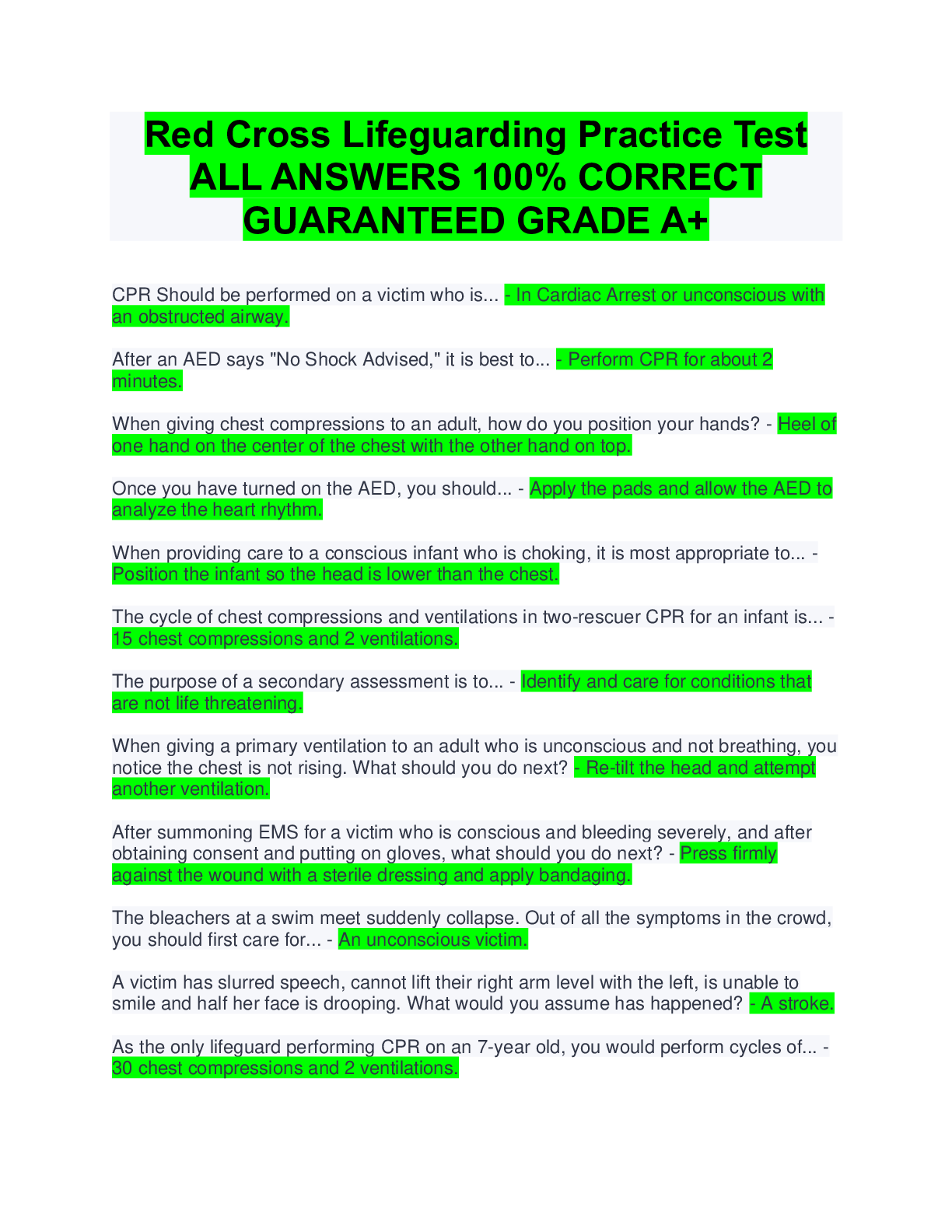
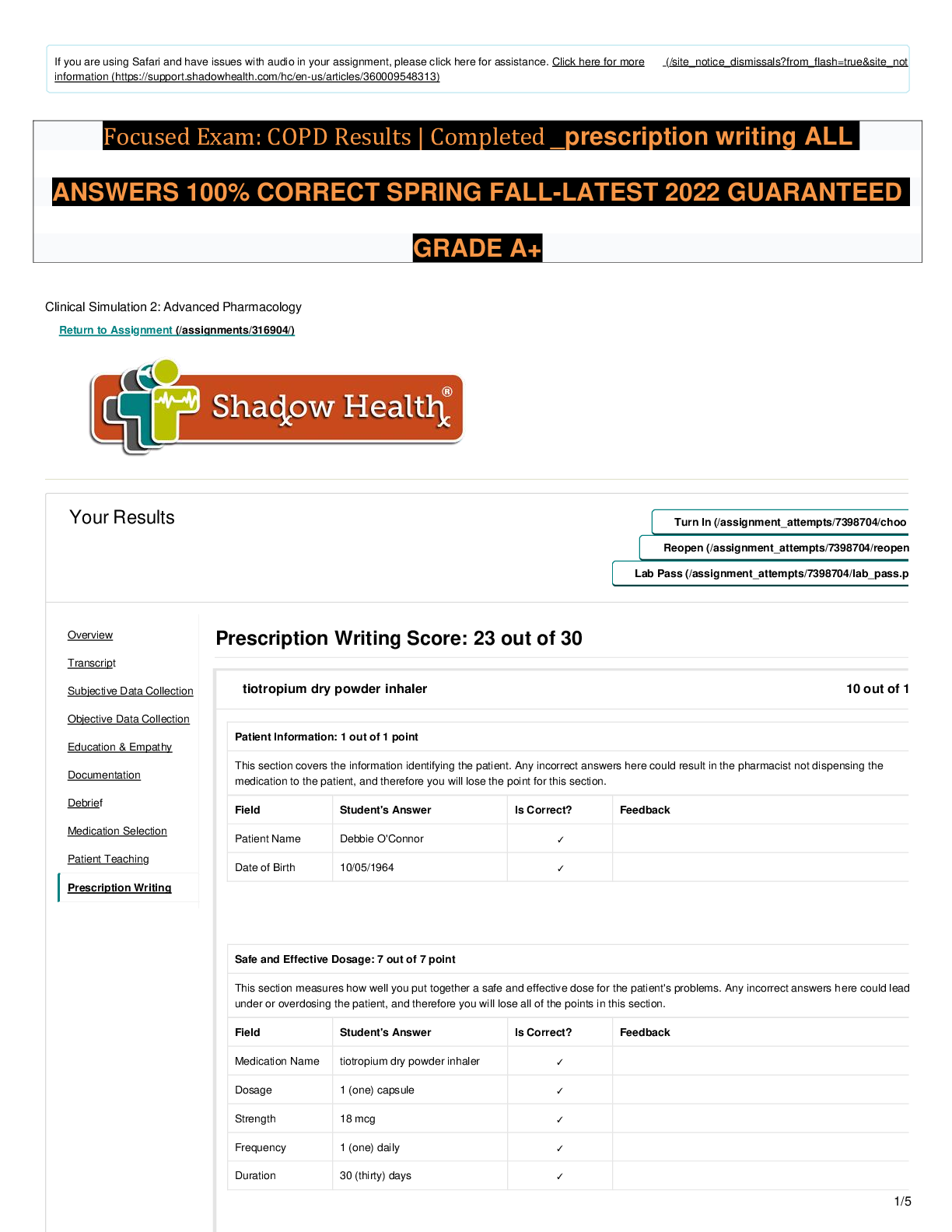
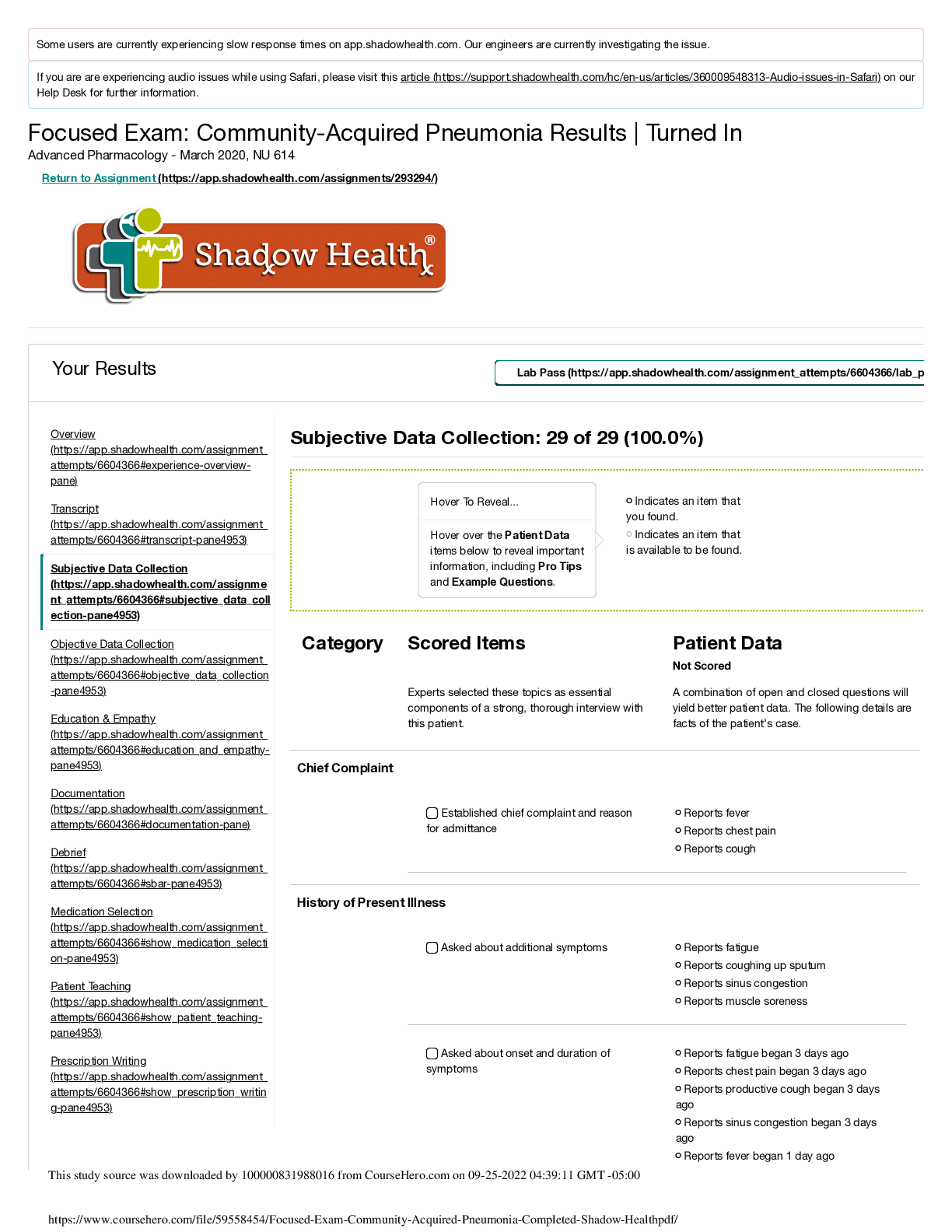
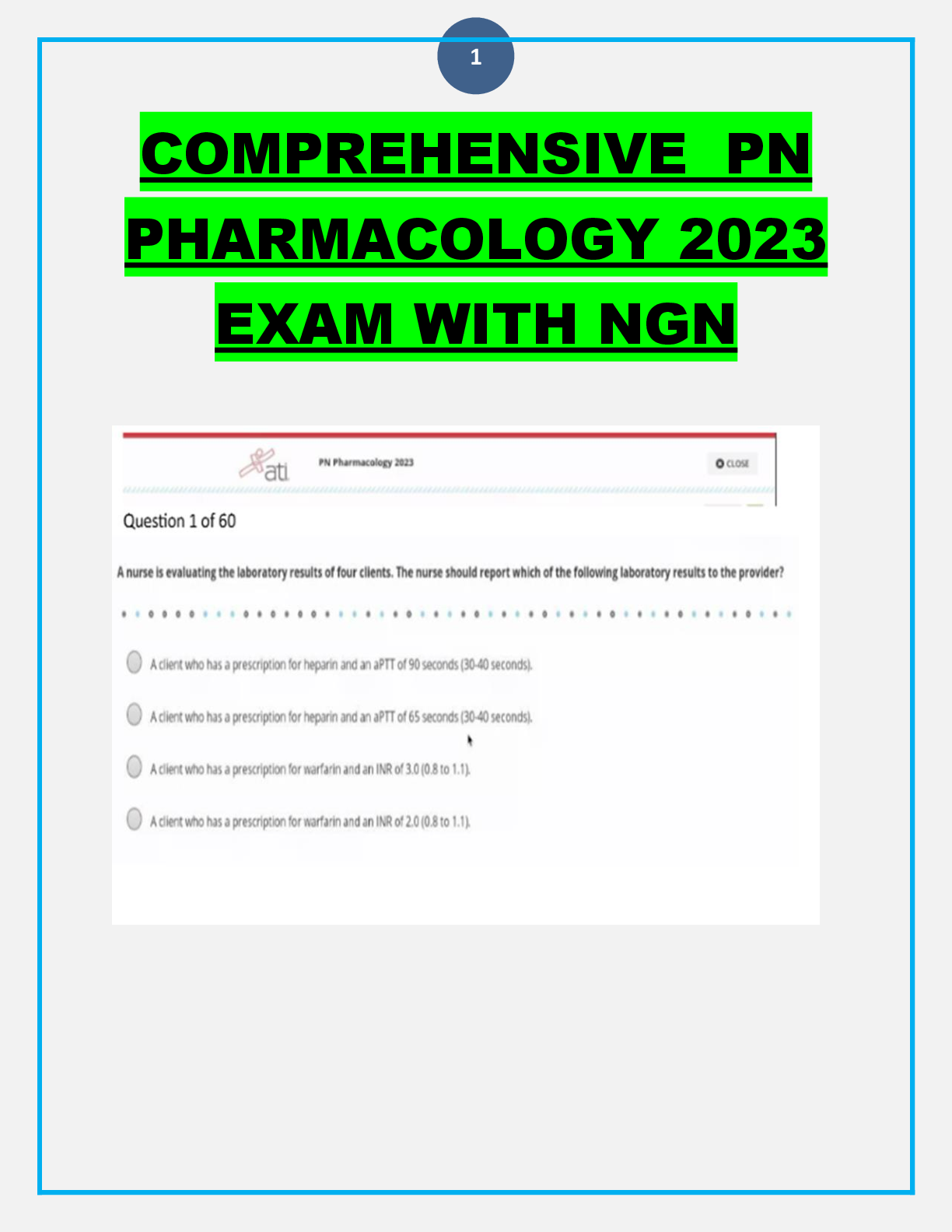
The Family Educational Rights and Privacy Act (FERPA) was put into law in 1974, and contains several key elements. Which of the key elements states that schools can share information without permission for legitimate edu
...
The Family Educational Rights and Privacy Act (FERPA) was put into law in 1974, and contains several key elements. Which of the key elements states that schools can share information without permission for legitimate education evaluation reasons as well as for health and safety reasons?
Selected Answer:
Correct Answer:
• Question 2
awareness exclusions
2 out of 2 points
Federal and state governments in the United States establish laws that define how to control, handle, share, and process the sensitive information that the new economy relies on. are then added to these laws, which are typically written by civil servants to implement the authority of the law.
Selected Answer:
Correct Answer:
• Question 3
Regulations Regulations
2 out of 2 points
In January 2013, two important changes were made to . First, it became easier to share records with child welfare agencies. Second, the change eliminates some requirements to notify parents when school records are being released.
Selected Answer: Correct Answer:
• Question 4
the Family Educational Rights and Privacy Act (FERPA) the Family Educational Rights and Privacy Act (FERPA)
2 out of 2 points
Which of the following agencies is responsible for developing information security standards and procedures that adhere to federal law?
Selected Answer:
Correct Answer:
• Question 5
The National Institute of Standards and Technology (NIST) The National Institute of Standards and Technology (NIST)
2 out of 2 points
refers to an attempt to cause fear or major disruptions in a society through hacking computers. Such attacks target government computers, major companies, or key areas of the economy.
Selected Answer:
Correct Answer:
• Question 6
Cyberterrorism Cyberterrorism
0 out of 2 points
An organization’s
meet regulatory requirements.
Selected Answer:
is a good source for determining what should be in security policies to
Correct Answer:
• Question 7
chief information security officer (CISO) privacy officer
2 out of 2 points
Of the six specific business risks, the risk results from negative publicity regarding an organization’s practices. Litigation and a decline in revenue are possible outcomes of this type of risk.
Selected Answer: Correct Answer:
• Question 8
reputational reputational
0 out of 2 points
In May 2013, a National Security Agency (NSA) contractor named Edward Snowden leaked thousands of documents to a journalist detailing how the U.S. implements intelligence surveillance across the Internet. In which of the following sectors did this breach occur?
Selected Answer:
Correct Answer:
• Question 9
federal government sector public sector
2 out of 2 points
The members of the committee help create priorities, remove obstacle, secure funding, and serve as a source of authority. Members of the committee, however, are leaders across the organization.
Selected Answer:
Correct Answer:
• Question 10
executive, security executive, security
0 out of 2 points
An illustration of would be an organization installing malware software on the network and endpoint, monitoring for suspicious traffic, and responding as needed.
Selected Answer:
Correct Answer:
• Question 11
risk evaluation disposal of risk
2 out of 2 points
While these two approaches have similarities in terms of the topics they address, will cover broad IT management topics and specify which security controls and management need to be installed; however,
does not address how to implement specific controls.
Selected Answer: Correct Answer:
• Question 12
COBIT, ISO COBIT, ISO
0 out of 2 points
Assume that the governance committee states that all projects costing more than $70,000 must be reviewed and approved by the chief information officer and the IT senior leadership team (SLT). At this point, the CIO has the responsibility to ensure that management processes observe the governance rules. For example, the project team might present the proposed project in an SLT meeting for a vote of approval. What does this scenario illustrate about organizational structure?
Selected Answer:
Correct Answer:
• Question 13
that individuals do not work in isolation
the difference between governance and management oversight
0 out of 2 points
The domain ensures risks are diminished and remediated in the most cost-effective manner. To prevent risk from increasing in severity and scope, this domain coordinates risk responses ensuring that the right people are engaged when appropriate.
Selected Answer:
Correct Answer:
• Question 14
risk governance risk response
2 out of 2 points
The key to security policy is being able to measure compliance against a set of controls. Security controls define
you protect the information. The security policies should define you set the goal.
Selected Answer:
Correct Answer:
• Question 15
how, why how, why
0 out of 2 points
There are many distinct benefits to control measurement. Which of the following benefits is the result of determining which security controls to measure?
Selected Answer: Correct Answer:
• Question 16
defines the effectiveness of the controls being measured defines the scope of the compliance being measured
2 out of 2 points
Once an organization clearly defines its IP, the security policies should specify how to documents with marks or comments, and the data, which determines in what location the sensitive file should be placed.
Selected Answer:
Correct Answer:
• Question 17
label, classify label, classify
0 out of 2 points
Which of the following security control design types does not prevent incidents or breaches immediately and relies on a human to decide what action to take?
Selected Answer:
Correct Answer:
• Question 18
corrective control
[Show More]