Computer Architecture > EXAM > FedVTE Cyber Security Overview for Managers Questions and Answers 100% Pass (All)
FedVTE Cyber Security Overview for Managers Questions and Answers 100% Pass
Document Content and Description Below
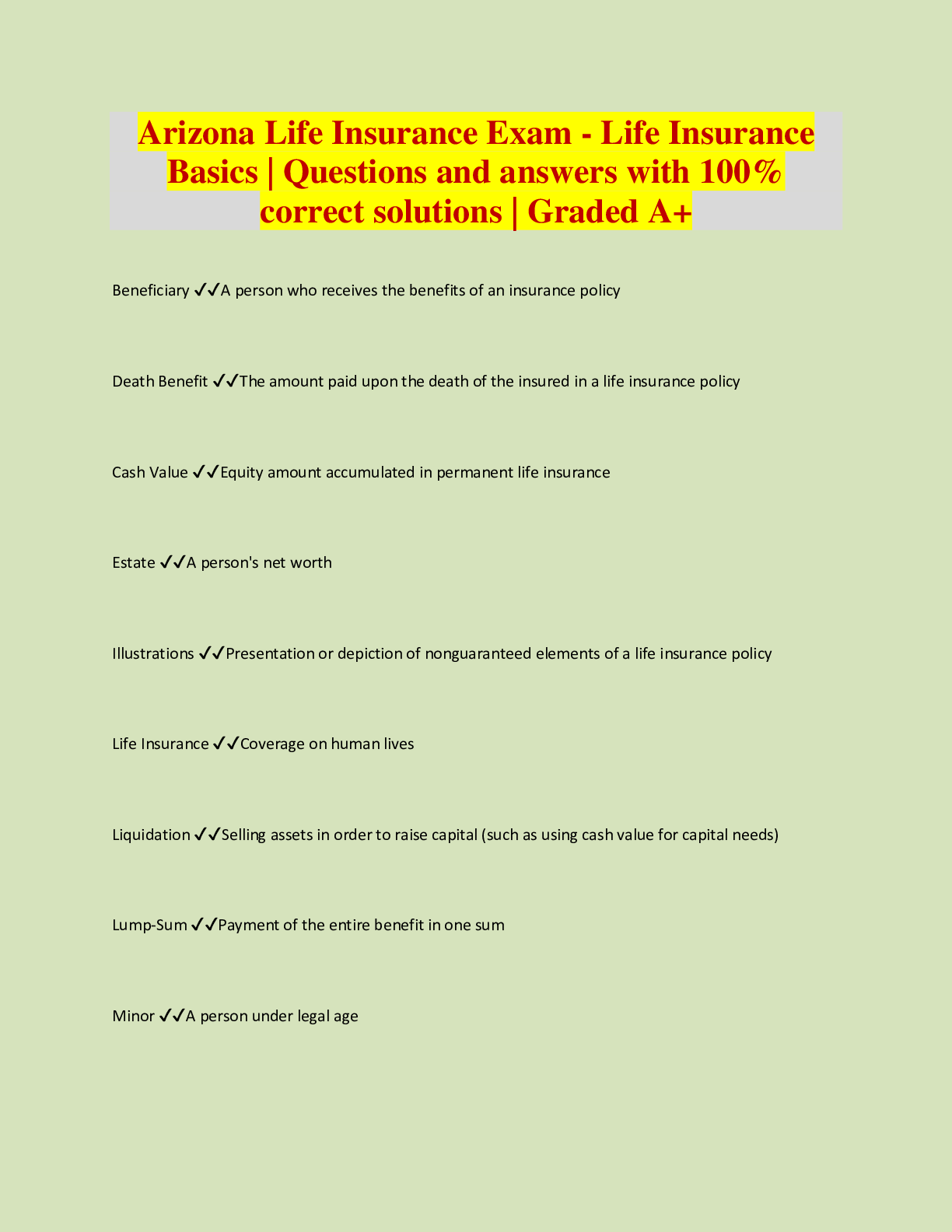
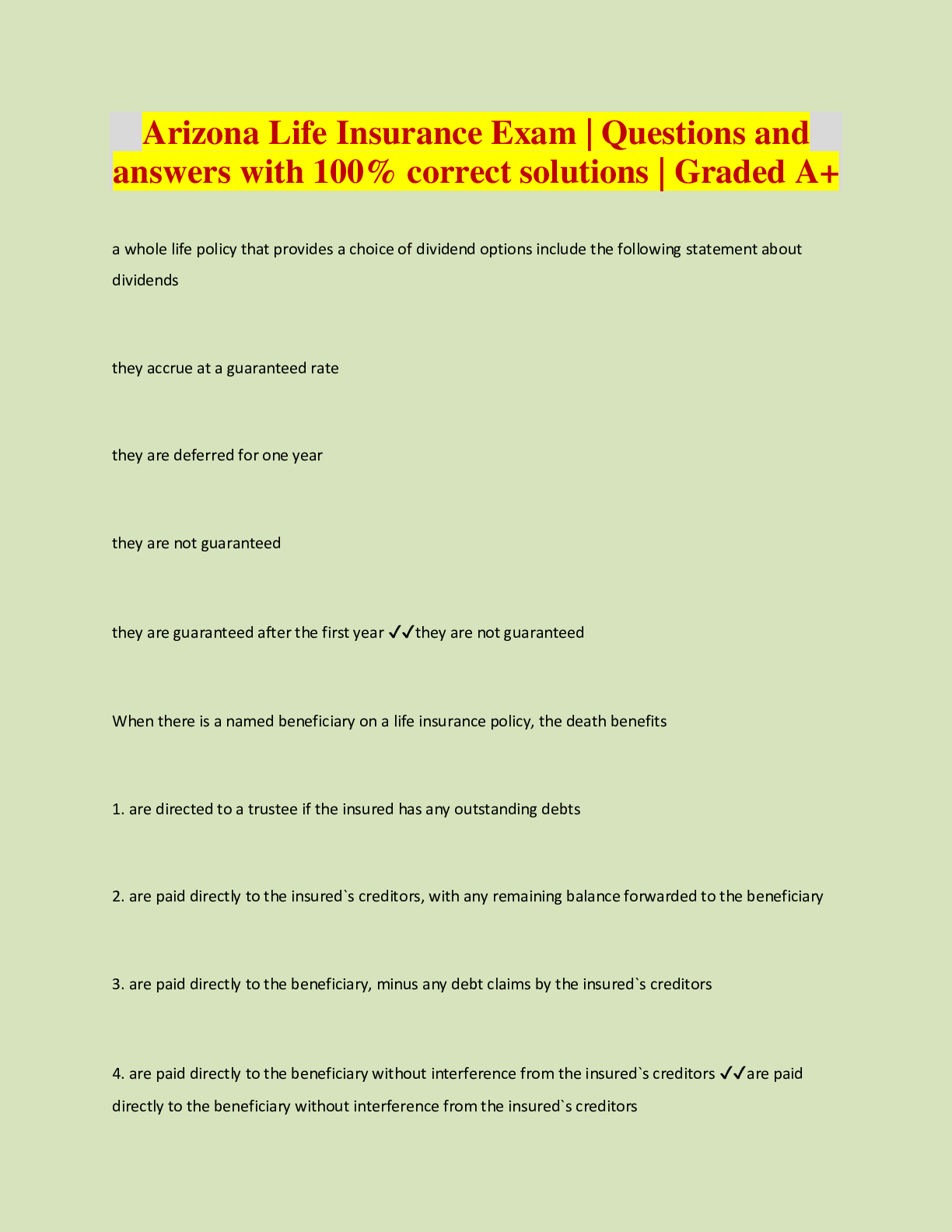
An insurance plan is what type of mitigation strategy? ✔✔Transfer Risk Which of the following is not a reason why a backdoor may exist? ✔✔Attempts to interfere with the ability of a provider... to keep services available What is the act of hiding messages in existing data called? ✔✔Steganography Which of the following addresses risk from a mission and business process perspective? ✔✔Tier 2 Which of the following provides procedures and guidance to sustain an organization's essential functions at an alternate site for up to 30 days? ✔✔Continuity of Operations Plan Which of the following is the correct order of the security life cycle? ✔✔Categorize Select Implement Assess Authorize Monitor Which of the following serves as an effective communications channel and provides an ongoing basis for ensuring the alignment of the security program with business objectives? ✔✔Steering committeeWhich of the following includes personnel and systems to perform health monitoring and management? ✔✔NOC Which of the following detects attacks but does not take action against the attack? ✔✔IDS Which of the following backup concepts includes everything since the last full backup and does NOT reset the archive attribute? ✔✔Differential When a compromised system is identified, it is a best practice to turn off the system immediately. ✔✔False Which one of the following is a type of malware that collects personal information about users without their knowledge? ✔✔Spyware Which major mobile device platform is open source software? ✔✔Google Android Which of the following characteristics applies to Information Technology Security? ✔✔Focuses on the security of information within the boundaries of the technological domain. The requirement that officers and others executives with fiduciary responsibilities meet certain requirements to protect the company's assets is known as Due Diligence. ✔✔False Which of the following sites is immediately available because systems and software and data are current copies? ✔✔Mirrored siteWhich of the following is not a mitigation strategy? ✔✔None of the above Which characteristic best describes the malware category "Downloaders"? ✔✔Targets web application vulnerabilities. Which of the following software licenses is free for use, retains copyrights, and usually includes an end-user license agreement? ✔✔Freeware Which of the following describes Aggregate Risk? ✔✔Exists when a particular threat affects a large number of minor vulnerabilities that combined have a significant impact. Attack scripts are used to install Trojans adware and other malware. ✔✔False RTO is the average length of time required to perform repairs on a device. ✔✔False Which of the following IS Governance Goals describes using information security knowledge and infrastructure efficiently and effectively to ensure captured knowledge is available? ✔✔Resource Management Which of the following is included in disaster recovery plans? ✔✔All of the above DoS attacks usually target chokepoints or single points of failure with [Show More]
Last updated: 1 year ago
Preview 2 out of 3 pages

Loading document previews ...
Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$3.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Aug 03, 2024
Number of pages
3
Written in
Additional information
This document has been written for:
Uploaded
Aug 03, 2024
Downloads
0
Views
19




















.png)


