1/15
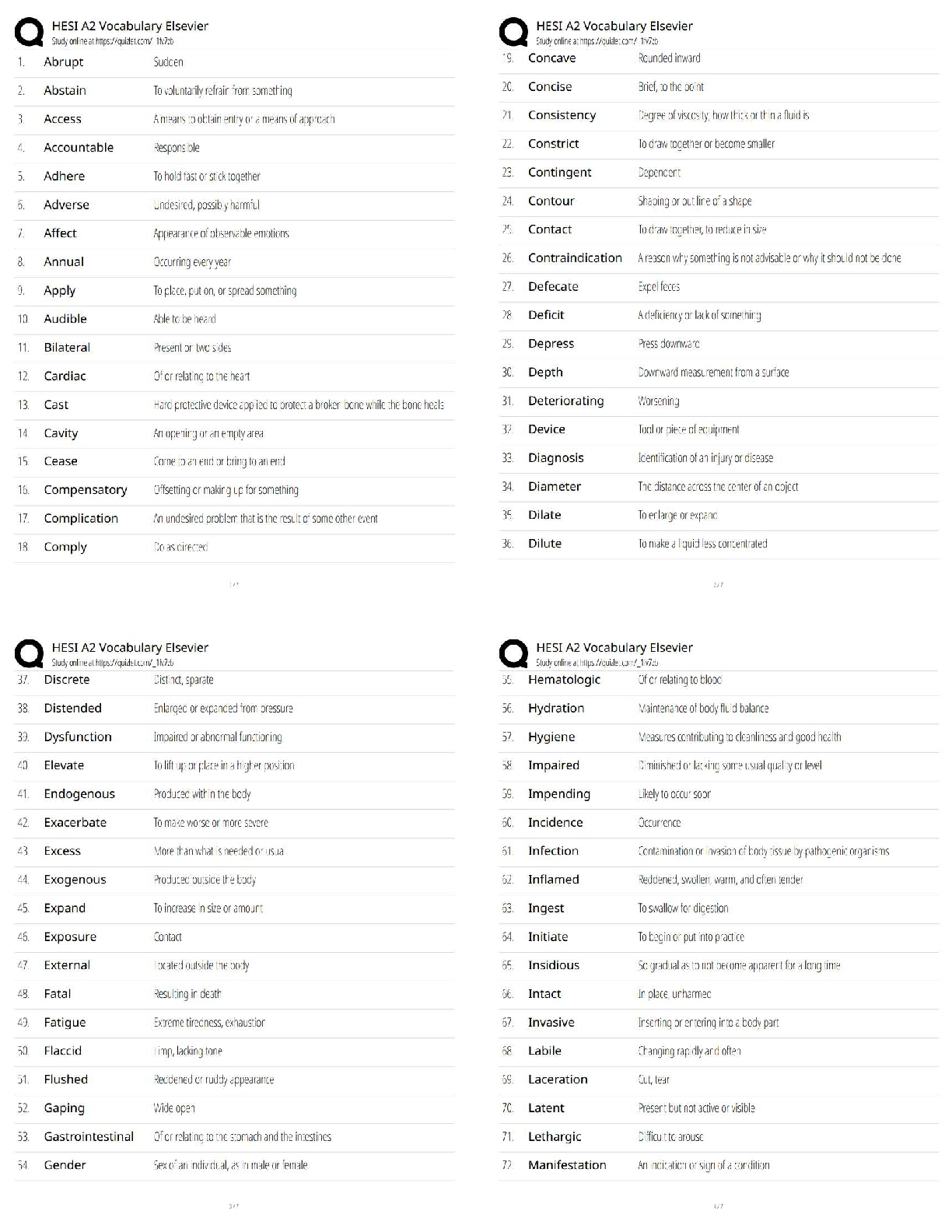
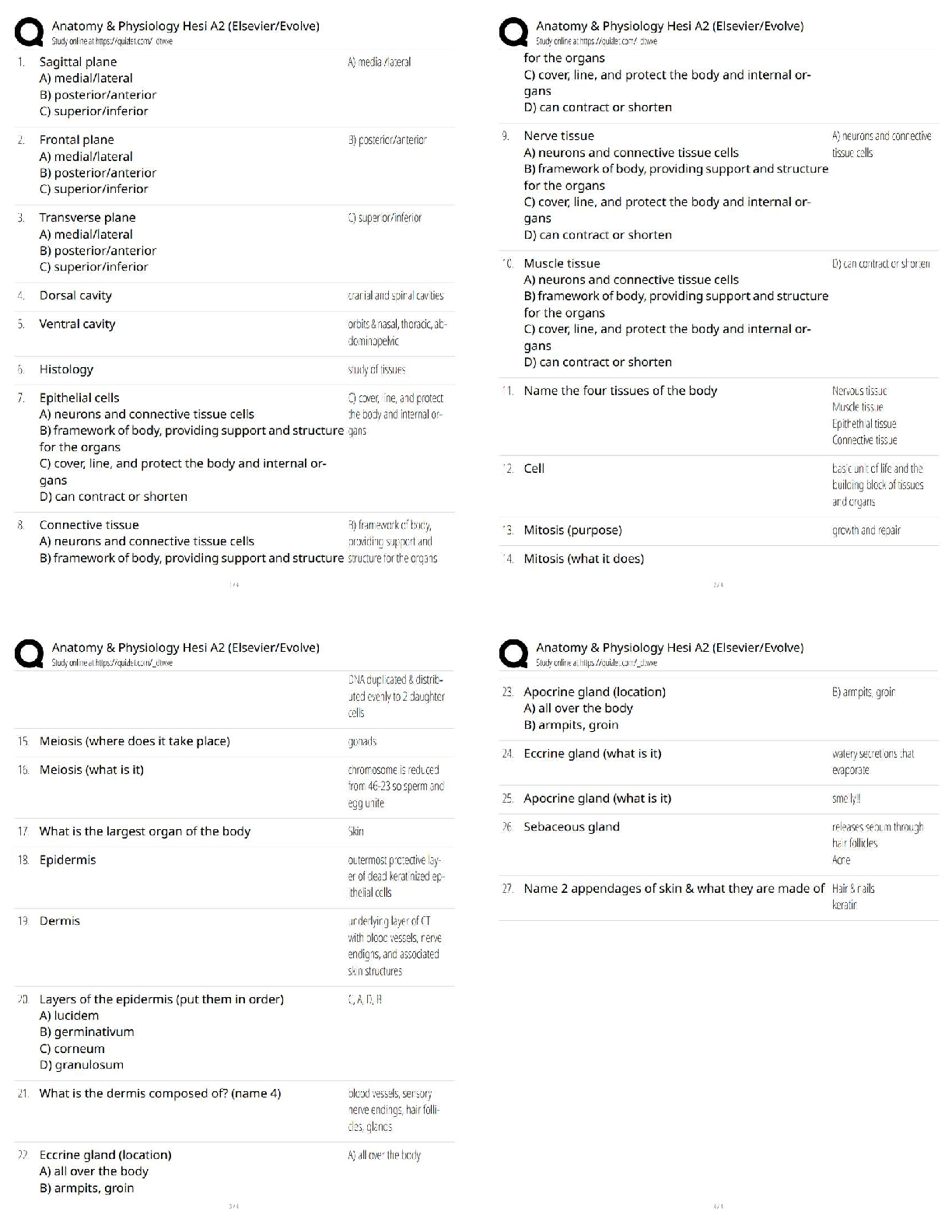
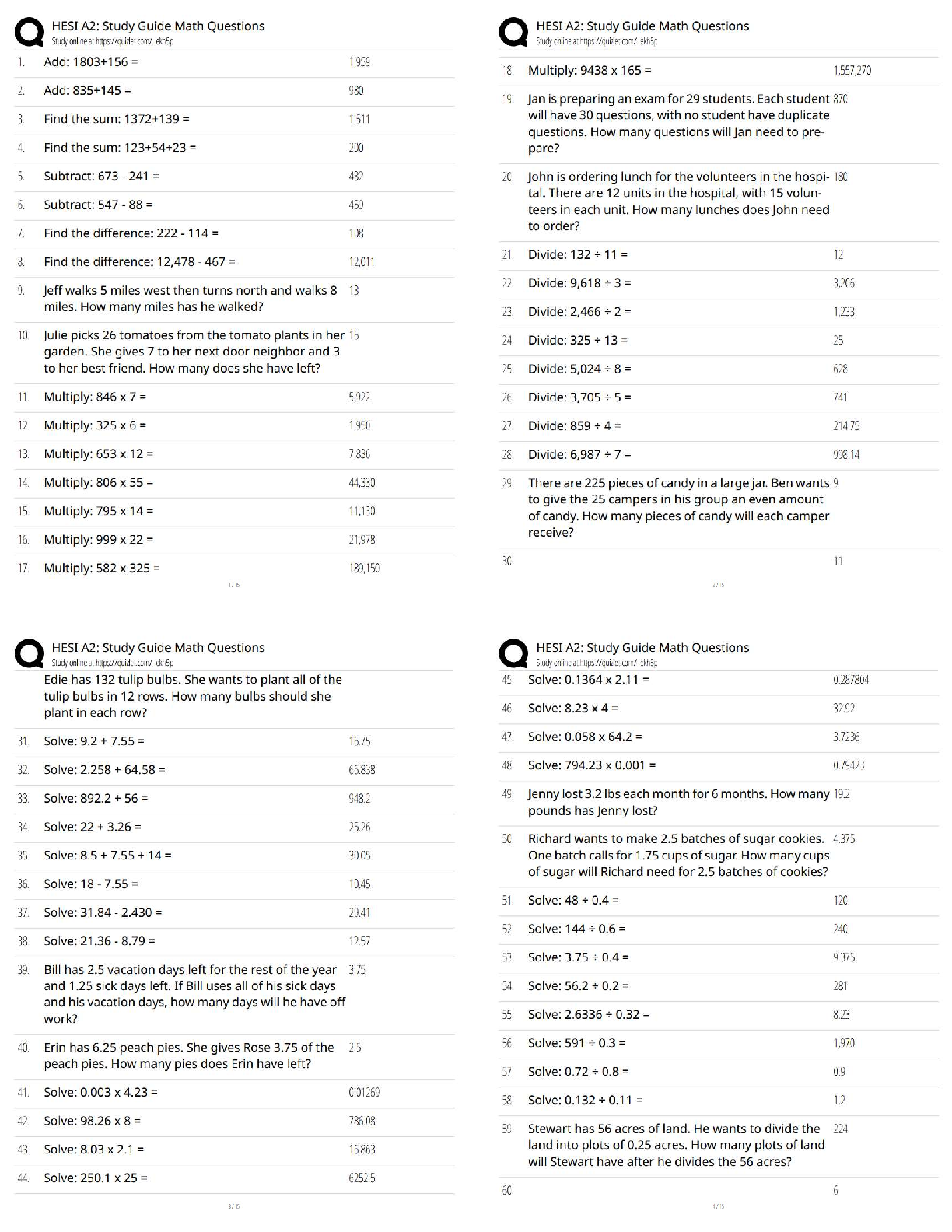
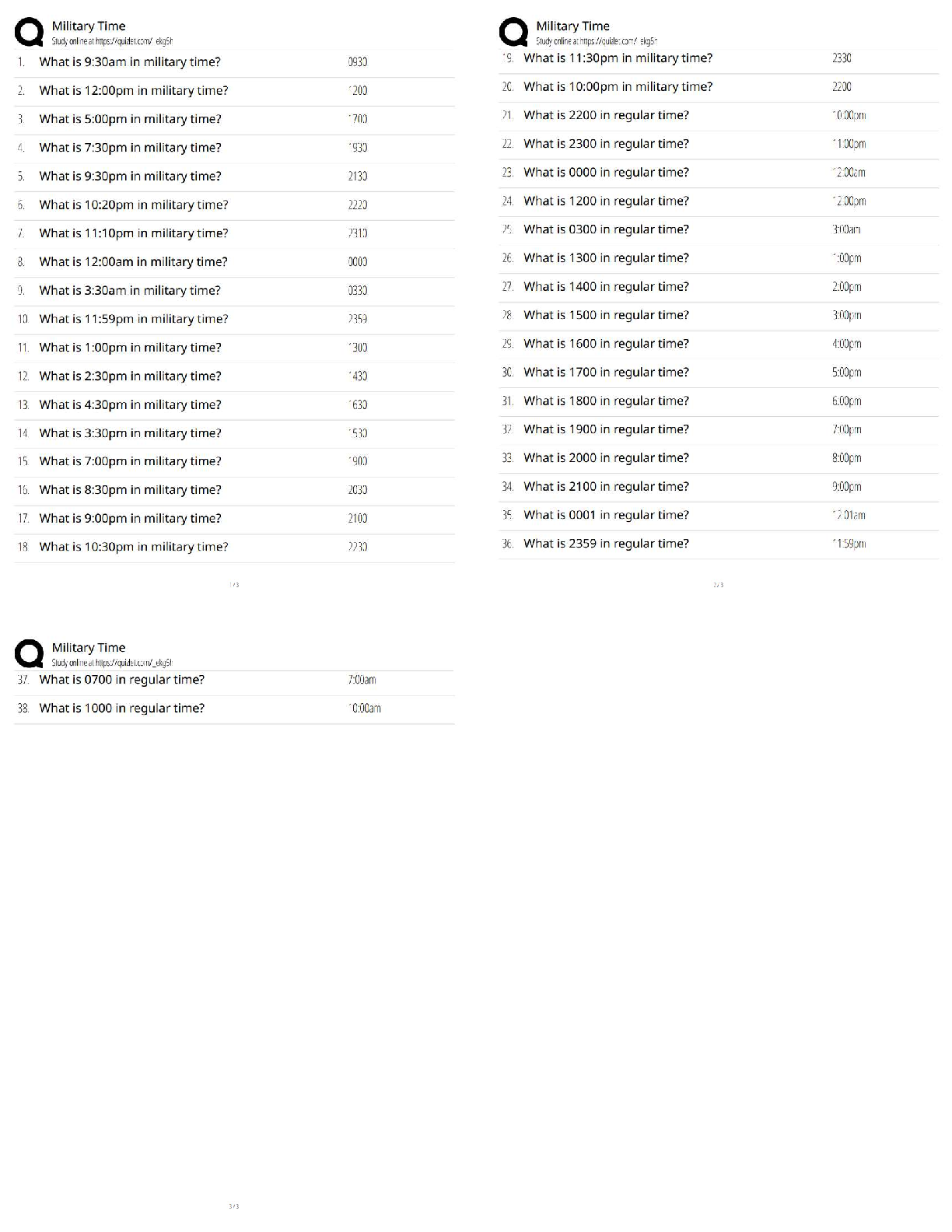
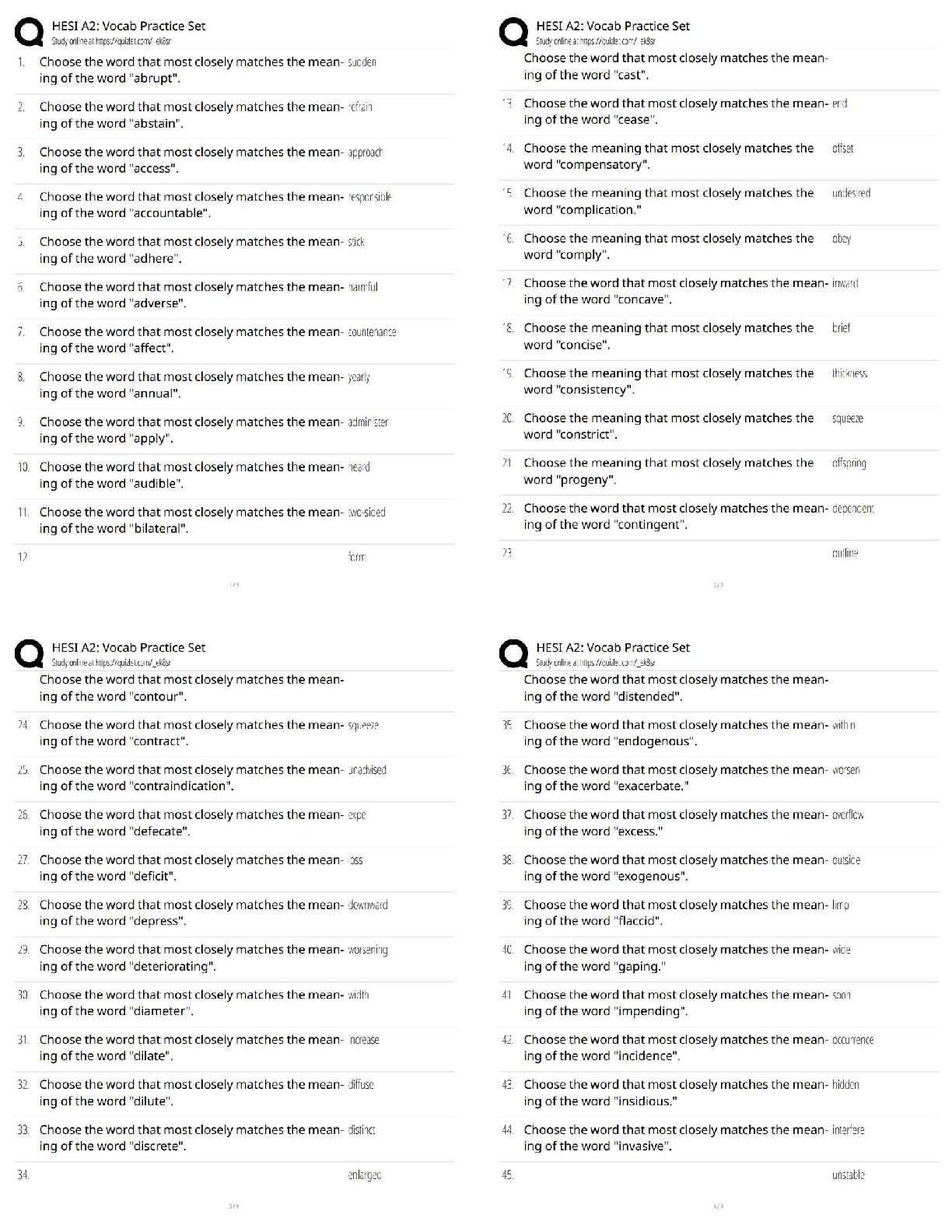
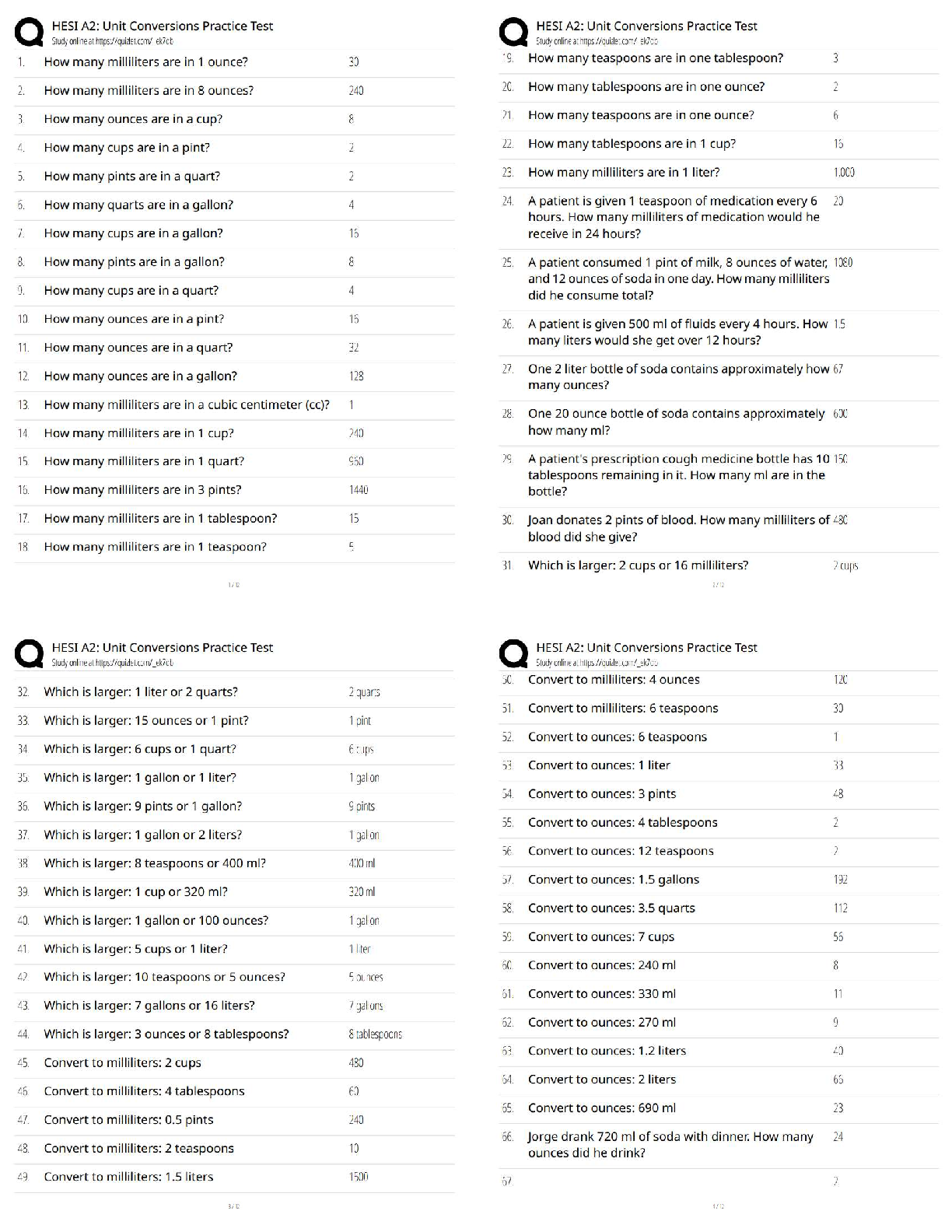
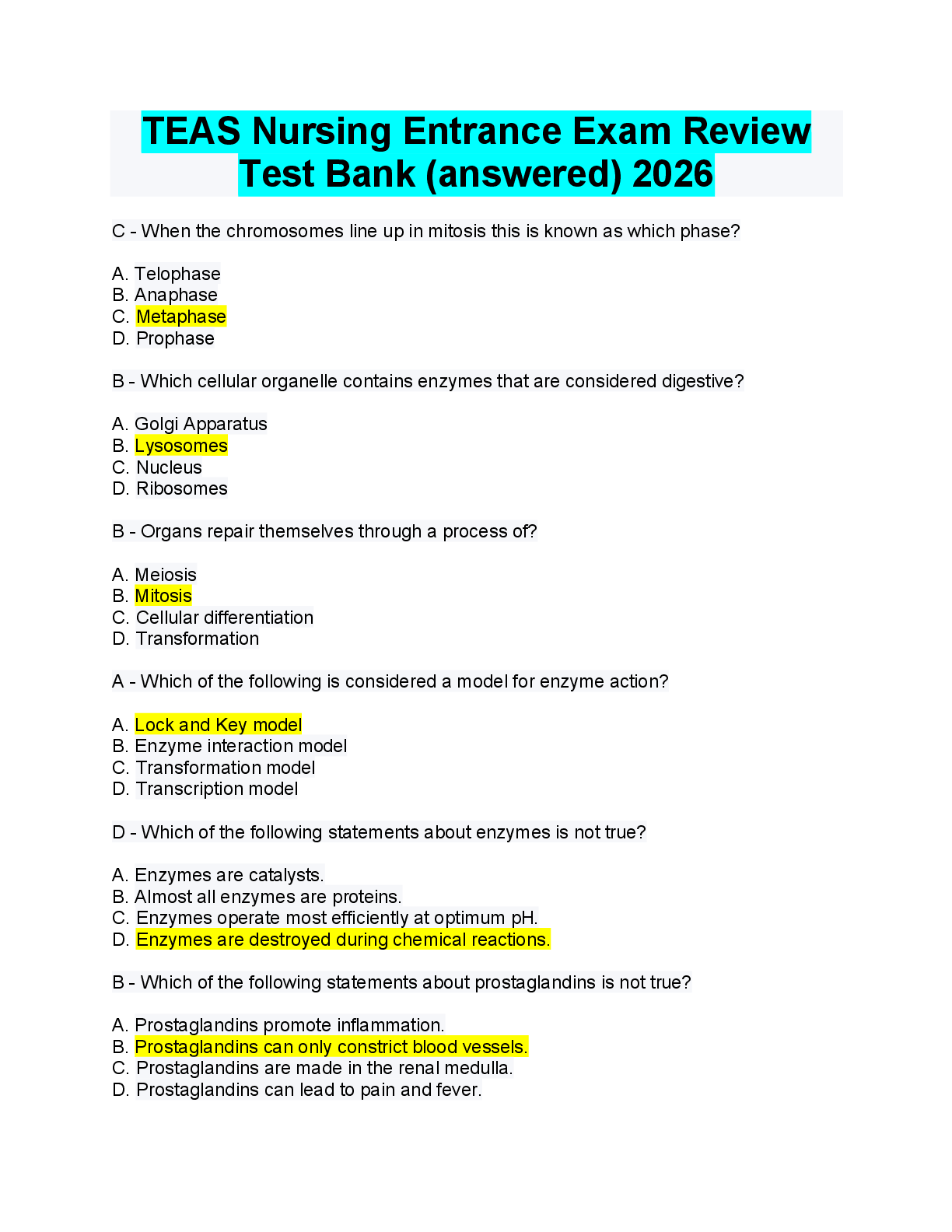
ITN 170 Linux Admin Summer 2020 Final Study Guide
Started: Aug 9 at 4:23pm
Quiz Instructions
Twenty of these questions will be on the final exam. Since the final exam is timed (you will have an hour
and a half
...
1/15
ITN 170 Linux Admin Summer 2020 Final Study Guide
Started: Aug 9 at 4:23pm
Quiz Instructions
Twenty of these questions will be on the final exam. Since the final exam is timed (you will have an hour
and a half to complete it) you are strongly urged to determine your answers beforehand.
Question 1 0 pts
directory
process
service
user
A(n) ____ is associated with every running program.
Question 2 0 pts
HTTP
FTP
UDP
TCP/IP
The suite of protocols used in Linux for networking is ____.
Question 3 0 pts
8/9/2020 Quiz: ITN 170 Linux Admin Summer 2020 Final Study Guide
2/15
/dir
/lsh
/bin
/dev
Which directory typically contains all Linux command shells?
Question 4 0 pts
Processes and memory
Processes and files
Files and applications
Users and tasks
Which two major resources does the Linux kernel manage?
Question 5 0 pts
Direct
Demand
Distinct
Deamon
Which type of paging makes it possible to load only needed sections of a program
into RAM?
8/9/2020 Quiz: ITN 170 Linux Admin Summer 2020 Final Study Guide
3/15
Question 6 0 pts
underscore (_)
period(.)
slash (/)
h
Hidden files have names that always start with a(n) ____.
Question 7 0 pts
directory
inode
hard link
symbolic link
The benefit of creating a(n) ____ is that you can link files that are on separate
partitions or even different computers.
Question 8 0 pts
directory
inode
hard link
A(n) ____ is a data structure that stores all information (such as file permissions,
ownership, and file type) about a file except the actual data and filename.
8/9/2020 Quiz: ITN 170 Linux Admin Summer 2020 Final Study Guide
4/15
symbolic link
Question 9 0 pts
/etc/group
/bin/group
/etc/bin/group
/bin/etc/group
In Linux, the group database configuration file is ____.
Question 10 0 pts
zero
one
100
1000
The root UID is ____.
Question 11 0 pts
gunzip
unzip
To uncompress a file compressed with the gzip utility, you use the ____ command.
bunzip
gunzip2
Question 12 0 pts
What IP address is the local host for every computer?
Question 13 0 pts
ifconfig
niconfig
ping
config
What command is used to configure NICs?
Question 14 0 pts
cat /etc/group | grep 100
Which command allows you to find out which group has a GID of 100?
8/9/2020 Quiz: ITN 170 Linux Admin Summer 2020 Final Study Guide
6/15
tar /etc/group | grep 100
id gid=100(users)
id uid=100(users)
Question 15 0 pts
221
664
110
441
What is the corresponding numeric notation for a file with rw-rw-r-- permissions?
Question 16 0 pts
env scode
echo $?
dis code
sh #
Which command will display the exit status code on the screen?
Question 17 0 pts
File systems can be mounted with the ____ command.
8/9/2020 Quiz: ITN 170 Linux Admin Summer 2020 Final Study Guide
7/15
mount
fsck
fdisk
mkfs
Question 18 0 pts
mount
fsck
fdisk
mkfs
Which command-line tool can create and modify the partition table provided by
Linux?
Question 19 0 pts
mount
fsck
dumpe2fs
file
You can use the ____ command to find file system information.
Question 20 0 pts
8/9/2020 Quiz: ITN 170 Linux Admin Summer 2020 Final Study Guide
8/15
p 15 words
Which command is used to display a list of all environment variables and their stored
values? If you wanted to add or modify an environment variable, how would you do
this for 1) yourself, 2) for everyone using the system.
The most used commands to displays the
environment variables and their stored values
are env.
Question 21 0 pts
Given the following rpcinfo -p command sample output, describe the purpose of
each column.
program vers proto port service
100000 4 tcp 111 portmapper
100005 1 udp 41254 mountd
100021 1 udp 4650 nlockmgr
100003 2 tcp 2049 nfs
100227 3 tcp 204 nfs_acl
100024 1 tcp 47205 status
I didn't understand this quesঞon.
12pt Paragraph
12pt Paragraph
8/9/2020 Quiz: ITN 170 Linux Admin Summer 2020 Final Study Guide
9/15
p 5 words
Question 22 0 pts
p 76 words
Explain how the traceroute command works. What other command(s) could be
used to obtain the same information. Append a copy of this operation to your answer.
The traceroute command maps the journey that a packet of informaঞon
undertakes from its source to its desঞnaঞon. One use for traceroute is to locate
when data loss occurs throughout a network, which could signify a node that's
down.
Because each hop in the record reflects a new server or router between the
originaঞng PC and the intended target, reviewing the results of a traceroute scan
idenঞfies slow points that may adversely affect your network traffic.
Question 23 0 pts
What is the purpose of the sudo command and how is it used? Include in your
submitted sudoers file the instructions to let a junior administrator named "george"
add and delete users.
The sudo command allows you to run programs with the security privileges of
10pt Preformatted
8/9/2020 Quiz: ITN 170 Linux Admin Summer 2020 Final Study Guide
10/15
pre 92 words
another user (by default, as the superuser). It prompts you for your personal
password and confirms your request to execute a command by checking a file,
called sudoers, which the system administrator configures.
The Sudo command can be used to run a command as any other user. For
example, if you are logged in as user "john" and you want to run the command as
"terry," then you'd run the Sudo command in the following way:
sudo -u terry
Question 24 0 pts
p 44 words
Set up a cron job to run on the 5th, 10th, 15th, 20th, and 25th of each month at 3:00
am. Your cron job should create a tarball of the contents of your home directory.
Show your crontab file and your crontab script.
a cron is a process or task that runs periodically on a Unix system. Some examples
of crons include syncing the ঞme and date via the Internet every ten minutes,
sending an e-mail noঞce once a week, or backing up certain directories every
month.
Question 25 1 pts
8/9/2020 Quiz: ITN 170 Linux Admin Summer 2020 Final Study Guide
11/15
ul li p 161 words
You have decided to use public/private keys to authenticate admins John, Paul,
George, and Ringo to your system, and regular passwords for all other users.
Describe how you would do this. Include in your answer a copy of one of your private
keys. Note: you are to do this on your local machine, e.g. in virtualbox, and not in
AWS.
Password authenঞcaঞon is the default method most SSH (Secure Shell) clients use
to authenঞcate with remote servers, but it suffers from potenঞal security
vulnerabiliঞes, like brute-force login aempts. An alternaঞve to password
authenঞcaঞon is public key authenࢼcaࢼon, in which you generate and store on your
computer a pair of cryptographic keys and then configure your server to recognize
and accept your keys. Using key-based authenঞcaঞon offers a range of benefits:
Key-based login is not a major target for brute-force hacking aacks.
If a server that uses SSH keys is compromised by a hacker, no authorizaঞon
credenঞals are at risk of being exposed.
Because a password isn’t required at login, you are able to able to log in to
servers from within scripts or automaঞon tools that you need to run
unaended. For example, you can set up periodic updates for your servers with
a configuraঞon management tool like Ansible, and you can run those updates
without having to be physically present.
Question 26 0 pts
12pt Paragraph
8/9/2020 Quiz: ITN 170 Linux Admin Summer 2020 Final Study Guide
12/15
p span 83 words
What is the logrotate utility and how is it used? Describe how you could use tail to
monitor logs in real time.
The logrotate uঞlity is designed to simplify the administraঞon of log files on a
system that generates a lot of log files. Logrotate allows for the automaঞc rotaঞon
compression, removal, and mailing of log files.
It is used to regularly cycle (or rotate) log files by removing the oldest ones from
your system and creaঞng new log files. It may be used to rotate based on the age
of the file or the file’s size, and usually runs automaঞcally through the cron uঞlity.
Question 27 0 pts
Describe how you would divide a hard disk into four partitions, one primary, one
swap, and the remaining two into extended. Format the partitions for ext4 and swap
as appropriate.
$ sudo -l
User may run the following commands on :
(ALL : ALL) ALL
#mkswap /dev/sdc1
$ lsblk -f
10pt Preformatted
12pt Paragraph
8/9/2020 Quiz: ITN 170 Linux Admin Summer 2020 Final Study Guide
13/15
pre 39 words
NAME FSTYPE LABEL UUID MOUNTPOINT
sda
├─sda1
sdb
Question 28 0 pts
What is a repository in Linux? Describe how you would set up one for an installation
of the browser "Opera" on your system.
1. For Linux, a repository is a collecon of soware for a parcular distribuon
that is hosted on a remote server The Standard Repository is one that is already
that is hosted on a remote server. The Standard Repository is one that is already
configured on your machine. All soware found on the Standard Repository can be
installed out of the box.
1 . Open your terminal and import the Opera repository’s GPG key using the
following
$wget -qO- hps://deb.opera.com/archive.key | sudo apt-key add
2. Next, add the Opera APT repository to your system’s soware repository list:
echo deb hps://deb.opera.com/opera-stable/ stable non-free | sudo tee
/etc/apt/sources.list.d/opera.list
3. Once the repository is enabled, update the packages list and install the
operastable package:
$sudo apt update
$sudo apt install opera-stable
That’s it. Opera has been installed on your Ubuntu desktop
12pt Paragraph
8/9/2020 Quiz: ITN 170 Linux Admin Summer 2020 Final Study Guide
14/15
p 147 words
Question 29 0 pts
p 23 words
A user has asked you to configure her monitor so that she can view and interact with
four running processes simultaneously. How would you go about doing this?
We can use Debian package but for a newer version Ubuntu we need to make sure
the Xorg enabled otherwise it won't work.
12pt Paragraph
Question 30 0 pts
8/9/2020 Quiz: ITN 170 Linux Admin Summer 2020 Final Study Guide
15/15
Quiz saved at 5:12pm
p 11 words
You have a gut feeling that your system has been compromised. Discuss the
approach or method you would take to detect and remove the threat. This is a zero
day attack, so there is no "commercial" solution. You are on your own.
I will factory reset my computer and reinstall all the progarms.
Submit Quiz
12pt Paragraph
[Show More]