Education > TEST BANKS > TEST BANK FOR Network Defense and Countermeasures Principles and Practices, 4th Edition by William E (All)
TEST BANK FOR Network Defense and Countermeasures Principles and Practices, 4th Edition by William Easttom
Document Content and Description Below
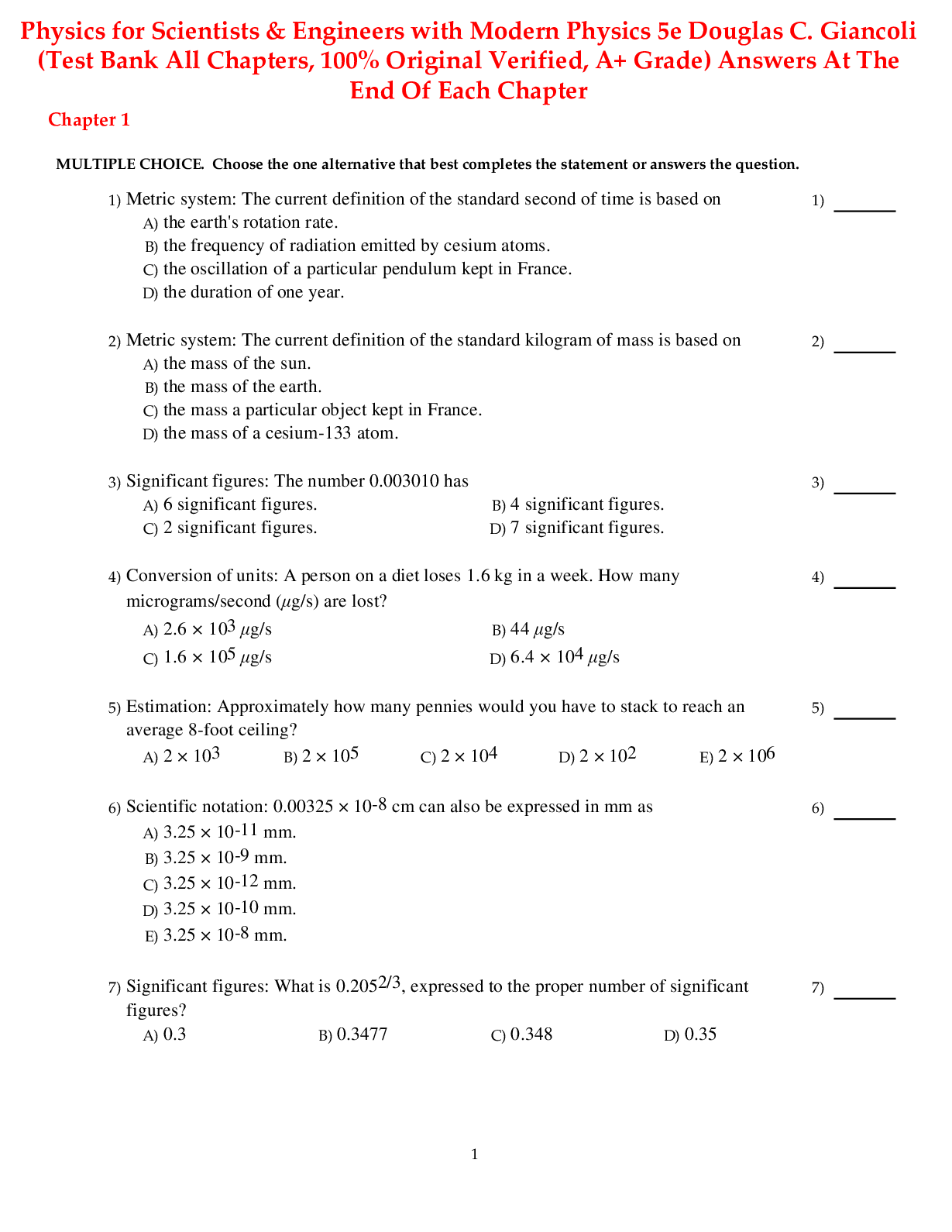
TEST BANK FOR Network Defense and Countermeasures Principles and Practices, 4th Edition by William Easttom-1) Which of the following is the unique address of the network interface card (NIC)? A) IP a... ddress B) NIC address C) MAC address D) URL address Answer: C 2) Which of the following commands can you use to find your computer‟s IP address and network information about your system? A) Ipconfig B) Ping C) Tracert D) None of the above Answer: A 3) Which of the following commands can be used to determine if a system is reachable and how long a packet takes to reach that system? A) Ipconfig B) Ping C) Tracert D) None of the above Answer: B 4) Which of the following protocols operates at the transport layer of the OSI model? A) FTP B) TCP C) DNS D) IP Answer: B 5) Which of the following layers of the OSI model is responsible for routing the information in the network? A) Transport layer B) Network layer C) Session layer D) Physical layer Answer: B 6) The OSI model is divided into how many layers? A) Four B) Five C) Six D) Seven Answer: D 7) Most attacks can be classified as one of three broad classes. Which of the following is not one of these classes? A) Viruses B) Malware C) Blocking D) Intrusion Answer: A 8) Denial of service (DoS) attacks fall under which of the following categories of attacks? A) Viruses B) Malware C) Blocking D) Intrusion Answer: C 9) Which of the following is a small text file that web pages can place on your computer to keep track of your browsing activity? A) Spyware B) Cookie C) Key logger D) Trojan Answer: B 10) In which of the following attacks does a hacker use a computer to call phone numbers in sequence until another computer answers? A) War-driving B) War-calling C) War-dialing D) War-flying Answer: C 11) Which of the following types of hackers will report a vulnerability when they find it? A) White hat B) Gray hat C) Green hat D) Black hat Answer: A 12) Which of the following types of hackers hacks into systems to cause harm or steal data? A) White hat B) Gray hat [Show More]
Last updated: 8 months ago
Preview 5 out of 69 pages

Loading document previews ...
Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$12.50
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Oct 09, 2024
Number of pages
69
Written in
Additional information
This document has been written for:
Uploaded
Oct 09, 2024
Downloads
0
Views
23



















.png)


