryption computations of the cipher text "QNGWFWD" do you need to perform to reach to the plaintext? (Consider the worst case.) a. 1 b. 13 c. 26 d. 52 Your friend proposes an update in the key and suggests a new key, k=523. How many cyclic shifts do you need to perform using the new key? You want to minimize the number of cyclic shifts on the letters. a. 3 b. 5 c. 7 d. 9 Let's use a modified Caesar Cipher where c = (p+2x) mod 26, where c and p are the ciphertext and the plaintext, respectively, and x is the key. How many distinct keys, producing distinct encryption/decryption transformations, are there now? 13 For c = (p+2x) mod 26, where c, p, and x are the ciphertext, the plaintext, and the key, respectively, what is the corresponding decryption? Select all that works. A. p = (c-2x) mod 26 B. p = (c-x) mod 26 C. p = (c-x) mod 13 D. p = (c-2x) mod 13 E. p = (c+26-2x) mod 26 Let's now use a modified Caesar Cipher where c = (p+3x) mod 26, where c and p are the ciphertext and the plaintext, respectively, and x is the key. How many distinct keys, producing distinct encryption/ decryption transformations, are there now? 26 Let's use Vigenere Cipher to encrypt English text, ignoring capitalization and other symbols beyond English alphabets. The key is of length 1 and of value "Y" or 24, i.e., the key is "Y". Which of the following statements is false? A. This cipher transforms a plaintext alphabet to distinct ciphertext alphabets with long enough plaintext inputs. B. The cipher is equivalent to a Caesar Cipher. C. The cipher can be expressed as c = (p+24) mod 26, where c is each ciphertext letter and p is each plaintext letter. D. The cipher is equivalent to the Vigenere cipher using a key of length 3 and of value "YYY". E. The cipher can be expressed as c = (p-2) mod 26, where c is each ciphertext letter and p is each plaintext letter. Vigenere cipher is used with a key "XO". What is the ciphertext corresponding to the plaintext, DRAGON? a. AFXULB b. ROODCK c. RFOUCB d. AOXDLK Vigenere cipher is used with a key "XO" to encrypt a long English book, comprised of English alphabet letters and ignoring capitalization and other symbols. The key length is fixed, i.e., the key is 2 alphabets long. What is the number of possible distinct keys? a. 26 b. 52 c. 676 d. 1352 (1 bảng có 26 chữ cái "2 alphabets long" = 26 x 26 ) Vigenere cipher is used with a key "XO" to encrypt a long English book. You order the letters appearing in the encrypted book in the decreasing order of frequency (i.e., from the most frequently appearing to the least frequently appearing), and the result is: RGZNFIBJWPESCXHTMYAUOLDKVQ. Which ciphertext letters correspond to the plaintext letter E (which is the most frequent letter in the plaintext)? Apply all those that apply. A. A B. R C. Z D. G E. E F. Y G. T The Rail Fence cipher uses 4 rows/rails (the example in the lecture used 3). What is the ciphertext (the outcome of the rail fence cipher) for MEETMELATER? MLEEAEMTRTE A Permutation Cipher has a key length of 5, e.g., one key can be [3 2 1 4 5]. How many possible keys are there? 120 ( 5! ) The plaintext MEETMELATER gets processed by a Permutation Cipher (with a key of [2 3 5 4 1] and no padding with extra letters. What is the corresponding ciphertext? MEMERELTTEA The plaintext MEETMELATER gets processed by a Permutation Cipher (with a key of [2 3 5 4 1] and with padding using the letter "z" (Alice and Bob agree to use the letter z for padding). What is the corresponding ciphertext? MEZMERELZTTZEAZ The plaintext MEETMELATER gets processed by a product cipher, comprised of Caesar Cipher (with a key of 23) and Permutation Cipher (with a key of [5 3 1 4 2] and no padding with extra letters). What is the corresponding ciphertext? BXJBBIQQJBO The same product cipher in the previous question, comprised of Caesar Cipher and Permutation Cipher (with a key of length 5), is again used but with different keys. Given a plaintext, how many distinct ciphertexts can there be? 3120 ( 5! x 26 ) The same product cipher in the previous question, comprised of Caesar Cipher and Permutation Cipher (with a key of length 5), is used to encrypt a long English book (ignoring capitalization and other symbols beyond English letters). Your friend makes the following claims. Select all those that are correct. A. "If we replace the Caesar Cipher with a Monoalphabetic Cipher, then it becomes harder to crack by an attacker (who does not know the key)." B. "The ordering between the Caesar and the Permutation does not matter within the product cipher, so we can decrypt it in any order." C. "If we another Caesar Cipher encryption in the product cipher (so that there are two Caesar Cipher operations and a Permutation Cipher operation), then it becomes harder to crack by an attacker (who does not know the key). D. "The letter-pair/digram AX appeared the most in the ciphertext, so they must be TH. In other words, A is mapped from the letter T, and X is mapped from H." E. "Letter Z appeared the most in the ciphertext, so it must be mapped from the latter E. You are given a stream cipher and a block cipher with a block size of 64 bits. The data input is 32 bits. How many bits do you need to pad before processing the data input using a stream cipher? a. 0 b. 16 c. 32 d. 64 The block cipher supports input/output of 64 bits. Which of the following is true about the key storage requirement? A. You need hundred million to one billion 1TB-hard-drives to store the key, where TB stands for Terabytes. B. You need more than one billion 1TB-hard-drives to store the key, where TB stands for Terabytes. C. You need ten to hundred million 1TB-hard-drives to store the key, where TB stands for Terabytes. D. You need less than ten million 1TB-hard-drives to store the key, where TB stands for Terabytes. A block cipher takes a 3-bit plaintext and outputs a 3-bit ciphertext. If the cipher is an ideal block cipher, how many reversible transformations (keys) can it have? a. 6 b. 24 c. 720 d. 40320 True or False: DES is an ideal block cipher. A. True B. False True or False: DES displaying Avalanche Effect is a limitation because it describes that an error occurring in one of the rounds propagate through the rest of the rounds. A. True B. False An attacker is equipped with a computer that performs 10 trillion (10^13) DES decryptions per second, what is the average time required, in hours, for a brute force attacker to break DES? 1 ( 2^56-1 / 10^13 / 60 / 60 ) Which of the followings are true about Feistel Cipher? Select all that applies. A. Feistel Cipher competed with DES and got outdated after the wide use of DES. B. Feistel Cipher requires smaller key than ideal block cipher. C. Feistel Cipher processes the data in halves. D. Feistel Cipher is a product cipher. E. Feistel Cipher requires different encryption and decryption implementations in hardware and software. F. The subkeys used in the Feistel Cipher rounds are independent to each other. Triple-DES or 3-DES encryption can be characterized by the following: C=Enc(K3,Dec(K2,Enc(K1,P))). Each keys, K1, K2, K3 are 56-bits-long and are independent to each other (the three-key version). The DES block size is 64 bits. Using the big O notation, which of the following best describe the meet-in-the-middle attacker's storage requirement? A. O(168) B. O(2^112) C. O(2^56) D. O(2^168) Triple-DES or 3-DES encryption can be characterized by the following: C=Enc(K3,Dec(K2,Enc(K1,P))). Each keys, K1, K2, K3 are 56-bits-long and are independent to each other (the three-key version). The DES block size is 64 bits. Using the big O notation, which of the following best describe the meet-in-the-middle attacker's encryption/ decryption computational effort? A. O(2^56) B. O(2^128) C. O(2^168) D. O(2^112) E. O(2^28) Triple-DES or 3-DES encryption can be characterized by the following: C=Enc(K3,Dec(K2,Enc(K1,P))). Each keys, K1, K2, K3 are 56-bits-long and are independent to each other (the three-key version). The DES block size is 64 bits. The attacker now does not have known plaintext-ciphertext pair that it can use for her cryptanalysis. Using the big O notation, which of the following best describe the attacker's encryption/ decryption computational effort? A. O(2^56) B. O(2^168) C. O(2^112) D. O(2^128) Quadruple-DES or 4-DES encryption can be characterized by the following: C=Enc(K4,Enc(K3,Enc(K2,Enc(K1,P)))). Each keys, K1, K2, K3, K4, are 56-bits-long and are independent to each other. The DES block size is 64 bits. Using the big O notation, which of the following best describe the meet-in-the-middle attacker's storage requirement? A. O(64*2^56) B. O(2^112) C. O(2^56) D. O(2^224) E. O(2^128) Quadruple-DES or 4-DES encryption can be characterized by the following: C=Enc(K4,Enc(K3,Enc(K2,Enc(K1,P)))). Each keys, K1, K2, K3, K4, are 56-bits-long and are independent to each other. The DES block size is 64 bits. Using the big O notation, which of the following best describe the meet-in-the-middle attacker's encryption/decryption computational effort? A. O(2^58) B. O(2^224) C. O(2^56) D. O(2^112) E. O(2^128) Quadruple-DES or 4-DES encryption can be characterized by the following: C=Enc(K4,Enc(K3,Enc(K2,Enc(K1,P)))). Each keys, K1, K2, K3, K4, are 56-bits-long and are independent to each other. The DES block size is 64 bits. The attacker now does not have known plaintext-ciphertext pair that it can use for her cryptanalysis. Using the big O notation, which of the following best describe the attacker's encryption/decryption computational effort? A. O(2^56) B. O(2^112) C. O(2^128) D. O(2^58) E. O(2^224) What is the block size for AES in Bytes? 16
[Show More]