.png)
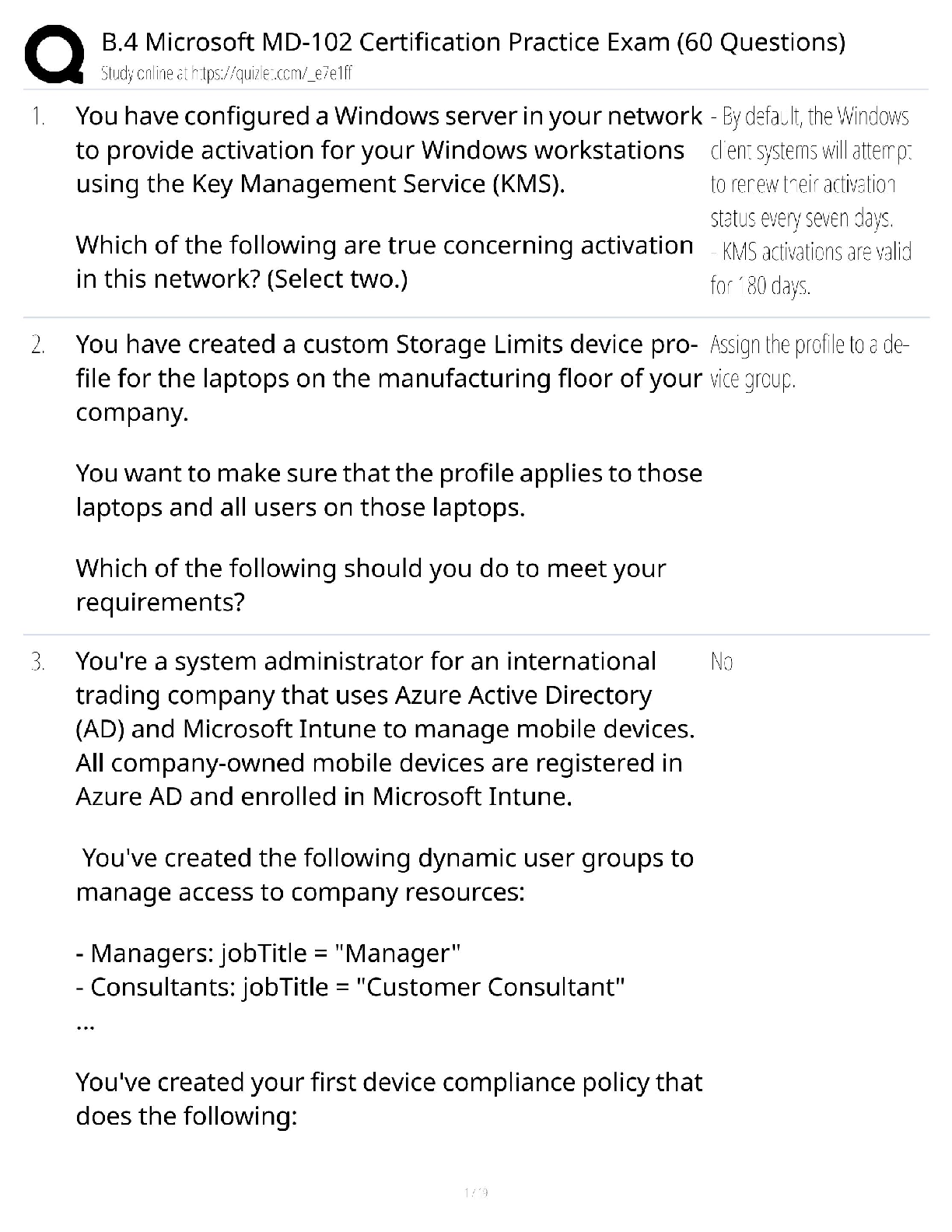
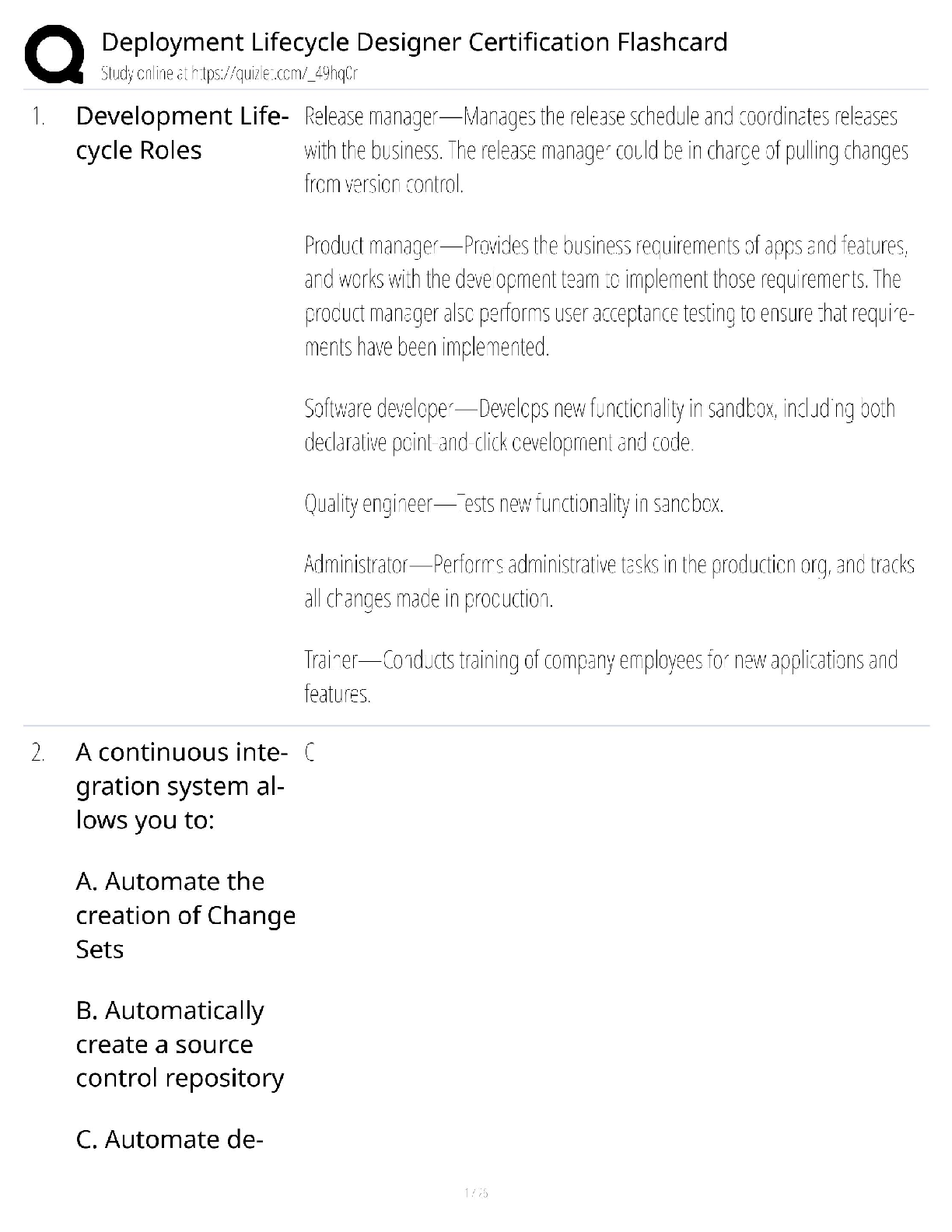
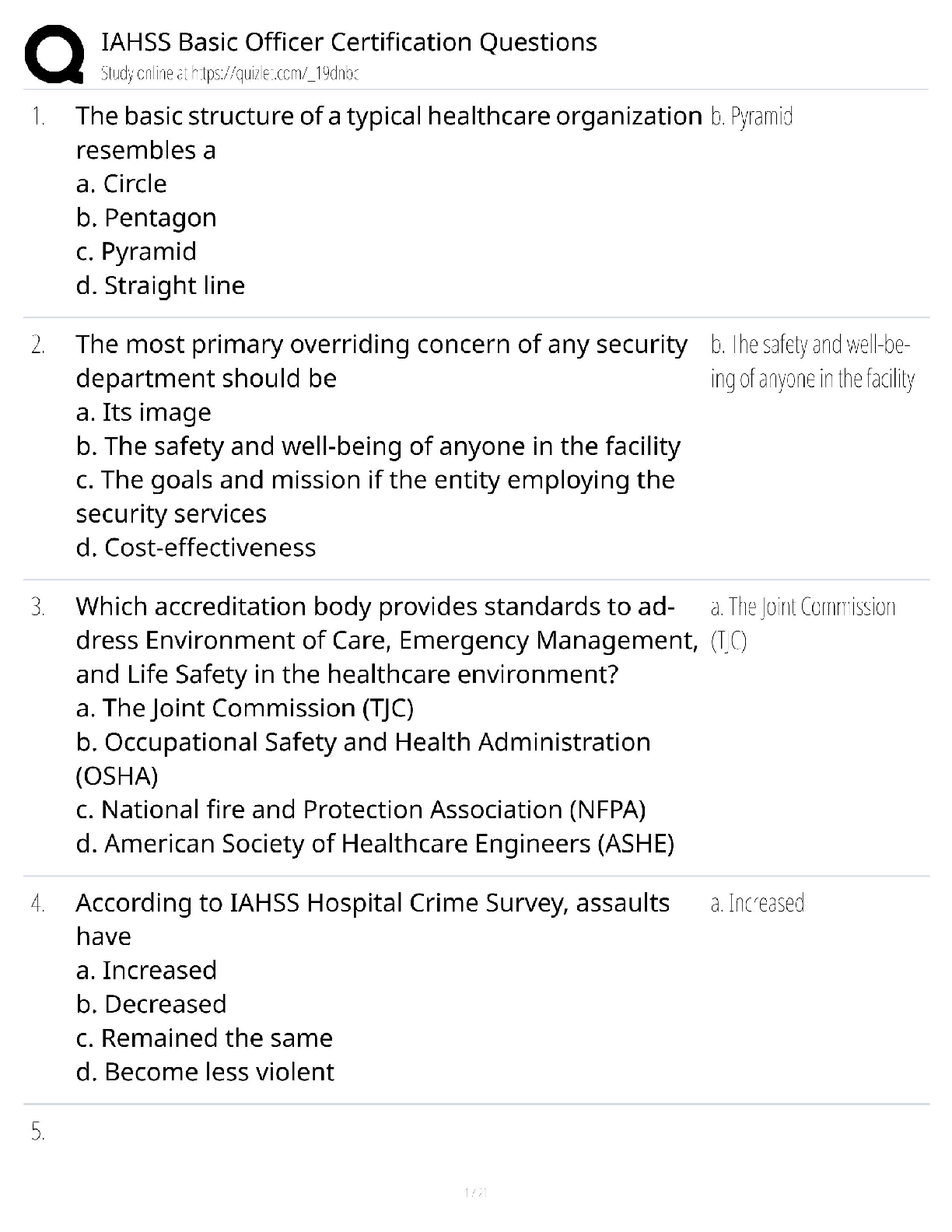
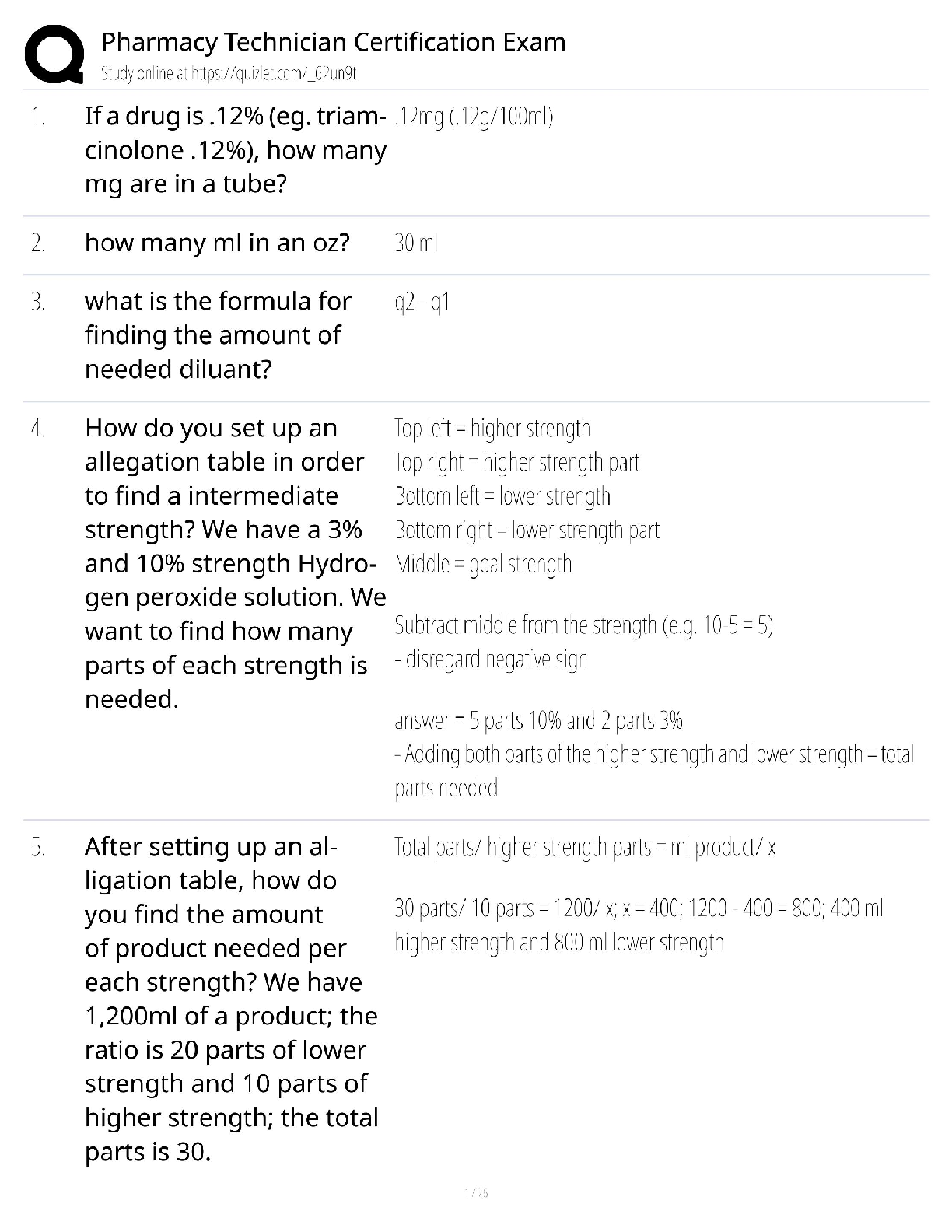
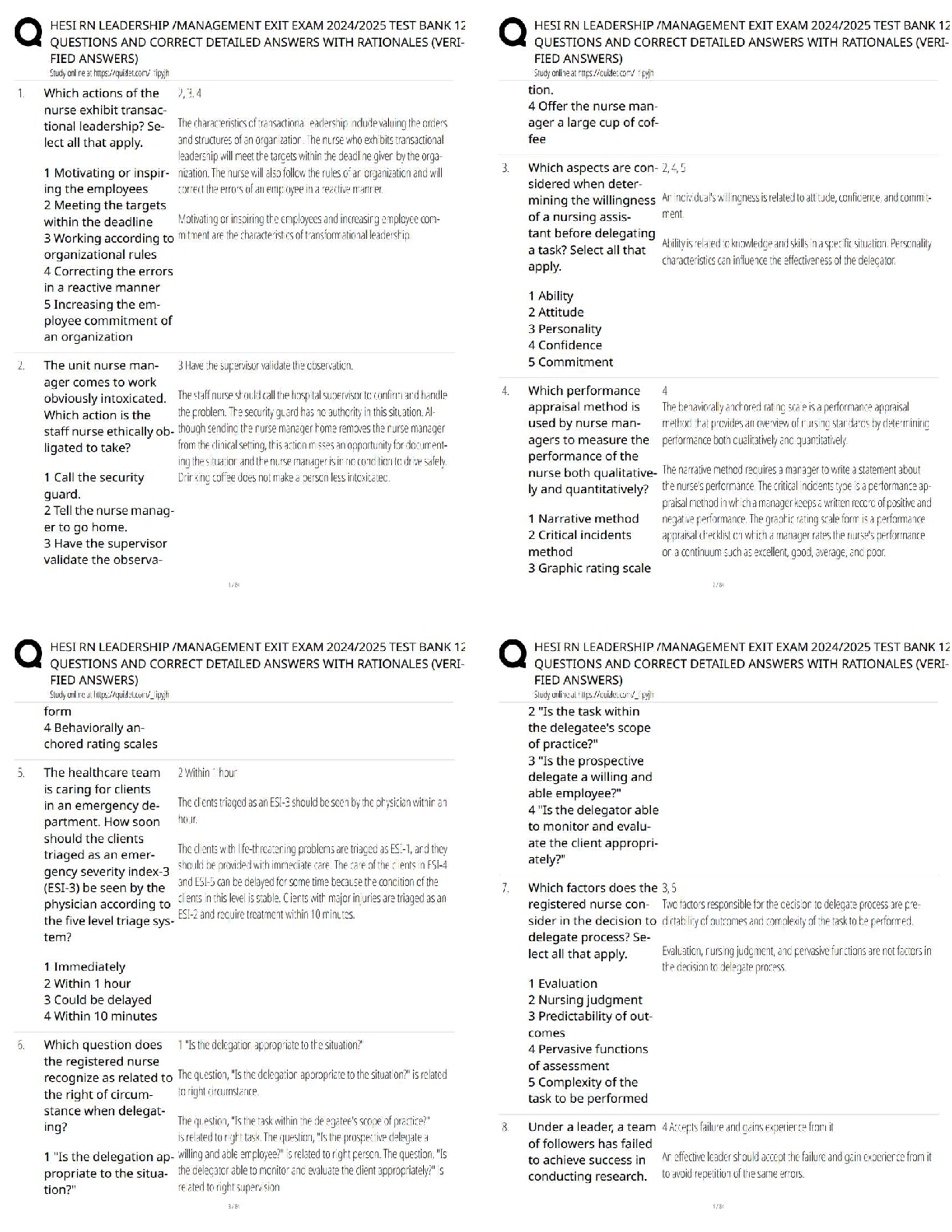
WGU C724 Information Systems Management Unit 8 Test Already Passed
$ 10
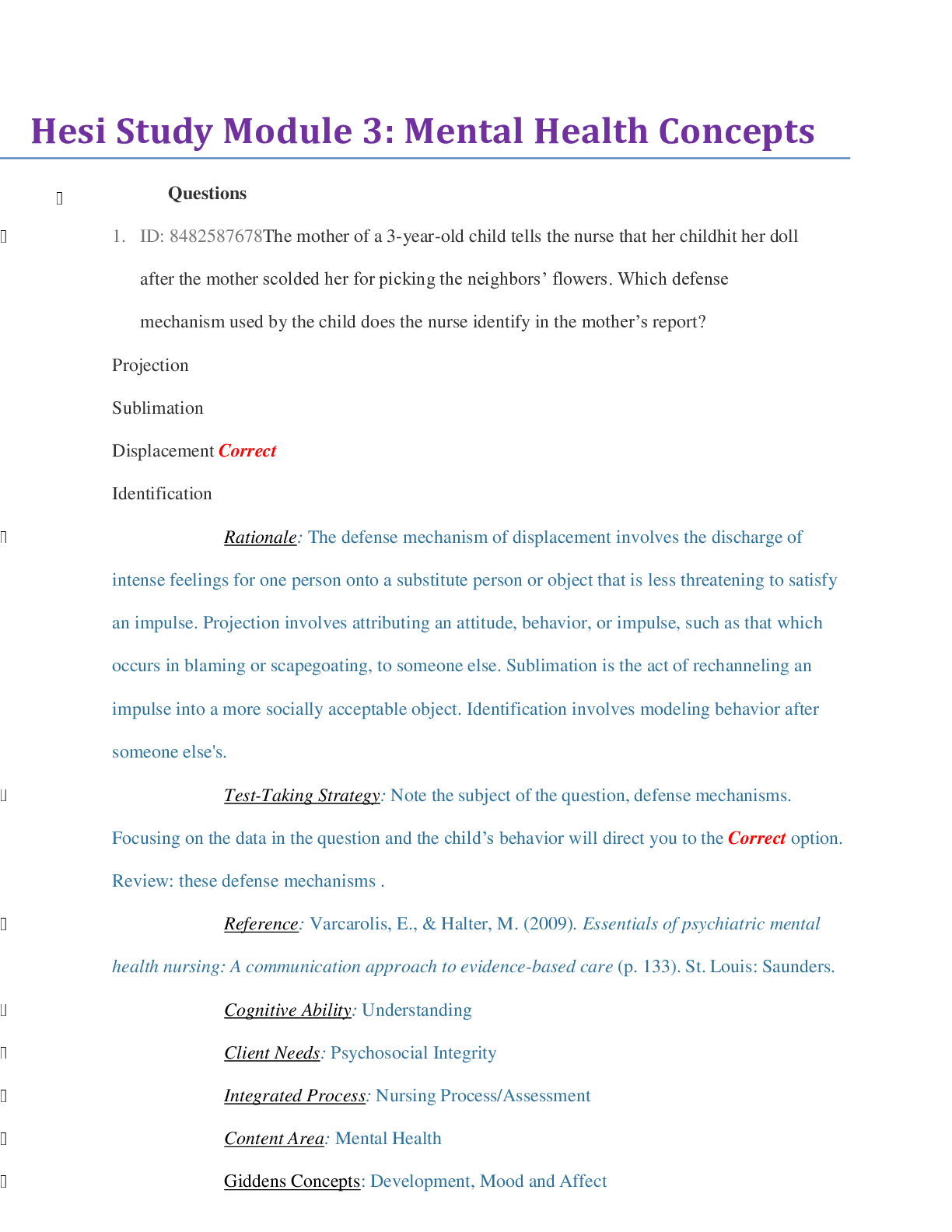
Hesi Study Module 3 _ Mental Health Concepts | Contains 50 QnA with the Rationale, Test taking strategy, Priority, Giddens and HESI Concepts and the References.
$ 11
.png)
EDEXCEL Examiners’ Report Principal Examiner Feedback November 2021/ EDEXCEL Examiners’ Report Principal Examiner Feedback November 2021;'
$ 13.5
NCCT MEDICAL ASSISTANT PRACTICE TEST 4 NEW EXAM SOLUTION
$ 12.5

Numerical Methods for Engineers and Scientists An Introduction with Applications using MATLAB® 3rd Edition by Amos Gilat Vish Subramaniam | eBook [PDF]
$ 16

[eTextbook] [PDF] Computer Science and Education. Educational Digitalization 18th Edition By Wenxing Hong , Geetha Kanaparan
$ 29

Solutions Manual for Abstract Algebra: A First Course (Textbooks in Mathematics) 2nd Edition by Stephen Lovett
$ 19

WALDEN UNIVERSITY NURS 6630: Approaches to Treatments. Case 1 Week 9 Case 1: Volume 1, Case #13: The 8-year-old girl who was naughty �(With Rationale)
$ 15

Business Its Legal, Ethical, and Global Environment: Chapter 6 . All Answers