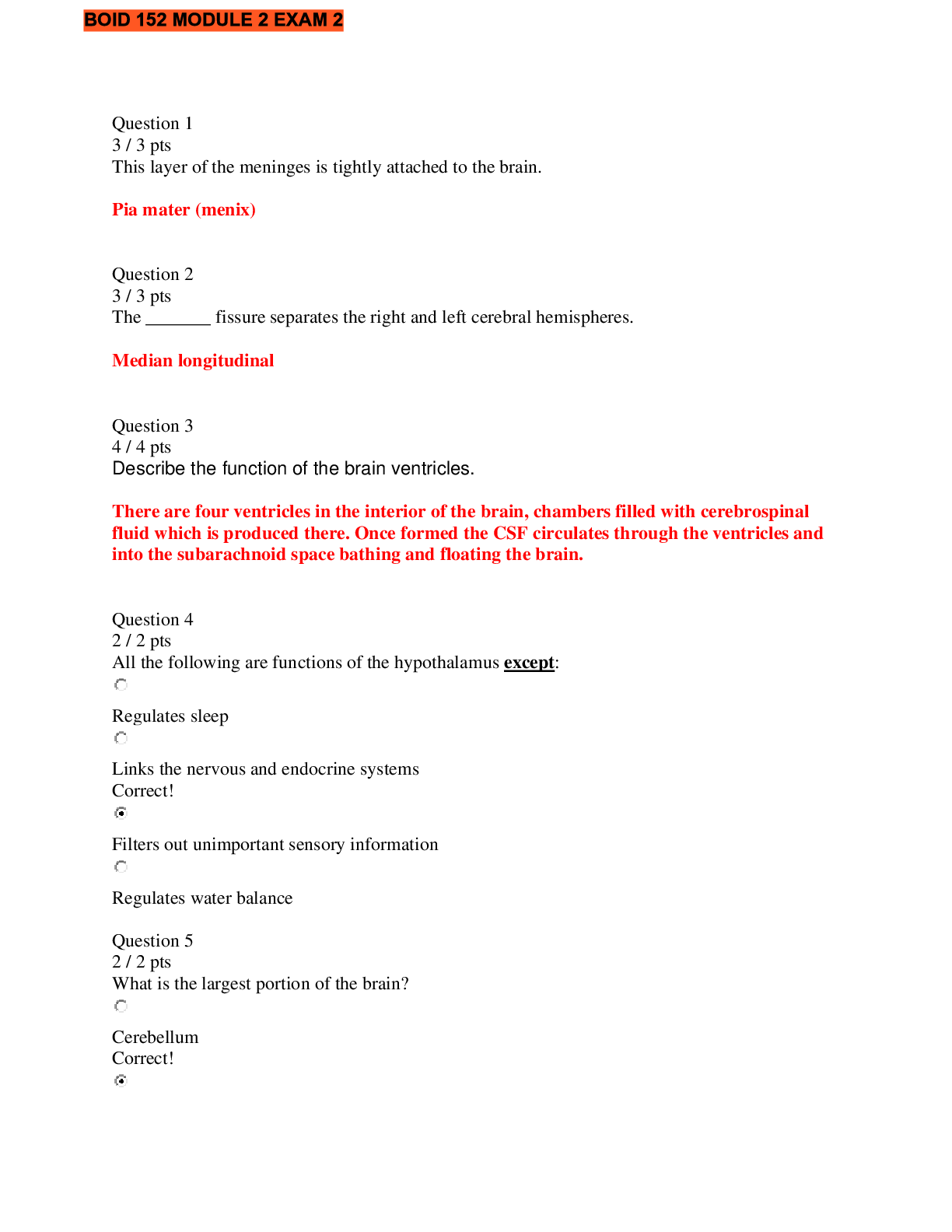
Social Sciences > QUESTIONS & ANSWERS > Chapter 5, Questions with accurate answers, Rated A. 2022/2023. Graded A (All)
Chapter 5, Questions with accurate answers, Rated A. 2022/2023. Graded A
Document Content and Description Below
Chapter 5, Questions with accurate answers, Rated A. 2022/2023. Graded A 1) Which of the following is not one of the AAA controls? A) authentication B) auditing C) accuracy D) authorization... s - ✔?C Diff: 1 Page Ref: 246 Question: 1a 2) ________ is the process of assessing the identity of each individual claiming to have permission to use a resource. A) Authorizations B) Authentication C) Accuracy D) Auditing - ✔?B Diff: 1 Page Ref: 246 Question: 1b 3) ________ is the process of assessing the identity of each individual claiming to have permission to use a resource. A) Authorizations B) Authentication C) Both A and B D) Neither A nor B - ✔?B Diff: 1 Page Ref: 246 Question: 1b 4) ________ is the process of collecting information about the activities of each individual in log files for immediate and later analysis. A) Authorizations B) Authentication C) Accuracy D) Auditing - ✔?D Diff: 1 Page Ref: 246 Question: 1b 5) Authentication is the process of collecting information about the activities of each individual in log files for immediate and later analysis. - ✔?FALSE Diff: 1 Page Ref: 246 7) Two-factor authentication can be defeated if ________. A) the user's computer is compromised B) the attacker uses a man-in-the-middle attack C) Both A and B D) Neither A nor B - ✔?C Diff: 2 Page Ref: 247 Question: 1c 8) Compared to access control based on individual accounts, RBAC is ________. A) less prone to error B) more expensive C) Both A and B D) Neither A nor B - ✔?A Diff: 2 Page Ref: 248 Question: 1g 9) In the military, departments do not have the ability to alter access control rules set by higher authorities in ________. A) policy-based access control B) mandatory access control C) discretionary access control D) multilevel access control - ✔?B Diff: 1 Page Ref: 249 Question: 2a 10) In ________ the department has discretion over giving access to individuals, within policy standards set by higher authorities. A) policy-based access control B) mandatory access control C) discretionary access control D) delegated access control - ✔?C Diff: 1 Page Ref: 250 Question: 2a 11) In military security, the term multilevel security means multifactor security. - ✔?FALSE Diff: 2 Page Ref: 250 Question: 2b 12) In military security, SBU documents are unclassified. - ✔?TRUE Diff: 1 Page Ref: 249 Question: 2c 13) All unattended exits should be locked to bar exit. - ✔?FALSE Diff: 2 Page Ref: 252 Question: 3c 14) In CobiT, entry must be ________. A) justified B) logged C) Both A and B D) Neither A nor B - ✔?C Diff: 2 Page Ref: 252 Question: 3d 15) On loading docks, outgoing shipments should be separated from incoming shipments ________. A) to ensure the segregation of duties B) to avoid confusion C) to reduce the risk of theft D) All of the above - ✔?C Diff: 2 Page Ref: 252 Question: 3f 16) Which of the following is not one of the rules for working in secure areas? A) Unsupervised work in secure areas should be avoided. B) When no one is in a secure area, it should be locked and verified periodically. C) No one should be allowed to work in secure areas for more than four hours in a row. D) Electronic devices that can record or copy mass amounts of information should be forbidden in secure areas. - ✔?C Diff: 2 Page Ref: 252 Question: 3h 17) Which of the following should be forbidden in secure areas? A) cameras B) USB flash drives C) Both A and B D) Neither A nor B - ✔?C Diff: 1 Page Ref: 256 Question: 3h 19) ________ can be used to supply power during long power outages. A) Uninterruptable power supplies B) Electrical generators C) Both A and B D) Neither A nor B - ✔?B Diff: 2 Page Ref: 257 Question: 4b 20) If a laptop needs to be taken off premises, ________. A) it should first be logged out. B) it should be logged in when returned C) all sensitive information should be removed D) All of the above - ✔?D Diff: 2 Page Ref: 257 Question: 4d 21) Buildings should be set back from streets and protected with rolling hill landscaping to reduce threats from ________. A) wireless eavesdropping B) industrial espionage C) casual observation D) terrorism - ✔?D Diff: 2 Page Ref: 258 Question: 5a 22) ________ is a social engineering trick where an intruder may follow an authorized user through a door that the authorized user opens with an access device. A) Shoulder surfing B) Shadowing C) Trailing D) Piggybacking - ✔?D Diff: 1 Page Ref: 258 Question: 5b 23) It is illegal to go through a company's trash bins even if the trash bins are outside the corporation. - ✔?FALSE Diff: 1 Page Ref: 259-260 Question: 5e 24) Most users who have access to servers use reusable passwords for authentication. - ✔?TRUE Diff: 1 Page Ref: 260 Question: 6a 25) PCs should require login screens with complex passwords. - ✔?TRUE Diff: 1 Page Ref: 260 26) Password cracking is usually done over the network by trying many passwords to log into an account. - ✔?FALSE Diff: 1 Page Ref: 260-261 Question: 6b 27) Long passwords that use several types of keyboard characters are called ________ passwords. A) complex B) reusable C) dictionary D) one-time - ✔?A Diff: 1 Page Ref: 266-268 Question: 7a 28) The book recommends that passwords be at least ________ characters long. A) 6 B) 8 C) 20 D) 100 - ✔?B Diff: 1 Page Ref: 266 Question: 9a 29) According to the book, r%Dv$ is a strong password. - ✔?FALSE Diff: 3 Page Ref: 266 Question: 9a 30) It is very important for testers to get permission before running a password cracking program on their company's computers to check for weak passwords, even if such testing is in their job definitions. - ✔?TRUE Diff: 1 Page Ref: 266-267 Question: 9c 31) Users should select very long and complex passwords and use the same password at all sites for auditability. - ✔?FALSE Diff: 1 Page Ref: 261 Question: 10a 33) Which of the following is true? A) human password resets are dangerous B) automated password resets are dangerous C) Both A and B D) Neither A nor B - ✔?B Diff: 2 Page Ref: 264 Question: 10e 34) In high-risk environments, password reset risks are reduced by requiring the user's physical presence. - ✔?TRUE Diff: 2 Page Ref: 265 Question: 10h 35) Passwords offer reasonable security at reasonable cost and will likely continue to increase in importance in the future. - ✔?FALSE Diff: 1 Page Ref: 267 Question: 11 36) A ________ card is an access card that has a built-in microprocessor and memory. A) magnetic stripe B) smart C) Both A and B D) Neither A nor B - ✔?B Diff: 2 Page Ref: 268-269 Question: 12a 37) A magnetic stripe card is an access card that has a built-in microprocessor and memory. - ✔?FALSE Diff: 1 Page Ref: 268-269 Question: 12a 38) A ________ card stores authentication data. A) magnetic stripe B) smart C) Both A and B D) Neither A nor B - ✔?C Diff: 2 Page Ref: 268-269 Question: 12a 40) A ________ is a small device that plugs into a standard computer port to identify the owner. A) one-time-password token B) USB token C) magnetic stripe card D) smart card - ✔?B Diff: 1 Page Ref: 270 Question: 12c 41) A ________ does not require a special reader to be added to a PC for access control. A) USB token B) magnetic stripe card C) smart card D) All of the above - ✔?A Diff: 2 Page Ref: 270 Question: 12e 42) ________ can be much shorter than ________. A) PINs, passwords B) Passwords, PINs C) there is no general length difference between passwords and PINs D) None of the above - ✔?A Diff: 1 Page Ref: 272 43) The major promise of biometrics is to replace reusable passwords - ✔?TRUE Diff: 1 Page Ref: 273-274 Question: 14c 45) The template is based on ________ generated during the enrollment scan. A) scan data B) key features C) Both A and B D) Neither A nor B - ✔?B Diff: 2 Page Ref: 274 Question: 15d 46) In biometric, a match occurs when a ________ meets the decision criteria. A) set of key features B) match index C) Both A and B D) Neither A nor B - ✔?B Diff: 1 Page Ref: 276 Question: 16a 47) A false rejection occurs when a person is improperly matched to a template. - ✔?FALSE Diff: 2 Page Ref: 276-277 Question: 16b 48) A false acceptance occurs when a person is improperly matched to a template. - ✔?TRUE Diff: 2 Page Ref: 276-277 Question: 16b 49) For computer access, a false ________ means that a legitimate user is denied access to a resource. A) rejection B) acceptance C) Both A and B D) Neither A nor B - ✔?A Diff: 1 Page Ref: 276-277 Question: 16d 50) From a security viewpoint, a false acceptance is always worse than a false rejection. - ✔?FALSE Diff: 2 Page Ref: 276-277 Question: 16f 51) For watch lists of criminals, a false ________ means that an innocent person is identified as a criminal. A) acceptance B) rejection C) Both A and B D) Neither A nor B - ✔?A Diff: 3 Page Ref: 276-277 Question: 17a 52) For watch lists of criminals, a false acceptance is worse than a false rejection from a security viewpoint. - ✔?FALSE Diff: 3 Page Ref: 276-277 Question: 17b 53) Identification is the process where the verifier determines whether the supplicant is a particular person that the supplicant claims who he or she is. - ✔?FALSE Diff: 3 Page Ref: 277 Question: 19a 54) Verification is the process where the verifier determines the identity of the supplicant. - ✔?FALSE Diff: 2 Page Ref: 278 Question: 19a 55) The verifier itself determines the identity of the supplicant in ________. A) verification B) identification C) Both A and B D) Neither A nor B - ✔?B Diff: 2 Page Ref: 278 Question: 19a 56) Verification requires more matches against templates than does identification. - ✔?FALSE Diff: 2 Page Ref: 278-279 Question: 19b 57) Identification requires more matches against templates than does verification. - ✔?TRUE Diff: 2 Page Ref: 279-280 Question: 19b 58) Which is more likely to generate a false acceptance? A) verification B) identification C) Both verification and identification are equally likely to generate a false acceptance. D) None of the above - ✔?B Diff: 3 Page Ref: 280 59) ________ is a form of identification that identifies a person as being a member of a group. A) RBAC B) Watch list matching C) Group ID matching D) Group acceptance - ✔?B Diff: 1 Page Ref: 279-280 Question: 19d [Show More]
Last updated: 2 years ago
Preview 1 out of 26 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$10.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Sep 24, 2022
Number of pages
26
Written in
Additional information
This document has been written for:
Uploaded
Sep 24, 2022
Downloads
0
Views
94















.png)

.png)