Computer Networking > TEST BANKS > CIST 1601 - Test Bank Complete study guide; A+ work (latest 2021) Augusta Technical College. (All)
CIST 1601 - Test Bank Complete study guide; A+ work (latest 2021) Augusta Technical College.
Document Content and Description Below
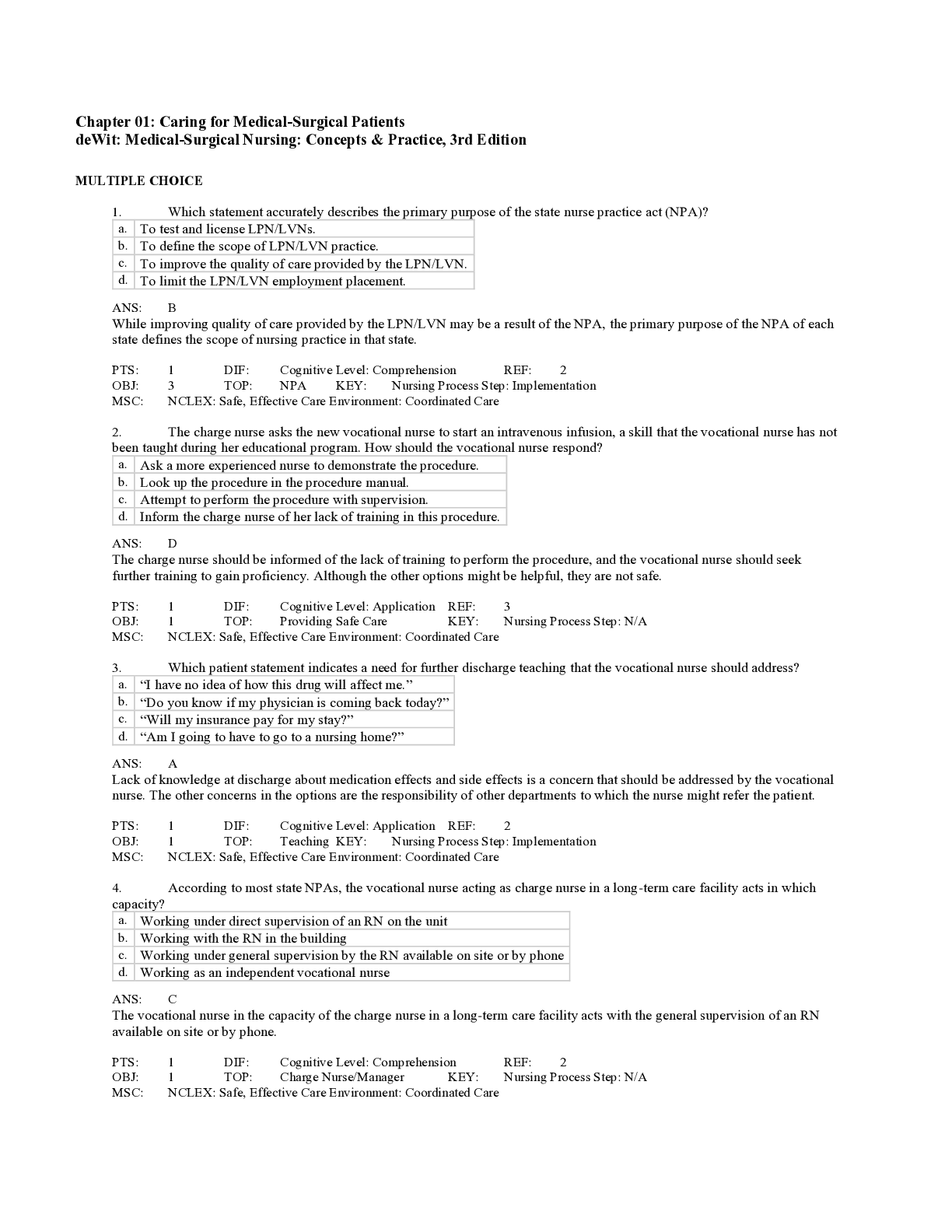
CIST 1601 - Test Bank Complete study guide; A work CIST 1601 Test Bank. CompTIA Security SYO-301 Certification Exam A 1. Actively monitoring data streams in search of malicious code or behavior is an ... example of: a. load balancing. b. an Internet proxy. c. URL filtering. d. content inspection. 2. Which of the following network devices would MOST likely be used to detect but not react to suspicious behavior on the network? a. Firewall b. NIDS c. NIPS d. HIDS 3. The security administrator is getting reports from users that they are accessing certain websites and are unable to download anything off of those sites. The security administrator is also receiving several alarms from the IDS about suspicious traffic on the network. Which of the following is the MOST likely cause? a. NIPS is blocking activities from those specific websites. b. NIDS is blocking activities from those specific websites. c. The firewall is blocking web activity. d. The router is denying all traffic from those sites. 4. Which of the following tools provides the ability to determine if an application is transmitting a password in clear-text? a. Protocol analyzer b. Port scanner c. Vulnerability scanner d. Honeypot 5. Which of the following can a security administrator implement to help identify smurf attacks? a. Load balancer b. Spam filters c. NIDS d. Firewall 6. Which of the following functions is MOST likely performed by a web security gateway? a. Protocol analyzer b. Content filtering c. Spam filtering d. Flood guard 7. Which of the following devices is often used to cache and filter content? a. Proxies b. Firewall c. VPN d. Load balancer 8. Which of the following devices is used to optimize and distribute data workloads across multiple computers or networks? a. Load balancer b. URL filter c. VPN concentrator d. Protocol analyzer 9. An IT administrator wants to provide 250 staff with secure remote access to the corporate network. Which of the following BEST achieves this requirement? a. Software based firewall b. Mandatory Access Control (MAC) c. VPN concentrator d. Web security gateway 10. Which of the following should be installed to prevent employees from receiving unsolicited emails? a. Pop-up blockers b. Virus definitions c. Spyware definitions d. Spam filters 11. Which of the following should a security administrator implement to prevent users from disrupting network connectivity, if a user connects both ends of a network cable to different switch ports? a. VLAN separation b. Access control c. Loop protection d. DMZ 12. A user is no longer able to transfer files to the FTP server. The security administrator has verified the ports are open on the network firewall. Which of the following should the security administrator check? a. Anti-virus software b. ACLs c. Anti-spam software d. NIDS 13. Which of the following BEST describes the proper method and reason to implement port security? a. Apply a security control which ties specific ports to end-device MAC addresses and prevents additional devices from being connected to the network. b. Apply a security control which ties specific networks to end-device IP addresses and prevents new devices from being connected to the network. c. Apply a security control which ties specific ports to end-device MAC addresses and prevents all devices from being connected to the network. d. Apply a security control which ties specific ports to end-device IP addresses and prevents mobile devices from being connected to the network. 14. Which of the following would need to be configured correctly to allow remote access to the network? a. ACLs b. Kerberos c. Tokens d. Biometrics 15. By default, which of the following stops network traffic when the traffic is not identified in the firewall ruleset? a. Access control lists b. Explicit allow c. Explicit deny d. Implicit deny 16. Based on logs from file servers, remote access systems, and IDS, a malicious insider was stealing data using a personal laptop while connected by VPN. The affected company wants access to the laptop to determine lossut the insider's lawyer insists the laptop cannot be identified. Which of the following would BEST be used to identify the specific computer used by the insider? a. IP address b. User profiles c. MAC address d. Computer name 17. Applying detailed instructions to manage the flow of network traffic at the edge of the network, including allowing or denying traffic based on port, protocol, address, or direction is an implementation of which of the following? a. Virtualization b. Port security c. IPSec d. Firewall rules 18. Which of the following is the default rule found in a corporate firewall's access control list? a. Anti-spoofing b. Permit all c. Multicast list d. Deny all 19. Which of the following is BEST used to prevent ARP poisoning attacks across a network? a. VLAN segregation b. IPSec c. IP filters d. Log analysis 20. A small company needs to invest in a new expensive database. The company's budget does not include the purchase of additional servers or personnel. Which of the following solutions would allow the small company to save money on hiring additional personnel and minimize the footprint in their current datacenter? a. Allow users to telecommute b. Setup a load balancer c. Infrastructure as a Service d. Software as a Service 21. Which of the following is MOST likely to be the last rule contained on any firewall? a. IP allow any any b. Implicit deny c. Separation of duties d. Time of day restrictions 22. Which of the following cloud computing concepts is BEST described as providing an easy-to- configure OS and on-demand computing for customers? a. Platform as a Service b. Software as a Service c. Infrastructure as a Service d. Trusted OS as a Service 23. MAC filtering is a form of which of the following? a. Virtualization b. Network Access Control c. Virtual Private Networking d. Network Address Translation 24. Reviewing an access control list on a firewall reveals a Drop All statement at the end of the rules. Which of the following describes this form of access control? a. Discretionary b. Time of day restrictions c. Implicit deny d. Mandatory 25. An administrator is taking an image of a server and converting it to a virtual instance. Which of the following BEST describes the information security requirements of a virtualized server? a. Virtual servers require OS hardening but not patching or antivirus. b. Virtual servers have the same information security requirements as physical servers. c. Virtual servers inherit information security controls from the hypervisor. d. Virtual servers only require data security controls and do not require licenses. 26. Webmail is classified under which of the following cloud-based technologies? a. Demand Computing b. Infrastructure as a Service (IaaS) c. Software as a Service (SaaS) d. Platform as a Service (PaaS) 27. A security engineer is troubleshooting a server in the DMZ, which cannot be reached from the Internet or the internal network. All other servers on the DMZ are able to communicate with this server. Which of the following is the MOST likely cause? a. The server is configured to reject ICMP packets. b. The server is on the external zone and it is configured for DNS only. c. The server is missing the default gateway. d. The server is on the internal zone and it is configured for DHCP only. 28. Which of the following may cause a useronnected to a NAC-enabled network, to not be prompted for credentials? a. The user's PC is missing the authentication agent. b. The user's PC is not fully patched. c. The user's PC is not at the latest service pack. d. The user's PC has out-of-date antivirus software. 29. Which of the following would be implemented to allow access to services while segmenting access to the internal network? a. IPSec b. VPN c. NAT d. DMZ 30. A security administrator needs to separate two departments. Which of the following would the administrator implement to perform this? a. Cloud computing b. VLAN c. Load balancer d. MAC filtering 31. Which of the following is a security control that is lost when using cloud computing? a. Logical control of the data b. Access to the application's administrative settings c. Administrative access to the data d. Physical control of the data 32. Which of the following protocols should be blocked at the network perimeter to prevent host enumeration by sweep devices? a. HTTPS b. SSH c. IPv4 d. ICMP 33. Which of the following uses TCP port 22 by default? a. SSL, SCP, and TFTP b. SSH, SCP, and SFTP c. HTTPS, SFTP, and TFTP d. TLS, TELNET, and SCP 34. Which of the following allows a security administrator to set device traps? a. SNMP b. TLS c. ICMP d. SSH 35. A security administrator needs to implement a site-to-site VPN tunnel between the main office and a remote branch. Which of the following protocols should be used for the tunnel? a. RTP b. SNMP c. IPSec d. 802.1X 36. Which of the following protocols would be the MOST secure method to transfer files from a host machine? a. SFTP b. WEP c. TFTP d. FTP 37. Which of the following port numbers is used for SCPy default? a. 22 b. 69 c. 80 d. 443 38. Which of the following is the MOST secure method of utilizing FTP? a. FTP active b. FTP passive c. SCP d. FTPS 39. Which of the following protocols can be implemented to monitor network devices? a. IPSec b. FTPS c. SFTP d. SNMP 40. Which of the following protocols would an administrator MOST likely use to monitor the parameters of network devices? a. SNMP b. NetBIOS c. ICMP d. SMTP 41. A remote office is reporting they are unable to access any of the network resources from the main office. The security administrator realizes the error and corrects it. The administrator then tries to ping the router at the remote office and receives no reply; however, the technician is able to telnet to that router. Which of the following is the MOST likely cause of the security administrator being unable to ping the router? a. The remote switch is turned off. b. The remote router has ICMP blocked. c. The remote router has IPSec blocked. d. The main office's router has ICMP blocked. 42. A network administrator is implementing a network addressing scheme that uses a long string of both numbers and alphanumeric characters to create addressing options and avoid duplicates. Which of the following describes a protocol built for this purpose? a. IPv6 b. ICMP c. IGMP d. IPv4 43. In which of the following locations would a forensic analyst look to find a hooked process? a. BIOS b. Slack space c. RAM d. Rootkit 44. Which of the following file transfer protocols is an extension of SSH? a. FTP b. TFTP c. SFTP d. FTPS 45. Which of the following secure protocols is MOST commonly used to remotely administer Unix/Linux systems? a. SSH b. SCP c. SFTP d. SNMP 46. The security administrator notices a number of TCP connections from the development department to the test network segregation. Large volumes of data are being transmitted between the two networks only on port 22. Which of the following is MOST likely occurring? a. The development team is transferring data to test systems using FTP and TFTP. b. The development team is transferring data to test systems using SCP and TELNET. c. The development team is transferring data to test systems using SFTP and SCP. d. The development team is transferring data to test systems using SSL and SFTP. 47. An administrator who wishes to block all database ports at the firewall should include which of the following ports in the block list? a. 445 b. 1433 c. 1501 d. 3389 48. If a security administrator wants to TELNET into a router to make configuration changes, which of the following ports would need to be open by default? a. 23 b. 135 c. 161 d. 3389 49. Which of the following wireless security controls can be easily and quickly circumvented using only a network sniffer? (Select TWO). a. MAC filtering b. Disabled SSID broadcast c. WPA2-Enterprise d. EAP-TLS e. WEP with 802.1x 50. In order to provide flexible working conditions, a company has decided to allow some employees remote access into corporate headquarters. Which of the following security technologies could be used to provide remote access? (Select TWO). a. Subnetting b. NAT c. Firewall d. NAC e. VPN Exam B 1. Which of the following ports would a security administrator block if the administrator wanted to stop users from accessing outside SMTP services? a. 21 b. 25 c. 110 d. 143 PTS: 1 2. A network consists of various remote sites that connect back to two main locations. The security administrator needs to block TELNET access into the network. Which of the followingy default, would be the BEST choice to accomplish this goal? a. Block port 23 on the L2 switch at each remote site. b. Block port 23 on the network firewall. c. Block port 25 on the L2 switch at each remote site. d. Block port 25 on the network firewall. PTS: 1 3. In an 802.11n network, which of the following provides the MOST secure method of both encryption and authorization? a. WEP with 802.1x b. WPA Enterprise c. WPA2-PSK d. WPA with TKIP PTS: 1 4. Isolation mode on an AP provides which of the following functionality types? a. Segmentation of each wireless user from other wireless users. b. Disallows all users from communicating directly with the AP. c. Hides the service set identifier. d. Makes the router invisible to other routers. PTS: 1 5. Which of the following is the BEST choice for encryption on a wireless network? a. WPA2-PSK b. AES c. WPA d. WEP PTS: 1 6. A user reports that their 802.11n capable interface connects and disconnects frequently to an access point that was recently installed. The user has a Bluetooth enabled laptop. A company in the next building had their wireless network breached last month. Which of the following is MOST likely causing the disconnections? a. An attacker inside the company is performing a bluejacking attack on the user's laptop. b. Another user's Bluetooth device is causing interference with the Bluetooth on the laptop. c. The new access point was mis-configured and is interfering with another nearby access point. d. The attacker that breached the nearby company is in the parking lot implementing a war driving attack. PTS: 1 7. Which of the following should the security administrator look at FIRST when implementing an AP to gain more coverage? a. Encryption methods b. Power levels c. SSID d. Radio frequency PTS: 1 8. Which of the following protocols requires the use of a CA based authentication process? a. FTPS implicit b. FTPS explicit c. MD5 d. PEAP-TLS PTS: 1 9. When configuring multiple computers for RDP on the same wireless router, it may be necessary to do which of the following? a. Forward to different RDP listening ports. b. Turn off port forwarding for each computer. c. Enable DMZ for each computer. d. Enable AP isolation on the router. PTS: 1 10. A technician needs to limit the wireless signal from reaching outside of a building. Which of the following actions should the technician take? a. Disable the SSID broadcast on the WAP. b. Place the WAP antenna on the exterior wall of the building. c. Decrease the power levels on the WAP. d. Enable MAC filtering in the WAP. PTS: 1 11. Which of the following will provide the HIGHEST level of wireless network security? a. WPA2 b. SSH c. SSID d. WEP PTS: 1 12. Which of the following facilitates computing for heavily utilized systems and networks? a. Remote access b. Provider cloud c. VPN concentrator d. Telephony PTS: 1 13. Risk can be managed in the following ways EXCEPT: a. mitigation. b. acceptance. c. elimination. d. transference. PTS: 1 14. A company that purchases insurance to reduce risk is an example of which of the following? a. Risk deterrence b. Risk acceptance c. Risk avoidance d. Risk transference PTS: 1 15. Which of the following is a best practice to identify fraud from an employee in a sensitive position? a. Acceptable usage policy b. Separation of duties c. False positives d. Mandatory vacations PTS: 1 16. A security administrator with full administrative rights on the network is forced to temporarily take time off of their duties. Which of the following describes this form of access control? a. Separation of duties b. Discretionary c. Mandatory vacation d. Least privilege PTS: 1 17. Instead of giving a security administrator full administrative rights on the network, the administrator is given rights only to review logs and update security related network devices. Additional rights are handed out to network administrators for the areas that fall within their job description. Which of the following describes this form of access control? a. Mandatory vacation b. Least privilege c. Discretionary d. Job rotation PTS: 1 18. A security administrator wants to determine what data is allowed to be collected from users of the corporate Internet-facing web application. Which of the following should be referenced? a. Privacy policy b. Human Resources policy c. Appropriate use policy d. Security policy PTS: 1 19. An administrator is updating firmware on routers throughout the company. Where should the administrator document this work? a. Event Viewer b. Router's System Log c. Change Management System d. Compliance Review System PTS: 1 20. Due to sensitive data concerns, a security administrator has enacted a policy preventing the use of flash drives. Additionally, which of the following can the administrator implement to reduce the risk of data leakage? a. Enact a policy that all work files are to be password protected. b. Enact a policy banning users from bringing in personal music devices. c. Provide users with unencrypted storage devices that remain on-site. d. Disallow users from saving data to any network share. PTS: 1 21. Performing routine security audits is a form of which of the following controls? a. Preventive b. Detective c. Protective d. Proactive PTS: 1 22. Which of the following is MOST commonly a part of routine system audits? a. Job rotation b. Business impact analysis c. User rights and permissions reviews d. Penetration testing PTS: 1 23. Which of the following is a method to prevent ad-hoc configuration mistakes? a. Implement an auditing strategy b. Implement an incident management strategy c. Implement a patch management strategy d. Implement a change management strategy PTS: 1 24. Which of the following should be reviewed periodically to ensure a server maintains the correct security configuration? a. NIDS configuration b. Firewall logs c. User rights d. Incident management PTS: 1 25. A security administrator finished taking a forensic image of a computer's memory. Which of the following should the administrator do to ensure image integrity? a. Run the image through AES128. b. Run the image through a symmetric encryption algorithm. c. Compress the image to a password protected archive. d. Run the image through SHA256. PTS: 1 26. Which of the following BEST explains the security benefit of a standardized server image? a. All current security updates for the operating system will have already been applied. b. Mandated security configurations have been made to the operating system. [Show More]
Last updated: 2 years ago
Preview 1 out of 124 pages
Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$16.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Jun 05, 2021
Number of pages
124
Written in
Additional information
This document has been written for:
Uploaded
Jun 05, 2021
Downloads
0
Views
125