Business > QUESTIONS & ANSWERS > E-commerce Business Models and Concepts Questions and Approved Answers 100% Guarantee to Score A+ (All)
E-commerce Business Models and Concepts Questions and Approved Answers 100% Guarantee to Score A+
Document Content and Description Below
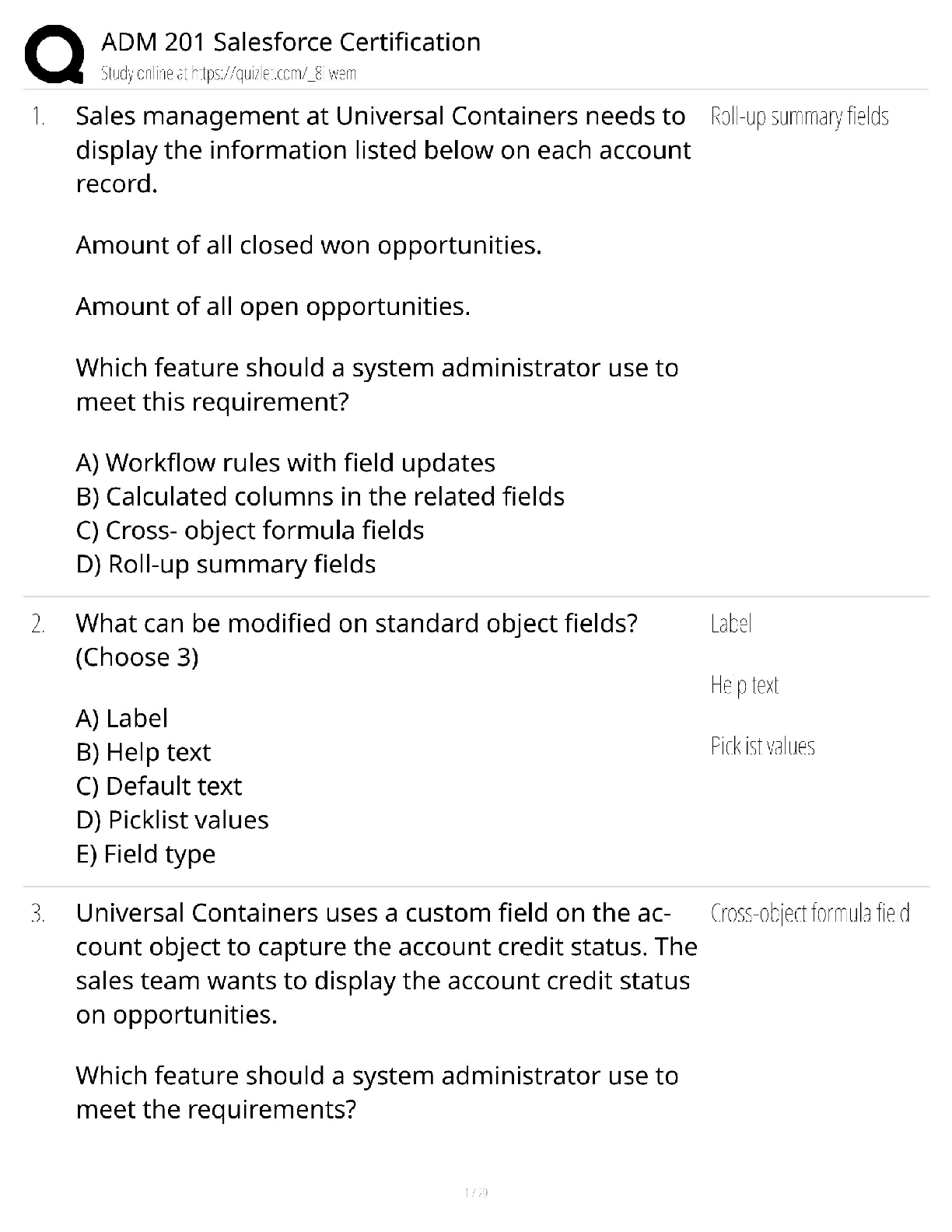
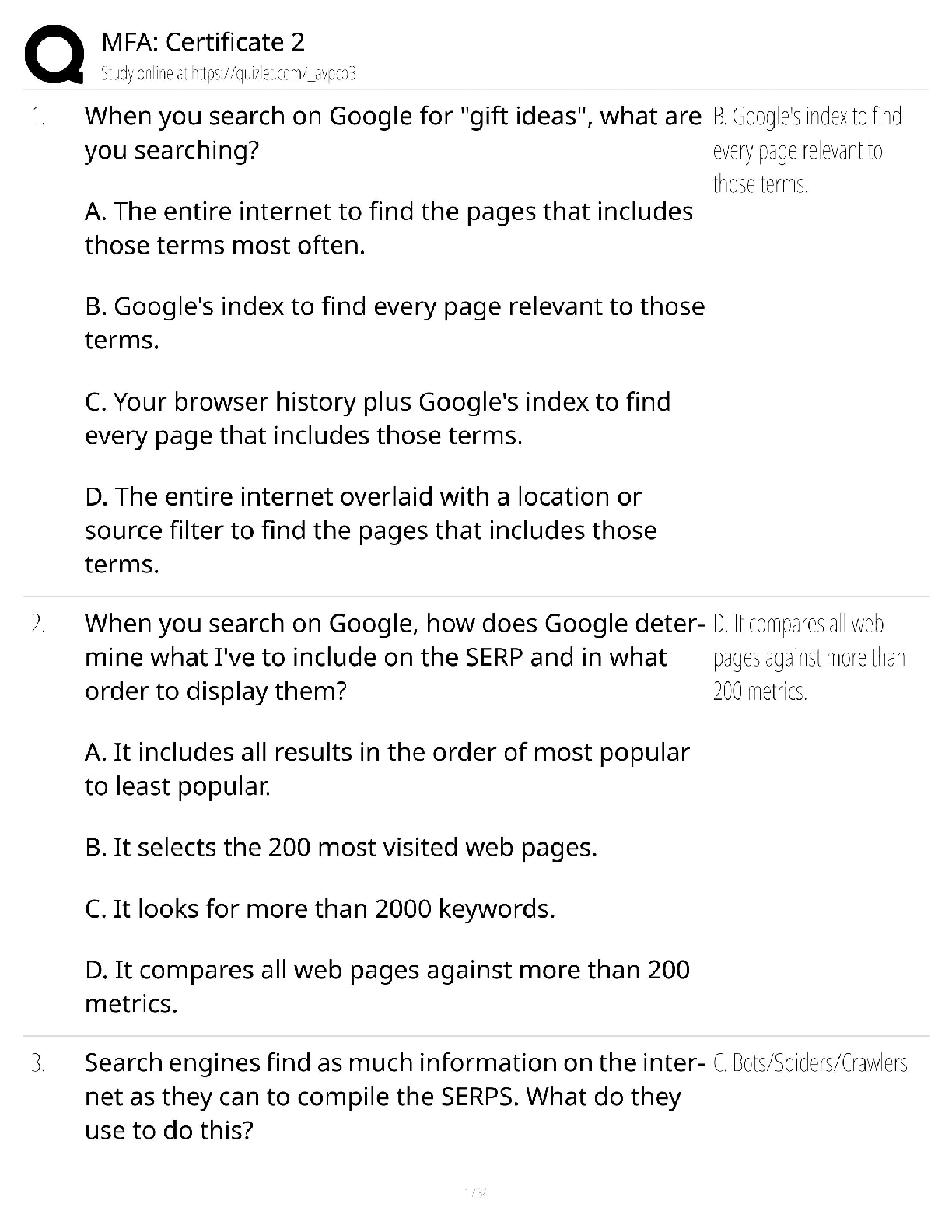
E-commerce 2013, 9e (Laudon/Traver) Chapter 2 E-commerce Business Models and Concepts 1) A value proposition defines how a company's product or service fulfills the needs of a customer. Answer: TR ... UE 2) The terms revenue model and financial model can be used interchangeably. Answer: TRUE 3) In order to be considered successful, a firm must produce returns greater than alternative investments. Answer: TRUE 4) An asymmetry exists whenever one participant in a market has more resources than other participants. Answer: TRUE 5) Most first movers have the complementary resources needed to sustain their advantage. Answer: FALSE 6) All firms need an organization to efficiently implement their business plans and strategies. Answer: TRUE 7) Visitors to specialized niche vortals tend to spend less money than the average visitor to a horizontal portal. Answer: FALSE 8) Barriers to entry into the e-tail marketplace are high. Answer: FALSE 9) Differentiation refers to situations in which there is little difference between products and the only basis of choosing a product is price. Answer: FALSE 10) Scale economies are efficiencies that result from flattening the hierarchy of an organization. Answer: FALSE 11) Real markets are perfect markets. Answer: FALSE 12) The Internet's universal standards decrease the cost of industry and firm operations. Answer: TRUE 13) Interactivity that enables product customization alters industry structure by reducing the threat of substitutes. Answer: TRUE 14) Interfirm rivalry is one area of the business environment where e-commerce technologies have had an impact on most industries. Answer: TRUE 15) Social technologies change industry structure by shifting programming and editorial decisions to consumers. Answer: TRUE 16) ________ and ________ are typically the most easily identifiable aspects of a company's business model. A) Market strategy; market opportunity B) Value proposition; revenue model C) Value proposition; competitive environment D) Revenue model; market strategy Answer: B 17) All of the following are key elements of a business model except: A) competitive environment. B) organizational development. C) information technology strategy. D) market strategy. Answer: C 18) Which element of the business model addresses the question of why a customer should buy from the firm? A) revenue model B) competitive advantage C) market strategy D) value proposition Answer: D 19) Which element of the business model examines who else occupies the firm's intended marketspace? A) value proposition B) competitive environment C) competitive advantage D) market strategy Answer: B 20) Which of the following are Amazon's primary value propositions? A) personalization and customization B) selection and convenience C) reduction of price discovery cost D) management of product delivery Answer: B 21) Your solar-panel manufacturing firm has developed a unique and patented process for creating high-efficiency solar panels at a fraction of current costs. This will enable your firm to adopt a strategy of: A) cost competition. B) scope. C) scale. D) focus. Answer: A 22) A firm's ________ describes how a firm will produce a superior return on invested capital. A) value proposition B) revenue model C) market strategy D) competitive advantage Answer: B 23) Which of the following is an example of the subscription revenue model? A) Ancestry.com B) eBay C) Amazon D) Twitter Answer: A 24) Stickiness is an important attribute for which revenue model? A) advertising revenue model B) subscription revenue model C) transaction fee revenue model D) sales revenue model Answer: A 25) Which of the following companies utilizes a transaction fee revenue model? A) WSJ.com B) E*Trade C) Twitter D) Sears.com Answer: B 26) Which of the following is an example of the affiliate revenue model? A) Yahoo B) eBay C) Gap.com D) MyPoints Answer: D 27) Assume you are analyzing the market opportunity of a distance learning company, Learnmore.com, that creates education courses delivered over the Internet for the Fortune 1000 corporate market. Assume that the overall size of the distance learning market is $25 billion. The overall market can be broken down into three major market segments: Corporate, College, and Elementary/High School, each of which accounts for a third of the market. Within the Corporate market, there are two market niches: Fortune 1000, which accounts for 60% of the market, and all others, which together account for 40% of the market. What is Learnmore.com's realistic market opportunity, approximately? A) $5 billion B) $6.6 billion C) $165 billion D) $25 billion Answer: A 28) Which of the following factors is not a significant influence on a company's competitive environment? A) how many competitors are active B) what the market share of each competitor is C) the availability of supportive organizational structures D) how competitors price their products Answer: C 29) Which of the following would be considered an indirect competitor of American Airlines? A) JetBlue B) Zipcar C) Orbitz D) British Airways Answer: B 30) The existence of a large number of competitors in any one market segment may indicate: A) an untapped market niche. B) the market is saturated. C) no one firm has differentiated itself within that market. D) a market that has already been tried without success. Answer: B 31) All of the following can be considered a direct or indirect competitor of Amazon.com except: A) eBay. B) Apple's iTunes Store. C) Barnesandnoble.com. D) Starbucks. Answer: D 32) A perfect market is one in which: A) there are no competitive advantages or asymmetries because all firms have equal access to all the factors to production. B) one firm develops an advantage based on a factor of production that other firms cannot purchase. C) one participant in the market has more resources than the others. D) competition is at a minimum, as each niche market within an industry is served by the company with the greatest competitive advantage. Answer: A 33) The business model of e-distributors is quite similar to that of: A) e-tailers. B) transaction brokers. C) exchanges. D) service providers. Answer: A 34) All of the following use an advertising revenue model except: A) Facebook. B) Yahoo. C) Google. D) Amazon. Answer: D 35) All of the following statements about Groupon are true except: A) Groupon has yet to show a profit. B) Groupon combines two major trends in e-commerce: localization and social networks. C) It is unclear if Groupon's business model is sustainable. D) Groupon believes it must scale up fast in a winner-take-all market. Answer: A 36) Which of the following is not considered a portal? A) Yahoo B) MSN C) WSJ.com D) AOL Answer: C 37) Horizontal or general portals primarily generate revenue in all of the following ways except: A) charging advertisers for ad placement. B) collecting transaction fees. C) sales of goods. D) charging subscription fees. Answer: C 38) A business document that specifically details how you plan on selling your product and find new customers is called a: A) sales analysis. B) business plan. C) competitive strategy. D) market strategy. Answer: D 39) Which of the following is not a community provider? A) LinkedIn B) Facebook C) Priceline D) Pinterest Answer: C 40) Which of the following is not a variation of the e-tailer business model? A) bricks-and-clicks B) virtual merchant C) market creator D) manufacturer-direct Answer: C 41) An example of a company using the content provider model is: A) Priceline. B) Rhapsody.com. C) Dell. D) eBay. Answer: B 42) Which of the following is not an example of the bricks-and-clicks e-tailing business model? A) Walmart.com B) JCPenney.com C) Dell.com D) Staples.com Answer: C 43) The overall retail market in the United States in 2012 was estimated at about: A) $37 trillion. B) $3.7 trillion. C) $370 billion. D) $37 billion. Answer: B 44) In general, the key to becoming a successful content provider is to: A) own the content being provided. B) own the technology by which content is created, presented, and distributed. C) provide online content for free. D) provide other services as well as online content. Answer: A 45) Expedia is an example of a: A) community provider. B) transaction broker. C) market creator. D) service provider. Answer: B 46) All of the following may lead to a competitive advantage except: A) less expensive suppliers. B) better employees. C) fewer products. D) superior products. Answer: C 47) The basic value proposition of community providers is: A) they offer a fast, convenient one-stop site where users can focus on their most important concerns and interests. B) they offer consumers valuable, convenient, time-saving, and low cost alternatives to traditional service providers. C) they create a digital electronic environment for buyers and sellers to meet, agree on a price and transact. D) they increase customers' productivity by helping them get things done faster and more cheaply. Answer: A 48) All of the following are examples of Business-to-Business (B2B) business models except: A) e-distributors. B) e-procurement. C) private industrial networks. D) e-tailers. Answer: D 49) What is the primary revenue model for an e-distributor? A) sales B) transaction fee C) advertising D) subscription Answer: A 50) Grainger.com is an example of which of the following business models? A) B2B service provider B) exchange C) e-distributor D) industry consortia Answer: C 51) ________ create and sell access to digital electronic markets. A) E-distributors B) Portals C) E-procurement firms D) Market creators Answer: C 52) One of the competitive advantages of a B2B service provider is that it can spread the cost of an expensive software system over many users, achieving efficiencies referred to as: A) application efficiencies. B) network efficiencies. C) scale economies. D) network externalities. Answer: C 53) Over the past decade: A) the number of exchanges greatly increased. B) the number of exchanges diminished sharply. C) the number of exchanges stayed about the same. D) exchanges have totally disappeared. Answer: B 54) Exostar is an example of a(n): A) private industrial network. B) exchange. C) industry consortium. D) e-distributor. Answer: C 55) Which of the following is an unfair competitive advantage? A) brand name B) access to global markets C) lower product prices D) superior technology Answer: A 56) The element of a business model that is responsible for making the model work is: A) the management team. B) the organizational structure. C) the firm's key competitive advantage. D) the market strategy. Answer: A 57) eBay uses all of the following business models except: A) B2C market creator. B) C2C market creator. C) content provider. D) e-commerce infrastructure provider. Answer: C 58) Your startup firm has developed Web-based note-taking software that allows participants to create and share virtual notes attached to existing Web pages. You anticipate marketing your online application to Web development and design companies. Which of the following revenue models is the most appropriate for your new company? A) advertising B) transaction fee C) affiliate D) subscription Answer: D 59) Which of the following community providers is focused on financial advice, news, and opinions? A) The Well (Well.com) B) The Motley Fool (Fool.com) C) RightStart D) iVillage Answer: B 60) Which of the following features of e-commerce technology changes industry structure by lowering barriers to entry but greatly expands the market at the same time? A) global reach B) richness C) interactivity D) personalization Answer: A 61) All of the following are business models employed by the music industry except: A) subscription. B) peer-to-peer streaming. C) download-and-own. D) cloud streaming. Answer: B 62) Which of the following is not a primary activity in a firm value chain? A) inbound logistics B) finance/accounting C) operations D) sales and marketing Answer: B 63) A ________ coordinates a firm's suppliers, distributors, and delivery firms with its own production needs using an Internet-based supply chain management system. A) value chain B) value system C) value web D) business strategy Answer: C 64) If you wished to leverage the ubiquitous nature of the Web to differentiate your product, you would: A) enable individual customization of the product by consumers. B) implement a strategy of commoditization. C) adopt a strategy of cost competition. D) develop a scope strategy to compete within a narrower market segment. Answer: A 65) A strategy designed to compete within a narrow market or product segment is called a ________ strategy. A) scope B) differentiation C) cost D) focus Answer: D E-commerce 2013, 9e (Laudon/Traver) Chapter 3 E-commerce Infrastructure: The Internet, Web, and Mobile Platform 1) Packet switching requires a dedicated circuit. Answer: FALSE 2) Transmission Control Protocol is the protocol that provides the Internet addressing scheme. Answer: FALSE 3) IPv6 provides for 64-bit IP addresses. Answer: FALSE 4) Tablet computers rely on the Internet cloud for processing and storage. Answer: TRUE 5) Google Apps is an example of cloud computing. Answer: TRUE 6) HTML is the Internet protocol used to transfer Web pages. Answer: FALSE 7) The major hubs in the United States where the Internet backbone intersects with regional and local networks are now commonly referred to as Internet Exchange Points (IXPs). Answer: TRUE 8) T1 and T3 refer to international telephone standards for digital communication. Answer: TRUE 9) One of Internet2's projects is a nationwide 100 gigabit-per-second network. Answer: TRUE 10) WLAN-based Internet access derives from the same technological foundations as telephonebased wireless Internet access. Answer: FALSE 11) Streaming media reduces the effects of latency. Answer: FALSE 12) XML is used to format the structure and style of a Web page. Answer: FALSE 13) FTP is a protocol used to transfer files to and from a server. Answer: TRUE 14) Internet access providers typically provide faster download speeds than upload speeds to consumers. Answer: TRUE 15) RSS is an XML format that allows users to have digital content automatically sent to their computers over the Internet. Answer: TRUE 16) During which period of time did the Institutionalization phase of Internet development take place? A) 1950-1960 B) 1961-1974 C) 1975-1995 D) 1995-through the present Answer: C 17) Which of the following occurred during the Commercialization phase of Internet development? A) The fundamental building blocks of the Internet were realized in actual hardware and software. B) Large mainframes on different college campuses were linked. C) The Domain Name System was introduced. D) NSF privatized the operation of the Internet's backbone. Answer: D 18) During which phase of the development of the Internet was Ethernet invented? A) Commercialization phase B) Institutional phase C) Innovation phase D) Consolidation phase Answer: C 19) Which of the following is not one of the basic technological foundations of the Internet? A) client/server computing B) Tracert C) TCP/IP communications protocol D) packet-switching hardware Answer: B 20) The process of slicing digital messages into parcels, sending them along different communication paths as they become available, and reassembling them at the destination point is called: A) routing. B) the Transmission Control Protocol. C) packet switching. D) the File Transfer Protocol. Answer: C 21) Which of the following is the core communications protocol for the Internet? A) Telnet B) FTP C) TCP/IP D) SSL Answer: C 22) The Transport Layer of TCP/IP is responsible for which of the following? A) placing packets on and receiving them from the network medium B) addressing, packaging, and routing messages C) providing communication with the application by acknowledging and sequencing the packets to and from the application D) providing a variety of applications with the ability to access the services of the lower layers Answer: C 23) The Internet Layer of TCP/IP is responsible for which of the following? A) placing packets on and receiving them from the network medium B) addressing, packaging, and routing messages C) providing communication with the application by acknowledging and sequencing the packets to and from the application D) providing a variety of applications with the ability to access the services of the lower layers Answer: B 24) Which of the following allows users to communicate visually and aurally in real-time, and uses high-resolution monitors to simulate the presence of participants? A) telepresence B) videoconferencing C) VOIP D) IP telephony Answer: A 25) An IPv4 address is expressed as a: A) 32-bit number that appears as a series of four separate numbers separated by semicolons. B) 64-bit number that appears as a series of four separate numbers separated by semicolons. C) 64-bit number that appears as a series of four separate numbers separated by periods. D) 32-bit number that appears as a series of four separate numbers separated by periods. Answer: D 26) The natural language convention used to represent IP addresses is called the: A) uniform resource locator system. B) Internet protocol addressing schema. C) domain name system. D) assigned numbers and names (ANN) system. Answer: C 27) The addresses used by browsers to identify the location of content on the Web are called: A) domain names. B) uniform resource locators. C) IP addresses. D) file paths. Answer: B 28) Which of the following statements about client/server computing is true? A) It exploded the available communications capacity. B) It provided communication rules and regulations. C) It connects multiple powerful personal computers together in one network with one or more servers dedicated to common functions that they all need. D) It does not provide sufficient computing capacity to support graphics or color. Answer: C 29) Which of the following is not an advantage of client/server computing over centralized mainframe computing? A) It is easy to expand capacity by adding servers and clients. B) Each client added to the network increases the network's overall capacity and transmission speeds. C) Client/server networks are less vulnerable, in part because the processing load is balanced over many powerful smaller computers rather than concentrated in a single huge computer. D) There is less risk that a system will completely malfunction because backup or mirror servers can pick up the slack if one server goes down. Answer: B 30) ________ is a model of computing in which firms and individuals obtain computing power and software applications over the Internet, rather than purchasing and installing it on their own computers. A) Client/server computing B) P2P computing C) Mobile computing D) Cloud computing Answer: D 31) Which of the following protocols is used to send mail to a server? A) SMTP B) FTP C) HTTP D) SSL Answer: A 32) Where does TSL operate within TCP/IP? A) between the Internet Layer and the Transport Layer B) between the Transport Layer and the Application Layer C) between the Network Interface Layer and the Transport Layer D) between the Internet Layer and the Application Layer Answer: B 33) A(n) ________ is an audio presentation stored as an audio file and posted to the Web for users to download. A) podcast B) RSS subscription C) weblog D) widget Answer: A 34) ________ is one of the original Internet services and is used to transfer files from a server computer to a client computer and vice versa. A) SMTP B) FTP C) HTTP D) SSL Answer: B 35) ________ is a utility program that allows you to check the connection between your client and a TCP/IP network. A) Ping B) Telnet C) Tracert D) Finger Answer: A 36) Which layer of Internet architecture is composed of the telecommunications networks and protocols? A) Network Technology Substrate layer B) Middleware Services layer C) Transport Services and Representation Standards layer D) Applications layer Answer: A 37) TCP/IP operates in which layer of Internet architecture? A) Network Technology Substrate layer B) Middleware Services layer C) Transport Services and Representation Standards layer D) Applications layer Answer: C 38) An Internet-enabled media player would run in which layer of Internet architecture? A) Network Technology Substrate layer B) Middleware Services layer C) Transport Services and Representation Standards layer D) Applications layer Answer: D 39) The layer of Internet architecture that ties the applications to the communications network and includes such services as security and authentication is called the: A) Network Technology Substrate layer. B) Middleware Services layer. C) Transport Services and Representation Standards layer. D) Applications layer. Answer: B 40) The backbone of the Internet is formed by: A) Internet Exchange Points (IXPs). B) Network Service Providers (NSPs). C) Internet Service Providers (ISPs). D) Metropolitan Area Exchanges (MAEs). Answer: B 41) When talking about the physical elements of the Internet, the term redundancy refers to: A) transmitting multiple copies of a single packet to safeguard against data loss. B) the use of tiered high-speed switching computers to connect the backbone to regional and local networks. C) delays in messages caused by the uneven flow of information through the network. D) multiple duplicate devices and paths in a network built so that data can be rerouted if a breakdown occurs. Answer: D 42) The "hubs" where the backbone owners connect with one another are called: A) Internet Exchange Points (IXPs). B) Network Service Providers (NSPs). C) Internet Service Providers (ISPs). D) Metropolitan Access Points (MAPs). Answer: A 43) Local area networks that operate within a single organization that leases access to the Web directly from regional and national carriers are called: A) wide area networks. B) extranets. C) campus area networks. D) private exchanges. Answer: C 44) The ________ is a consortium of corporations, government agencies, and nonprofit organizations that monitors Internet policies and practices. A) Internet Engineering Steering Group (IESG) B) World Wide Web Consortium (W3C) C) Internet Engineering Task Force (IETF) D) Internet Society (ISOC) Answer: D 45) The ________ helps define the overall structure of the Internet. A) IAB B) IESG C) W3C D) ITU Answer: A 46) Which of the following is not a limitation of the current Internet? A) HTML, which is not proficient for designing business documents or databases for Web viewing B) limited bandwidth, which causes congestion and cannot adequately handle video and voice traffic C) architectural restrictions, which stipulate that numerous requests for the same file must each be answered individually, slowing network performance D) the difficulty in expanding capacity by adding servers and clients Answer: D 47) Which of the following is not true about the mobile platform? A) Most smartphones use Intel chips. B) The number of cell phones worldwide exceeds the number of PCs. C) About 25% of the world's cell phones are smartphones. D) Unlike PCs, smartphones do not need fans. Answer: A 48) Which of the following statements about fiber-optic cable is not true? A) It consists of twelve or sixteen strands of glass. B) It is thinner and lighter than coaxial or twisted pair cable. C) It enables better data security than coaxial cable. D) There are thousands of miles of installed fiber-optic cable in the United States that are not being used. Answer: A 49) In the United States, there are two main types of cellular networks, CDMA and: A) GSM. B) Bluetooth. C) wireless. D) WiMAX. Answer: A 50) Which of the following is the "killer app" of 2012? A) social networks B) blogs C) tablet PCs D) search engines Answer: A 51) The major technologies used with wireless local area networks are: A) Wi-Fi and Bluetooth. B) Wi-Fi and WiMAX. C) Bluetooth and 3G. D) WiMAX and 3G. Answer: A 52) Which of the following is a short-range, low-power, wireless network technology useful for remotely controlling industrial, medical, and home automation devices? A) Wi-Fi B) WiMAX C) UWB D) ZigBee Answer: D 53) Which of the following is a high-speed, medium-range, broadband wireless metropolitan area network? A) Wi-Fi B) WiMAX C) Bluetooth D) ZigBee Answer: B 54) Siri is a type of: A) intelligent personal assistant. B) widget. C) gadget. D) social network. Answer: A 55) The first Web browser to make it possible to view documents on the Web with colored background, images, and animations was: A) Netscape Navigator. B) Mosaic. C) Mozilla. D) Internet Explorer. Answer: B 56) In the address http://www.company.com/clients.html, which of the following is the toplevel domain? A) .com B) company.com C) www D) http Answer: A 57) You could expect to find all of the following services in a Web server software package except: A) security services. B) FTP. C) data capture. D) an RSS aggregator. Answer: D 58) Which of the following is currently the most popular Web browser? A) Internet Explorer B) Netscape C) Safari D) Firefox Answer: A 59) The concept behind document formatting had its roots in which of the following? A) XML B) SGML C) HTML D) GML Answer: D 60) Which of the following is a Web application that enables Internet users to communicate with each other, although not in real time? A) online chat B) online forum C) IM D) VoIP Answer: B 61) Which of the following is a Web 2.0 service or application? A) wikis B) e-mail C) IM D) online forums Answer: A 62) A(n) ________ is a Web application that allows users to easily add and edit content on a Web page. A) wiki B) podcast C) blog D) RSS feed Answer: A 63) The protocol that enables the transmission of voice and other forms of audio communication over the Internet is called: A) VoIP. B) IPTP. C) VTP. D) IP. Answer: A 64) Which of the following was the largest source of mobile commerce revenue in 2012? A) mobile advertising B) location-based services C) e-book sales D) mobile retail purchases Answer: D 65) All of the following are true about iPhone apps except: A) They are distributed through Apple's App Store. B) They are typically written in the Java programming language. C) They were estimated to generate over $2 billion in 2012. D) More than 30 billion have been downloaded. Answer: B E-commerce 2013, 9e (Laudon/Traver) Chapter 4 Building an E-commerce Presence: Web Sites, Mobile Sites, and Apps 1) The systems development life cycle methodology is useful when creating an e-commerce Web site. Answer: TRUE 2) One of the most important challenges in developing an e-commerce presence is understanding that the technology must drive the business. Answer: FALSE 3) Using prebuilt templates is typically one of the most cost-effective choices when building a Web site. Answer: TRUE 4) The annual maintenance cost for a Web site is likely to be as high as its development cost. Answer: TRUE 5) In a two-tier architecture, a Web server is linked to one middle-tier layer that typically includes a series of application servers, as well as to another back-end layer. Answer: FALSE 6) Apache HTTP Web server software is based on Microsoft's Windows operating system. Answer: FALSE 7) The Web server software used does not significantly impact how a Web site's Web pages look on users' computers. Answer: TRUE 8) Prior to the development of e-commerce, Web sites primarily delivered static content. Answer: TRUE 9) Dynamic page generation makes market segmentation easier. Answer: TRUE 10) A list server is an application server used to provide a database for product descriptions and prices. Answer: FALSE 11) Upgrading a server from a single processor to multiple processors is an example of scaling a site horizontally. Answer: FALSE 12) Storing HTML pages in RAM rather than on a server's hard drive is an inexpensive way to fine-tune the processing architecture of a Web site. Answer: TRUE 13) A "native" app is one designed to specifically operate using a mobile device's hardware and operating system. Answer: TRUE 14) Accessibility rules help to ensure that low-bandwidth users can access your Web site. Answer: FALSE 15) Mobile Web apps are typically built using HTML5 and Java. Answer: TRUE 16) What are the two most important management challenges in building a successful ecommerce presence? A) developing a clear understanding of business objectives and knowing how to choose the right technology to achieve those objectives B) having an accurate understanding of your business environment and an achievable business plan C) building a team with the right skill sets and closely managing the development process D) identifying the key components of your business plan and selecting the right software, hardware, and infrastructure for your site Answer: A 17) In order from beginning to end, the major steps in the SDLC, are: A) systems analysis/planning; systems design; building the system; testing; and implementation. B) systems design; testing; building the system; and implementation. C) systems analysis/planning; systems design; building the system; implementation; and testing. D) systems analysis/planning; implementation; building the system; and testing. Answer: A 18) ________ are the types of information systems capabilities needed to meet business objectives. A) Information requirements B) System functionalities C) System design specifications D) Physical design specifications Answer: B 19) Which of the following basic system functionalities is used to display goods on a Web site? A) product database B) digital catalog C) shopping cart system D) customer database system Answer: B 20) Which system functionality must your Web site have in order to be able to personalize or customize a product for a client? A) an ad server B) a site tracking and reporting system C) an inventory management system D) customer on-site tracking Answer: D 21) A system design has two main components: A) a logical design and a physical design. B) a behavioral design and a technological design. C) business objectives and technology requirements. D) front-end systems and back-end systems. Answer: A 22) Which of the following helps you understand the marketing effectiveness of your ecommerce site? A) shopping cart B) product database C) site tracking and reporting system D) inventory management system Answer: C 23) Which of the following is not one of the basic business objectives for an e-commerce site? A) display goods B) execute a transaction C) provide production and supplier links D) optimize system architecture Answer: D 24) All of the following are basic information requirements for a product database except: A) product descriptions. B) stock numbers. C) customer ID numbers. D) inventory levels. Answer: C 25) Which of the following typically includes a data flow diagram to describe the flow of information for a Web site? A) physical design B) logical design C) testing plan D) co-location plan Answer: B 26) Which of the following details the actual hardware components to be used in a system? A) architecture plan B) system functionalities plan C) logical design D) physical design Answer: D 27) ________ verifies that the business objectives of the system as originally conceived are in fact working. A) System testing B) Acceptance testing C) Unit testing D) Implementation testing Answer: B 28) ________ involves testing a site program's modules one at a time. A) System testing B) Acceptance testing C) Unit testing D) Implementation testing Answer: C 29) Most of the time required to maintain an e-commerce site is spent on: A) debugging code. B) responding to emergency situations. C) general administration and making changes and enhancements to the system. D) changes in reports, data files, and links to backend databases. Answer: C Diff: 2 Page Ref: 214 AACSB: Reflective Thinking 30) An e-commerce site that cost $25,000 to develop is likely to require a yearly maintenance budget of approximately: A) $5,000. B) $10,000. C) $25,000. D) $50,000. Answer: C 31) All of the following are simple steps for optimizing Web page content that can reduce response times except: A) reducing unnecessary HTML comments. B) segmenting computer servers to perform dedicated functions. C) using more efficient graphics. D) avoiding unnecessary links to other pages on the site. Answer: B 32) All of the following can enhance page delivery speed except: A) using edge caching services. B) using specialized content delivery networks. C) increasing local bandwidth. D) increasing the dynamic content on the pages. Answer: D 33) All of the following might be part of a Web site's backend layer except: A) a pre-existing corporate database. B) a human resources system. C) a production MRP system. D) an application server. Answer: D 34) All of the following might be part of a Web site's middle-tier layer except: A) a database server. B) an ad server. C) legacy corporate applications. D) a mail server. Answer: C 35) The leading Web server software is: A) Apache. B) Microsoft Internet Information Server. C) Linux. D) Google Enterprise Server. Answer: A 36) All of the following are basic functionality provided by Web servers except: A) site management tools. B) data capture tools. C) security services. D) a shopping cart. Answer: D 37) Which of the following is used to process certificates and private/public key information? A) HTTP B) SSL C) FTP D) data capture tools Answer: B 38) Which of the following would you use to identify orphan files? A) HTTP B) FTP C) data capture tools D) site management tools Answer: D 39) Which of the following is an example of a CMS? A) Apache B) WordPress C) Oracle D) WebTrends Analytics Answer: B 40) Advantages of dynamic page generation include all of the following except: A) lowered menu costs. B) market segmentation. C) nearly cost-free price discrimination. D) client-side execution of programming. Answer: D 41) Which of the following cannot be used to retrieve objects from a database? A) CGI B) ASP C) JSP D) HTML Answer: D 42) Which of the following types of servers monitors and controls access to a main Web server and implements firewall protection? A) proxy server B) list server C) groupware server D) mail server Answer: A 43) Which of the following technologies could you use to place the content of your Web site in a database so that you can then dynamically generate requests for pages? A) Apache web server B) proxy server C) shopping cart D) CMS Answer: D 44) Which of the following is not a type of application server? A) proxy server B) mail server C) ad server D) FTP server Answer: D 45) All of the following are basic functionality provided by e-commerce merchant server software except: A) a product catalog. B) marketing software. C) a shopping cart. D) credit card processing. Answer: B 46) Which of the following is not one of the main factors in Web site optimization? A) page content B) page generation C) page delivery D) page stickiness Answer: D 47) An e-commerce Web site that processes orders requires, at minimum, a ________ system architecture. A) single-tier B) two-tier C) three-tier D) multi-tier Answer: B 48) All of the following are Web site design features that annoy customers except: A) slow-loading pages. B) pop-under ads. C) splash pages. D) redundant navigation. Answer: D 49) Which of the following is not an open source software tool? A) WebSphere B) Apache C) MySQL D) PHP Answer: A 50) The term stateless refers to the fact that: A) no one government entity controls the Internet. B) the server does not have to maintain an ongoing dedicated interaction with the client computer. C) system performance degrades as more simultaneous users require service. D) Web servers may maintain multiple instances of server software to handle requests. Answer: B 51) Which of the following is not an activity typically associated with a social media ecommerce presence? A) search B) conversation C) sharing D) advice Answer: A 52) Which of the following types of sites typically tends to have high to very high page views (hits)? A) Web services B) customer self-service C) trading D) publishing/subscription Answer: D 53) Which of the following types of sites typically needs a high percent of secure pages? A) Web services B) customer self-service C) trading D) publishing/subscription Answer: C 54) Which of the following is not a main factor in determining overall demand for an ecommerce site? A) static file sizes B) number of items in inventory C) user profiles D) type of content Answer: A 55) The cost of hardware, software, and telecommunications services needed to build a Web site have ________ over the last decade. A) increased dramatically B) increased moderately C) decreased dramatically D) decreased slightly Answer: C 56) Which of the following is the final stage suggested for a six-phase plan to develop an ecommerce presence? A) mobile plan B) maintenance C) testing plan D) Twitter plan Answer: A 57) Which of the following is not an example of one of the four kinds of e-commerce presence? A) e-mail list B) customer management system C) Twitter feed D) print ad that refers to a Web site Answer: B Diff: 2 Page Ref: 201 AACSB: Reflective Thinking 58) All of the following are steps one can take to right-size a Web site's hardware platform and meet demands for service except: A) scaling hardware vertically. B) scaling hardware horizontally. C) replacing static pages with dynamically generated pages. D) improving processing architecture. Answer: C 59) All of the following are methods of improving the processing architecture of a Web site except: A) separating static content from dynamic content. B) optimizing ASP code. C) optimizing the database schema. D) adding Web servers. Answer: D 60) Which of the following is the least expensive path to creating a mobile Internet presence? A) developing a native app B) resizing an existing Web site for mobile use C) building a mobile Web app using HTML D) building a mobile Web app using Java Answer: B 61) All of the following are important factors in Web site optimization except: A) selecting keywords and page titles. B) identifying market niches for your services or products. C) buying search engine ads. D) adhering to accessibility guidelines. Answer: D 62) ________ provides a set of standards for communicating between a browser and a program running on a server that allows for interaction between the user and server. A) CGI B) ColdFusion C) JavaScript D) VBScript Answer: A 63) ________ is a programming language invented by Netscape used to control the objects on an HTML page and handle interactions with the browser. A) VBScript B) ActiveX C) ColdFusion D) JavaScript Answer: D 64) The primary way a Web site is able to personalize the content presented to a visitor is through the use of: A) privacy policies. B) cookies. C) accessibility rules. D) site management tools. Answer: B 65) Which of the following is an example of dynamic content? A) product photographs B) product descriptions C) home page graphic D) blog posts Answer: D E-commerce 2013, 9e (Laudon/Traver) Chapter 5 E-commerce Security and Payment Systems 1) Typically, the more security measures added to a Web site, the slower and more difficult it becomes to use. Answer: TRUE 2) A worm does not need to be activated by a user in order for it to replicate itself. Answer: TRUE 3) A Trojan horse appears to be benign, but then does something other than expected. Answer: TRUE 4) Phishing attacks rely on browser parasites. Answer: FALSE 5) Insiders present a greater security threat to e-commerce sites than outsiders. Answer: TRUE 6) The use of a digital signature helps to ensure integrity, authenticity, and nonrepudiation. Answer: TRUE 7) Drive-by downloads are now the most common method of infecting computers. Answer: TRUE 8) Smishing attacks exploit SMS messages. Answer: TRUE 9) TLS does not guarantee server-side authentication. Answer: FALSE 10) The easiest and least expensive way to prevent threats to system integrity is to install antivirus software. Answer: TRUE 11) The United States federal government has historically not been in favor of the development and export of strong encryption systems. Answer: TRUE 12) Credit cards are the dominant form of online payment throughout the world. Answer: FALSE 13) In order to accept payments by credit card, online merchants typically must have a merchant account established with a bank or financial institution. Answer: TRUE 14) Digital cash is legal tender that is instantly convertible into other forms of value without the intermediation of any third parties. Answer: FALSE 15) PayPal requires the recipient of a payment to have a PayPal account to receive funds. Answer: TRUE 16) All of the following are factors in contributing to the increase in cybercrime except: A) the ability to remotely access the Internet. B) the Internet's similarity to telephone networks. C) the ability to anonymously access the Internet. D) the Internet is an open, vulnerable design. Answer: B 17) The Computer Security Institute reported in its 2011 survey that approximately ________ percent of responding organizations experienced a computer security incident within the previous 12 months. A) 25 B) 45 C) 75 D) 95 Answer: B 18) The overall rate of online credit card fraud is ________ percent of all online card transactions. A) less than 1 B) around 1 C) around 5 D) around 10 Answer: A 19) According to the Computer Security Institute's 2011 Computer Crime and Security Survey, which of the following was the most commonly reported type of attack? A) malware infection B) laptop theft C) Web site defacement D) insider abuse Answer: A 20) The six key dimensions to e-commerce security are nonrepudiation, authenticity, availability, integrity, privacy, and: A) confidentiality. B) usability. C) functionality. D) viability. Answer: A 21) ________ refers to the ability to ensure that e-commerce participants do not deny their online actions. A) Nonrepudiation B) Authenticity C) Availability D) Integrity Answer: A 22) ________ refers to the ability to identify the person or entity with whom you are dealing on the Internet. A) Nonrepudiation B) Authenticity C) Availability D) Integrity Answer: B 23) Which of the following is an example of an integrity violation of e-commerce security? A) A Web site is not actually operated by the entity the customer believes it to be. B) A merchant uses customer information in a manner not intended by the customer. C) A customer denies that he or she is the person who placed the order. D) An unauthorized person intercepts an online communication and changes its contents. Answer: D 24) ________ refers to the ability to ensure that an e-commerce site continues to function as intended. A) Nonrepudiation B) Authenticity C) Availability D) Integrity Answer: C 25) An example of a privacy violation of e-commerce security is: A) your e-mail being read by a hacker. B) your online purchasing history being sold to other merchants without your consent. C) your computer being used as part of a botnet. D) your e-mail being altered by a hacker. Answer: B 26) ________ refers to the ability to ensure that messages and data are only available to those authorized to view them. A) Confidentiality B) Integrity C) Privacy D) Availability Answer: A 27) Which of the following is not a key point of vulnerability when dealing with e-commerce? A) the client computer B) the server C) the communications pipeline D) the credit card companies Answer: D 28) All of the following were computer crimes committed in 2011-2012 except: A) Russian hackers posting over 6 million Facebook usernames and passwords online. B) 77 million user credit card numbers stolen from Sony's PlayStation gameserver. C) A Stuxnet worm wiped computers in the Iranian Oil Ministry clean. D) Melissa worm spreads through Microsoft Word templates. Answer: D 29) Which of the following is a prominent hacktivist group? A) Anonymous B) Anti-Phishing Working Group C) IC3 D) Symantec Answer: A 30) Most of the world's spam is delivered via which of the following? A) viruses B) worms C) Trojan horses D) botnets Answer: D 31) Botnets are typically used for all of the following except: A) DDoS attacks. B) phishing attacks. C) storing network traffic for analysis. D) stealing information from computers. Answer: B 32) Software that is used to obtain private user information such as a user's keystrokes or copies of e-mail is referred to as: A) spyware. B) a backdoor. C) pupware. D) adware. Answer: A 33) The Conficker worm targeted: A) Microsoft Word. B) Microsoft Outlook Express. C) Microsoft operating systems. D) Microsoft Access database software. Answer: C 34) Netsky.P, which spreads by sending e-mails from an infected computer to all of the e-mail addresses found on that infected computer, is an example of a: A) macro virus. B) worm/Trojan horse. C) Trojan horse/virus. D) bot program. Answer: B 35) What is the most frequent cause of stolen credit cards and card information today? A) lost cards B) the hacking and looting of corporate servers storing credit card information C) sniffing programs D) phishing attacks Answer: B 36) Which dimension(s) of security is spoofing a threat to? A) integrity B) availability C) integrity and authenticity D) availability and integrity Answer: C 37) All of the following are examples of malicious code except: A) viruses. B) bots. C) worms. D) sniffers. Answer: D 38) Symmetric key encryption is also known as: A) public key encryption. B) secret key encryption. C) PGP. D) PKI. Answer: B 39) All the following statements about symmetric key encryption are true except: A) In symmetric key encryption, both the sender and the receiver use the same key to encrypt and decrypt a message. B) The Data Encryption Standard is a symmetric key encryption system. C) Symmetric key encryption is computationally slower. D) Symmetric key encryption is a key element in digital envelopes. Answer: C 40) The Data Encryption Standard uses a(n) ________-bit key. A) 8 B) 56 C) 256 D) 512 Answer: B 41) All of the following statements about public key encryption are true except: A) Public key encryption uses two mathematically related digital keys. B) Public key encryption ensures authentication of the sender. C) Public key encryption does not ensure message integrity. D) Public key encryption is based on the idea of irreversible mathematical functions. Answer: B 42) If you used a symmetric key encryption for large documents, with public key encryption to encrypt and send the symmetric key, you would be using a digital: A) envelope. B) signature. C) certificate. D) hash. Answer: A 43) All of the following statements about PKI are true except: A) The term PKI refers to the certification authorities and digital certificate procedures that are accepted by all parties. B) PKI is not effective against insiders who have a legitimate access to corporate systems including customer information. C) PKI guarantees that the verifying computer of the merchant is secure. D) The acronym PKI stands for public key infrastructure. Answer: C 44) A digital certificate contains all of the following except the: A) subject's private key. B) subject's public key. C) digital signature of the certification authority. D) digital certificate serial number. Answer: A 45) Which of the following dimensions of e-commerce security is not provided for by encryption? A) confidentiality B) availability C) message integrity D) nonrepudiation Answer: B 46) All of the following are methods of securing channels of communication except: A) SSL/TLS. B) certificates. C) VPN. D) FTP. Answer: D 47) A ________ is hardware or software that acts as a filter to prevent unwanted packets from entering a network. A) firewall B) virtual private network C) proxy server D) PPTP Answer: A 48) Proxy servers are also known as: A) firewalls. B) application gateways. C) dual home systems. D) packet filters. Answer: C 49) All of the following are used for authentication except: A) digital signatures. B) certificates of authority. C) biometric devices. D) packet filters. Answer: D 50) What is the first step in developing an e-commerce security plan? A) Create a security organization. B) Develop a security policy. C) Perform a risk assessment. D) Perform a security audit. Answer: C 51) What is the last step in developing an e-commerce security plan? A) Perform a security audit. B) Develop an implementation plan. C) Create a security organization. D) Develop a security policy. Answer: A 52) Which of the following is not an example of an access control? A) firewalls B) proxy servers C) digital signatures D) login passwords Answer: C 53) Which of the following is the primary federal statute used to combat computer crime? A) Homeland Security Act B) CAN-SPAM Act C) Computer Security Enhancement Act D) Computer Fraud and Abuse Act Answer: D 54) To allow lower-level employees access to the corporate network while preventing them from accessing private human resources documents, you would use: A) access controls. B) an authorization management system. C) security tokens. D) an authorization policy. Answer: B 55) All of the following are features of cash except: A) It is instantly convertible into other forms of value without intermediation. B) It requires no authentication. C) It is anonymous. D) It provides float. Answer: D 56) All the following are stakeholders in payment systems except: A) ISPs. B) consumers. C) financial intermediaries. D) government regulators. Answer: A 57) P2P payment systems are a variation on what type of payment system? A) stored value payment system B) digital checking system C) accumulating balance system D) digital credit card system Answer: A 58) All of the following statements about debit cards are true except: A) Debit cards eliminate the need for consumers to write a paper check when making a purchase. B) Debit cards enable consumers to make purchases even if they do not have sufficient funds at the time of purchase. C) Debit cards do not provide any float. D) Debit cards do not have the protections provided by Regulation Z to credit cards. Answer: B 59) All of the following are examples of stored value payment systems except: A) smart cards. B) credit cards. C) gift certificates. D) prepaid cards. Answer: B 60) None of the following payment systems offers immediate monetary value except: A) personal checks. B) credit cards. C) stored value/debit card. D) accumulating balance. Answer: C 61) Malware that comes with a downloaded file that a user requests is called a: A) Trojan horse. B) backdoor. C) drive-by download. D) PUP. Answer: C 62) Which of the following is not an example of a PUP? A) adware B) browser parasite C) drive-by download D) spyware Answer: C 63) All of the following are limitations of the existing online credit card payment system except: A) poor security. B) cost to consumers. C) cost to merchant. D) social equity. Answer: B 64) Linden Dollars, created for use in Second Life, are an example of: A) digital cash. B) virtual currency. C) EBPP D) peer-to-peer payment systems. Answer: B Diff: 2 Page Ref: 319 AACSB: Reflective Thinking 65) Which of the following is a set of short-range wireless technologies used to share information among devices within about 2 inches of each other? A) DES B) NFC C) IM D) text messaging Answer: B E-commerce 2013, 9e (Laudon/Traver) Chapter 6 E-commerce Marketing Concepts: Social, Mobile, Local 1) In the United States today, single, white, young college-educated males with high income dominate the Internet in terms of percentage of Internet usage. Answer: FALSE 2) Households with incomes of below $75,000 are obtaining Internet access at faster rates than households with incomes above that level. Answer: TRUE 3) Price is the top factor in online purchase decisions. Answer: TRUE 4) E-commerce is a major conduit and generator of offline commerce. Answer: TRUE 5) Online shoppers tend to browse for available products rather than search for specific products they have determined in advance. Answer: FALSE 6) Research shows that the two most important factors shaping the decision to purchase online are utility and trust. Answer: TRUE 7) In 2012, mobile marketing grew at nearly the same rate as traditional online marketing. Answer: FALSE 8) Evidence suggests that real-time customer chat increases sales. Answer: TRUE 9) Transaction logs are built into Web server software. Answer: TRUE 10) Cookies, when combined with Web beacons, can be used to create cross-site profiles. Answer: TRUE 11) The four generic market entry strategies are first mover, fast follower, slow follower, and pure play. Answer: FALSE 12) Online banking is more popular with men than with women. Answer: TRUE 13) The marginal cost of the production of information goods distributed over the Internet is zero or near zero. Answer: TRUE 14) Versioning involves selling the same product at different prices. Answer: FALSE 15) Bundling is the process of selling two or more products together for a price that is less than the sum of the two product's individual prices. Answer: TRUE 16) On a typical day, approximately ________ percent of adult users in the United States logs on to the Internet. A) 52 B) 62 C) 72 D) 82 Answer: D 17) Which of the following activities is the one engaged in by the highest percentage of online users? A) using e-mail B) using a social networking site C) researching products and services D) reading news Answer: A 18) On average, which of the following activities was most frequently engaged in by Internet users in 2012? A) checking the weather B) banking online C) buying a product D) rating a product Answer: A 19) The dial-up audience is ________ the broadband audience. A) virtually indistinguishable from B) more educated than C) less intensely involved with the Internet than D) wealthier than Answer: C 20) Which of the following age groups has the highest percentage of Internet access? A) 18-29 B) 30-49 C) 50-64 D) 65+ Answer: A 21) Which of the following demographic groups had the greatest increase in Internet access between 2002 and 2012? A) Black, non-Hispanic B) Asians C) White, non-Hispanic D) Hispanic Answer: A 22) Which of the following age groups had the lowest percentage of Internet access in 2012? A) 18-29 B) 30-49 C) 50-64 D) 65+ Answer: D 23) In 2012, what was the approximate Internet penetration rate for individuals that have attained less than a high-school education? A) 45 percent B) 60 percent C) 75 percent D) 90 percent Answer: B 24) Toyota's use of the Internet to target Hispanic customers is an example of targeting a specific: A) lifestyle group. B) culture. C) subculture. D) psychological profile. Answer: C 25) A person's profession or occupation is part of their: A) indirect reference group. B) direct reference group. C) lifestyle group. D) subculture. Answer: B 26) Which of the following is an example of an indirect reference group? A) social class B) family C) religion D) profession Answer: A 27) A(n) ________ profile describes an individual's set of needs, drives, motivations, perceptions and learned behaviors. A) psychographic B) opinion C) psychological D) lifestyle Answer: C 28) All of the following are online communications that are used to support the evaluation of alternatives stage of the consumer decision process except: A) search engines. B) online catalogs. C) social networks. D) targeted banner ads. Answer: D 29) "Shoppers" constitute approximately ________ percent of the online Internet audience. A) 38 B) 68 C) 88 D) 98 Answer: C 30) Small ticket item sales outnumbered large ticket item sales during the early days of e- commerce for all of the following reasons except: A) Purchase price was low. B) Items were physically small. C) Margins were low. D) Selection was broad. Answer: C 31) Which of the following is the top concern of Internet users about purchasing online? A) inability to see and touch before buying B) difficulty of returning products C) shipping costs D) inability to speak to sales assistant in person Answer: A 32) Studies of the effects of social "connectedness" on Internet purchases indicate that the more "connected" an individual: A) the less purchasing that individual does. B) the less that individual is influenced by friends' purchases. C) the more that individual shares purchasing decisions with friends. D) the more purchasing that individual does. Answer: B 33) The broadest factor in consumer behavior is: A) culture. B) gender. C) education. D) psychological background. Answer: A 34) In modeling online consumer behavior, consumer skills refers to the: A) education level of the consumer. B) communication skills of the consumer. C) knowledge consumers have about how to conduct online transactions. D) product evaluation skills of the consumer. Answer: C 35) All of the following are important clickstream behavior factors except: A) the number of days since last visit. B) the speed of clickstream behavior. C) the amount of personal information supplied. D) the number of advertisements viewed. Answer: D 36) Approximately ________ in annual offline retail sales is influenced by online browsing. A) $1.2 trillion B) $102 billion C) $120 million D) $12 million Answer: A 37) Which of the following types of online market segmentation and targeting involves using age, ethnicity, religion, etc.? A) psychographic B) demographic C) technical D) contextual Answer: B 38) Which of the following types of online market segmentation and targeting involves using consumers' explicitly expressed interest to segment and target? A) psychographic B) technical C) search D) contextual Answer: C 39) Which of the following types of online market segmentation and targeting involves tracking the actions users take on a Web site? A) technical B) behavioral C) contextual D) psychographic Answer: B 40) Which of the following is not one of the main elements of a comprehensive multi-channel marketing plan? A) local marketing B) offline marketing C) social marketing D) mobile marketing Answer: A 41) All of the following statements are true except: A) Online merchants can avoid direct price comparison by introducing information asymmetries into the marketplace. B) Relative dispersion of prices for online goods has decreased. C) Price dispersion is less for commodities than for differentiated products. D) Depending on the seller, there can be large differences in price sensitivity for the same products. Answer: B 42) Which of the following statements about the Internet's impact on marketing is not true? A) The Internet has broadened the scope of marketing communications. B) The Internet has decreased the impact of brands. C) The Internet has increased the richness of marketing communications. D) The Internet has expanded the information intensity of the marketplace. Answer: B 43) Which of the following features of e-commerce technology has reduced the cost of delivering marketing messages and receiving feedback from users? A) ubiquity B) richness C) interactivity D) universal standards Answer: D 44) Which of the following features of e-commerce technology allows fine-grained, highly detailed information on consumers' real-time behavior to be gathered and analyzed? A) personalization/customization B) information density C) social technology D) interactivity Answer: B 45) The richness made possible by e-commerce technologies does which of the following? A) It reduces the cost of delivering marketing messages and receiving feedback from users. B) It allows consumers to become co-producers of the goods and services being sold. C) It allows video, audio, and text to be integrated into a single marketing message and consuming experience. D) It enables worldwide customer service and marketing communications. Answer: C 46) For a Web site that has 5 million visitors a month, and where on average, a visitor makes 10 page requests per visit, there will be ________ entries in the transaction log each month. A) 50 B) 500,000 C) 5 million D) 50 million Answer: D 47) Which of the following is not a social marketing technique? A) Pinterest marketing B) app marketing C) game marketing D) video marketing Answer: B 48) All of the following statements about cookies are true except: A) Cookies can be used with Web bugs to create cross-site profiles of users. B) The data typically stored in cookies includes a unique ID and e-mail address. C) Cookies make shopping carts possible by allowing a site to keep track of a user's actions. D) The more cookies are deleted, the less accurate ad server metrics become. Answer: B 49) A Web beacon is: A) a cookie that carries a virus. B) an executable cookie. C) an automated applet for performing Web searches. D) a tiny graphics file embedded in an e-mail or Web page. Answer: D 50) ________ is an industry-standard database query and manipulation language. A) SQL B) PHP C) DBMS D) JSP Answer: A 51) All of the following are traditional online marketing tools except: A) affiliate marketing. B) permission marketing. C) social marketing. D) sponsorship marketing. Answer: C 52) Which of the following examples illustrates the "Long Tail" phenomenon? A) Rhapsody music streaming service reported that its no play rate had increased to over 20 percent. B) The number of blockbuster "winner take all" video titles is declining. C) Over 50 percent of Netflix's 100,000 titles are rented at least once a day by someone. D) The average blog has a readership of slightly more than 1. Answer: C 53) A ________ is a repository of customer information that records all of the contacts that a customer has with a firm and generates a customer profile available to everyone in the firm with a need to know the customer. A) customer service chat system B) CRM system C) data warehouse D) transactive content system Answer: B 54) Netflix entered the market with a(n) ________ strategy. A) brand extender B) fast follower C) first mover D) alliance Answer: C 55) Walmart used which of the following market entry strategies? A) first mover B) strategic alliance C) fast follower D) brand extender Answer: D 56) The marketing technique known as ________ involves merchants offering products or services for a very low price for a short period of time. A) search engine marketing B) flash marketing C) yield management D) bait-and-switch Answer: B 57) Which of the following is not a kind of Twitter marketing product? A) Promoted Shopping B) Promoted Tweets C) Promoted Accounts D) Promoted Trends Answer: A 58) Which of the following is not a feature that is driving social e-commerce growth? A) social sign-on B) network notification C) collaborative shopping D) personal intelligent agents Answer: D 59) Permission marketing: A) is a component of e-mail marketing. B) is required now by federal law via "opt-in" regulations. C) allows Web site users to "turn off" display ads. D) is a method of pre-approved marketing to juveniles. Answer: A 60) All of the following are attributes of personalized marketing except: A) suitable for highly complex products. B) unique price. C) targeting of individuals. D) use of mass media. Answer: D 61) The Nike iD program is an example of which of the following marketing techniques? A) customer co-production B) transactive content C) price discrimination D) permission marketing Answer: A 62) The incremental cost of building the next unit of a good is called the: A) demand curve. B) variable cost. C) marginal cost. D) fixed cost. Answer: C 63) Which of the following statements about a free pricing strategy is false? A) Free products and services can knock out potential and actual competitors. B) The free pricing strategy was born in the early days of the Web. C) It is difficult to convert free customers into paying customers. D) Free products and services can help build market awareness. Answer: B 64) Creating multiple variations of information goods and selling these to different market segments at different prices is called: A) bundling. B) customization. C) dynamic pricing. D) versioning. Answer: D 65) All of the following are fixed price strategies except: A) bundling. B) versioning. C) free pricing. D) yield management. Answer: D E-commerce 2013, 9e (Laudon/Traver) Chapter 7 E-commerce Marketing Communications 1) The sole purpose of marketing communications is sales. Answer: FALSE 2) Online video advertising now accounts for the largest amount of the Internet advertising spending. Answer: FALSE 3) The growth rate of search engine advertising is slowing compared to other formats. Answer: TRUE 4) The amount spent on online advertising in 2012 accounts for approximately 10 percent of the total amount spent on all advertising. Answer: FALSE 5) Online advertising methods include sponsorships, e-mail marketing, and referrals. Answer: TRUE 6) Search engine marketing saves consumers cognitive energy and reduces search costs. Answer: TRUE 7) Sending e-mail marketing messages is typically less costly than sending direct mail marketing messages. Answer: TRUE 8) A majority of states in the United States have laws regulating or prohibiting spam. Answer: TRUE 9) The 2003 CAN-SPAM Act required that the Federal Trade Commission establish a "do not email" registry. Answer: FALSE 10) Studies have shown that the most successful marketing campaigns concentrate efforts along a single marketing channel. Answer: FALSE 11) Spending on social advertising is less than 10 percent of spending on all online advertising. Answer: TRUE 12) Research indicates that social network influence may not extend to distant friends. Answer: TRUE 13) Interest-based advertising is another name for behavioral targeting. Answer: TRUE 14) Display ads produce the highest click-through rates. Answer: FALSE 15) In general, the costs for offline customer acquisition are lower than online, but more effective. Answer: FALSE 16) Which of the following is an example of "pull" advertising? A) search engine ads B) spam C) pop-ups D) interstitials Answer: A 17) Which of the following is not one of the current trends in Internet advertising? A) Spending on search engine advertising is overtaken by video ads. B) Online ad spending grows as a share of the total advertising budget. C) Mobile and local advertising expands. D) Display ad marketing continues strong growth. Answer: A 18) Which of the following advertising messages is a branding communication? A) Try Adobe Acrobat Professional 10 free for 30 days. B) Free shipping on every item we sell. Buy two or more items to qualify. C) Barnesandnoble.com: The Best Place to Buy Textbooks. D) 50 percent off all calendars. Shop now while supplies last. Answer: C 19) The amount spent on online advertising in 2012 was approximately: A) $373 million. B) $3.73 billion. C) $37.3 billion. D) $373 billion. Answer: C 20) Which of the following is not one of the advantages of online advertising? A) The Internet is where the audience is moving. B) Online ads provide for greater interactivity with the customer. C) Online costs versus benefits are well established and understood. D) Online advertising can target ads to narrow market segments. Answer: C 21) Which of the following online advertising formats is the most effective? A) banner ads B) rich media ads C) video ads D) e-mail Answer: C 22) Which of the following online advertising formats attracted the least amount of spending in 2012? A) search B) classifieds C) rich media D) e-mail Answer: D 23) Which of the following forms of online advertising is growing the fastest? A) paid search B) sponsorships C) video D) rich media Answer: C 24) The size of a leaderboard is: A) 728 × 90 pixels. B) 300 × 600 pixels. C) 160 × 600 pixels. D) 180 × 150 pixels. Answer: A 25) If you want to determine the size of your Web site's audience, the metric you will use for the most accurate measurement will be: A) page views. B) unique visitors. C) hits. D) reach. Answer: B 26) Which of the following types of display ads is 160 × 600 pixels? A) leaderboard B) half-page ad C) medium rectangle D) wide skyscraper Answer: D 27) All of the following statements about interstitials are true except: A) Interstitials typically appear as a user moves from one page to another. B) Interstitials typically last 30 seconds. C) Interstitials are full-page messages. D) Interstitials can be deployed over an advertising network. Answer: B 28) Which of the following is not one of the four main methods advertisers use to behaviorally target ads? A) Nielsen ratings B) data collected from social networks C) integration of offline data D) clickstream data Answer: A 29) Search engine advertising expenditures in 2012 were approximately: A) $17 million. B) $170 million. C) $1.7 million. D) $17 billion. Answer: C 30) Which of the following is not true about search engine advertising? A) Spending on search engine advertising constitutes around 46 percent of all online advertising spending. B) The top three search engine providers supply over 95 percent of all online searches. C) The click-through rate for search engine marketing has been fairly steady over the years. D) Search engine advertising is the fastest growing type of online advertising. Answer: D 31) Research studies have shown that viewers scan search engine results pages: A) in an "F" shaped pattern with greater attention to the left side of the page. B) in an inverted "T" pattern with greater attention to the left side of the page. C) from top to bottom, with little consideration for elements along either margin of the page. D) from top to bottom, with the greatest attention to the right side of the page. Answer: A 32) Which of the following is not a practice that degrades the results and usefulness of search engines? A) social search B) link farms C) content farms D) click fraud Answer: A 33) A Crayola arts-and-crafts column on a parenting Web site is an example of what form of advertising? A) sponsorship B) banner swapping C) affiliate relationship D) public relations Answer: A 34) A typical response rate for an e-mail campaign would be ________ percent. A) 2 B) 5 C) 25 D) 50 Answer: B 35) Legitimate e-mail addresses based on a high-quality commercial opt-in e-mail list might cost ________ per thousand. A) 50 cents to $1 B) $5 to $10 C) $50 to $100 D) $500 to $1000 Answer: B 36) The percentage of all e-mail that is spam was approximately ________ percent in 2012. A) 30 B) 50 C) 70 D) 90 Answer: C 37) All of the following statements about CAN-SPAM are true except: A) CAN-SPAM went into effect in January 2004. B) CAN-SPAM prohibits unsolicited e-mail (spam). C) CAN-SPAM prohibits the use of deceptive subject lines and false headers. D) Large spammers are among CAN-SPAM's biggest supporters. Answer: B 38) CAN-SPAM imposes fines of ________ for each unsolicited pornographic e-mail. A) $1 B) $10 C) $100 D) $1000 Answer: B 39) Direct e-mail marketing refers to marketing e-mails sent to: A) recipients who have expressed an interest in receiving messages from that advertiser. B) any recipient from a verifiable company e-mail address. C) recipients who have signed on to a company's e-mail list. D) recipients with known names and addresses. Answer: A 40) Promoted Trends is an example of which of the following types of online advertising? A) blog advertising B) interest-based advertising C) game advertising D) social network advertising Answer: D 41) Which of the following generated the most social advertising revenues in 2012? A) MySpace B) YouTube C) Twitter D) Facebook Answer: D 42) Axe's posting of video ads online that were subsequently forwarded and shared by millions of Internet users is an example of: A) referral marketing. B) nonlinear video advertisement. C) behavioral targeting. D) viral marketing. Answer: D 43) Impressions are a measure of the: A) number of times an ad is clicked. B) number of times an ad is served. C) number of http requests. D) number of pages viewed. Answer: B 44) View-through rate measures the ________ response rate to an ad. A) 30-minute B) 24-hour C) 7-day D) 30-day Answer: D 45) Hits are a measure of the: A) number of times an ad is clicked. B) number of times an ad is served. C) number of http requests. D) number of pages viewed. Answer: C 46) CTR is a measure of the: A) percentage of times an ad is clicked. B) number of times an ad is served. C) number of http requests. D) number of pages viewed. Answer: A 47) Which of the following measures the average length of stay at a Web site? A) loyalty B) stickiness C) recency D) retention rate Answer: B 48) Acquisition rate is a measure of the: A) percentage of visitors who indicate an interest in a site's products by registering or visiting a product's pages. B) percentage of visitors who become customers. C) percentage of existing customers who continue to buy on a regular basis. D) percentage of shoppers who do not return within a year after their initial purchase. Answer: A 49) Recency refers to the: A) percentage of customers who do not return during the next year after an initial purchase. B) time elapsed since the last action taken by a customer. C) percentage of existing customers who continue to buy on a regular basis. D) percentage of customers who return to the site within a year to make additional purchases. Answer: B 50) Conversion rate is a measure of the: A) percentage of visitors who indicate an interest in a site's products by registering or visiting a product's pages. B) percentage of visitors who become customers. C) percentage of existing customers who continue to buy on a regular basis. D) percentage of shoppers who do not return within a year after their initial purchase. Answer: B 51) Which of the following measures the ratio of items purchased to product views? A) conversion rate B) cart conversion rate C) browse-to-buy ratio D) view-to-cart ratio Answer: C 52) Which of the following measures the ratio of actual orders to checkouts started? A) checkout conversion rate B) conversion rate C) acquisition rate D) cart conversion rate Answer: A 53) In ________ advertising, companies pay for ads to be placed dynamically on any participating Web site that the search engine determines is appropriate. A) paid inclusion B) network keyword C) keyword D) social Answer: B 54) Typical click-through rates for an online display ad are: A) .02%-.16%. B) .03%-.30%. C) 1.5%-2%. D) 3%-6%. Answer: B 55) Which of the following forms of online advertising typically has the highest click-through rate? A) e-mail marketing in-house list B) interstitials C) search engine keyword purchase D) sponsorships Answer: C 56) The typical dwell rate for rich media and video ads is: A) 1%-2%. B) 4%-5%. C) 7%-8%. D) 10%-12%. Answer: C 57) Purchasing an online ad on a CPA basis means that the advertiser: A) pays for impressions in 1,000 unit lots. B) pays a prenegotiated fee for each click an ad receives. C) pays only for those users who perform a specific action, such as registering, purchasing, etc. D) exchanges something of equal value for the ad space. Answer: C 58) Purchasing an online ad on a CPC basis means that the advertiser: A) pays for impressions in 1,000 unit lots. B) pays a prenegotiated fee for each click an ad receives. C) pays only for those users who perform a specific action, such as registering, purchasing, etc. D) exchanges something of equal value for the ad space. Answer: B 59) A typical banner ad might cost ________ per 1,000 impressions. A) 5 cents B) $5 C) $50 D) $500 Answer: B 60) The most expensive form of online advertising on a per thousand viewer basis is a(n): A) exclusive sponsorship arrangement. B) e-mail campaign. C) banner ad. D) rich media ad. Answer: A 61) All of the following are true statements about the choice of a domain name except: A) A domain name should be short. B) Domain names play an important role in reinforcing an existing brand and developing a new brand. C) Having a dot-com domain is no longer considered preferable, especially in the United States. D) It is possible to buy domain names. Answer: C 62) According to the Fogg et al. 2003 study, which of the following is the most important factor in the credibility of a Web site? A) information design/structure B) information focus C) design look D) information usefulness Answer: C 63) Amazon's "one-click" purchase capability is an example of using ________ to enhance sales. A) advertising B) search engine functionality C) Web site functionality D) offline communications Answer: C 64) Frequency of Web site use is a function of four independent variables: Web site organization, perceived ease of use, perceived usefulness of the Web site, and: A) design look. B) credibility. C) content quality. D) simple navigation. Answer: C 65) Which of the following is not a major Web design feature that impacts online purchasing? A) redundant navigation B) fast download times C) easy product list navigation D) responsiveness Answer: A [Show More]
Last updated: 3 years ago
Preview 1 out of 66 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$8.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Jul 23, 2021
Number of pages
66
Written in
All
Additional information
This document has been written for:
Uploaded
Jul 23, 2021
Downloads
0
Views
151








.png)