WGU, Information Security and
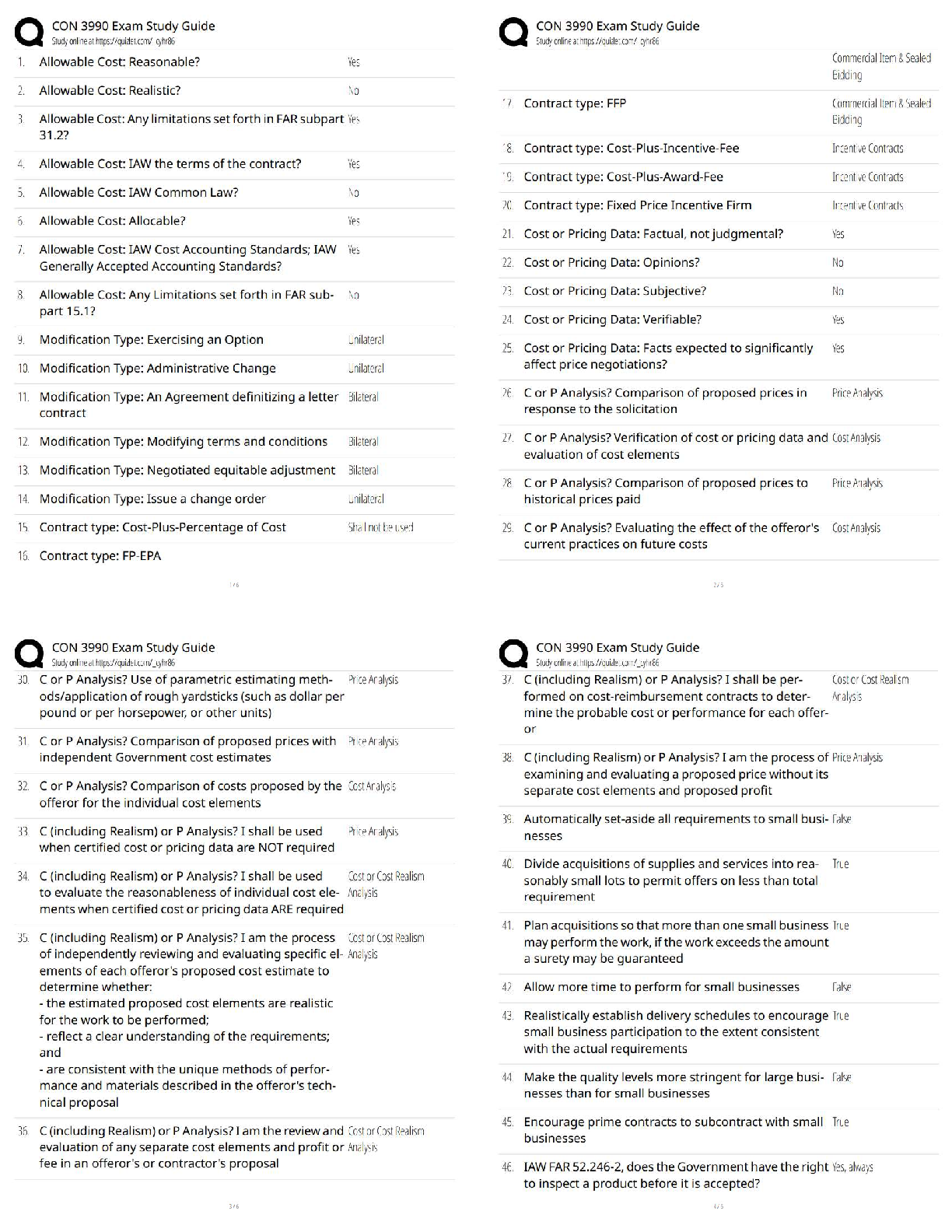
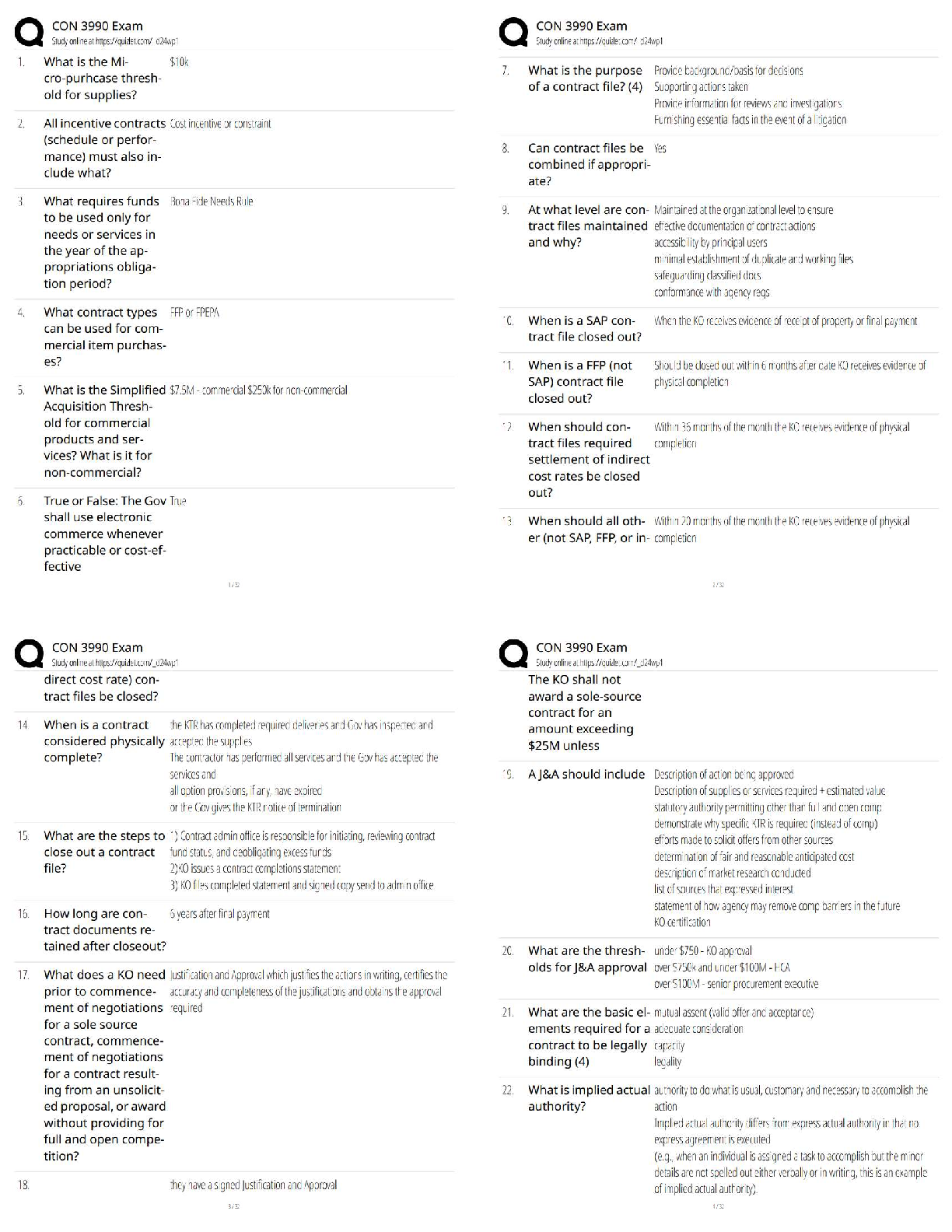
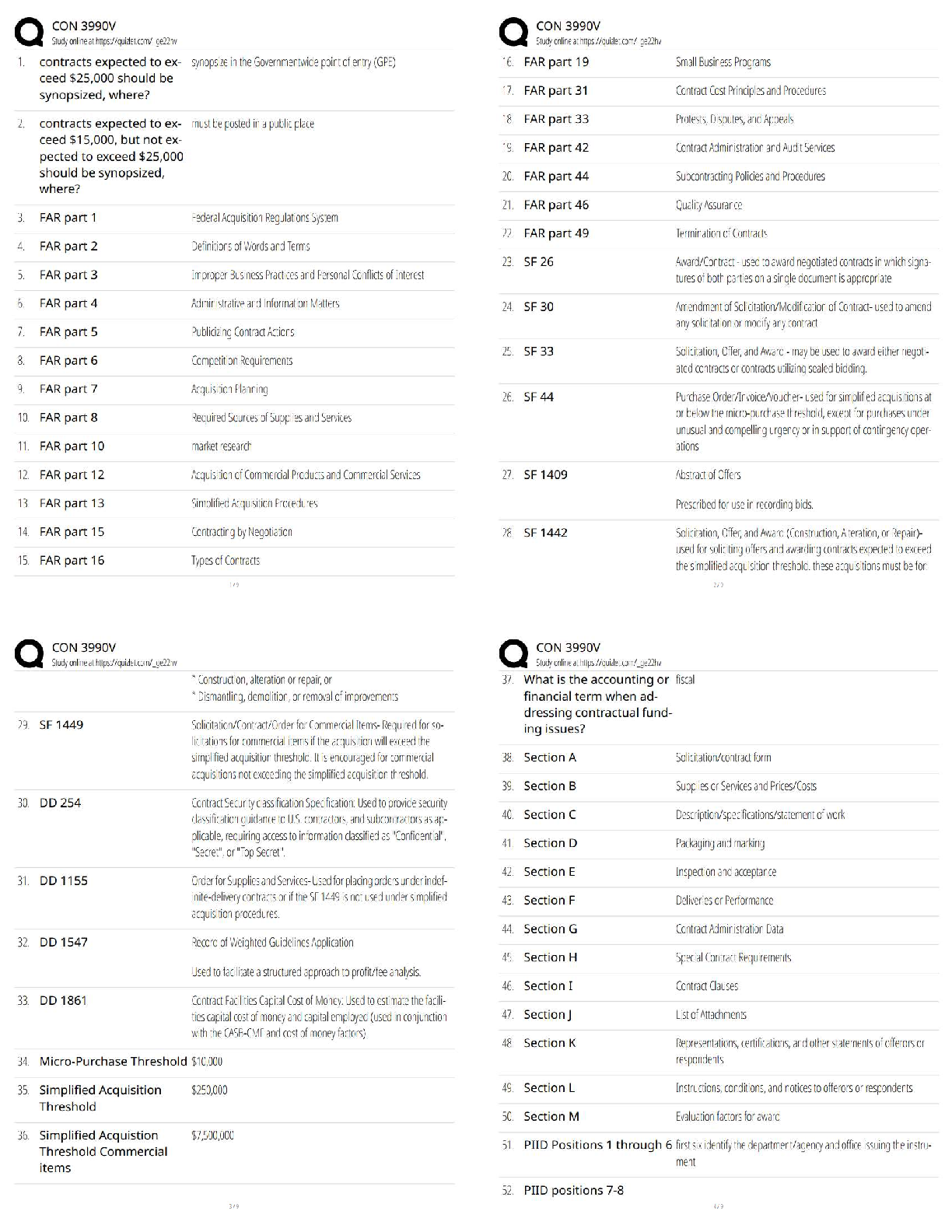
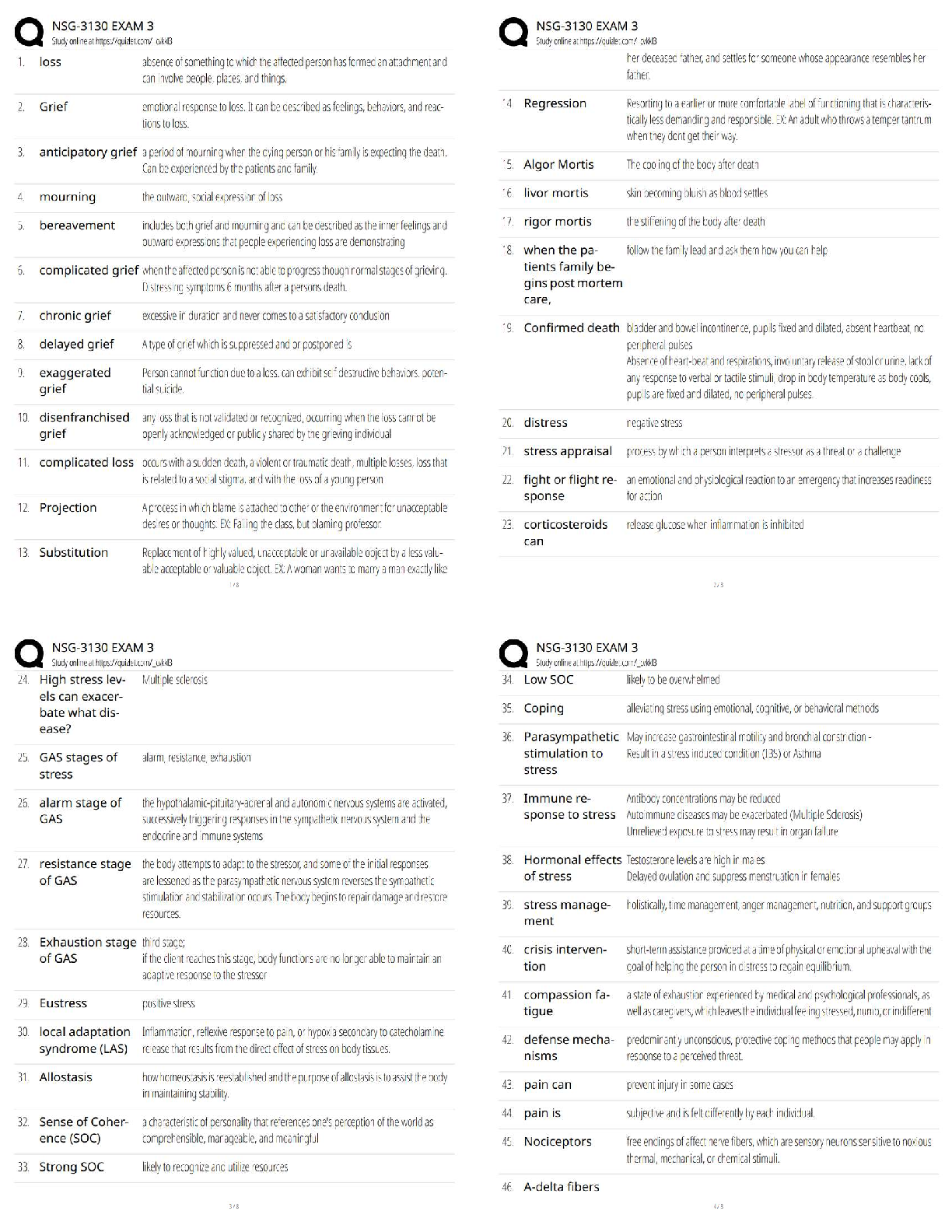
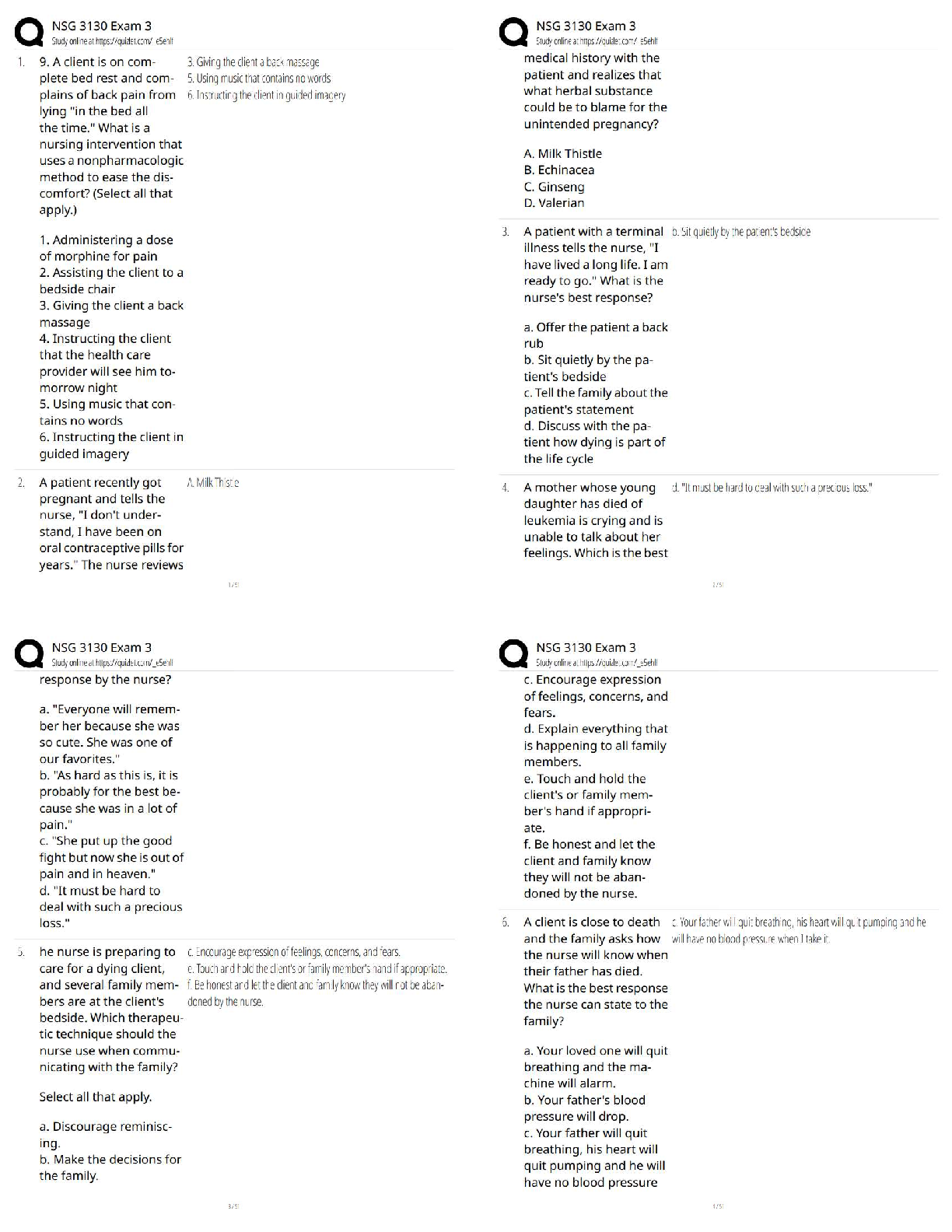
Assurance (C725), SET II
After determining the potential attack concepts, the next step in threat modeling is to
perform ______________ analysis. ______________ analysis is also known as
...
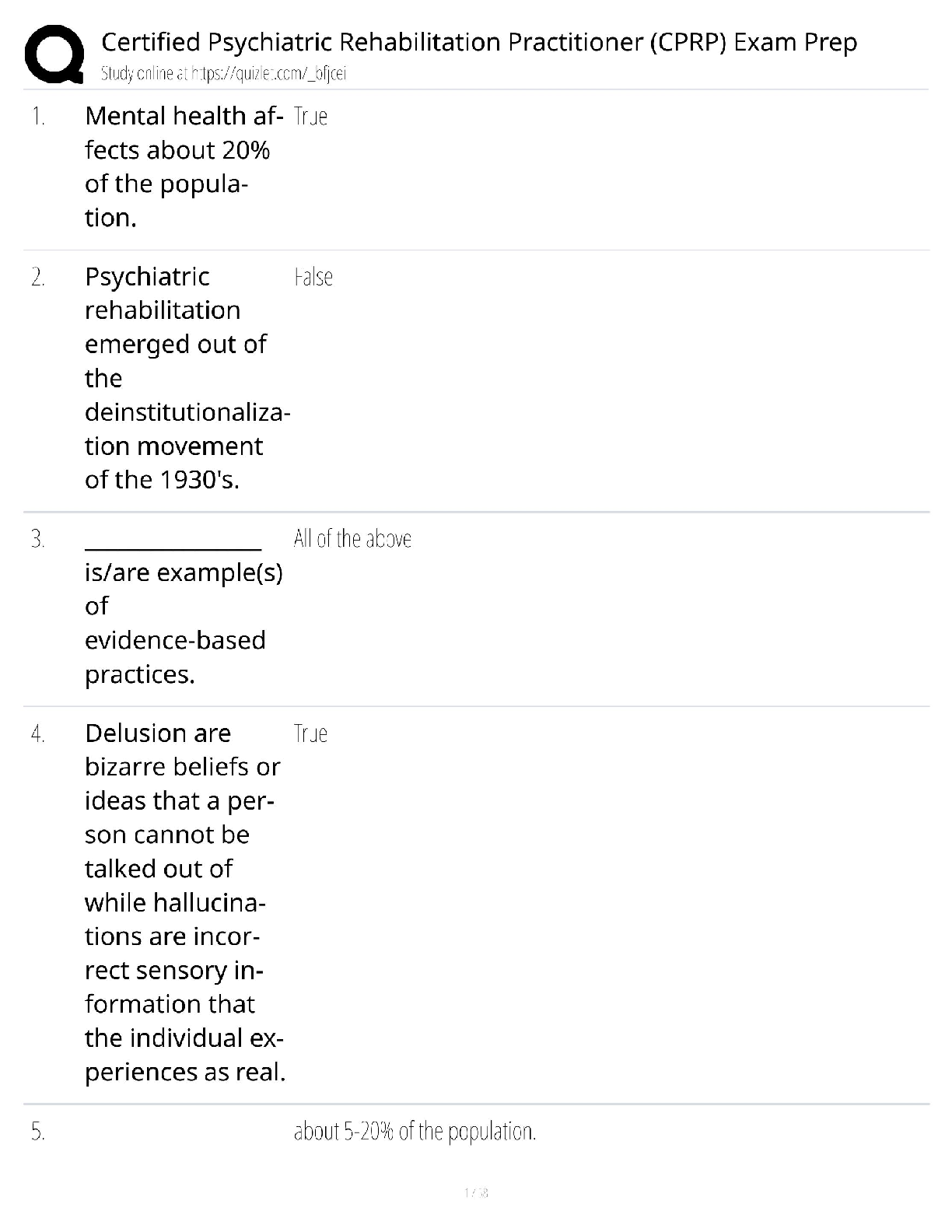
WGU, Information Security and
Assurance (C725), SET II
After determining the potential attack concepts, the next step in threat modeling is to
perform ______________ analysis. ______________ analysis is also known as
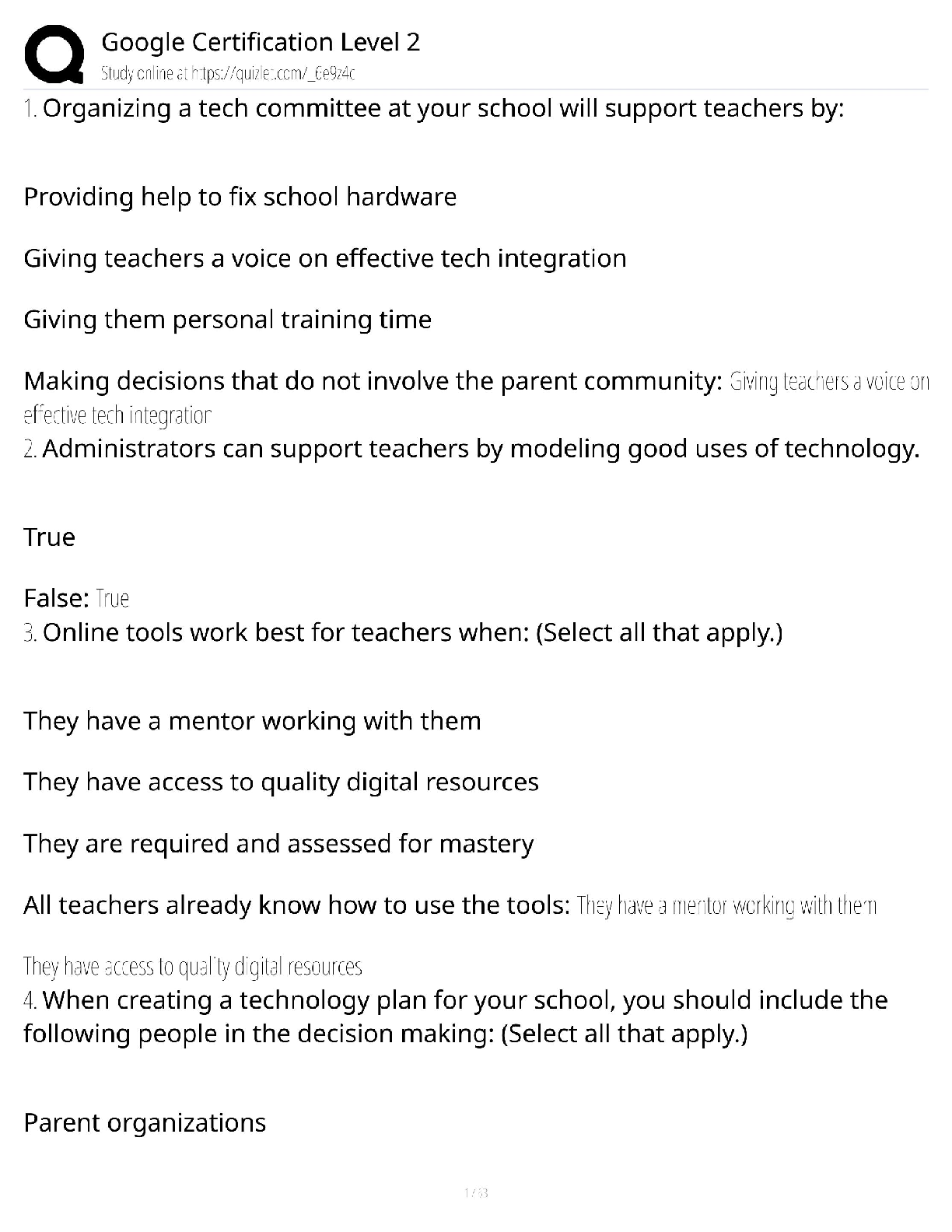
decomposing the application, system, or environment. The purpose of this task is to
gain a greater understanding of the logic of the product as well as its interactions with
external elements.Also known as decomposing the application - ✔✔Reduction analysis
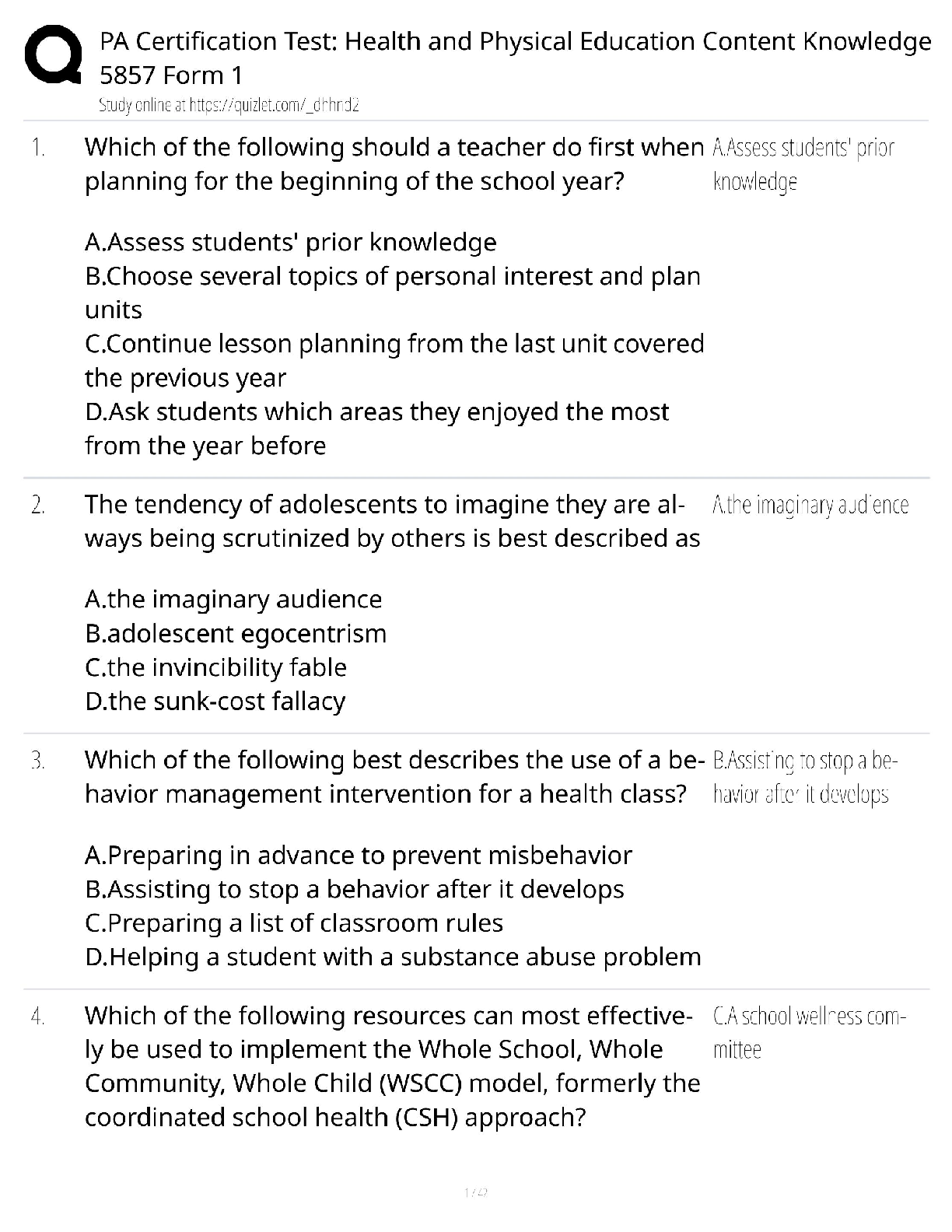
Whether an application, a system, or an entire environment, it needs to be divided into
smaller containers or compartments. Those might be subroutines, modules, or objects if
you're focusing on software, computers, or operating systems; they might be protocols if
you're focusing on systems or networks; or they might be departments, tasks, and
networks if you're focusing on an entire business infrastructure. Each identified subelement should be evaluated in order to understand inputs, processing, security, data
management, storage, and outputs.
Trust Boundaries, Data Flow Paths, Input Points, Privileged Operations, Details about
Security Stance and Approach - ✔✔The Five Key Concepts in the Decomposition
process.
In the decomposition process, any location where the level of trust or security changes.
- ✔✔Trust Boundaries
In the decomposition process, the movement of data between locations - ✔✔Data Flow
Paths
In the decomposition process, locations where external input is received - ✔✔Input
Points
In the decomposition process, any activity that requires greater privileges than of a
standard user account or process, typically required to make system changes or alter
security - ✔✔Privileged Operations
In the decomposition process, the declaration of the security policy, security
foundations, and security assumptions - ✔✔Details about Security Stance and
Approach
The concept that most computers, devices, networks, and systems are not built by a
single entity. - ✔✔supply chain
T or FWhen evaluating a third party for your security integration, you should consider the
following processes:On-Site Assessment, Document Exchange and Review,
Process/Policy Review, Third-Party Audit - ✔✔True
When engaging third-party assessment and monitoring services, keep in mind that the
external entity needs to show security-mindedness in their business operations. If an
external organization is unable to manage their own internal operations on a secure
basis, how can they provide reliable security management functions for yours?
Investigate the means by which datasets and documentation are exchanged as well as
the formal processes by which they perform assessments and reviews. - ✔✔Document
Exchange and Review
Visit the site of the organization to interview personnel and observe their operating
habits. - ✔✔On-Site Assessment
Request copies of their security policies, processes/procedures, and documentation of
incidents and responses for review. - ✔✔Process/Policy Review
Having an independent third-party auditor, as defined by the American Institute of
Certified Public Accountants (AICPA), can provide an unbiased review of an entity's
security infrastructure, based on Service Organization Control (SOC) (SOC) reports.
Statement on Standards for Attestation Engagements (SSAE) is a regulation that
defines how service organizations report on their compliance using the various SOC
reports. The SSAE 16 version of the regulation, effective June 15, 2011, was replaced
by SSAE 18 as of May 1, 2017. The SOC1 and SOC2 auditing frameworks are worth
considering for the purpose of a security assessment. The SOC1 audit focuses on a
description of security mechanisms to assess their suitability. The SOC2 audit focuses
on implemented security controls in relation to availability, security, integrity, privacy,
and confidentiality. For more on SOC audits, see AICPA.For all acquisitions, establish
minimum security requirements. These should be modeled from your existing security
policy. The security requirements for new hardware, software, or services should always
meet or exceed the security of your existing infrastructure. When working with an
external service, be sure to review any service-level agreement (SLA) to ensure that
security is a prescribed component of the contracted services. This could include
customization of service-level requirements for your specific needs. - ✔✔Third-Party
Audit
This is the collection of practices related to supporting, defining, and directing the
security efforts of an organization. This is closely related to and often intertwined with
corporate and IT governance. - ✔✔Security governance
[Show More]













.png)