Telecommunication and Information Technology > EXAM > This is the final exam that will consist of 50 multiple choice and true/false questions. Please sele (All)
This is the final exam that will consist of 50 multiple choice and true/false questions. Please select the most important response for each question. You will have 2 attempts with the highest grade being accepted as final. All answers 100% correct aid grade ‘A’
Document Content and Description Below
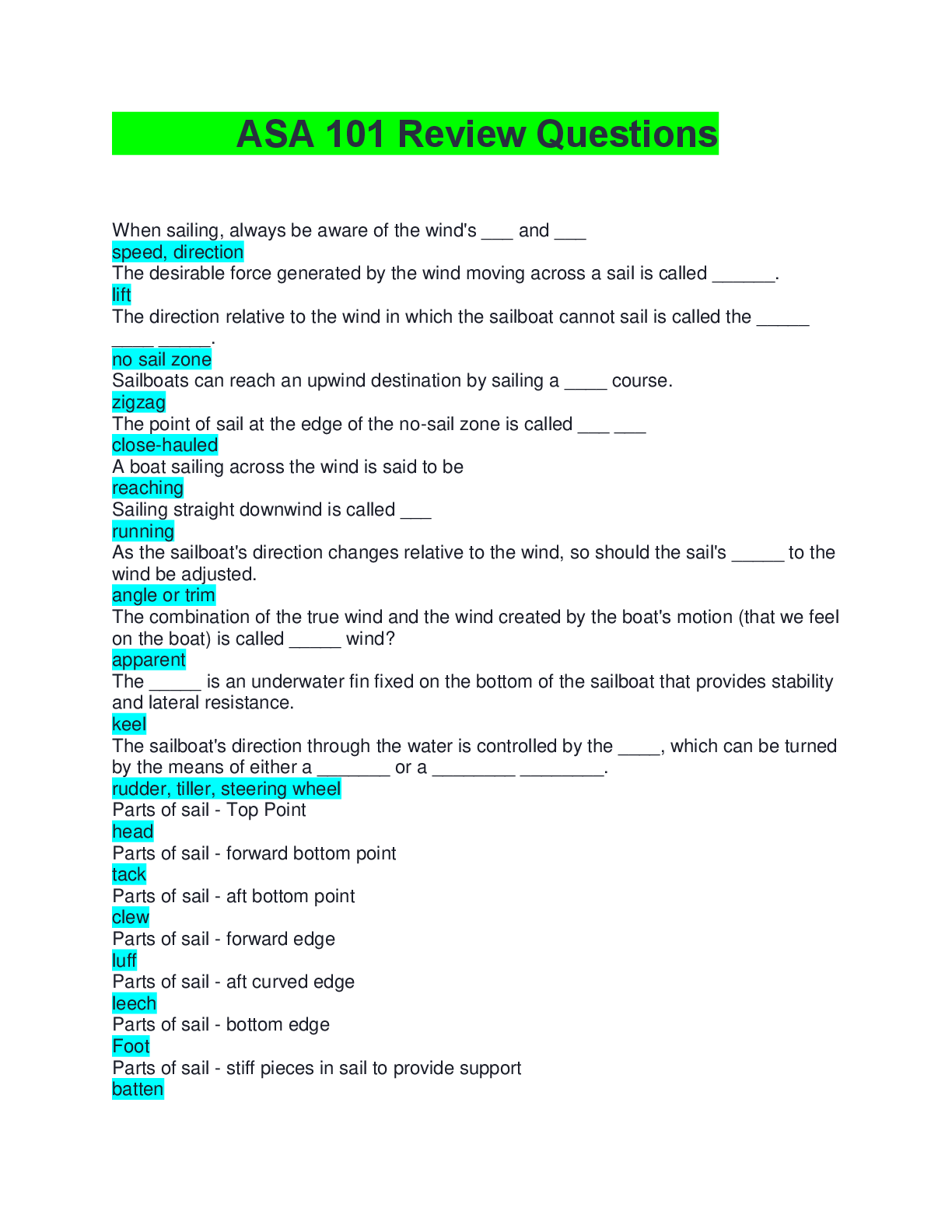
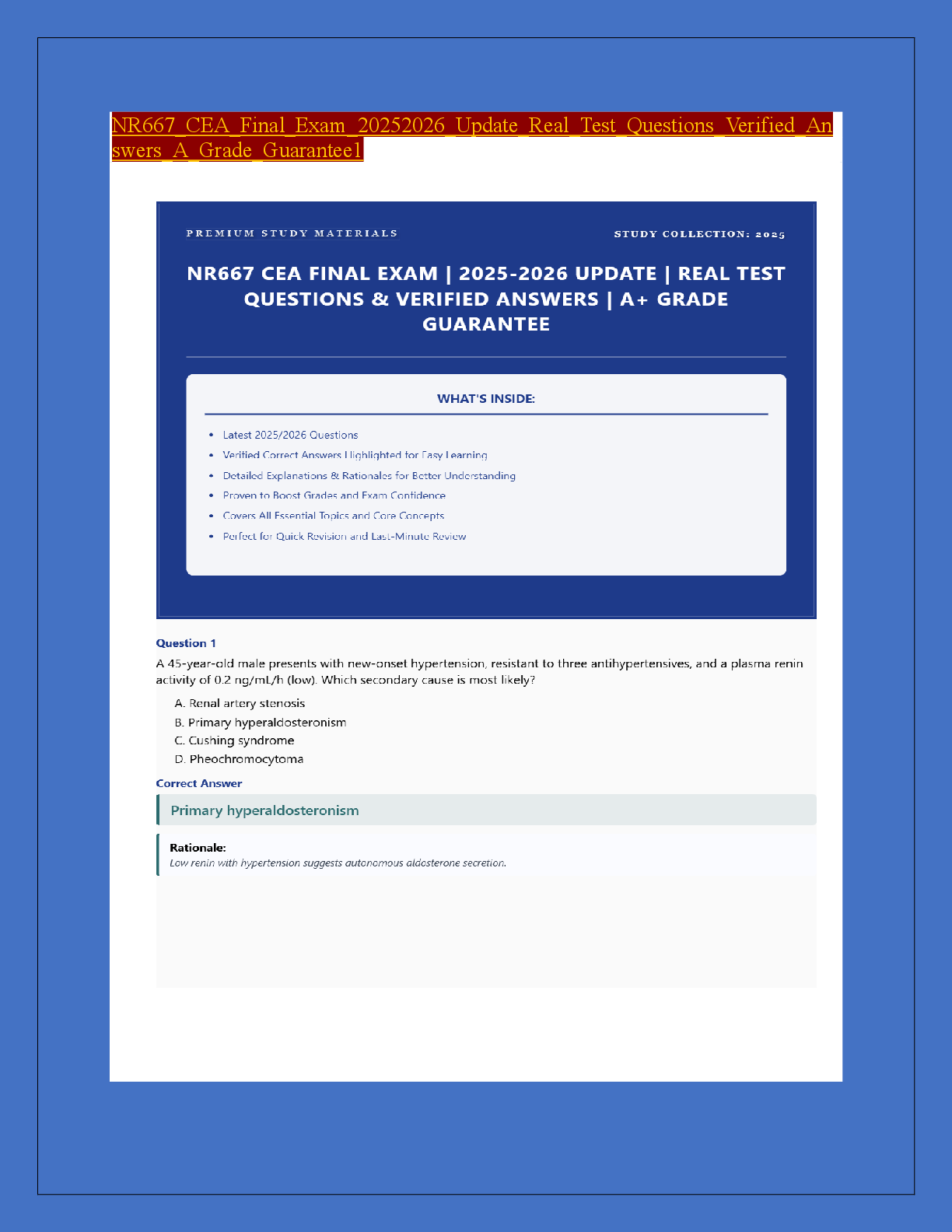
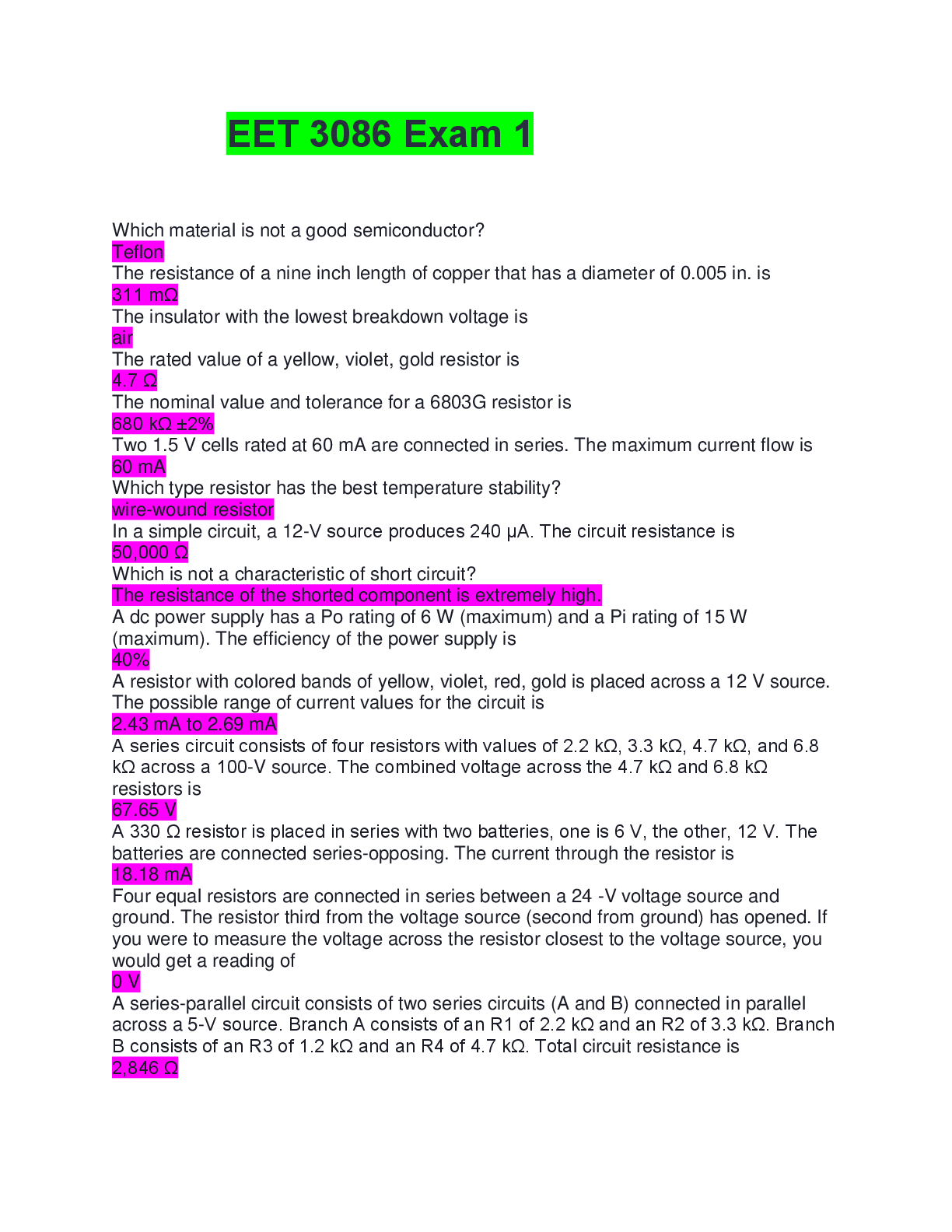
Question 1 1. There are several types of domains in the IT infrastructure. Which of the following is not one of these domains? A. user B. workstation C. remote access D ... . VPN Question 2 1. Policies and standards are a collection of concrete definitions that describe acceptable and unacceptable human behavior. The questions related to are more appropriate for procedures or guidelines than policies or standards, which require detail that is more at the level of . where, when and how; what and why how; what where and when; what, who and why where, when, and how; what, who, and why Question 3 1. Though there are many ways to group security policies, a common method is to organize common risks and related policy issues into that share similarities but are distinctive enough to allow logical separation into more manageable secure areas. A. segmented networks B. system access policies C. domains D. workstations Question 4 1. Of the eight classic personality types in the workplace, commanders, can often appear angry or even hostile toward ideas and others on the team and are critical of others’ ideas. True False Question 5 1. in e-commerce broadly deals with creating rules on how to handle a consumer’s transaction and other information. A. Security controls B. Consumer rights C. Personal privacy D. Shareholder rights Question 6 1. describes how to design and implement an information security governance structure, whereas describes security aspects for employees joining, moving within, or leaving an organization. A. Human resources security, organization of information security B. Information security policy, organization of information security C. Organization of information security, human resources security D. Human resources security, asset management Question 7 1. Security controls are measures taken to protect systems from attacks on the integrity, confidentiality, and availability of the system. If a potential employee is required to undergo a drug screening, which of the following controls is being conducted? A. preventive security controls B. technical security controls C. physical security controls D. administrative controls Question 8 1. is a measurement that quantifies how much information can be transmitted over the network. Memory DMZ Cloud storage Bandwidth Question 9 1. controls the processes associated with monitoring and changing configuration throughout the life of a system. This includes the original baseline configuration. A. Web-Based Enterprise Management B. Simple Network Management C. Configuration management D. Change management Question 10 1. Policy and standards often change as a result of business drivers. One such driver, known as , occurs when business shifts and new systems or processes are incorporated; these business shifts and new systems and processes may differ from what a standard or policy requires. A. business-as-usual developments B. business technology innovations C. business innovations D. business exceptions Question 11 1. In order to gain a deeper understanding of how employees interact in the workplace, it is useful to learn about the eight classic personality types that have been identified by HR Magazine. One of these is the achievers. Which of the following descriptions best captures this personality type? A. These people like structure and deadlines and tend to be obsessed with precision and attention to detail. B. These people are very result oriented. They genuinely want the best result and may seek different ways to bring that result into being. C. These people like to entertain and be the center of attention. They develop over time a wit and charm to capture people’s attention. D. These people are very kind and thoughtful to others. They want everyone to “feel good” and will put their own self-interest aside for the good of the whole. Question 12 1. make use of baselines to identify changes in the behavior of the network. I. Anomaly-based intrusion detection systems II. Protocols III. Authenticated configuration scanners IV. Misconfiguration remediation Question 13 1. If an organization is creating a customized data classification scheme, it is important to keep in mind the accepted guidelines. Which of the following is not one these guidelines? A. Define the number of classification levels. B. Identify each classification level. C. Connect the classification to particular handling requirements. D. Make recommendations for how audits can be conducted. Question 14 1. Using switches, routers, internal firewalls, and other devices, you can restrict network traffic with a , which limits what and how computers are able to talk to each other. A. demilitarized zone B. flat network C. sniffer D. segmented network Question 15 1. In workstation domain policies, _ provide the specific technology requirements for each device. IT staff uses recorded and published procedures to enact configurations by devices to ensure that secure connectivity for remote devices exists, as well as virus and malware protection and patch management capability, among several other related functions. A. procedures B. baseline standards C. guidelines D. control standards Question 16 1. refers to an attempt to cause fear or major disruptions in a society through hacking computers. Such attacks target government computers, major companies, or key areas of the economy. I. Cyberterrorism II. Globalization III. Nation-state attack IV. Sovereign war Question 17 1. The window of is the time between when an opportunity for risk is identified and when the risk is ultimately eliminated by a patch. A. threat B. risk C. vulnerability D. danger Question 18 1. While it would not be possible to classify all data in an organization, there has nonetheless been an increase in the amount of unstructured data retained in recent years, which has included data and logs. There are many different ways to make the time-consuming and expensive process of retaining data less challenging. Which of the following is not one these approaches? A. Classify only the data that is most vital and contains the highest risk to the organization. B. Classify data by point of origin or storage location. C. Classify data at use or time of inception. D. Classify all forms of data no matter the risk to the organization. Question 19 1. If human action is required, the control is considered _ . A. corrective B. automated C. manual D. Preventative [Show More]
Last updated: 3 years ago
Preview 1 out of 20 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$12.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Jun 28, 2021
Number of pages
20
Written in
All
Additional information
This document has been written for:
Uploaded
Jun 28, 2021
Downloads
0
Views
125