Information Technology > EXAMs > SEC280_final exam (SOLVED) (All)
SEC280_final exam (SOLVED)
Document Content and Description Below
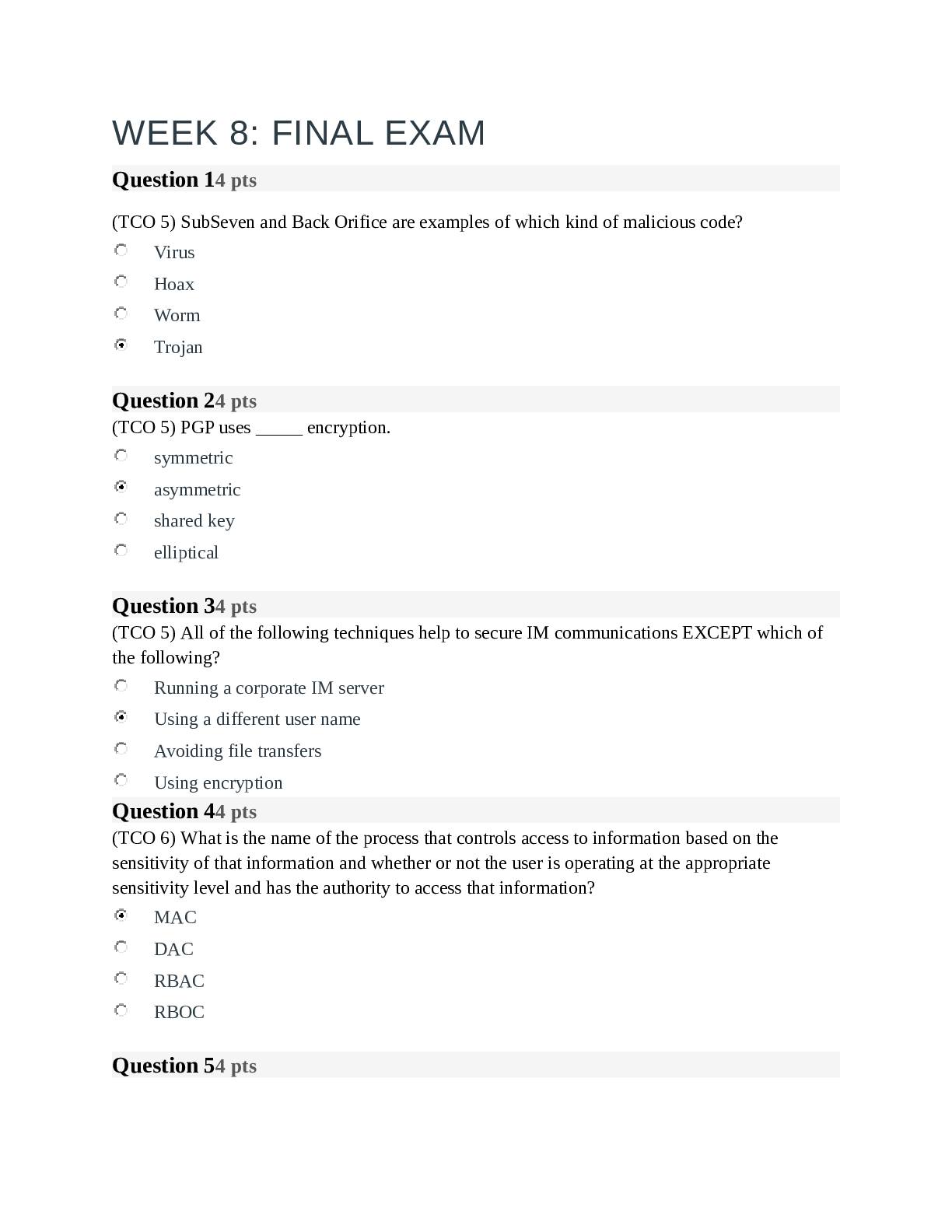
SEC 280SEC280_final exam Question 1.1. (TCO 5) SubSeven and Back Orifice are examples of what kind of malicious code? (Points : 4) Trojan Question 2.2. (TCO 5) Two tools that can be used to enc ... rypt e-mail are _____. (Points : 4) PGP and SIME Question 3.3. (TCO 5) All of the following techniques help secure IM communications except _____. (Points : 4) using a different user name Question 4.4. (TCO 6) What is the name of the process that controls the access to information based on the sensitivity of that information, whether or not the user operates at the appropriate sensitivity level, and whether the user has the authority to access that information? (Points : 4) MAC Question 5.5. (TCO 6) The access-control model that most closely resembles an organization's structure is _____. (Points : 4) RBAC Question 6.6. (TCO 6) Running Java applets from the Web on your system is considered _____. (Points : 4) a security risk Question 7.7. (TCO 6) Which is more secure? (Points : 4) Server-side scripting Question 8.8. (TCO 6) Which of the following does not enhance the security of the browser? (Points : 4) Browser plug-ins Question 9.9. (TCO 6) Your boss wants you to make company files available to the general public, but she does not want you to have to create user accounts for anyone who wants access to the file transfer. In this case, you should use _____. (Points : 4) FTP Blind FTP SFTP FTPS Question 10.10. (TCO 2) What are the security risks of installing games on an organization's system? (Points : 4) Users can't always be sure where the software came from, and it may have hidden software inside of it. Question 11.11. (TCO 2) Which of the following is the weakest password? (Points : 4) P@$$w0rd Question 12.12. (TCO 8) The law that regulates unsolicited, commercial e-mail is the _____. (Points : 4) CAN-SPAM Act Question 13.13. (TCO 4) Which of the following is not one of the three forms of trust models? (Points : 4) Star Question 14.14. (TCO 4) Once you have properly obtained a digital certificate for a website, _____. (Points : 4) you cannot be sure of the certificate's validity, and you must check the CRL each time before use Question 15.15. (TCO 2) PGP uses _____. (Points : 4) private-key encryption Question 16.16. (TCO 2) HTTPS uses port _____. (Points : 4) 443 Question 17.17. (TCO 3) Which Transport Layer protocol is connection oriented? (Points : 4) UDP TCP Question 18.18. (TCO 3) Which protocol is responsible for resolving an IP address to a MAC address? (Points : 4) ARP Question 19.19. (TCO 3) Which of the following is a valid IP address? (Points : 4) 12.12.12.12 Question 20.20. (TCO 3) The series of worldwide, interconnected networks is referred to as the _____. (Points : 4) Internet Question 21.21. (TCO 3) The network that is an extension of a selected portion of a company's Intranet to external partners is referred to as the _____. (Points : 4) [Show More]
Last updated: 3 years ago
Preview 1 out of 10 pages
.png)
Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$10.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Sep 03, 2021
Number of pages
10
Written in
All
Additional information
This document has been written for:
Uploaded
Sep 03, 2021
Downloads
0
Views
89

.png)
.png)
.png)