Computer Science > QUESTIONS & ANSWERS > NT2580 Introduction to Information Security- NT 2580NT2580 Week 3, Assignment 3-1(2) (1) (All)
NT2580 Introduction to Information Security- NT 2580NT2580 Week 3, Assignment 3-1(2) (1)
Document Content and Description Below
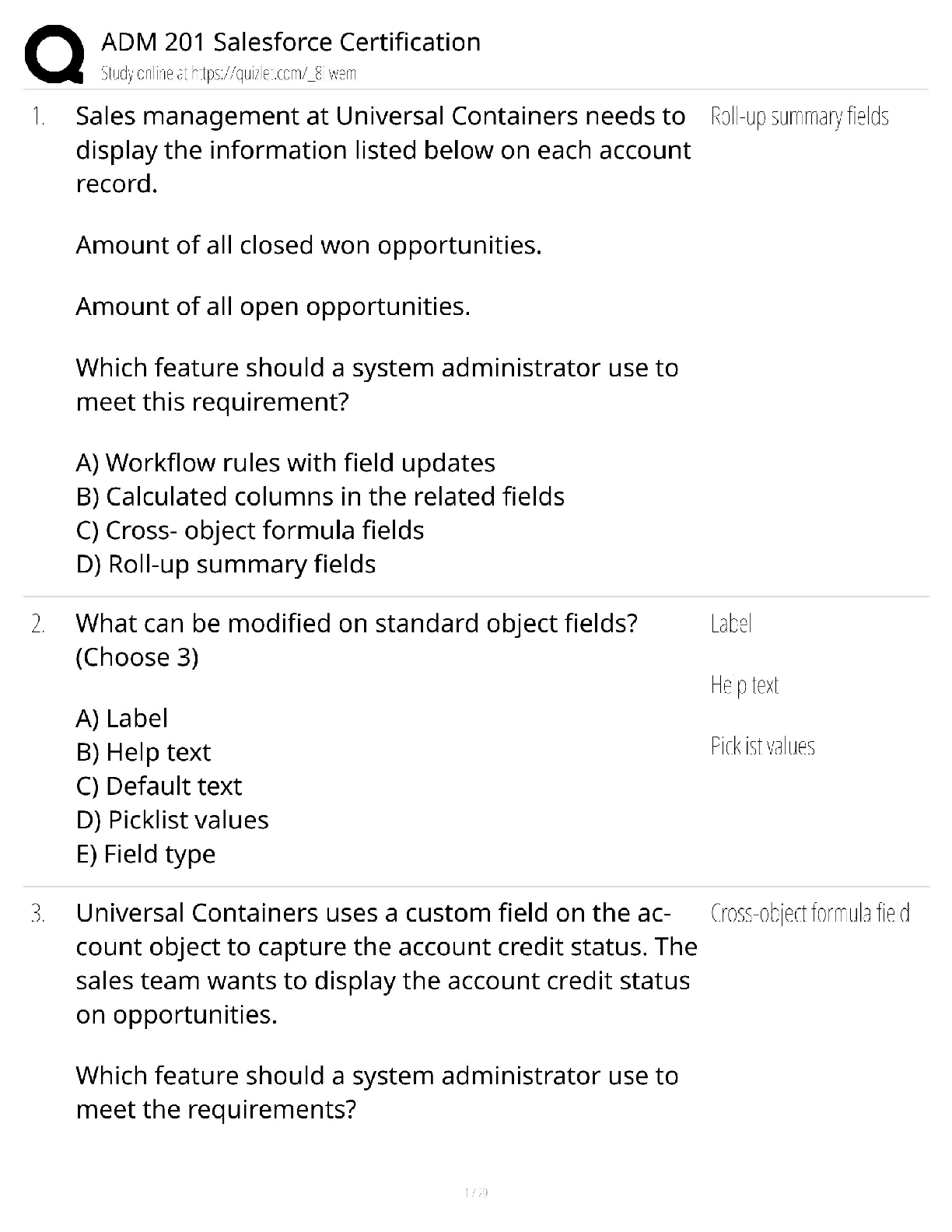
NT2580 Introduction to Information Security Week 3, Unit 3 – Appropriate Access Controls for Systems, Applications and Data Access Assignment Unit 3 Assignment 1: Remote Access Control Policy Def ... inition Learning Objectives and Outcomes You will learn how to design a remote access control policy definition for an IT infrastructure. Assignment Requirements Richman Investments is an investment and consulting firm. The company wants to expand its business operations both in the U.S. and in foreign countries. It intends to eventually have 10,000 employees in 20 countries. The Richman corporate headquarters is located in Phoenix, Arizona. Currently, there are eight branch offices in: Atlanta, Georgia Chicago, Illinois Cincinnati, Ohio Denver, Colorado Los Angeles, California Montreal, Canada New York City, New York Washington, D.C. The North American offices have a total of 5,000 employees who use desktops, mobile computers, and wireless devices. The Phoenix office has an Internet connection to all remote offices because redundancy is extremely important to the company. There are several sensitive applications that all offices use. The management from each office share application information that is hosted at the corporate office. Design a remote access control policy for Richman using the appropriate access controls for systems, applications, and data access. Include the design and justification for using the selected access controls for systems, applications, and data access. Required Resources None Submission Requirements Format: Microsoft Word Font: Times New Roman, Size 12, Double-Space Citation Style: APA 6 v2 Length: 1–2 pages Due By: 11:59 PM 11 October 2013 Self-Assessment Checklist I have correctly designed a remote access control policy for the given scenario. I have correctly selected appropriate access controls for systems, applications, and data access. I have included my justification for using the selected access controls for systems, applications, and data access. [Show More]
Last updated: 3 years ago
Preview 1 out of 4 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$7.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Apr 03, 2021
Number of pages
4
Written in
All
Additional information
This document has been written for:
Uploaded
Apr 03, 2021
Downloads
0
Views
87