Computer Networking > EXAM > Midterm-operation security All answers 100% correct aid grade’A’ (All)
Midterm-operation security All answers 100% correct aid grade’A’
Document Content and Description Below
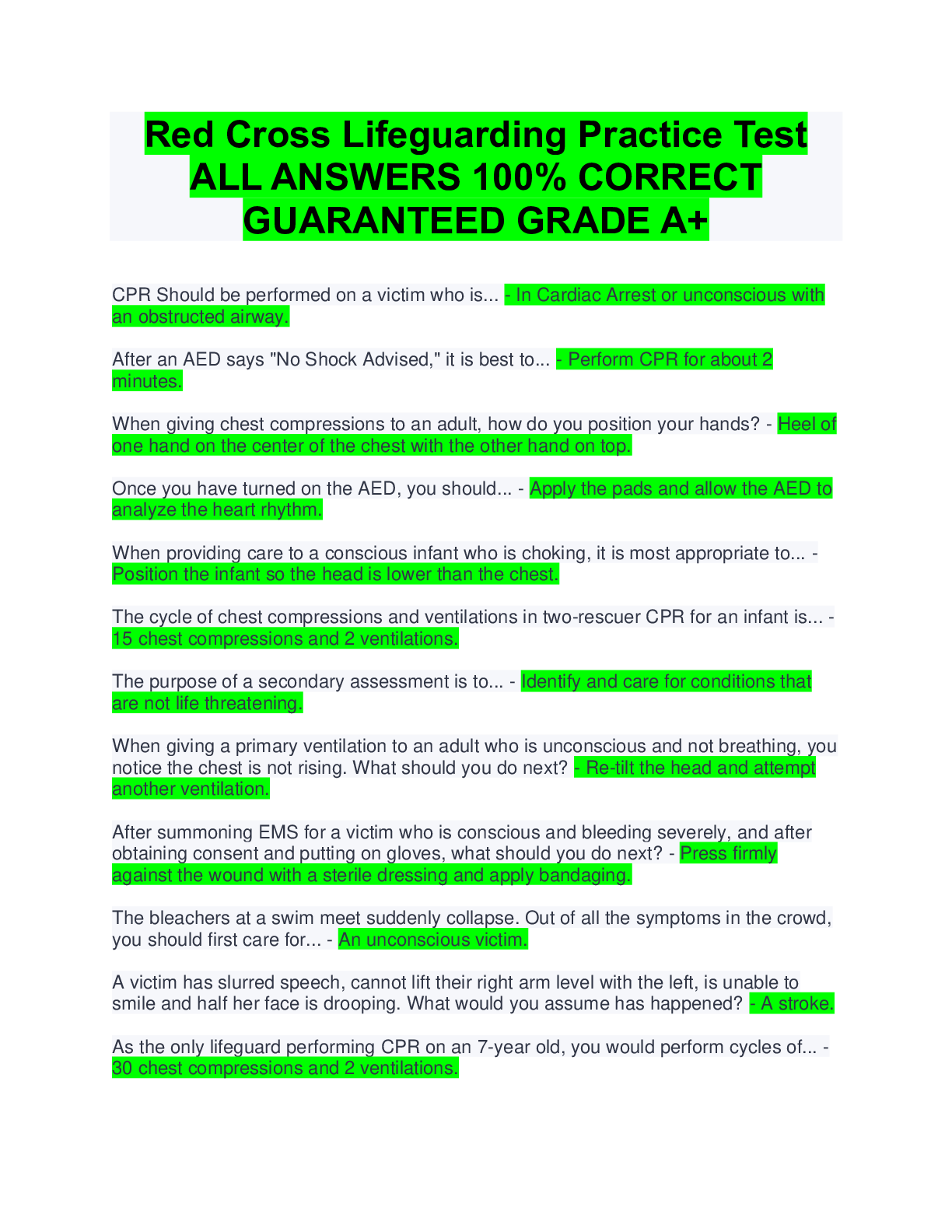
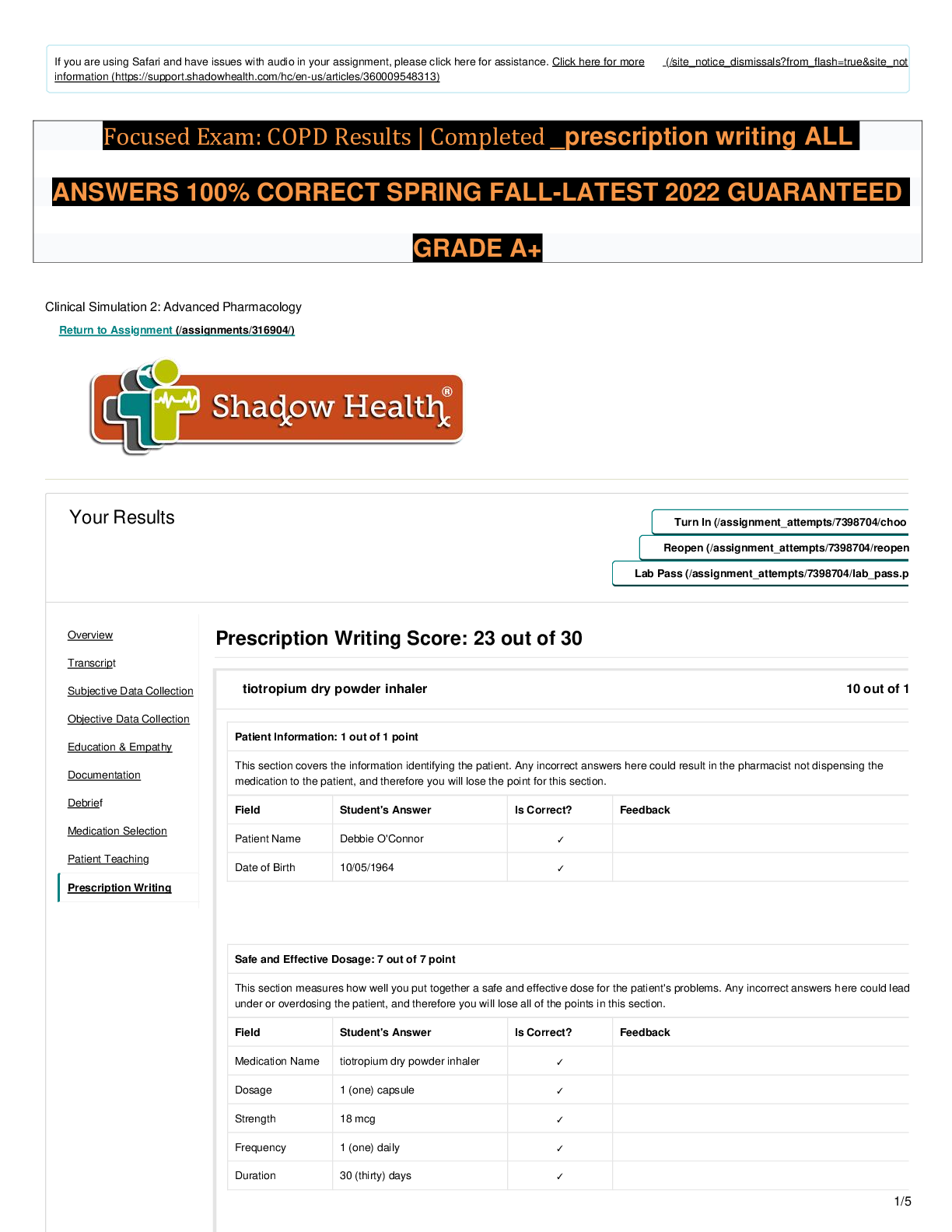
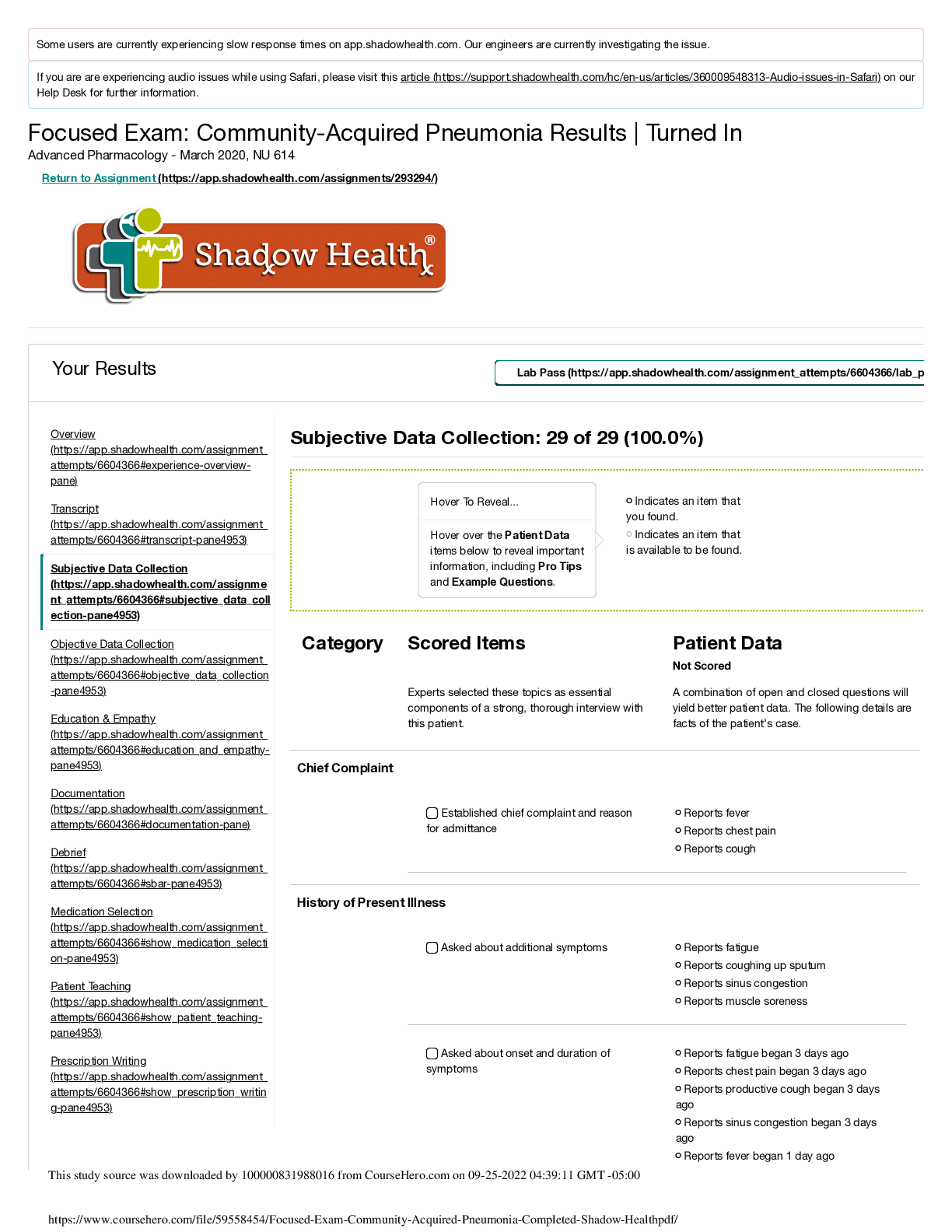
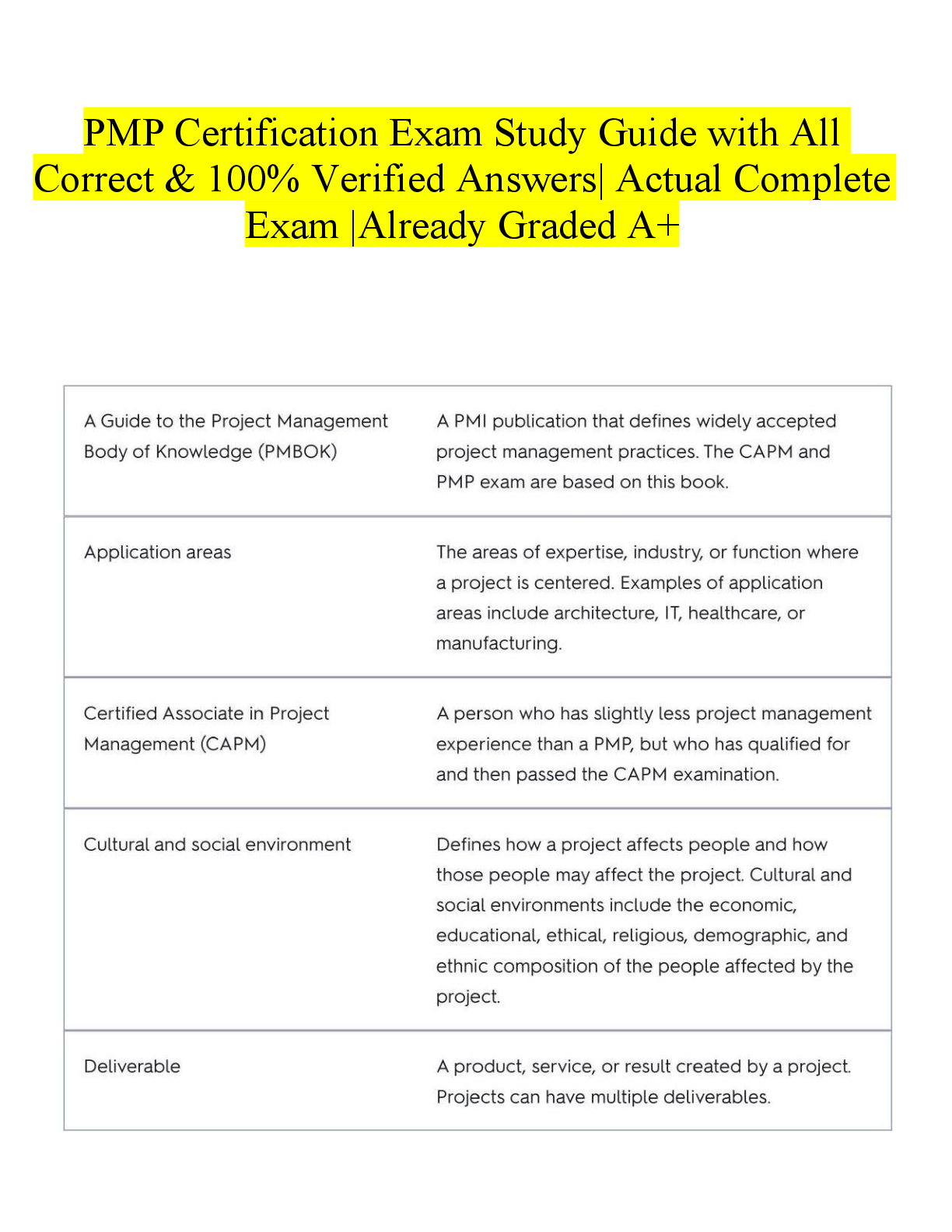
Question 1 1. is the act of protecting information and the systems that store and process it. Information systems security Policy framework Change management Policy principles document Questio ... n 2 1. Which of the following situations best illustrates the process of authentication? A Web site sets users’ passwords to expire every 90 days Using an electronic signature on official documentation When an application sets a limit on the amount of payment a user can approve When a service is made unavailable to a user due to a server crash Question 3 1. A vulnerability is a human-caused or natural event that could impact the system, whereas a risk is a weakness in a system that can be exploited. True False Question 4 1. Integrity ensures that only authorized individuals are able to access information. True False Question 5 1. Availability ensures information is available to authorized users and devices. Initially, the information owner must determine availability requirements. The owner must determine who needs access to the data and when. True False Question 6 1. Policies, which can be a process or a method for implementing a solution, often become the measuring stick by which an organization is evaluated for compliance. True False Question 7 1. Data exists generally in one of two states: data at rest, such as on a backup tape, or data in transit, such as when traveling across a network. True False Question 8 1. If human action is required, the control is considered . correctiv e automate d manual preventat ive Question 9 1. A(n) is a confirmed event that compromises the confidentiality, integrity, or availability of information. breach residual risk operational deviation threat Question 10 1. The most senior leader responsible for managing an organization’s risks is the chief privacy officer (CPO). Which of the following is not one of the responsibilities of the CPO? The CPO is responsible for keeping up with privacy laws. The CPO also needs to understand how the laws impact business. The CPO must be a lawyer. The CPO must work closely with a technology team to create strong security policies. Question 11 1. The domain refers to any endpoint device used by end users, which includes but is not limited to mean any smart device in the end user’s physical possession and any device accessed by the end user, such as a smartphone, laptop, workstation, or mobile device workstation user remote access system/applica tion Question 12 1. Authentication of a workstation and encryption of wireless traffic are issues that belong to which of the following two domains? LAN and WAN workstation and LAN LAN-WAN and remote access workstation and WAN Question 13 1. In recent years, has emerged as major technology. It provides a way of buying software, infrastructure, and platform services on someone else’s network. remote access domain social networking cloud computing web graffiti [Show More]
Last updated: 3 years ago
Preview 1 out of 12 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$10.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Jun 28, 2021
Number of pages
12
Written in
All
Additional information
This document has been written for:
Uploaded
Jun 28, 2021
Downloads
0
Views
51