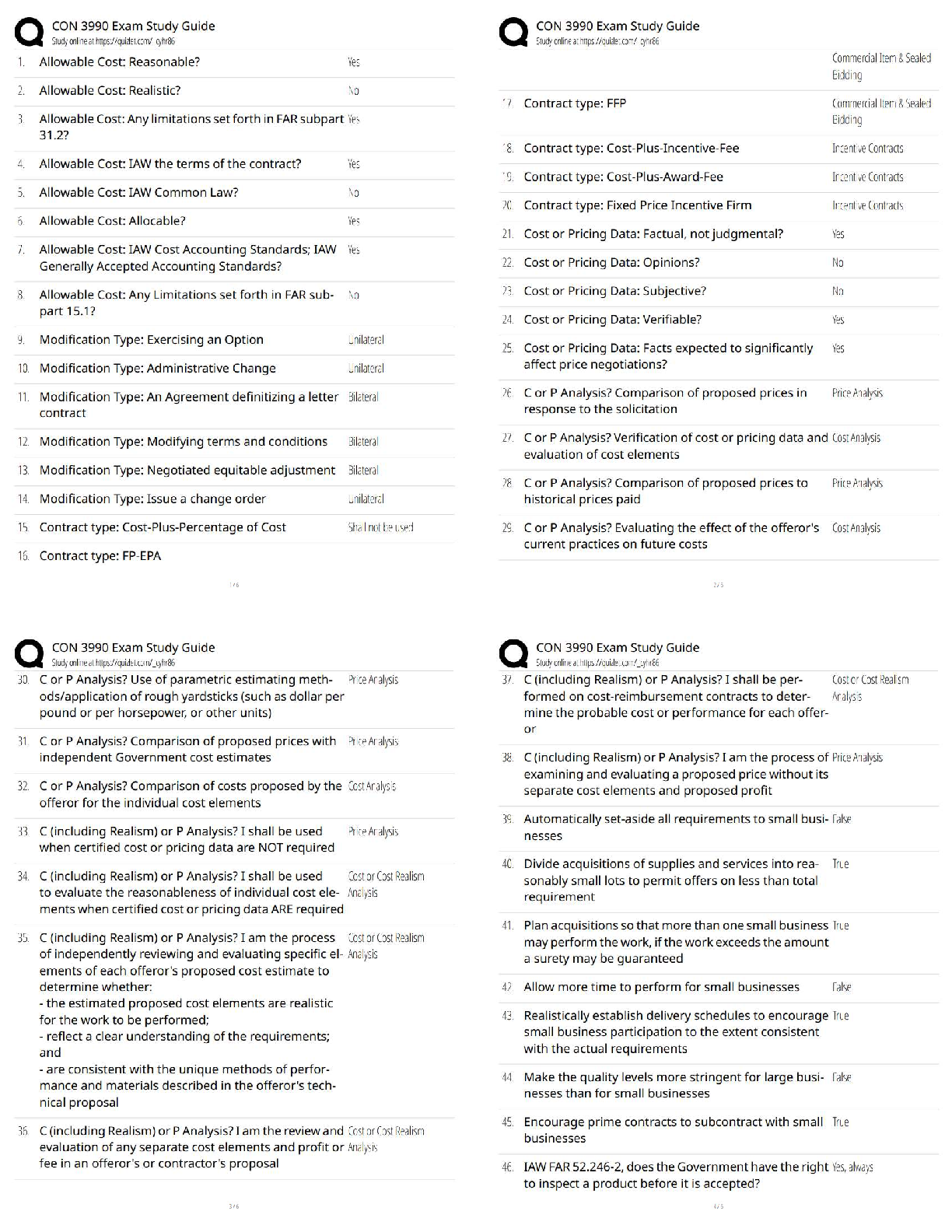
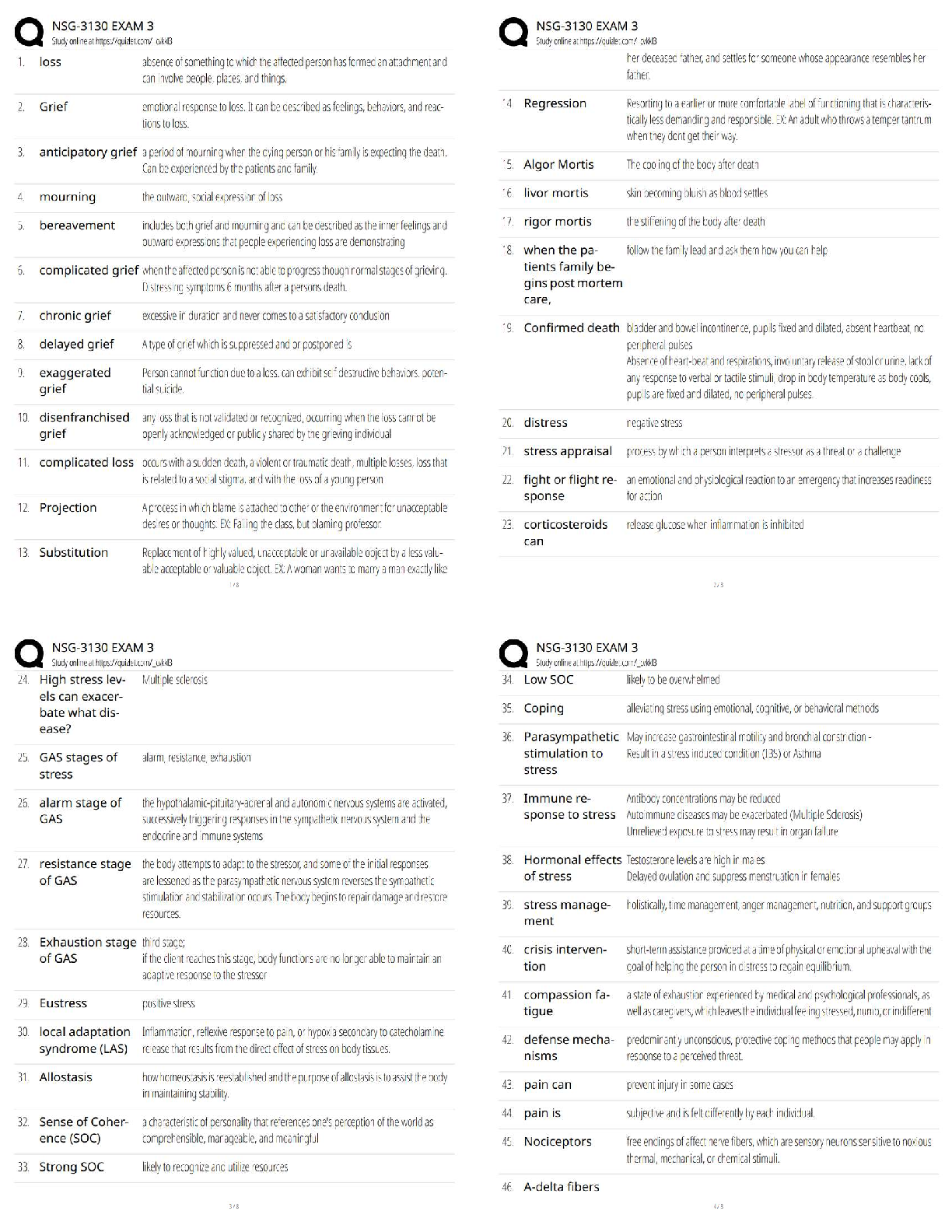
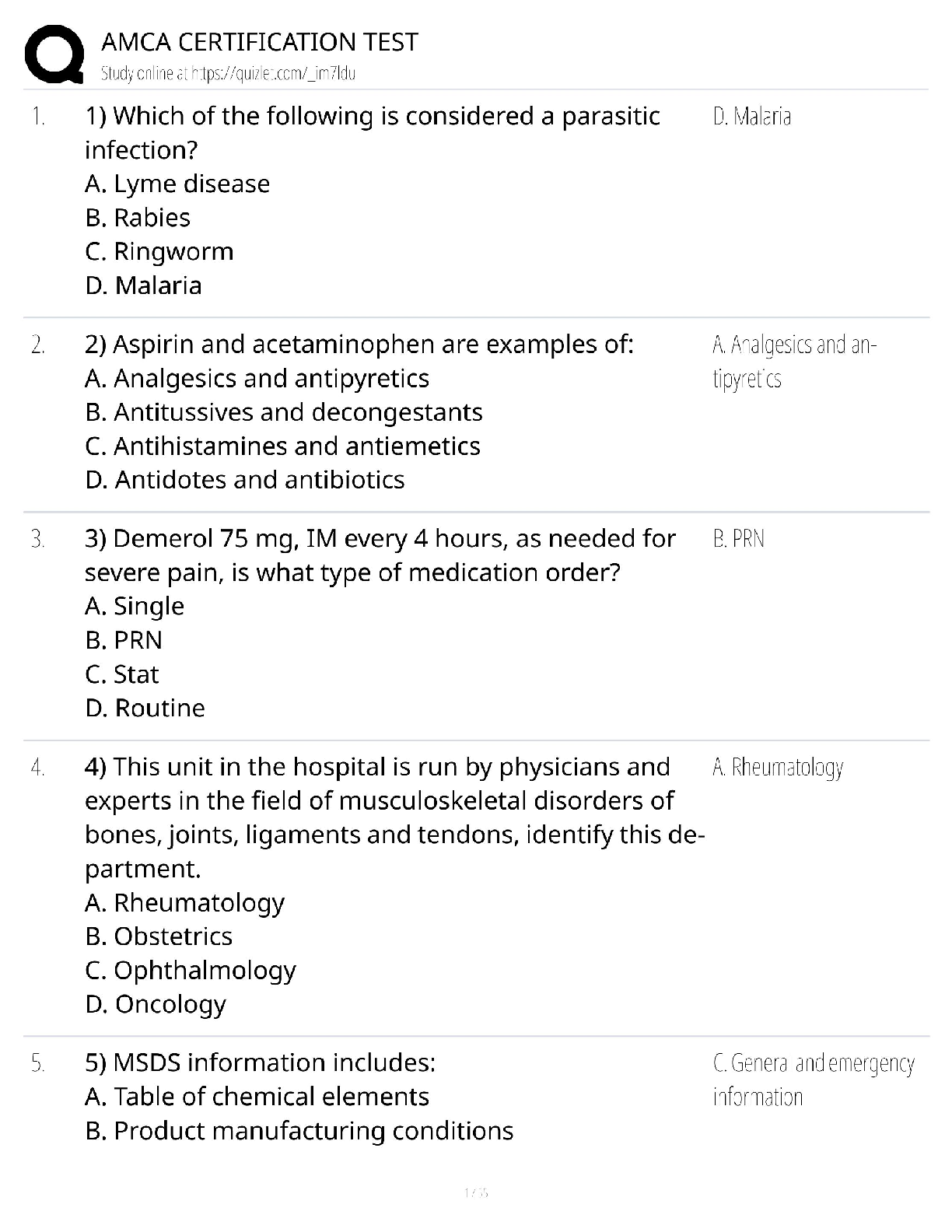
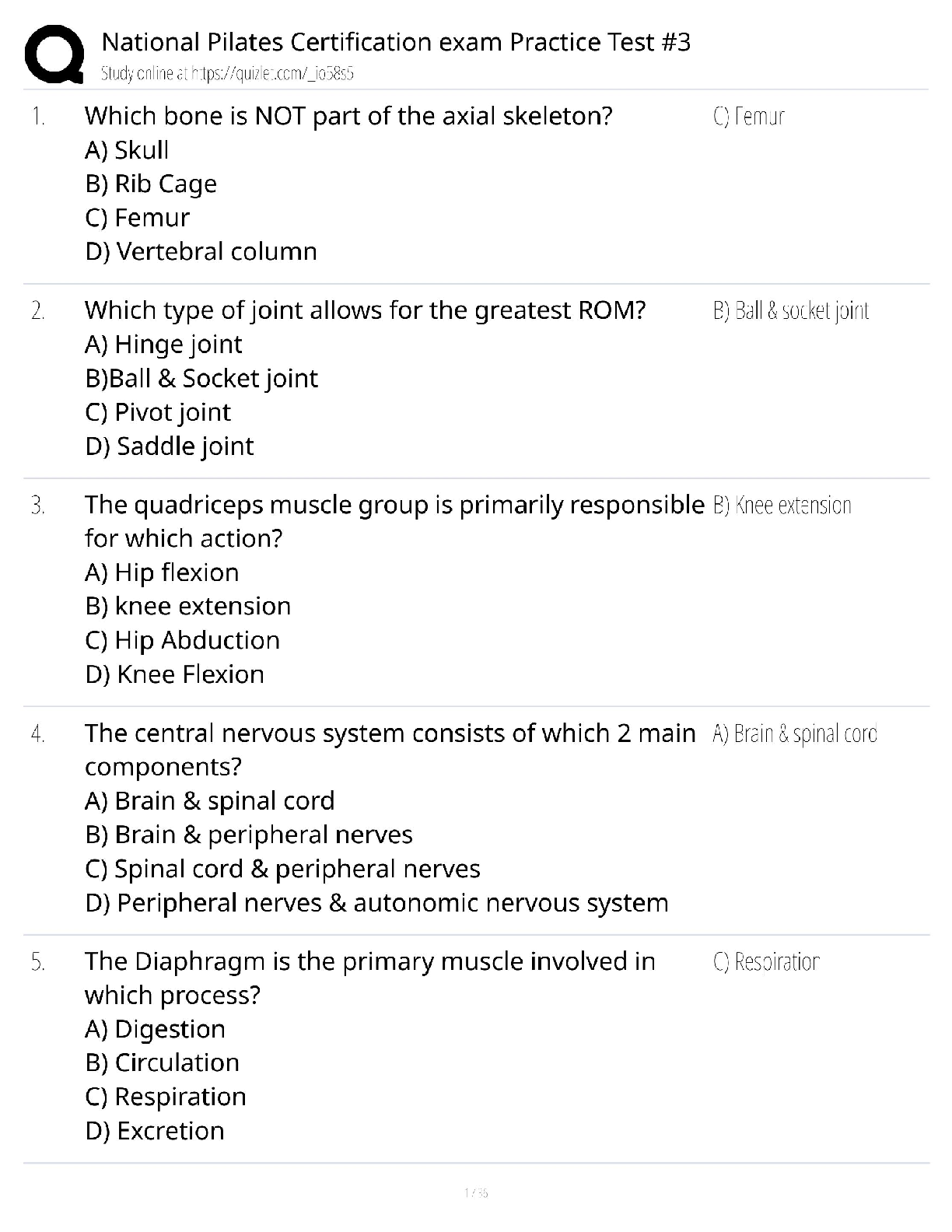
HIM 615 Interview Questions (Grand Canyon University) updated docs 2020
1. What is your role and title?
2. What degrees or certifications do you currently have?.
3. Do you have to recertify or any continuing educatio
...
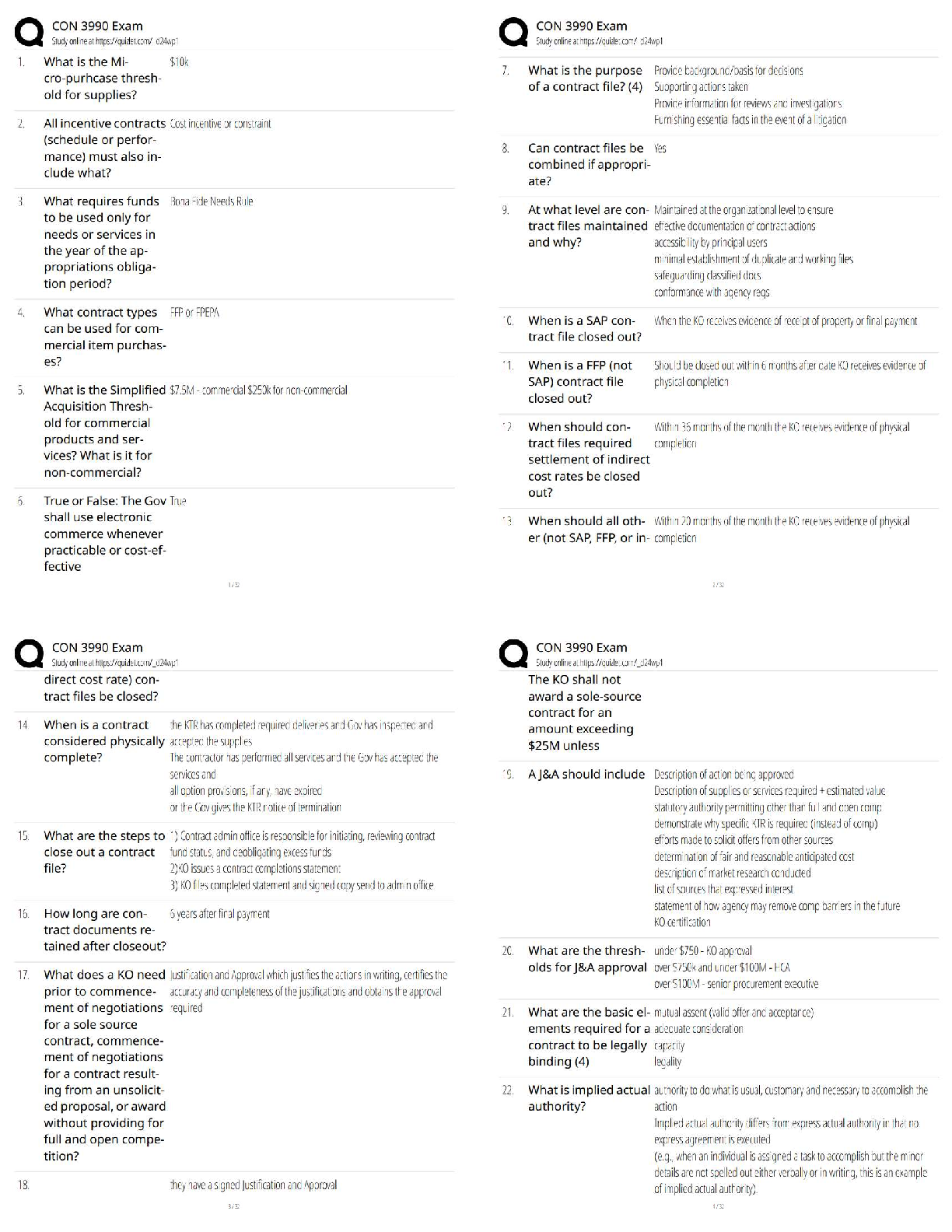
HIM 615 Interview Questions (Grand Canyon University) updated docs 2020
1. What is your role and title?
2. What degrees or certifications do you currently have?.
3. Do you have to recertify or any continuing education units to maintain IT security credentials?
4. What is your experience with Information Technology in the past? Have you worked in IT all of you career? If not, what other experience has led you to the IT field?
5. What is your professional involvement with the privacy and security of patient data and EHR hardware?
6. What are the components that are important to have a secure electronic environment?
7. How will you confront the breach reality?
8. What are the common security breaches, and how are these security breaches handled?
9. What are the biggest barriers in regards to protecting patient data and HIPAA, especially in the EHR?.
10. How is the data stored within the EHR safeguarded? (Role-based, Attribute-based, other)
11. Have you, or would you ever consider, hiring an individual who has been known to be a hacker? If no, why, and if yes what would the benefits to our organization be?
12. How will you work with the business relative to new initiatives and new technology?
13. How have you worked with and interacted with executive and business stakeholders to make security a strategic priority that translated to business value?
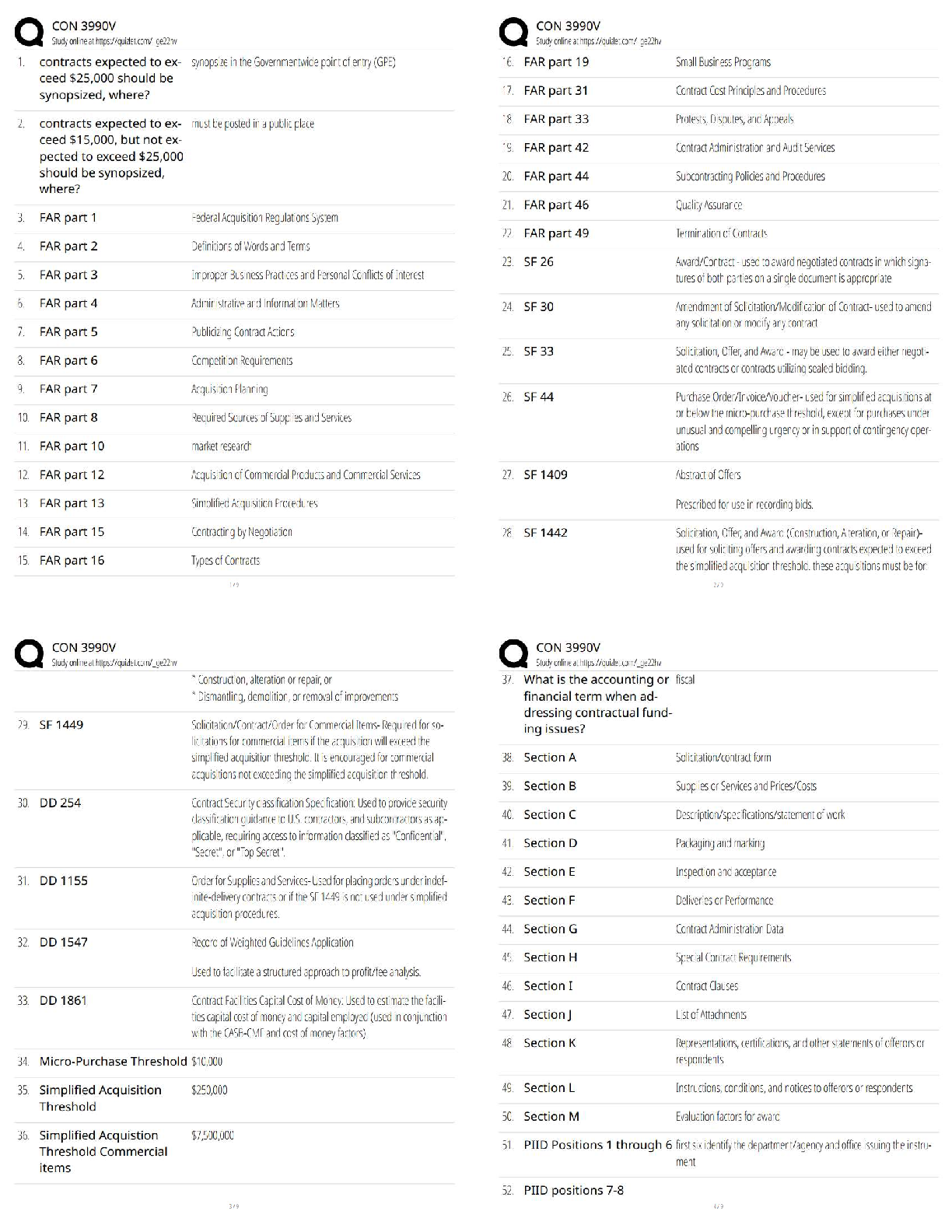
14. How will you ensure that no one person in the organization can take down a production environment?
15. How do you keep up with the latest security issues and methods?
16. What is the EHR your organization utilizes?
17. How are security credentials received for the EHR?
18. Who is accessing the system?
19. How do you protect the data in the EHR both internally and via VPN/mobile devices?
20. What are the organizational policies established to ensure patient data is secure?
21. Impending government regulations-How do you feel government regulations like HIPAA have shaped the info security discipline?
[Show More]



 answers.png)