Business > QUESTIONS & ANSWERS > BIS245 WEEK 8 FINAL EXAM / BIS 245 WEEK8 FINAL EXAM (All)
BIS245 WEEK 8 FINAL EXAM / BIS 245 WEEK8 FINAL EXAM
Document Content and Description Below
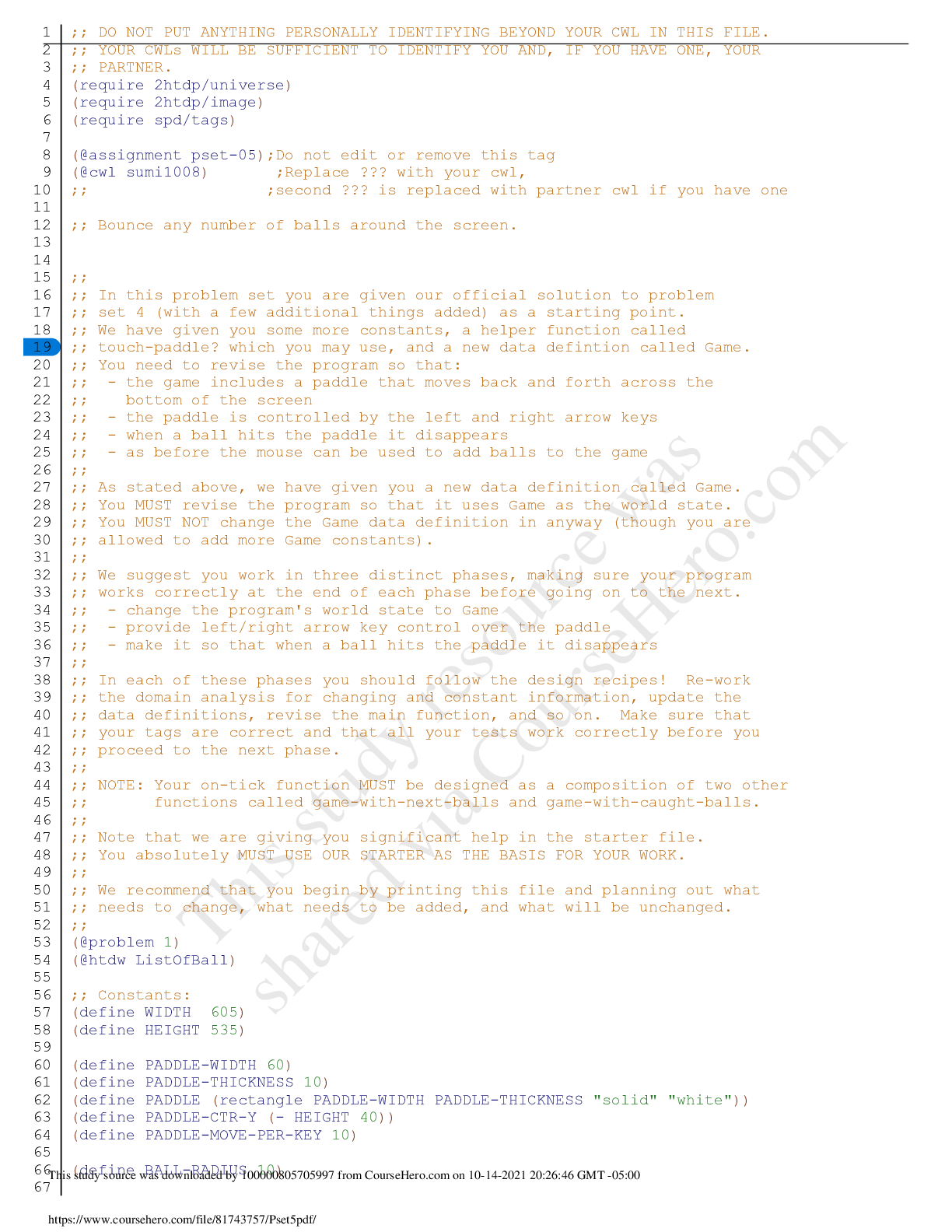
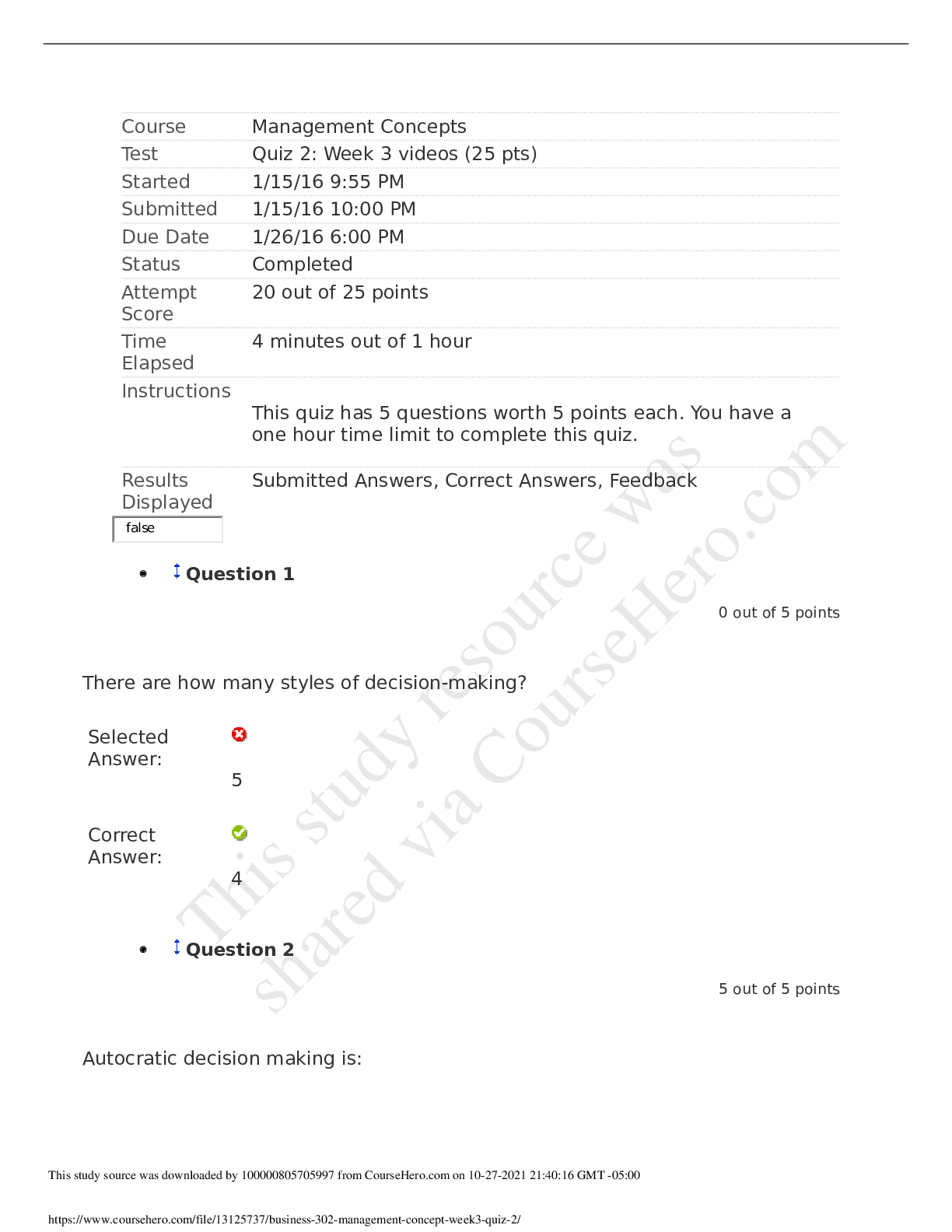
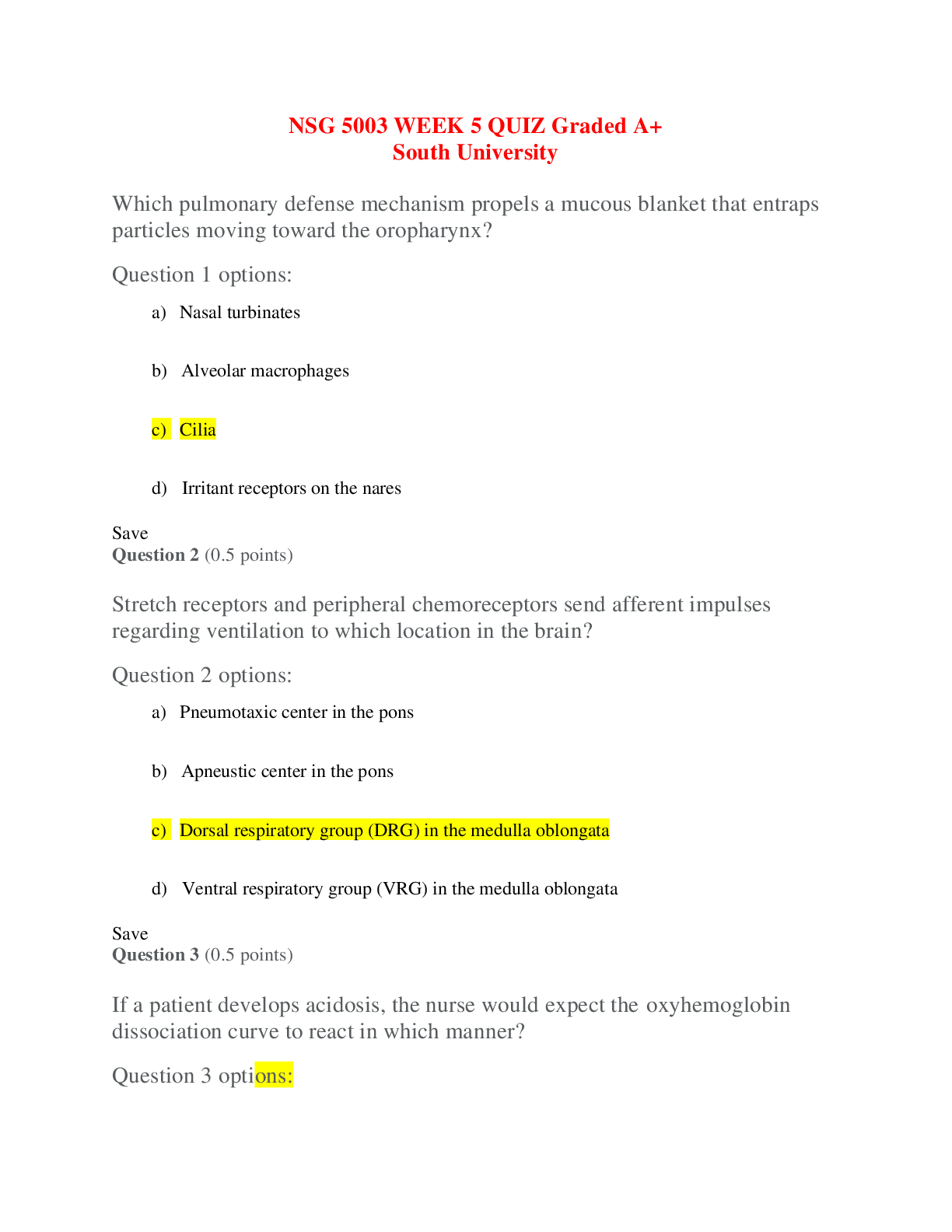
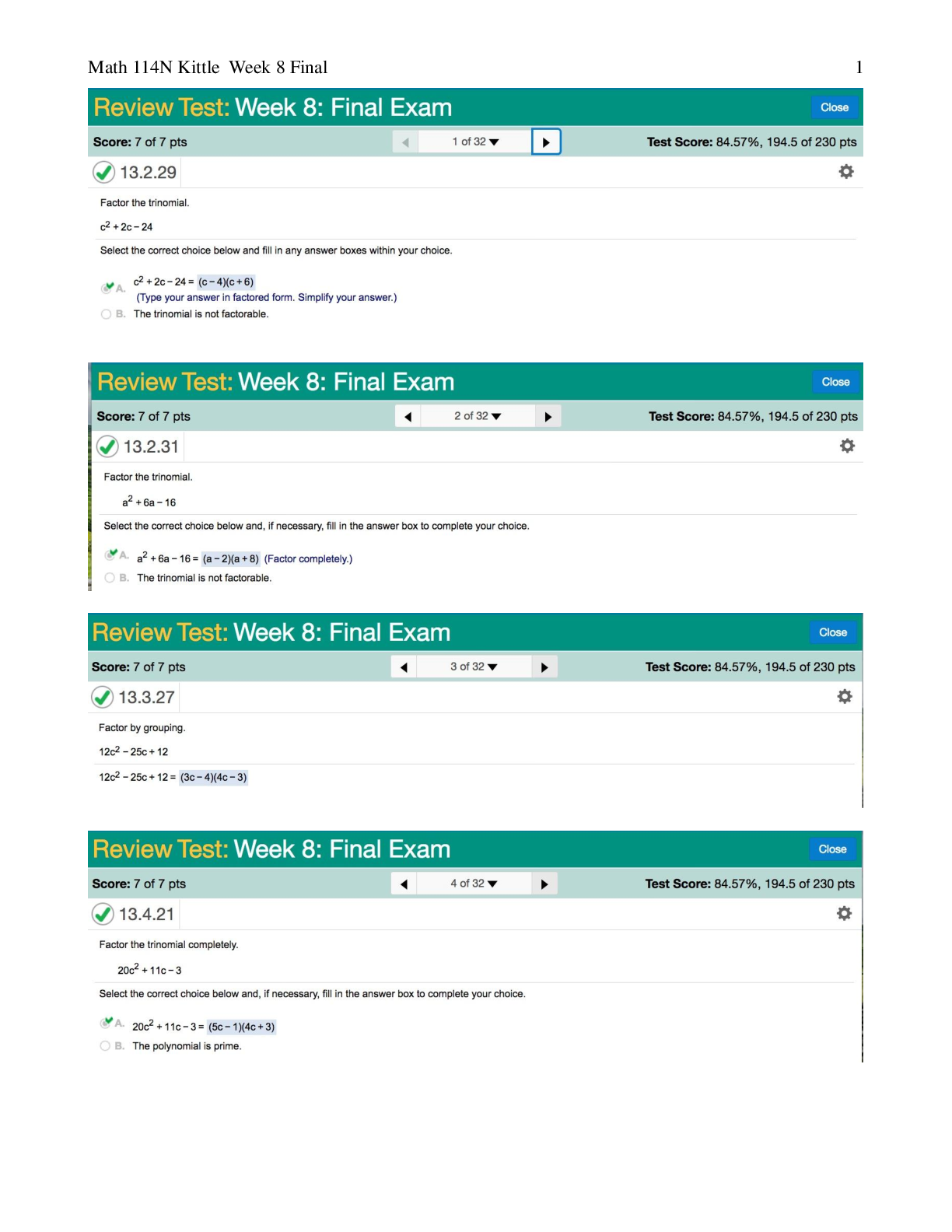
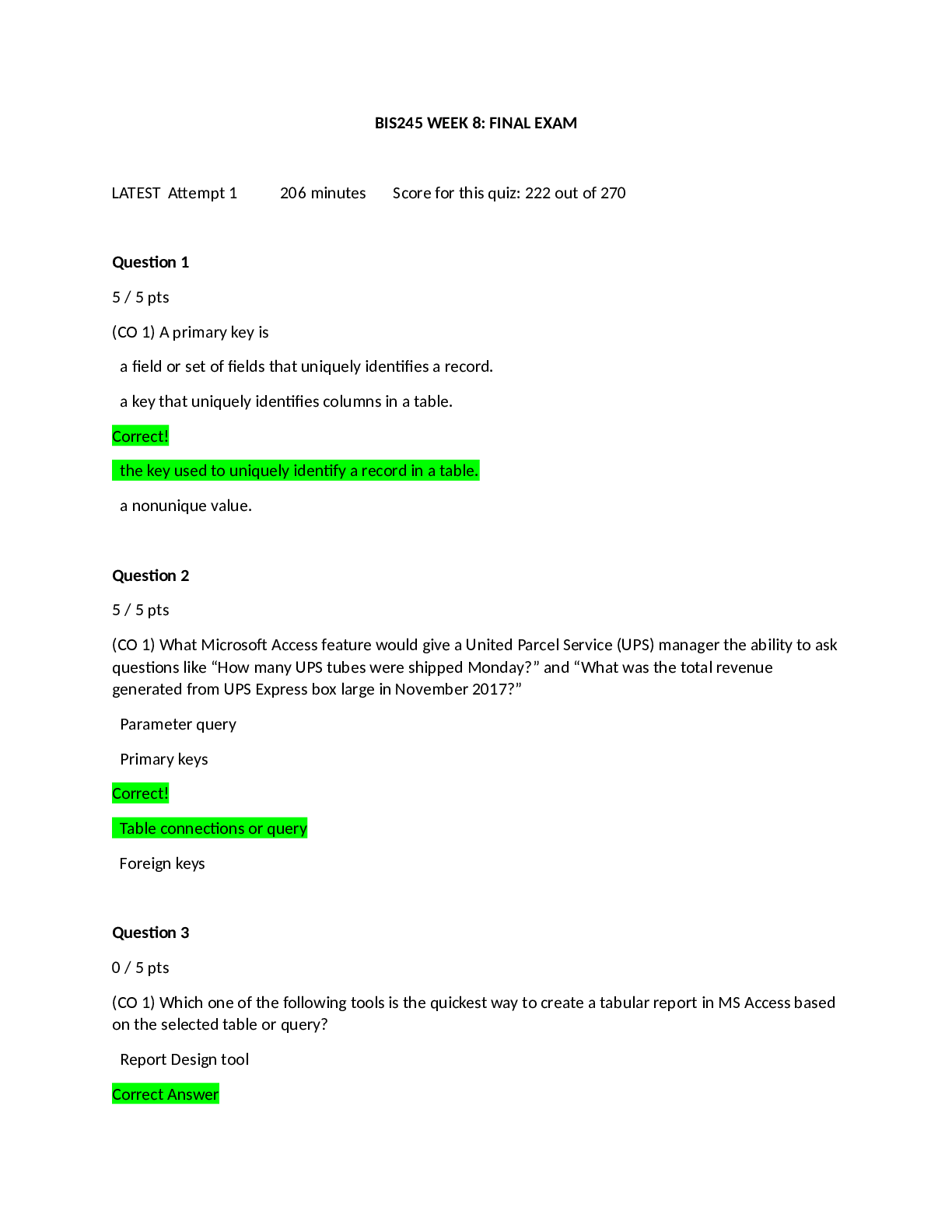
LATEST Attempt 1 206 minutes Score for this quiz: 222 out of270 Question 1 5 / 5 pts (CO 1) A primary key is a field or set of fields that uniquely identifies a record. a key that uniquely id... entifies columns in a table. Correct ! the key used to uniquely identify a record in a table. a nonunique value. Question 2 5 / 5 pts (CO 1) What Microsoft Access feature would give a United Parcel Service (UPS) manager the ability to ask questions like “How many UPS tubes were shipped Monday?” and “What was the total revenue generated from UPS Express box large in November 2017?” Parameter query Primary keys Correct ! Table connections or query Foreign keys Question 3 0 / 5 pts (CO 1) Which one ofthe following tools is the quickest way to create a tabular report in MS Access based on the selected table or query? Report Design tool Correct Answer Report Wizard tool You Answered Blank Report tool Report tool options Question 4 5 / 5 pts (CO 1) Most of the printed documents generated by managers using Access will come from queries. Correct ! reports. tables. forms. Question 5 3 / 5 pts (CO 1) A Report section that is used to summarize grouped field data is Correct Answer group footer. report footer. group header. You Answered detail. Question 6 5 / 5 pts (CO 2) A table is also recognized as a(n) domain. Correct ! entity. key. cardinality. Question 7 1 / 5 pts (CO 2) SQL is a fourth-generation language that is Correct Answer table oriented and nonprocedural. oriented toward static data. flat-file oriented and nonprocedural. You Answered procedural and record oriented. Question 8 5 / 5 pts (CO 3) Which o fthe following should be considered when designing a database? How calculated fields are used The relationships between records The relationship between attribute keys Correct ! Store data in its smallest parts Question 9 5 / 5 pts (CO 3) The following data type would appear as a checkbox in a table. Attribute Correct ! Yes/No Text Number Question 10 5 / 5 pts (CO 3) Which of the following does NOT describe a caption property? The label allows spaces between words. A label can substitute for a field name in datasheet view. The caption appears in datasheet view, form, and report. Correct ! The label can be used in place ofa field name in an expression. Question 11 5 / 5 pts (CO 4) Which of the following does NOT describe the following description ofa one-to-one relationship? FE_IMG55.jpg Description: Image Description: There are two tables. Table number 1 is named Employees and has a primary key ofEmpID with fields: LastName, FirstName, and Salary. Table number 2 is named NewEmployees and has a primary key ofEmpID with fields ofLastName, FirstName, and Hiring Expenses. The two tables are related with a line. The line has no symbols. It may be used for security reasons to protect data availability. More tables can be joined to either table. The Employees and NewEmployees tables use the same primary key. Correct ! The tables must have exactly the same fields. Question 12 5 / 5 pts (CO 5) To edit a form, use You Answered layout view. Correct Answer design view. wizard view. datasheet view. Question 13 5 / 5 pts (CO 5) The following are form creation tools except Correct ! form layout. form design. blank form. form wizard. Question 14 5 / 5 pts (CO 6) Queries are objects in a database based on one or more underlying Correct ! tables. modules. forms. macros. Question 15 2 / 5 pts (CO 6) The benefit ofa relationship is to determine which fields to include in each table. Correct Answer efficiently combine data from related tables. You Answered minimize data redundancy. facilitate how Access will manage the relationship. Question 16 5 / 5 pts (CO 9) A deletion anomaly is Correct ! deleting facts about one entity and deleting facts about another entity. deleting a table. deleting only one fact from a column. deleting facts about one entity successfully. Question 17 2 / 5 pts (CO 2) Which ofthe following statements best describes data mining? Correct Answer It is identifying patterns or relationships through a process ofanalyzing large quantities ofdata. You Answered It is the predicting offuture customer buying behavior. It is the determining offuture volume ofsales. It is tracking customer purchasing behavior. Question 18 5 / 5 pts (CO 8) A navigation form is a screen that is used to hide objects from users. design tool to analyze and optimize a database. Correct ! form that looks like a menu or a series ofmenus that ties objects in a database and helps users look to forms and reports that they are authorized to view. report that looks like a menu or a series ofmenus that ties objects in a database and is not user friendly. Question 19 0 / 5 pts (CO 9) An encrypted file is created by scrambling the content. Correct Answer unreadable if it is opened through a tampering tool or another program. saved with a specific file extension. You Answered protected by a password. Question 20 5 / 5 pts (CO 9) A digital signature Correct ! helps confirm who created the file, that the file is valid, and that no changes have been made to the file once it is authenticated. must be obtained from a certification authority, such as VeriSign. is a tracking system ofa file activity. is used with database files exclusively. Question 21 5 / 5 pts (CO 10) After creating an ACCDE file, you can convert it back to its source format. will see a "file already in use" message that continues to display to all other users. will be able to modify forms and reports but not tables. Correct ! will need to go back to the original file if an underlying object requires a change. Question 22 5 / 5 pts (CO 4) The term cascading refers to Correct ! data changes travel from one table to another. data is put in sequential order. records are arranged in order. queries can retrieve data at a faster rate. Question 23 40 / 40 pts (CO 1) Describe three-tier architecture. Explain the functions performed by each tier. Your Answer: Three-tier architecture is an architectural deployment style style that portray the detachment ofusefulness into layers with each section being a tier that can be situated on a physically separate computer. Using this, architecture the software is partitioned into 3 different tiers: Presentation tier, Logic tier, and Data tier. Presentation tier: This is the highest level ofthe application. The introduction layer gives the application’s user interface. Ordinarily, this includes the utilization ofGraphical User Interface for savvy customer cooperation, and Web based advances for program-based cooperation. Logic tier: The logic tier is hauled out from the presentation tier and, as its own layer; it controls an application's usefulness by performing point by point preparing. Logic tier is where mission-critical business problems are settled. These segments can be utilized to implement business rules, for example, business calculations and legitimate or legislative directions, and information rules, which are intended to keep the information structures reliable inside either particular or different databases. Because these middle-tier components are not tied to a specific client, they can be utilized by all applications and can be moved to various areas, as reaction time and different principles require. Data tier: This tier comprises ofdatabase servers, is the genuine DBMS get to layer. It can be gotten to through the business administrations layer and now and again by the client administrations layer. In here, data is stored and retrieved. This tier keeps data neutral and free from application servers or business rationale. Giving information its own particular tier likewise enhances adaptability and execution. This layer comprises ofinformation get to segments to help in asset sharing and to enable customers to be designed without introducing the DBMS libraries and ODBC drivers on every customer. An illustration would be a computer facilitating a database administration framework. A computing architecture consists ofthe following. (1) Client computers capture user input, send requests for information, and present the results ofthe request. (2) Application servers enable business logic. (3) Data servers store data that provide data to the application server. Question 24 14 / 40 pts (CO 2) Explain the purpose ofa conceptual database model, and describe the most common method ofcreating one. Question 25 40 / 40 pts (CO 4) Explain the terms entity and attribute. Describe an example ofan entity and then list two attributes. Using your examples, explain the data types that would be used to capture the attributes. Question 26 40 / 40 pts (CO 4) If you were given an ERD that contained a M:N relationship between orders and products, what would you need to do in order to create the tables and relationship in Access? Quiz Score: 222 out of270 [Show More]
Last updated: 2 years ago
Preview 1 out of 11 pages
Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$3.50
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Sep 14, 2021
Number of pages
11
Written in
Additional information
This document has been written for:
Uploaded
Sep 14, 2021
Downloads
0
Views
36


.png)