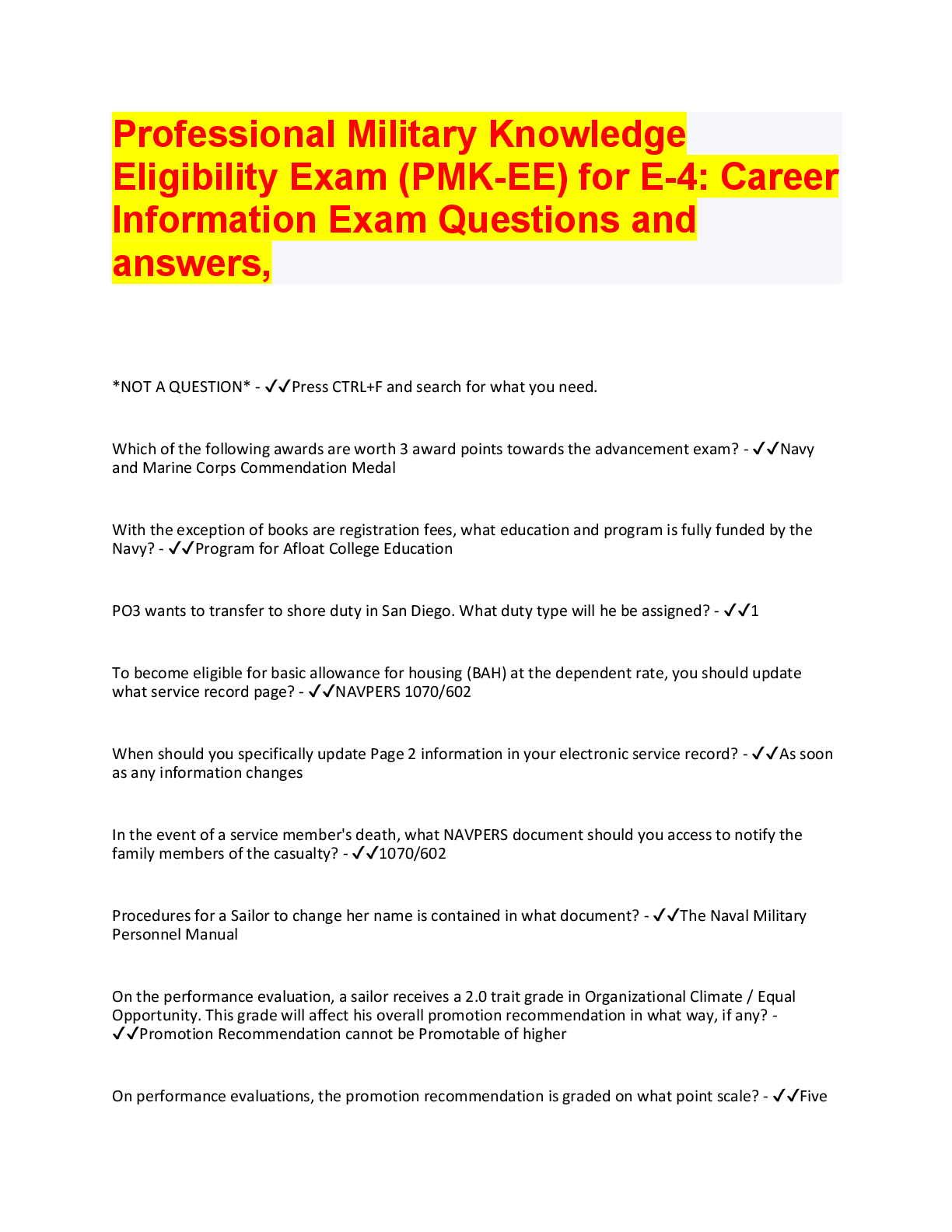
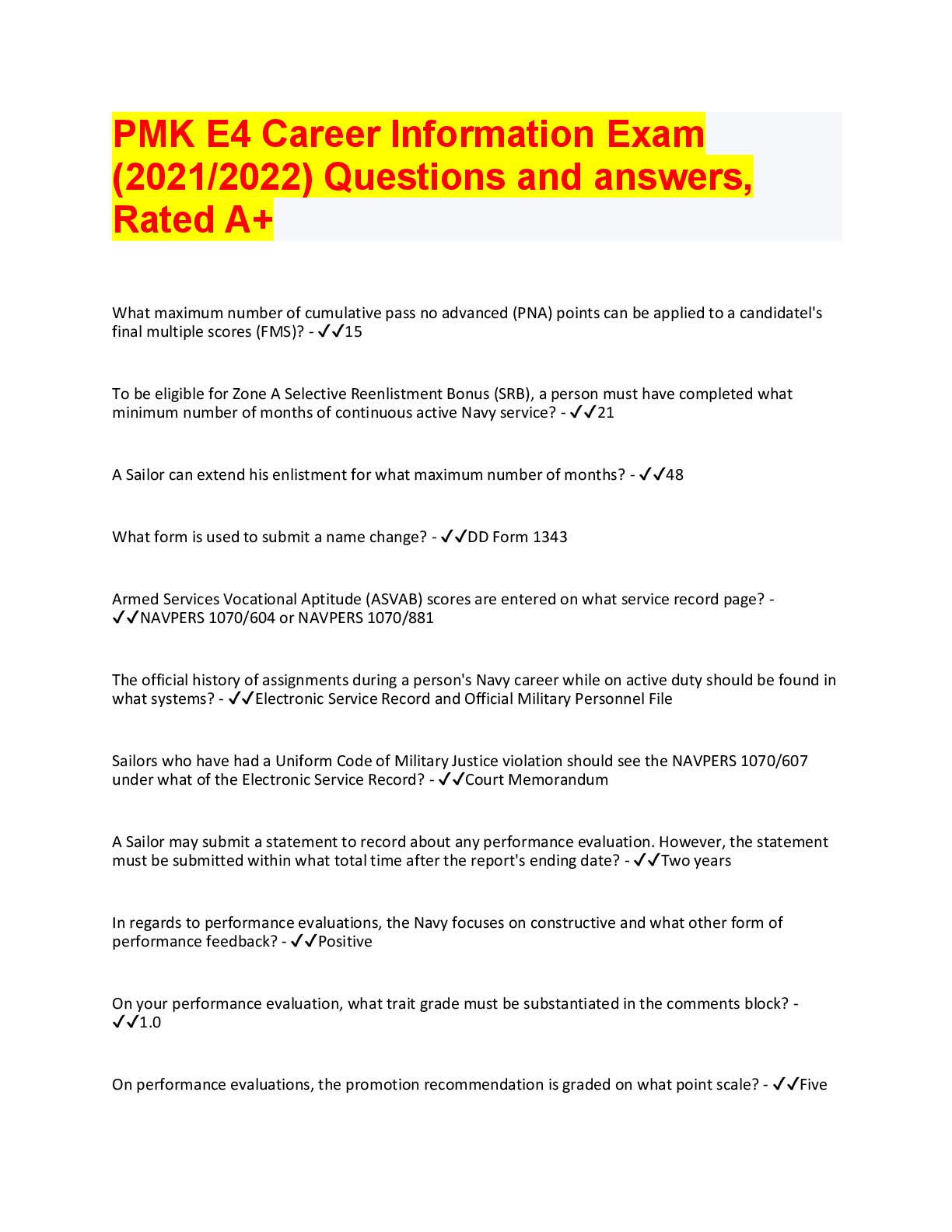
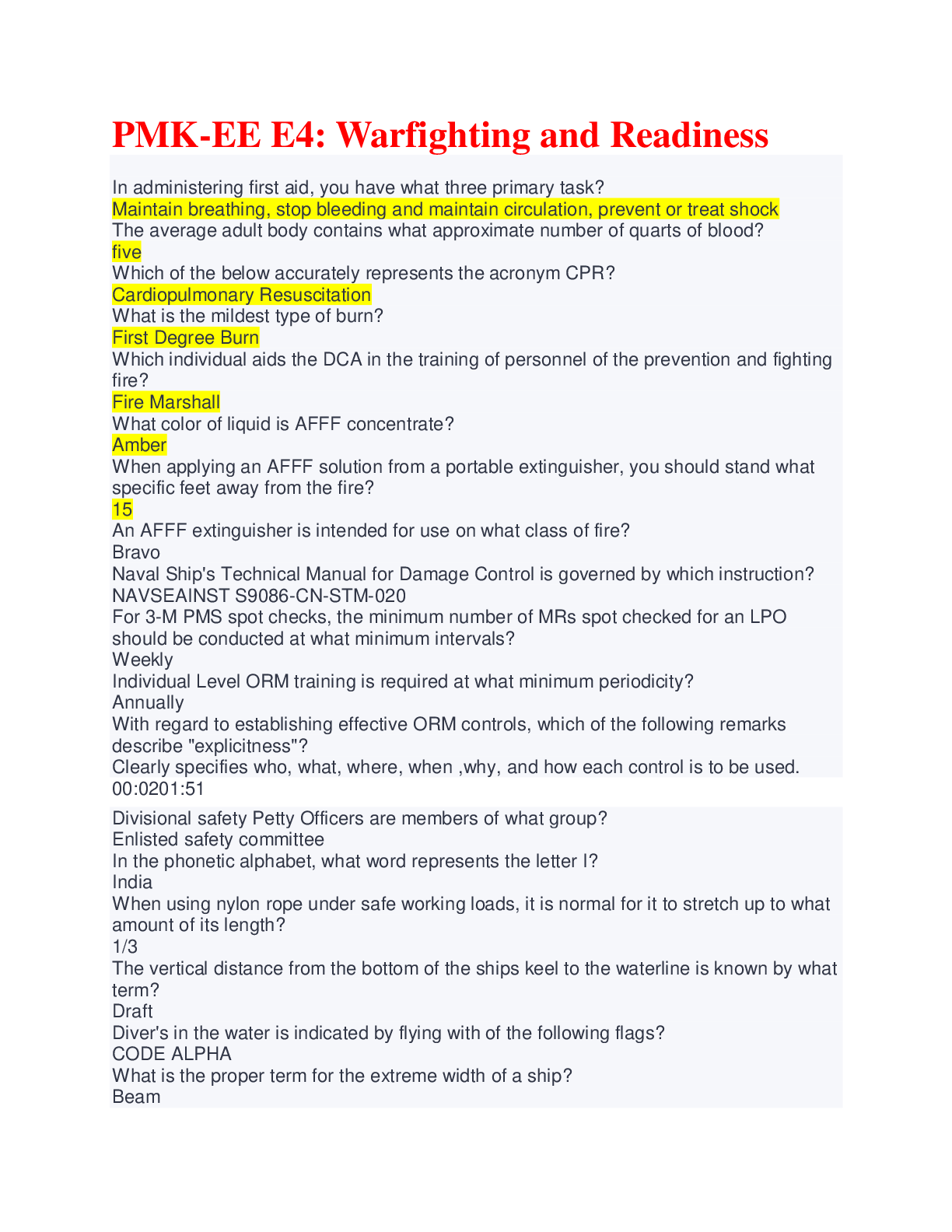
Database Management > QUESTIONS & ANSWERS > CISM - Test Practice 2022 with complete solution. Rated A+. Examinable Questions (All)
CISM - Test Practice 2022 with complete solution. Rated A+. Examinable Questions
Document Content and Description Below
CISM - Test Practice 2022 with complete solution Security governance is most concerned with: A. Security policy B. IT policy C. Security strategy D. Security executive -Answer- C. Security Strate... gy A gaming software startup company does not employ penetration testing of its software. This is an example of: A. High tolerance of risk B. Noncompliance C. Irresponsibility D. Outsourcing -Answer- A. High tolerance of risk An organization's board of directors wants to see quarterly metrics on risk reduction. What would be the best metric for this purpose? A. Number of firewall rules triggered B. Viruses blocked by the firewall C. Packets dropped by the firewall D. Time to patch vulnerabilities on critical servers -Answer- D. Time to patch vulnerabilities on critical servers Which of the following metrics is the best example of a leading indicator? A. Average time to mitigate security incidents B. Increase in the number of attacks blocked by the intrusion prevention system (IPS) C. Increase in the number of attacks blocked by the firewall D. Percentage of critical servers being patched within service level agreements (SLAs) - Answer- D. Percentage of critical servers being patched within service level agreements (SLAs) What are the elements of the business model for information security (BMIS)? A. Culture, governing, architecture, emergence, enabling and support, human factors B. People, process, technology C. Organization, people, process, technology D. Financial, customer, internal processes, innovation, and learning -Answer- C. Organization, people, process, technology The best definition of a strategy is: A. The objective to achieve a plan B. The plan to achieve an objective C. The plan to achieve business alignment D. The plan to reduce risk -Answer- B. The plan to achieve an objective The primary factor related to the selection of a control framework is: A. Industry verticalB. Current process maturity level C. Size of the organization D. Compliance level -Answer- A. Industry vertical As part of understanding the organization's current state, a security strategist is examining the organization's security policy. What does the policy tell the strategist? A. the level of management commitment to security B. The compliance level of the organization C. The maturity level of the organization D. None of these -Answer- D. None of these While gathering and examining various security-related business records, the security manager has determined that the organization has no security incident log. What conclusion can the security manager make from this? A.The organization does not have security incident detection capabilities B. The organization has not yet experienced a security incident C. The organization is recording security incidents in its risk register D. The organization has effective preventive and detective controls. -Answer- A. The organization does not have security incident detection capabilities The purpose of a balanced scorecard is to: A. Measure the efficiency of a security organization B. Evaluate the performance of individual employees C. Benchmark a process in the organization against peer organizations D. Measure organizational performance and effectiveness against strategic goals - Answer- D. Measure organizational performance and effectiveness against strategic goals A security strategist has examined a business process and has determined that personnel who perform the process do so consistently, but there is no written process document. The maturity level of this process is: A. Initial B. Repeatable C. Defined D. Managed -Answer- B. Repeatable A security strategist has examined several business processes and has found that their individual maturity levels range from Repeatable to Optimizing. What is the best future state for these business processes? A. All processes should be changed to Repeatable. B. All processes should be changed to Optimizing C. There is insufficient information to determine the desired end states of these processes D. Processes that are Repeatable should be changed to Defined. -Answer- C. There is insufficient information to determine the desired end states of these processesIn an organization using PCI-DSS as its as its control framework, the conclusion of a recent risk assessment stipulates that additional controls not present in PCI-DSS but present in ISO 27001 should be enacted. What is the best course of action in this situation? A. Adopt ISO 27001 as the new control framework B. Retain PCI-DSS as the control framework and update process documentation C. Add the required controls to the existing control framework D. Adopt NIST 800-53 as the new control framework -Answer- C. Add the required controls to the existing control framework A security strategist is seeking to improve the security program in an organization with a strong but casual culture. What is the best approach here? A. Conduct focus groups to discuss possible avenues of approach B. Enact new detective controls to identify personnel who are violating policy C. Implement security awareness training that emphasizes new required behavior D. Lock users out of their accounts until they agree to be compliant -Answer- A. Conduct focus groups to discuss possible avenues of approach A security strategist recently joined a retail organization that operates with slim profit margins and has discovered that the organization lacks several important security capabilities. What is the best strategy here? A. Insist that management support an aggressive program to quickly improve the program. B. Develop a risk ledger that highlights all identified risks. C. Recommend that the biggest risks be avoided D. Develop a risk-based strategy that implements changes slowly over an extended period of time. -Answer- D. Develop a risk-based strategy that implements changes slowly over an extended period of time. A risk manager is planning a first-ever assessment in an organization. What is the best approach for ensuring success? A. Interview personnel separately so that their responses can be compared B. Select a framework that matches the organization's control framework. C. Work with executive management to determine the correct scope D. Do not inform executive management until the risk assessment has been completed. -Answer- C. Work with executive management to determine the correct scope A security manager has completed a vulnerability scan and has identified numerous vulnerabilities in production servers. What is the best course of action? A. Notify the production servers' asset owners B. Conduct a formal investigation C. Place a single entry into the risk register D. Put individual vulnerability entries into the risk register -Answer- A. Notify the production servers' asset ownersThe concept of security tasks in the context of a SaaS or IaaS environment is depicted in a: A. Discretionary control model B. Mandatory control model C. Monte Carlo risk model D. Shared responsibility model -Answer- D. Share responsibility model The categories of risk treatment are: A. Risk avoidance, risk transfer, risk mitigation, and risk acceptance B. Risk avoidance, risk transfer, and risk mitigation C. Risk avoidance, risk reduction, risk transfer, risk mitigation, and risk acceptance D. Risk avoidance, risk treatment, risk mitigation, and risk acceptance -Answer- A. Risk avoidance, risk transfer, risk mitigation, and risk acceptance Which of the following recovery objectives is associated with the longest allowed period of service outrage? A. Recovery Tolerance objective (RTO) B. Recovery point objective (RPO) C. Recovery capacity objective (RCap) D. Recovery time objective (RTO) -Answer- D. Recovery time objective (RTO) When would it make sense to spend $50,000 to protect an asset worth $10,000? A. If the protective measure reduced treat impact by more than 90 percent. B. It would never make sense to spend $50,00 to protect an asset worth $10,000 C. If the asset was required for realization of $500,000 monthly revenue D. If the protective measure reduced threat probability by more than 90 percent - Answer- C. if the asset was required for realization of $500,000 monthly revenue Which of the following statements are true about compliance risk? A. Compliance risk can be tolerated when fines cost less than controls B. Compliance risk is just another risk that needs to be measured C. Compliance risk can never be tolerated D. Compliance risk can be tolerated when it is optional -Answer- B. Compliance risk is just another risk that needs to be measured A security steering committee empowered to make risk treatment decisions has chosen to accept a specific risk. What is the best course of action? A. Refer the risk to a qualified external security audit firm B. Perform additional risk analysis to identify residual risk C. Reopen the risk item for reconsideration after one year D. Mark the risk item as permanently closed -Answer- C. Reopen the risk item for reconsideration after one year A security steering committee has voted to mitigate a specific risk. Some residual risk remains. What is the best course of action regarding the residual risk? A. Accept the residual risk and close the risk ledger itemB. Continue cycles of risk treatment until the residual risk reaches an acceptable level C. Continue cycles of risk treatment until the residual risk reaches zero D. Accept the residual risk and keep the risk ledger item open -Answer- B. Continue cycles of risk treatment until the residual risk reaches an acceptable level A security manager has been directed by executive management to not document a specific risk in the risk register. This course of action is known as: A. Burying the risk B. Transferring the risk C. Accepting the risk D. Ignoring the risk -Answer- D. Ignoring the risk A security manager is performing a risk assessment on a business application. The security manager has determined that security patches have not been installed for more than a year. This finding is known as a: A. Probability B. Threat C. Vulnerability D. Risk -Answer- C. Vulnerability A security manager is performing a risk assessment on a data center. The security manager has determined that it is possible for unauthorized personnel to enter the data center through the loading dock door and shut off utility power to the building. This finding is known as a: A. Probability B. Threat C. Vulnerability D. Risk -Answer- B. Threat A security manager has developed a scheme that prescribes required methods be used to protect information at rest, in motion, and in transit. This known as a(n): A. Data classification policy B. Asset classification policy C. Data loss prevention plan D. Asses lost prevention plan -Answer- A. Data classification policy A security manager is developing a strategy for making improvements to the organization's incident management process. The security manager has defined the desired future state. Before specific plans can b [Show More]
Last updated: 2 years ago
Preview 1 out of 10 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$10.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Sep 22, 2022
Number of pages
10
Written in
Seller

Reviews Received
Additional information
This document has been written for:
Uploaded
Sep 22, 2022
Downloads
0
Views
107