Computer Science > EXAM > ITN 263 Final Pt 2 | Verified with 100% Correct Answers (All)
ITN 263 Final Pt 2 | Verified with 100% Correct Answers
Document Content and Description Below
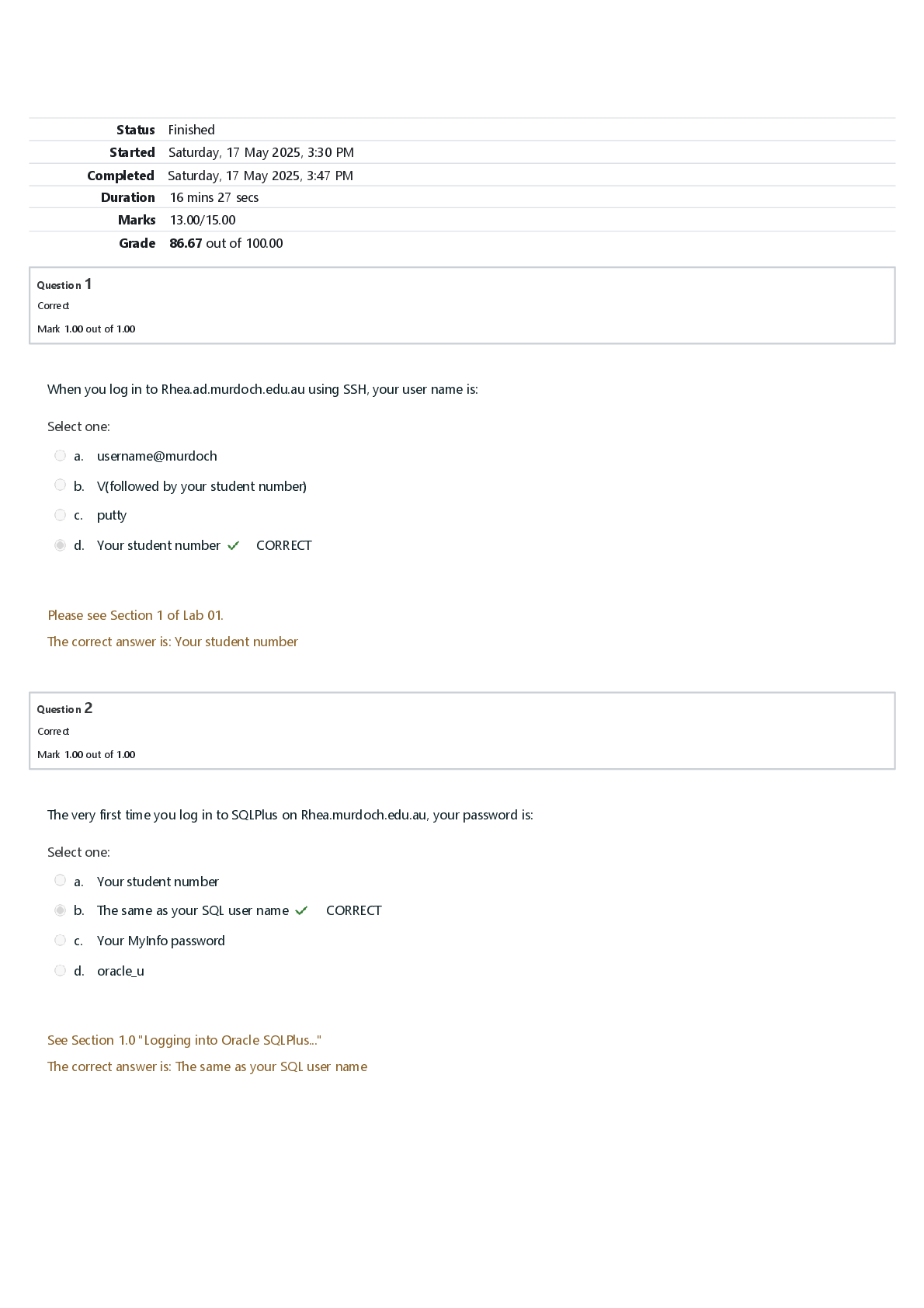
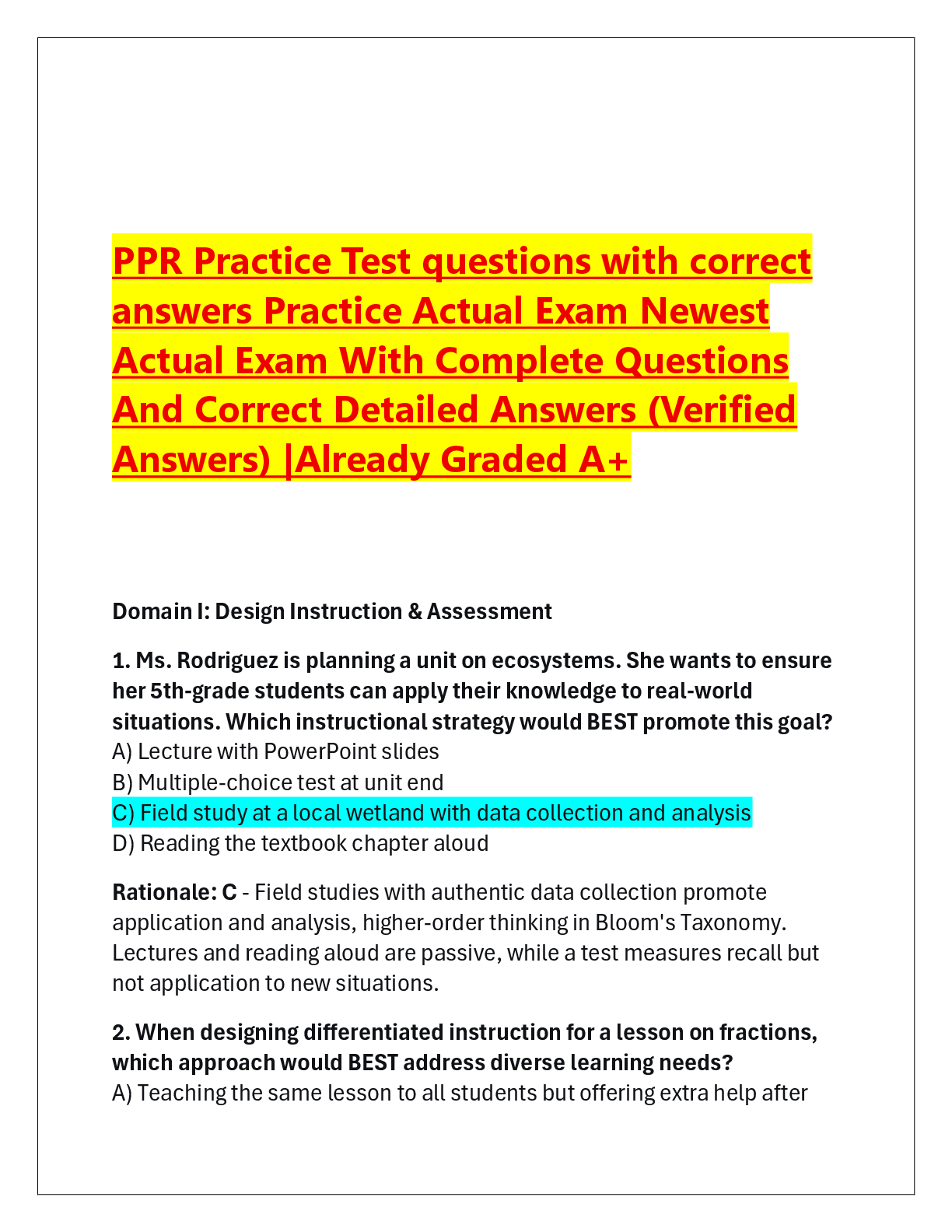
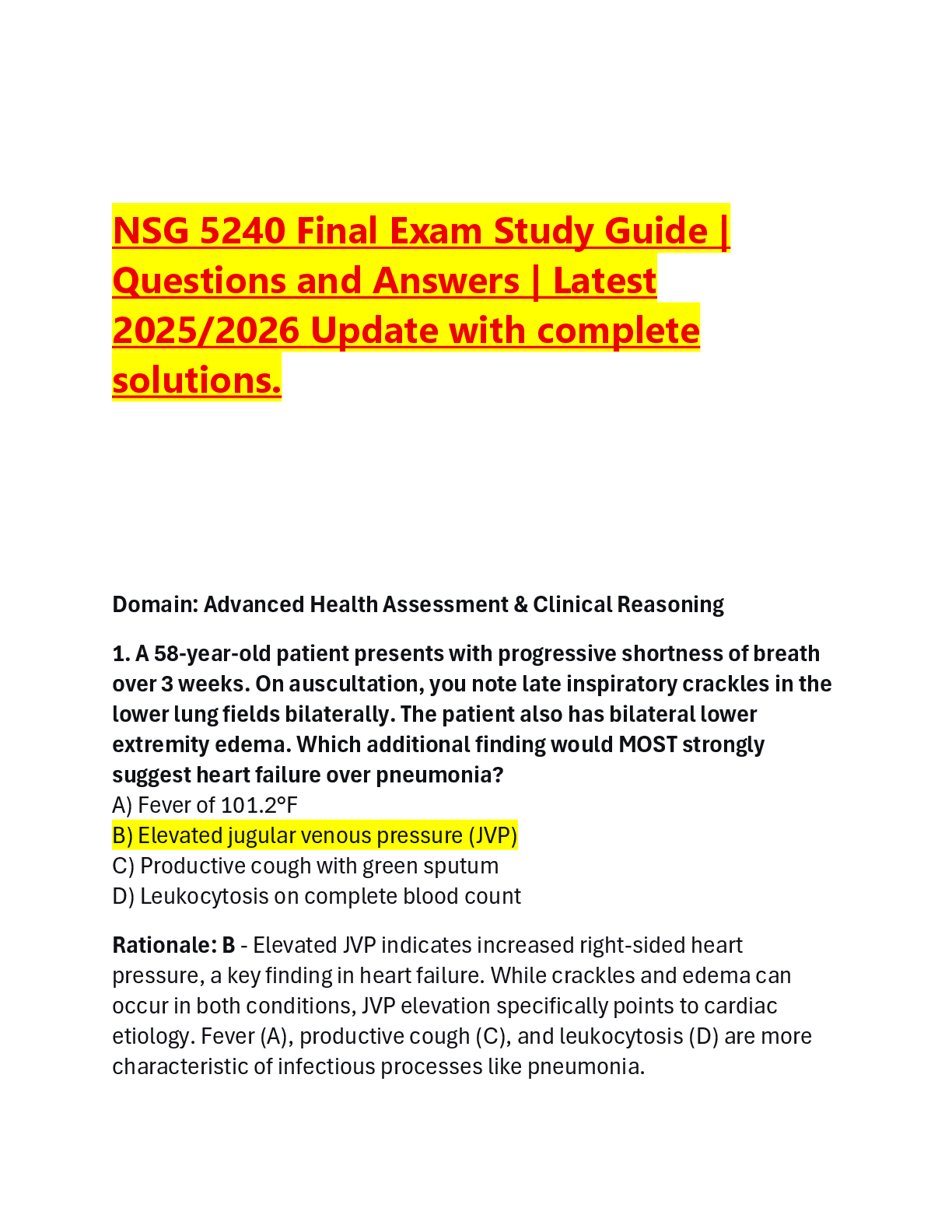
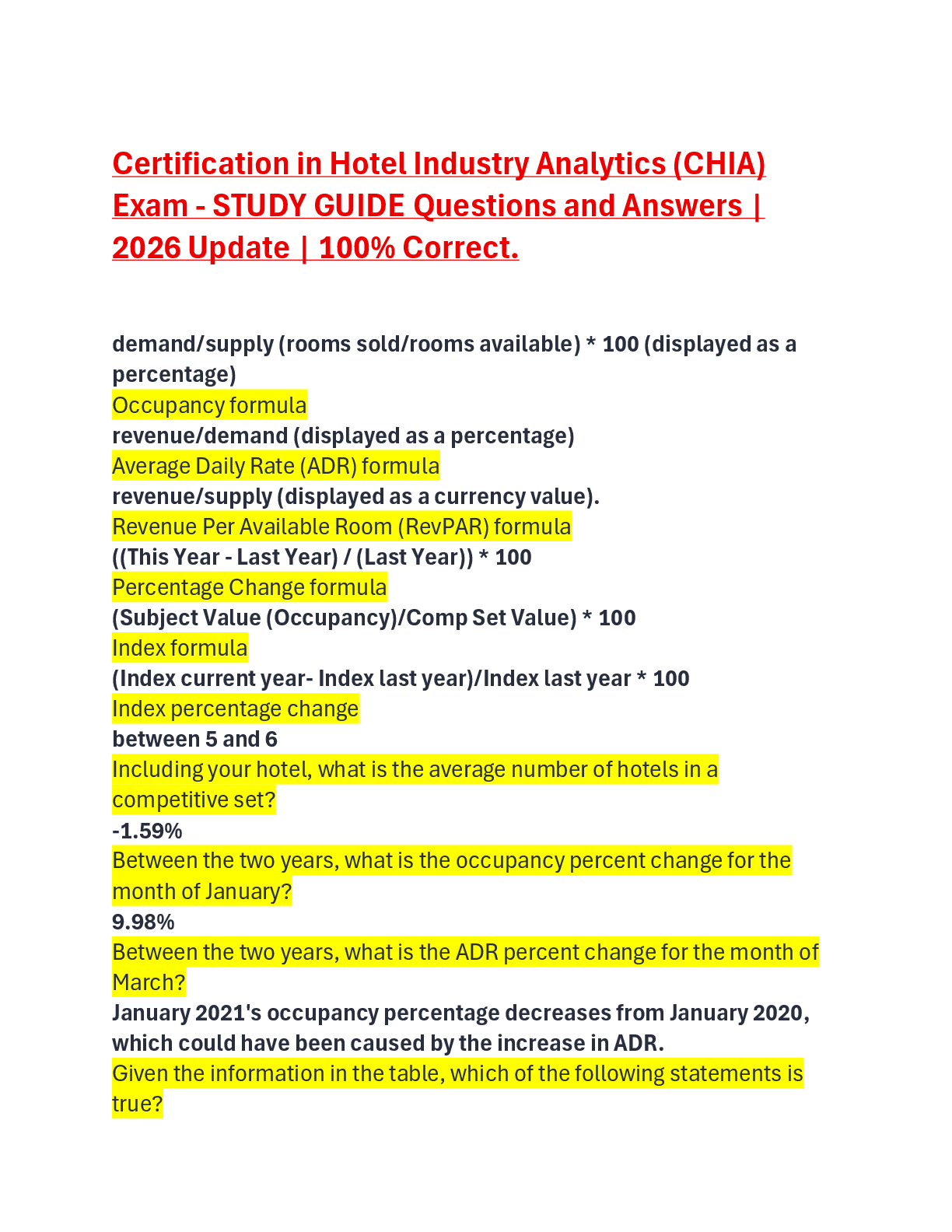
ITN 263 Final Pt 2 | Verified with 100% Correct Answers Which layer of the OSI model is the Data Link Layer? Layer 2 Chad is a network engineer. He is tasked with selecting a virtual private network ... (VPN) platform for his company. He chooses a solution that is inexpensive and runs on UNIX, although it is less scalable and less stable than other solutions. What has he chosen? Operating system-based VPN Your sales department likes to stream professional sports games across the computer network on Wednesday afternoons, causing VPN performance issues during that time. What is the most likely cause of the performance issues? Traffic spike Felicia is a network engineer deploying a virtual private network (VPN) solution. The VPN operates using Secure Shell (SSH). When asked by a new help desk tech about which layer of the OSI model it employs, how does Felicia answer? 7 Internet Protocol Security (IPSec) is a standards-based protocol suite designed specifically for securing ____________ communications. Internet Protocol (IP) Which of the following can perform authentication to provide integrity protection for the outermost IP header? Authentication Header (AH) Which of the following provides integrity protection for packet headers and data and can optionally provide replay protection and access protection? Authentication Header (AH) Maria is a new network engineer for a company that was established more than 30 years ago. She is examining the IT infrastructure and discovers that the virtual private network (VPN) solution employs an older encryption protocol for backward compatibility. This protocol has largely been replaced, but it used to be popular in early VPN solutions. What is this protocol? Layer 2 Tunneling Protocol (L2TP) Which of the following is a protocol that supports Advanced Encryption Standard (AES) with 128, 192, and 256 keys? Transport Layer Security (TLS) Chris is a network engineer deploying a virtual private network (VPN) solution. He needs an implementation of Secure Sockets Layer/Transport Layer Security (SSL/TLS) that adds a layer of authentication to the access. What feature does he require? Bidirectional authentication Which of the following statements is TRUE of an Internet Protocol Security (IPSec) virtual private network (VPN) when compared to a Secure Sockets Layer/ Transport Layer Security (SSL/TLS) VPN? It requires client software Which of the following is a protocol that replaces the use of telnet and rlogin to log in to a shell on a remote host? Secure Shell (SSH) Mei is a new network technician for a mid-sized company. She is trying to determine what is causing a performance lag on the infrastructure's virtual private network (VPN). The lags typically occur between 8 a.m. and 9 a.m., and again between 1 p.m. and 2 p.m. What is the most likely cause? Peak usage loads The configuration, location, software version, and underlying operating system of a virtual private network (VPN) are all factors that are most likely to affect: Stability Virtual private networks (VPNs) and which standard have historically suffered from conflicts when used together? Network Address Translation (NAT) Which of the following is an advantage of Secure Sockets Layer/Transport Layer Security (SSL/TLS) virtual private networks (VPNs) versus Internet Protocol Security (IPSec) VPNs? No NAT problems The IT department of a company has just rolled out a virtual private network (VPN) solution that offers greater flexibility, delegation of management, and added security over the previous implementation. What is this solution called? Secure Sockets Layer (SSL) virtualization Which of the following is a core Internet Protocol Security (IPSec) protocol that provides encryption only, both encryption and integrity protection, or integrity protection only in all but the oldest IPSec implementations? Encapsulating Security Payload (ESP) Which Internet Protocol Security (IPSec) core component negotiates, creates, and manages security associations? Internet Key Exchange (IKE) Which of the following is the protocol used with HTTPS for encrypting communications to and from websites? Secure Sockets Layer/Transport Layer Security (SSL/TLS) A software-based virtual private network (VPN) may be part of a server operating system, part of an appliance operating system, or a third-party add-on software solution. True A hardware virtual private network (VPN) is a standalone device, dedicated to managing VPN functions. True The functionalities of software and hardware virtual private network (VPN) solutions are fundamentally different. False Software-based virtual private networks (VPNs) are typically more scalable than hardware VPNs. False Layer 2 of the Open Systems Interconnection (OSI) Reference Model is the Data Link Layer. True The Network Layer of the Open Systems Interconnection (OSI) Reference Model is the protocol layer that transfers data between adjacent network nodes. False Internet Protocol Security (IPSec) has three major components: Authentication Header (AH), Encapsulating Security Payload (ESP), and Internet Key Exchange (IKE). True Authentication Header (AH) provides integrity protection for packet headers and data, as well as user authentication. True Internet Protocol Security (IPSec) supports both transport mode and tunnel mode. True The Secure Shell (SSH) protocol is a method for secure remote login and other secure network services over a public network. True In IPSec tunnel mode, only the data packet payload is encapsulated, while the packet header is left intact. False The performance characteristics associated with an Internet Protocol Security (IPSec) virtual private network (VPN) can be very different from a Secure Sockets Layer (SSL) VPN implementation. True How you apply Internet Protocol Security (IPSec) and Secure Sockets Layer/Transport Layer Security (SSL/TLS) in a virtual private network (VPN) solution can affect VPN performance. True Client capabilities do not affect the performance of a remote virtual private network (VPN) connection. False Depending on the location of a virtual private network's (VPN's) endpoints, the topology may affect performance. True The higher the encryption level of a virtual private network (VPN) connection, the greater the impact on the memory and processor of the endpoint devices. True The stability of a virtual private network (VPN) connection can be affected by the number of firewalls and routers it must traverse. True Internet Protocol Security (IPSec) is designed to work well with network address translation (NAT). False A virtualized desktop is hosted on a remote central server instead of on the local hardware of the remote client. True A virtualized Secure Sockets Layer (SSL) virtual private network (VPN) provides the ability to create custom authentication methods. True Oscar is deploying a virtual private network (VPN) solution for his company. The VPN needs to connect to remote servers by their Internet Protocol (IP) addresses rather than using network address translation (NAT). What type of VPN is Oscar deploying? Operating system (OS) Wen, a network engineer for a mid-sized company, is rolling out a virtual private network (VPN) solution that is easy to set up, manage, and maintain and represents the majority of VPN platforms on the market. What type of VPN is Wen deploying? Customer premise equipment (CPE) Tonya is an accountant working from home. She connects to her office each day over a virtual private network (VPN). The IT department for her company has deployed a VPN appliance to assist employees such as Tonya in performing their tasks remotely. What solution does Tonya use to access her files on the company's accounting server? Host-to-gateway Remote Desktop Connection (RDC) is a built-in application that uses what proprietary protocol? Remote Desktop Protocol (RDP) Dhruv is a network engineer using a command-line interface on his computer. He types the command mstsc/v and then a server name. What is he doing? Connecting to a Windows server running a virtual private network (VPN) Alice is a network engineer who has been tasked with researching a virtual private network (VPN) tunneling protocol to be used by her company. It must be able to pass traffic through a network address translation (NAT) server and be compatible with a number of well-known proprietary and open source platforms. What solution does she select? Internet Key Exchange v2 (IKEv2) Various virtual private network (VPN) encryption technologies offer access to almost any network application or resource. Which one offers additional features, such as easy connectivity from non-company-managed desktops, little or no desktop software maintenance, and user-customized web portals upon login? Secure Sockets Layer/Transport Layer Security (SSL/TLS) Jacob is a remote employee. He clicks the Start menu button in Windows and selects an application to run. Most of the time, he is unaware that he is really accessing the application on a server at his company's main office several miles away. What solution is he using? RD RemoteApp Bill's work-issued Windows laptop has been configured so he can remotely connect to his office from home without having to initiate a virtual private network (VPN) connection. What technology is he using? DirectAccess Isabelle is a network engineer deploying an IT infrastructure in one of her company's new branch offices. Currently, she is designing a local subnetwork that contains and exposes the office's external services to a larger, untrusted network, specifically the Internet. What is this called? Demilitarized zone (DMZ) James is a network engineer. He has been assigned the responsibility of designing a virtual private network (VPN) solution that will allow customers, suppliers, and business partners access to network resources without exposing the secure private LAN. The parties accessing these resources must use digital certificates issues by a certification authority (CA). What form of VPN is he setting up? Extranet Which of the following best describes a technology with the least inherent security risks and is less likely to reveal information a user did NOT intend to share? Onion routing A company uses an Internet Protocol Security (IPSec) virtual private network (VPN) solution. It allows remote users to connect to the main office and allows communication between the main office and branch offices securely over the Internet. The main office network uses network address translation (NAT) with an internal IP address range of 192.168.0.1 to 192.168.0.254. Which of the following ranges must remote offices and users NOT use on their internal networks? 192.168.0.x Nimi has deployed a new virtual private network (VPN) solution in her company's IT infrastructure. She is testing the connection to the server from a client. Which tool is the best choice for her to use? Ping Marta is a network technician intern at a mid-sized company. She is learning hardware virtual private network (VPN) best practices from one of the engineers. Which of the following does the engineer tell Marta is NOT a best practice? Connecting a client computer to more than one network interface while connected to the office via VPN Susan is a network professional at a mid-sized company. Her supervisor has assigned her the task of designing a virtual private network (VPN) implementation. Susan has set up strong authentication and encryption in a test environment, and the VPN appliance is directly facing the Internet. When her work is evaluated, what does her supervisor immediately notice? The VPN device is not protected by a firewall. Carl is a student in a computer networking class who is studying virtual private network (VPN) implementations. He is learning the basics about VPNs. Which of the following statements does he find is TRUE? VPNs are both hardware and software solutions. Lin is designing a virtual private network (VPN) implementation as a class project. The assignment includes a budget she has to follow. To save money, she decided to use a VPN without a firewall. What is the problem with her decision? This approach will not work because VPNs cannot take the place of firewalls. Arturo is a new network technician. He wants to use Remote Desktop Protocol (RDP) to connect to a server from his computer. The server is on the other side of the building. His computer is running Windows 10. Will he be able to make the connection? Yes, because the RDP protocol has clients that work on most common operating systems. What is a virtual private network (VPN) protocol that requires public key infrastructure (PKI) support to obtain and use a certificate? Secure Sockets Layer/Transport Layer Security (SSL/TLS) A customer premise equipment (CPE)-based virtual private network (VPN) is a VPN appliance. True A virtual private network (VPN) replaces a firewall. False Whereas a virtual private network (VPN) encrypts pieces of data, a firewall protects the internal network from outside threats. True In a gateway-to-gateway virtual private network (VPN), the mobile user takes specific actions to connect to the VPN. False Remote Desktop Protocol (RDP) is a proprietary protocol developed by Microsoft. True Remote Desktop Connection (RDC) is a built-in application that uses Remote Desktop Protocol (RDP). True Microsoft Remote Assistance allows support professionals to remotely control a user's system. True An SSL/TLS-based virtual private network (VPN) enables remote access connectivity from almost any Internet-enabled location using a web browser. True RD RemoteApp is a Microsoft solution that runs on a Microsoft Remote Desktop Services (RDS) server but appears to end users as if it were actually running on their systems. True RD Web Access is a Microsoft Remote Desktop Services (RDS) server role that allows desktops and RD RemoteApp applications to launch from a web browser. True Microsoft RD Web Access connects remote clients to internal resources over a virtual private network (VPN) connection. False With hosted services, an Internet service provider (ISP) or a software vendor leases applications to organizations. True Microsoft DirectAccess enables administrators to execute control over remote clients such as through Group Policy. True A virtual private network (VPN) server for remote access must be located in the demilitarized zone (DMZ). False An intranet virtual private network (VPN) connects two or more internal networks. True An intranet virtual private network (VPN) never traverses a wide area network (WAN) link. False Extranets differ from intranets in that remote users outside of the enterprise are allowed access to resources inside the network. True Onion routing limits a network's vulnerability to eavesdropping and traffic analysis. True A virtual private network (VPN) implementation best practice is to use strong authentication. True A virtual private network (VPN) implementation best practice is to protect the VPN server behind a firewall. True Besides a firewall, numerous other elements are often implemented to protect a network, EXCEPT: a public IP address proxy. While fragmentation of IP packets is supported when they encounter network segments that have a smaller maximum transmission unit (MTU), that feature can be manipulated by malicious parties in overlapping attacks. In calculating a defense for such an exploit, what is the only reliable defense? A dynamic filtering system that performs virtual reassembly Hacker tunneling uses two techniques. The first is to install a server component on an internal system and then have an external client make a connection. What is the second? Install a server component on an external system and then use an internal client to make the connection. In a tunneling attack, once the tunnel is open, what are the limitations? Data can move in either direction. During which step of firewall incident response is the compromise resolved? Eradication Which of the following is a malicious remote control tool? NetBus All of the following protect against fragmentation attacks, EXCEPT: Internal code planting Hong is a network engineer. He is developing a firewall policy that addresses troubleshooting a firewall that has either failed or is under attack. In his plan, what should be included as a best practice? Collect firewall documentation before an attack. Lin is a disgruntled IT technician who believes she is about to be discharged from her job. While she still has access to her company's network infrastructure, she decides to reset the main firewall to its factory settings so she will know the default administrative username and password. Which of the following is the method she is MOST likely to use? She uses a straightened paper clip to press the pinhole-sized reset button in the back of the firewall for 30 seconds. Arturo is troubleshooting a firewall that may have been hacked by a malicious outsider. He is under pressure and immediately tries a fix that, if it fails, will not be easy to back out of. Before he makes the attempt, his supervisor warns him of the danger. What does Arturo's supervisor say? Avoid destructive or irreversible solutions until last. ______ is commonly exploited by many hackers because most enterprise web traffic is _________. Encryption; encrypted [Show More]
Last updated: 1 year ago
Preview 4 out of 16 pages

Loading document previews ...
Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Also available in bundle (1)
Click Below to Access Bundle(s)

ITN 263 FINAL EXAMS BUNDLE
ITN 263 FINAL EXAMS BUNDLE
By Ajay25 1 year ago
$18
2
Reviews( 0 )
$15.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Aug 04, 2024
Number of pages
16
Written in
All
Additional information
This document has been written for:
Uploaded
Aug 04, 2024
Downloads
0
Views
253