ICT378 Sample Exam Questions
Hot topics for long answer questions:
COC(chain of custody) ,
Chain of Custody refers to the logical sequence that records the sequence of custody,
control, transfer, analysis and disposi
...
ICT378 Sample Exam Questions
Hot topics for long answer questions:
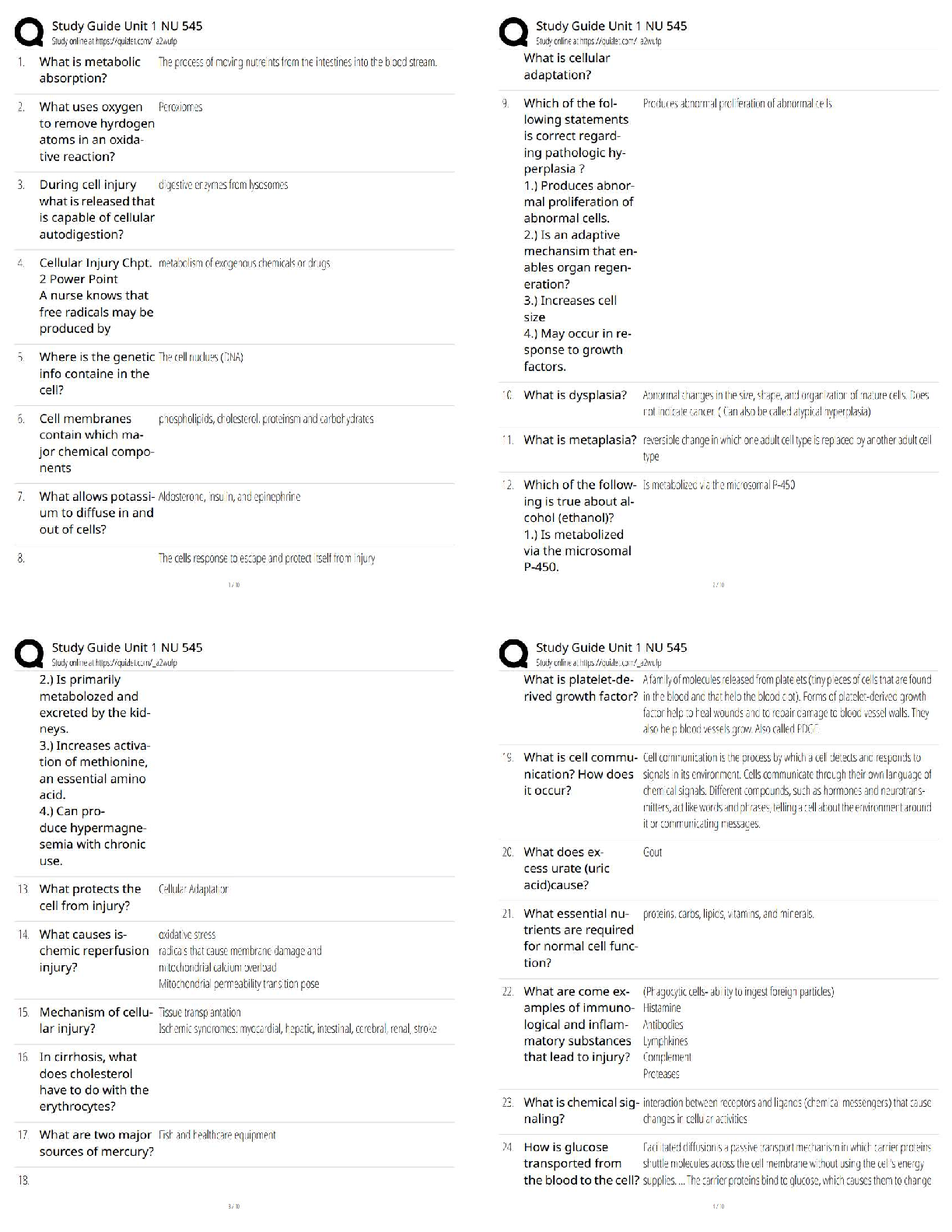
COC(chain of custody) ,
Chain of Custody refers to the logical sequence that records the sequence of custody,
control, transfer, analysis and disposition of physical or electronic evidence in legal cases.
Each step in the chain is essential as if broke, the evidence may be rendered inadmissible.
Thus we can say that preserving the chain of custody is about following the correct and
consistent procedure and hence ensuring the quality of evidence.
Chain of Custody Process:
In order to preserve digital evidence, the chain of custody should span from the first step of
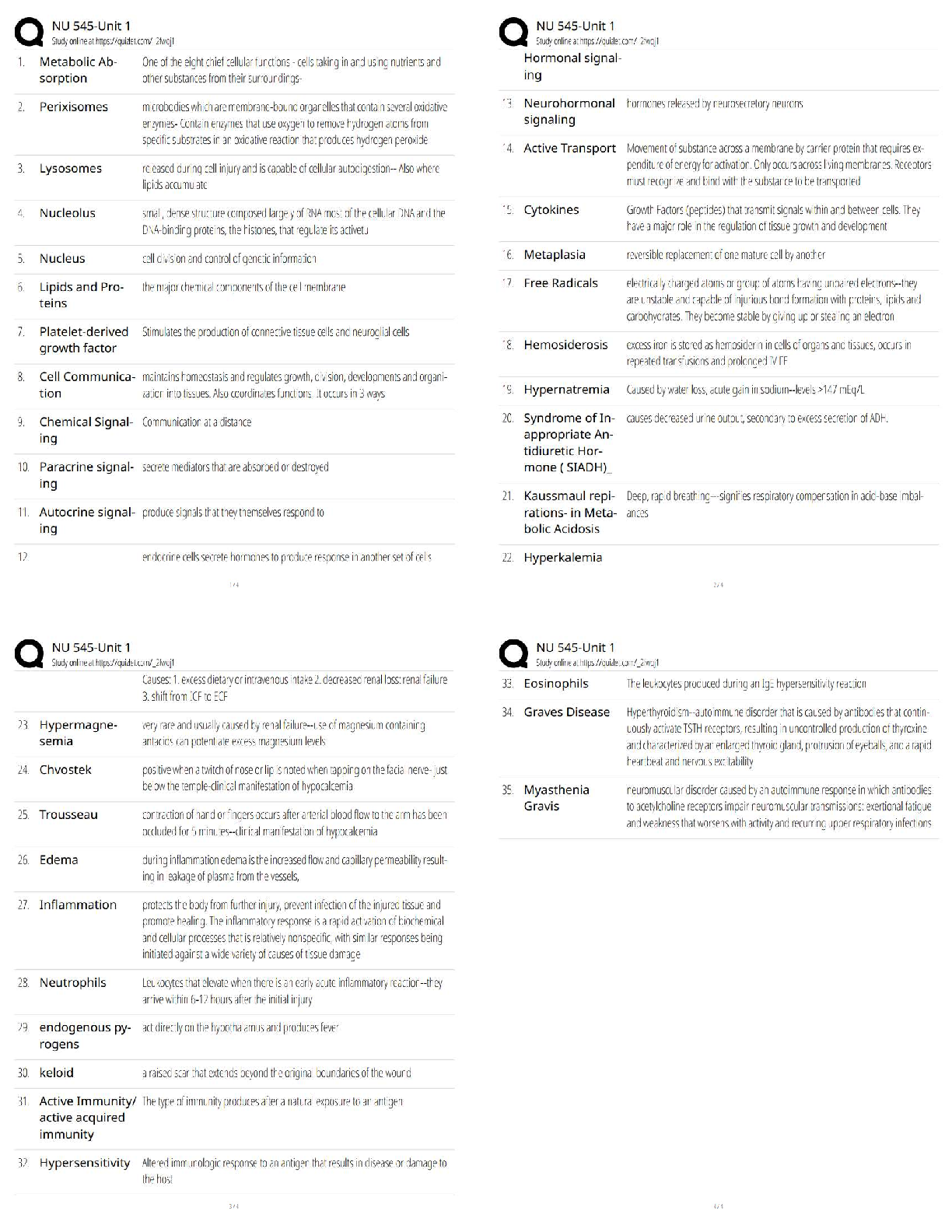
data collection to examination, analysis, reporting, and the time of presentation to the
Courts. This is very important to avoid the possibility of any suggestion that the evidence has
been compromised in any way.
1. Data Collection: This is where chain of custody process is initiated. It
involves identification, labeling, recording, and the acquisition of data from all
the possible relevant sources that preserve the integrity of the data and
evidence collected.
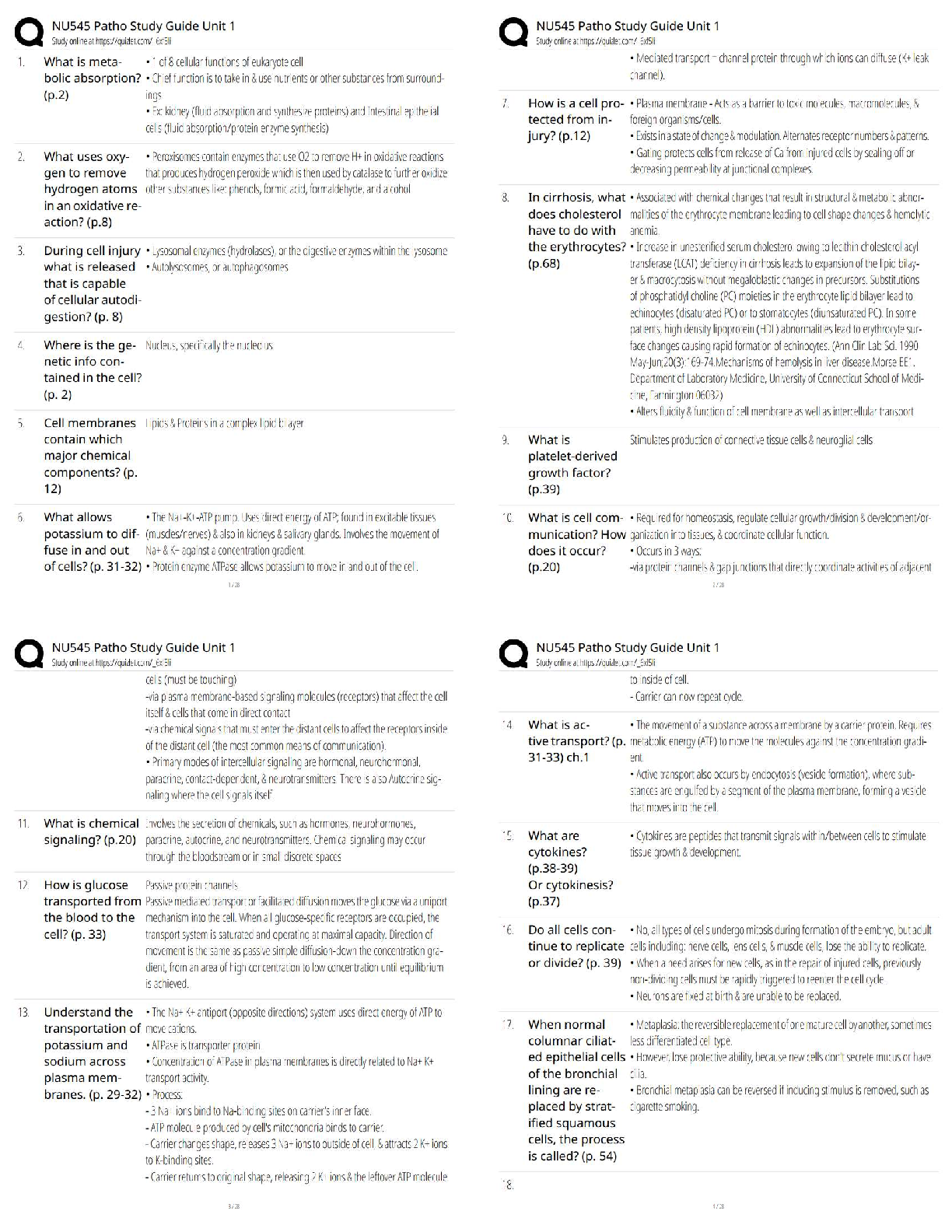
2. Examination: During this process, the chain of custody information is
documented outlining the forensic process undertaken. It is important to capture
screenshots throughout the process to show the tasks that are completed and
the evidence uncovered.
3. Analysis: This stage is the result of the examination stage. In the Analysis
stage, legally justifiable methods and techniques are used to derive useful
information to address questions posed in the particular case.
4. Reporting: This is the documentation phase of the Examination and Analysis
stage. Reporting includes the following:
Statement regarding Chain of Custody.
Explanation of the various tools used.
A description of the analysis of various data sources.
Issues identified.
Vulnerabilities identified.
Recommendation for additional forensics measures that can be taken.
Stenography
Steganography is an encryption technique that can be used along with cryptography as an extrasecure method in which to protect data. Steganography techniques can be applied to images, a
video file or an audio file
5 Steps for conducting forensics investigations
Policy and Procedure Development, Evidence Assessment, Evidence Acquisition, Evidence
Examination, Documenting and Reporting.
[Show More]










.png)

.png)