Computer Science > EXAM > ITN 260 Midterm Exam | Q & A (Complete Solutions) (All)
ITN 260 Midterm Exam | Q & A (Complete Solutions)
Document Content and Description Below
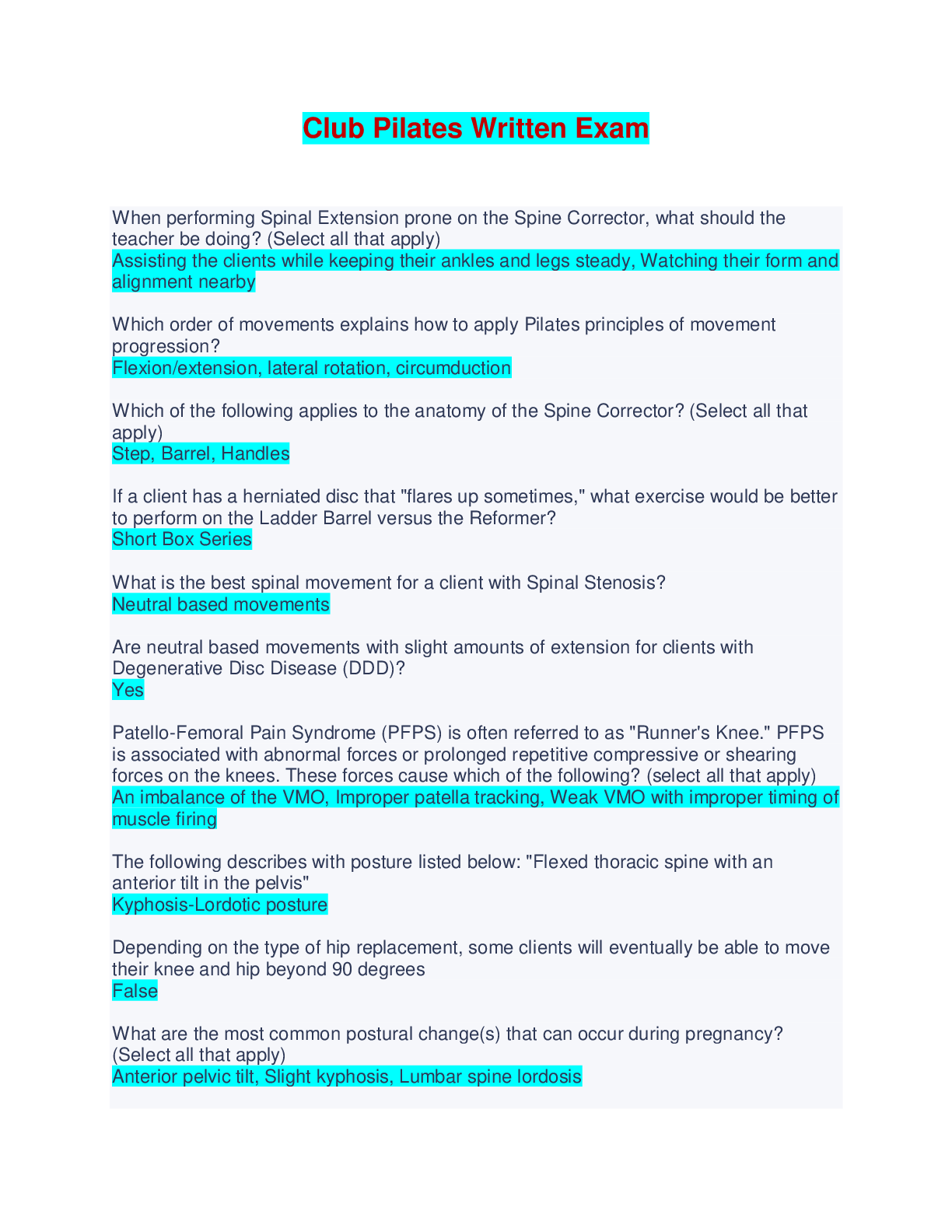
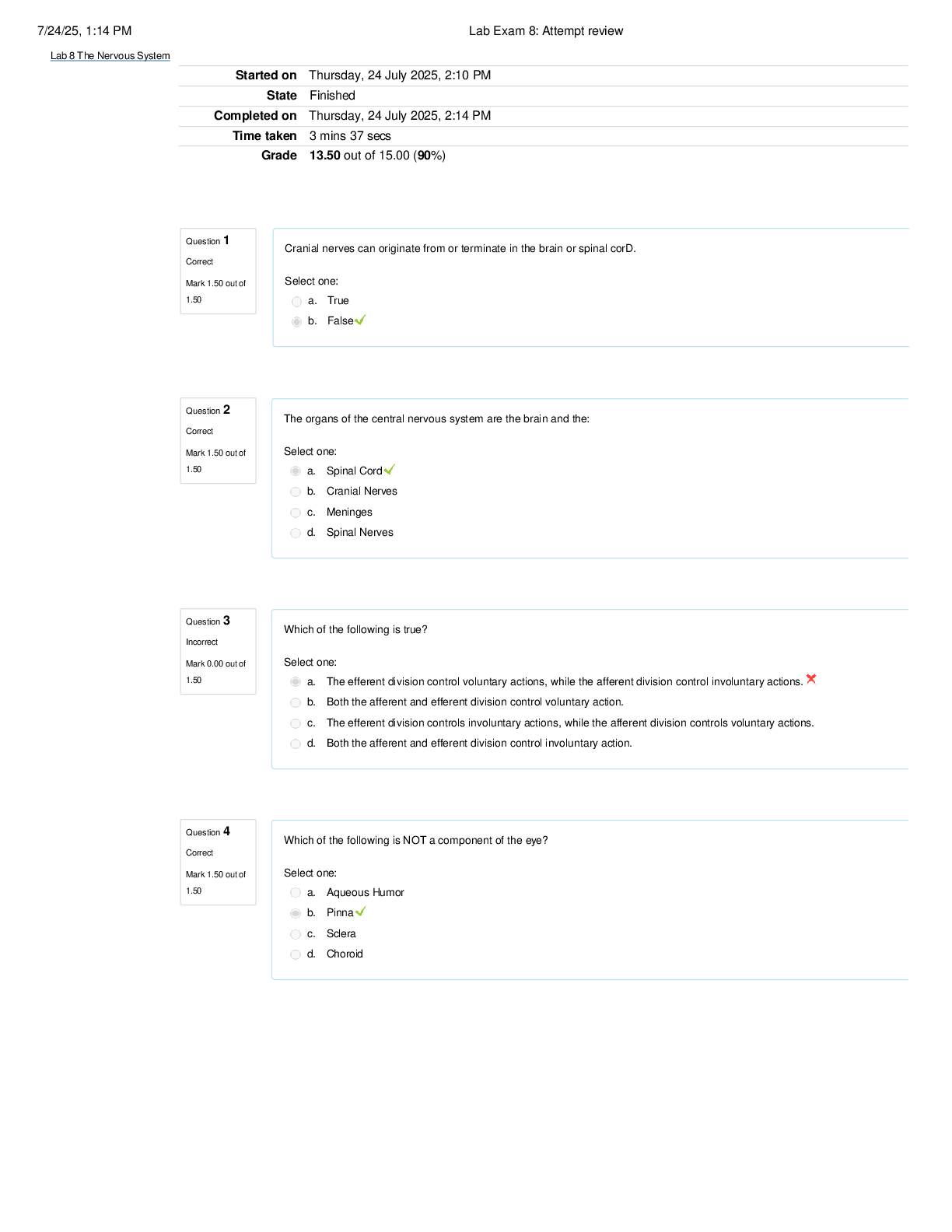
ITN 260 Midterm Exam | Q & A (Complete Solutions) Which of the following is a major objective of a packet analysis? a. Ensure physical security b. Estimate network cost c. Calculate employee work h ... ours d. Assess and secure networks You are a cyber forensic expert wanting to protect devices retrieved from a crime scene from being remotely wiped of evidence. Which of the following physical security equipment should you use so that inbound and outbound signals cannot be sent or received? a. Faraday bags b. Protected cable distribution c. Mantraps d. Cable locks A source computer's ability to reach a specified destination computer can be tested using which of the following? a. ifconfig b. ping c. curl d. ipconfig In an interview, you are given the following scenario: David sent a message to Tina saying, "There is no school today!" For some reason, the message shoed up on Tina's device as, "Come to the school ASAP!" You (the candidate) are asked to name the type of attack that would cause this situation. Which of the following should you identify? a. Macro attack b. DNS hijacking c. MITM d. DDoS Which of the following best describes bash? a. Bash is a network assessment tool b. Bash is computer hardware c. Bash is a command language interpreter d. Bash is a physical security measure Which of the following is a third-party network analysis tool? a. netstat b. hping c. curl d. nmap In an interview, you are asked to change the permissions of a file on a Linux system so that the file can only be accessed by its owner. Which of the following tools should you use? a. Nessuss b. grep c. chmod d. Cuckoo Which of the following is an external perimeter defense method? a. Fire supression b. Barrier c. Demilitarized zone (DMZ) d. Electronic lock Which of the following statements about domain reputation is correct? a. Domain reputation will be low if the domain is used for distributing malware or launching attacks b. Domain reputation will be high if the enterprise has access to a huge volume of resources c. Domain reputation will be high if the domain is used for distributing malware or launching attacks d. Domain reputation will be low if the enterprise has access to a huge volume of resources Which of the following is a layer 2 attack? a. DNS poisoning b. DNS hijacking c. ARP poisoning d. DDoS Your enterprise is hosting a web app that has limited security. As a security administrator, you are asked to take appropriate measures to restrict threat actos from hijacking users' sessions. Which of the following is the most appropriate action for you to take? a. You should mention "log off after visit" on the web app b. You should implement cryptography using OpenSSL c. You should provide each user a unique static session ID d. You should encrypt the session ID displayed on the URL Which of the following best describes VBA? a. VBA is a hardware network security device b. VBA is an event-driven programming language c. VBA is a network assessment tool d. VBA is a command language interpreter You are asked to configure your firewall in such a way that the traffic from source address range 117.112.10.25 through 117.112.15.100 is allowed, while traffic from 117.112.12.25 through 117.112.13.25 is denied, and traffic from 117.112.12.200 through 117.112.13.10 is allowed. How should you configure the firewall? a. Deny 117.112.12.200 through 117.112.13.10; deny 117.112.12.25 through 117.112.13.25; allow 117.112.10.25 through 117.112.15.100 b. Allow 117.112.12.200 through 117.112.13.10; deny 117.112.12.25 through 117.112.13.25; force-allow 117.112.10.25 through 117.112.15.100 c. Allow 117.112.10.25 through 117.112.15.100; deny 117.112.12.25 through 117.112.13.25; force-allow 117.112.12.200 through 117.112.13.10 d. Allow 117.112.10.25 through 117.112.15.100; deny 117.112.12.25 through 117.112.13.25; allow 117.112.12.200 through 117.112.13.10 Which of the following outlines the process of a proxy server? a. User - forward proxy - Internet - reverse proxy - server b. User - internet - reverse proxy - forward proxy - user c. User - reverse proxy - Internet - forward procy - server d. User - forward proxy - user - reverse proxy - Internet Which of the following techniques is the best fit for monitoring traffic on switches with large volumes of traffic? a. Signature-based monitoring b. Port spanning c. Port mirroring d. Port TAP In an interview, Max was asked to tell one difference between a software firewall and a virtual firewall. How should Max answer? a. Software firewalls are locally installed on a device, whereas virtual firewalls run in the cloud b. Software firewalls can protect all the endpoints in a network, whereas virtual firewalls can protect only one device c. Virtual firewalls are cost-free, whereas software firewalls are paid services d. Virtual firewalls are used on almost all devices, whereas software firewalls are mostly used by enterprises What action does a BPDU guard take when a BPDU is received from an endpoint and not a switch? a. The port is disabled, and no traffic will be sent by the port while it can still receive traffic b. The port is disabled, and no traffic will be sent or received by the port c. The port remains active, and no traffic will be received by the port, but it can still send traffic d. The port remains active, and the traffic will be forwarded to another port Which of the following best describes east-west traffic? a. Movement of data from a router to an enterprise switch b. Movement of data from an unsecured endpoint to a server outside a data center c. Movement of data from one server to another within a data center d. Movement of data from one unsecured endpoint to another The head of cybersecurity at your enterprise has asked you to set p an IDS that can create the baseline of all system activities and raise an alarm whenever any abnormal activities take place, without waiting to check the underlying cause. Which of the following actions should you take? a. You should set up an IDS with signature-based monitoring methodology b. You should set up an IDS with heuristic monitoring methodology c. You should set up an IDS with behavior-based monitoring methodology d. You should set up an IDS with anomaly-based monitoring methodology An employee at your enterprise is caught violating company policies by transferring confidential data to his private email. As a security admin, you are asked to prevent this from happening in the future. Which of the following actions should you perform? a. You should set up a VPN b. You should set up a DLP c. You should set up a NAC d. You should set up an ACL After encountering a network attack in your enterprise network, the chief network security engineer assigned you a project. The project was to create a vulnerable network that is similar to your enterprise network and entices the threat actor to repeat the attack. This is to analyze the behavior and techniques the attacker is using to ensure better defenses to your enterprise network in the future. Which of the following appliances should you use? a. You should set up a network access control b. You should use a proxy server c. You should use a honeynet d. You should set up behavioral IDS monitoring Which type of intrusion detection system can also block attacks? a. Inline b. Preline c. Postline d. Passive In an interview, you are asked ot analyze the following statements regarding secure network designs and choose the correct one. Which of the following should you choose? a. Load balancers can detect and stop protocol attacks directed at a server or application b. Workgroup switches reside at the top of the hierarchy and carry traffic between switches c. When VLAN members on the same switch communicate with each other, the switch uses tags to transfer the packets d. Zero trust is designed to make a system trusted Which of the following best describes a host-based firewall? a. A host-based firewall is a software firewall that protects a single endpoint device b. A host-based firewall is a software firewall that protects multiple endpoint devices c. A host-based firewall is a hardware firewall that protects a single endpoint device d. A host-based firewall is a hardware firewall that protects multiple endpoint devices Which monitoring methodology will trigger the IDS if any application tries to scan multiple ports? a. Anomaly-based monitoring b. Signature-based monitoring c. Heuristic monitoring d. Behavior-based monitoring In an interview, you are asked to configure a DNS server on a Linux michaine. After successfully configuring the DNS server, you are asked to examine it using a client machine. After changing the nameserver of the client's machine to a newly created server, which of the following commands should you run to validate the DNS server to ensure it is working properly? a. ifconfig www.google.com b. dig www.google.com c. ping www.google.com d. nslookup www.google.com During an interview, you are provided the following scenario: The enterprise that you recently joined is using the ISP DNS server to resolve domain names. You are asked which specific attack will need to be mitigated first to secure the enterprise network. Which of the following attacks should you choose? a. MAC cloning b. Session replay attack c. DDoS attack d. DNS hijacking You are a security expert asked to protect the webservers hosted in your building from exposure to anyone other than server admins. Which of the following physical security methos should you implement ot achieve this? a. Demilitarized zones b. Vault c. Faraday cage d. Protected cable distribution Which of the following correctly differentiates between a man-in-the-middle (MITM) attack and a man-in-the-browser (MITB)? a. A MITM attack occurs between two endpoints, whereas a MITB attack occurs between a browser and web server b. A MITM attack occurs between two endpoints, whereas a MITB attack ocurs between a browser and underlying computer c. A MITM attack can only analyze the intercepted packet, whereas a MITB attack can modify the intercepted packet d. a MITM attack can modify the intercepted packet, whereas a MITB attack can only analyze it Which of the following correctly differentiates between Tcpreplay and Tcpdump? a. Tcpdump can analyze, edit, and load the edited packet back to the network, whereas Tcpreplay can only be used to analyze the packets b. Tcpdump is a packet capture tool without GUI, whereas Tcpreplay is a packet capture tool with GUI c. Tcpdump can only be used to analyze the packets, whereas Tcpreplay can analyze, edit, and load the edited packet back to the network d. Tcpdump is a packet capture tool with GUI, whereas Tcpreplay is a packet capture tool without GUI Maze must establish a communication channel between two data centers. After conducting a study, she came up with the idea of establishing a wired connection between them since they have to communicate in unencryted form. Considering the security requirements, Maze proposed using an alarmed carrier PDS over a hardened carrier PDS. Why would Maze make this suggestion in her proposal? a. Data transmission between buildings wouldn't be possible if they used a hardened carrier PDS b. Network speeds would be slowed too much if they used a hardened carrier PDS c. Using a hardened carrier PDS would restrict their ability to transfer large amounts of data d. Using a hardened carrier PDS would require someone to conduct periodic visual inspections Which of the following can prevent macros attacks? a. Private DNS server b. VBA c. Protected view d. PowerShell You are analyzing the settings for your network's firewall. There is currently a log-only rule set for the source address 112.101.2.4. Which of the following configuration may create a log entry? a. A rule is set to deny all packets from 112.101.1.1 through 112.101.2.11 b. A rule is set to bypass all packets from 112.101.1.1 through 112.101.2.5 c. A rule is set to bypass all packets from 112.101.2.4 d. A rule is set to allow all packets from 112.101.2.1 through 112.101.2.22 Which protocol is used to prevent looping in a switch? a. STP b. SMTP c. SSL d. SSTP Which of the following best describes an extranet? a. Private network only accessed by an authorized party b. Additional network bandwidth being allocated c. Private network accessed by the public d. Public network accessed by proper authorization What is a jump box used for? a. Restricting access to a demilitarized zone b. bypassing a firewall by generating a log entry c. Deceiving threat actors by internationally creating vulnerable devices d. Switching from a public IP to a private IP As a cybersecurity expert, you are asked to take adequate measures to mitigate DDoS attacks on your enterprise servers. Which of the following techniques should you apply? a. You should set up a DNS sinkhole b. You should set up a virtual private network c. You should set up a proxy server d. You should set up a host-based firewall How do NACs ensure that a device is safe to connect to a secure network? a. The NAC ensures the safety of the device by deleting all suspicious files b. The NAC encrypts all of the data on an unknown device before connecting it to the secured network c. The NAC issues a health certificate, only allowing healthy devices to connect to the secured network d. The NAC moves suspicious data on an unknown device onto an external storage device Which technology allows scattered users to be logically grouped even when they are connected to different physical switches? a. WAN b. VPN c. VLAN d. LAN As a cybersecurity specialist, you are asked to defend the web app hosted by your enterprise from web application attacks like cross-site scripting, SQL injections, etc. Which of the following actions should you take? a. You should install a NGFW b. You should install an NAT c. You should install a WAF d. You should install a proxy server Which of the following best describes a network address translation? a. A network address translation (NAT) is a device that combines several security functions like packet filtering, anty-spam, anti-phishing, anti-spyware, encryption, intrusion protection, and web filtering b. A network address translation (NAT) blocks specific websites or attacks that attempt to exploit known vulnerabilities in specific client software c. A network address translation (NAT) can detect applications using deep packet inspection by examining the packet payloads and determining if they are carrying any malware d. A network address translation (NAT) enables a private IP network to connect to the internet You oversee your company's physical security, and you are asked to protect their CCTV cameras. The cameras are installed along the pathway, mounted on poles. They need protection from being physically handled by potential intruders. Which of the following fencing deterrents should you use? a. Rotating spikes b. Roller barrier c. Anticlimb collar d. Bollards Which specific type of attack occurs when a threat actor redirects network traffic by modifying the local host file to send legitimate traffic anywhere they choose? a. On-path browser attack b. DNS hijacking c. DNS poisoning d. Port stealing Tyler is a cybersecurity expert assigned to look after the security of a public DNS server. One day, during his usual inspection of the DNS server, he found that the DNS take has been altered, resulting in URL redirection for some users. What type of attack has Tyler discovered? a. DNS hijacking b. DNS poisoning c. XSS d. DDoS Which of the following sensors is best suited for fire detection? a. Noise detection sensor b. Motion detection sensor c. Proximity sensor d. Temperature detection sensor Which of the following is physical security equipment for computer hardware? a. Alarmed carrier PDS b. Robot sentry c. Faraday cage d. Bollards Which of the following best describes a network hardware security module? a. A network hardware security module is a hardware firewall that monitors incoming and outgoing traffic of a network b. A network hardware security module is an intrusion detection system that detects any intrusion in a network c. A network hardware security module is a deception instrument used to deceive threat actos by intentionally deploying vulnerable devices d. A network hardware security module is a trusted network computer that performs cryptographic operations Sansa is a network security administrator at an enterprise. She is asked to take appropriate steps to defend against a MAC address spoofing attack in the enterprise network. Which of the following methods should Sansa apply? a. Increase the capacity of CAM to allow for an increased volume of MAC addresses b. Configure the switch so that no changes can be done once a port is assigned to a MAC address c. Close all unused ports in the switch so that old MAC addresses are not allowed d. Configure the switch so that only one port can be assigned per MAC address Which of the following is associated with port security? a. Split tunnel b. Spanning-tree protocol c. Masking d. Tokenization You are asked to configure your enterprise network in such a way that the customer support team gets a higher priority in the network and can conduct customer video calls without any connectivity issues. Which of the following methods should you apply? a. You should set up quality of service to give higher priority to the customer support team b. You should set up a VPN to give higher priority to the customer support team c. You should set up load balancers to give higher priority to the customer support team d. You should set up masking to give higher priority to the customer support team Which of the following best describes DLP? a. DLP is a VPN protocol b. DLP is a protocol used to transfer data within switches c. DLP is used to control access to digital assets d. DLP is used to prevent leakage of confidential data John needs to add an algorithm for his company communication process, which encryption uses two keys. One is the public key, and the other one is a private key. Which algorithm will be suitable to achieve this? a. Asymmetric cryptographic b. Private key cryptographic c. Lightweight cryptographic d. Symmetric cryptographic Which feature of cryptography is used to prove a user's identity and prevent an individual from fraudulently reneging on an action? a. Confidentiality b. Nonrepudiation c. Ofuscation d. Authenticaiton Which of the following statements describe a quantum computer? a. A quantum computer is a computer that relies on qubits that can be both 0 and 1 at the same time b. A quantum computer uses encrypted hardware until the correct password is provided and all data copied to the computer is automatically encrypted c. A quantum computer is a computer that uses the structure of physical gadgets with sensors, software, and other technologies to connect and swap data with other devices and systems over the internet d. A quantum computer is a computer with a chip on its motherboard that provides cryptographic services, includes a true random number generator, and supports fully asymmetric encryption A manager working in ABC Consulting shared a list of employees from his team who were eligible for an extra week off. Later, he claimed that he has never shared this list. Which principle or functionality of a secured communication can be used to substantiate or verify the manager's claim? a. Obfuscation b. Nonrepudiation c. Steganography d. Hashing Which characteristic of cryptography makes information obscure or unclear, and by which the original information becomes impossible to be determined? a. Obfuscation b. Nonrepudiation c. Authentication d. Integrity A new e-commerce startup with global operations is looking for a method to manage its supply-chain data for production. Instead of using bar codes, scanners, paper forms, and individual databases, making the system difficult to use, which method should be used to quickly track shipments? a. File and file system cryptography b. USB device encryption c. Full disk encryption d. Blockchain Alex needs to find a method that can change a single character of plaintext into multiple characters of ciphertext. Which method should Alex use? a. Steganography b. Diffusion c. Obfuscation d. Confusion Which encryption method in BitLocker prevents attackers from accessing data by booting from another OS or placing the hard drive in another computer? a. Filesystemcryptography b. Blockchain c. GNU privacy guard d. Full disk encryption Kainat is asked to suggest a cipher in which the entire alphabet is rotated (as in, A=N, B=O), making it difficult to identify. Which cipher should she suggest? a. 3DES b. ROT13 c. XOR d. AES Spectrum Technologies uses SHA-256 to share confidential information. The enterprise reported a breach of confidential data by a threat actor. You are asked to verify the cause of the attack that occurred despite implementing secure cryptography in communication. Which type of attack should you consider first, and why? a. Known ciphertext attack; the attacker can create the cryptographic keys from ciphertext because of the SHA-256 algorithm b. Downgrade attack; SHA-256 is vulnerable to downgrades in the operating system to earlier versions, allowing threat actos to easily attack c. Misconfiguration attack; the company should have configured a higher security hash algorithm rather than using the less-secure SHA-256 d. Collsion attacks; the threat actor has created a malicious file with the same digest using SHA-256 Blockchain relies on which cryptographic algorithm to make it computationally infeasible to try to replace a block or insert a new block of information without the approval of all entities involved? a. Cryptographic hash algorithms b. Symmetric cryptographic algorithms c. RSA algorithm d. Asymmetric cryptographic algorithms Which of the following is NOT an attack on cryptography? a. Algorithm attack b. Collission attack c. Watering hole attack d. Birthday attack Which of the following is defined as a structure for governing all the elements involved in digital certificate management? a. PKI b. Web of trust model c. M-of-N control d. CA During an investigation, it was found that an attacker did the following: Intercepted the request from the user to the server and established an HTTPS connection between the attacker's computer and the server while having an unsecured HTTP connection with the user. This gave the attacker complete control over the secure webpage. Which protocol helped facilitate this attack? a. S/MIME b. SSL c. SSH d. ECB Which of the following terms best describes the process in which a user believes that the browser connection they are using is secure and the data sent is encrypted when in reality, the connection is insecure, and the data is sent in plaintext? a. SSL stripping b. Revocation c. SQL injection d. API attack Which of the following is a process where a private key is split into two halves, encrypted, and stored separately for future use? a. Revocation b. Escrow c. Renewal d. Destruction Samira is developing a virtual private chat application for ABC Consulting. The following are requirements provided by the organization while making the application: 1. All the communications should happen within the same network, network-to-network 2. The information shared through this app should be kept confidential. Hence, the whole IP packet should be encrypted, giving access to only authorized personnel 3. There should be a private network for network-to-network communication Which of the following modes should Sara consider for encryption in this project? a. Transport mode b. Tunnel mode c. GCM mode d. Counter mode Sarah needs to send an email with important documents to her client. Which of the following protocols ensures that the email is secure? a. SSH b. SSL c. S/MIME d. SHTTP Under which of the following modes does the ciphertext depend only on the plaintext and the key, independent of the previous ciphertext blocks? a. GCM b. CRT c. ECB d. CBC Which of the following is a characteristic of electronic code book (ECB) mode? a. Only one character is processed at a time b. It requires access to a synchronous counter for both the sender and receiver of the message c. Each block of plaintext is XORed with the previous block of ciphertext f before being encrypted, making it susceptible to attacks d. Two identical plaintext blocks are encrypted into two identical ciphertext blocks, making them susceptible to attacks Which of the following is the earliest and most general cryptographic protocol? a. SSH b. SSL c. TLS d. HTTPS Star Technology is working on a project that needs a communication mode specializing in encryption, where only authorized parties should understand the information. The company also requires accuracy, completeness, and reliability of data throughout the project. The company has contact you for an ideal cipher mode solution. Which mode should you suggest? a. SSH b. HTTPS c. CBC d. S/MIME Which of the following is a standard format for digital certificates? a. JPG b. .cer c. MPEG-4 Part 14 d. X.509 Sigma Technology is a company based in Singapore, with branches in 24 countries. It needs multiple CAs in different locations to verify and sign digital certificates for the company. They are looking for an option where, even in the absence of a CA, other CAs can issue the certificates. Additionally, they are also looking for CAs who will overlook other CAs in different locations. In such a scenario, which PKI trust model should they use? [Show More]
Last updated: 9 months ago
Preview 1 out of 41 pages

Loading document previews ...
Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$19.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Mar 11, 2025
Number of pages
41
Written in
All
Additional information
This document has been written for:
Uploaded
Mar 11, 2025
Downloads
0
Views
39