Computer Science > EXAMs > Certified Hacking Forensic Investigator (CHFI) - Exam Prep (All)
Certified Hacking Forensic Investigator (CHFI) - Exam Prep
Document Content and Description Below
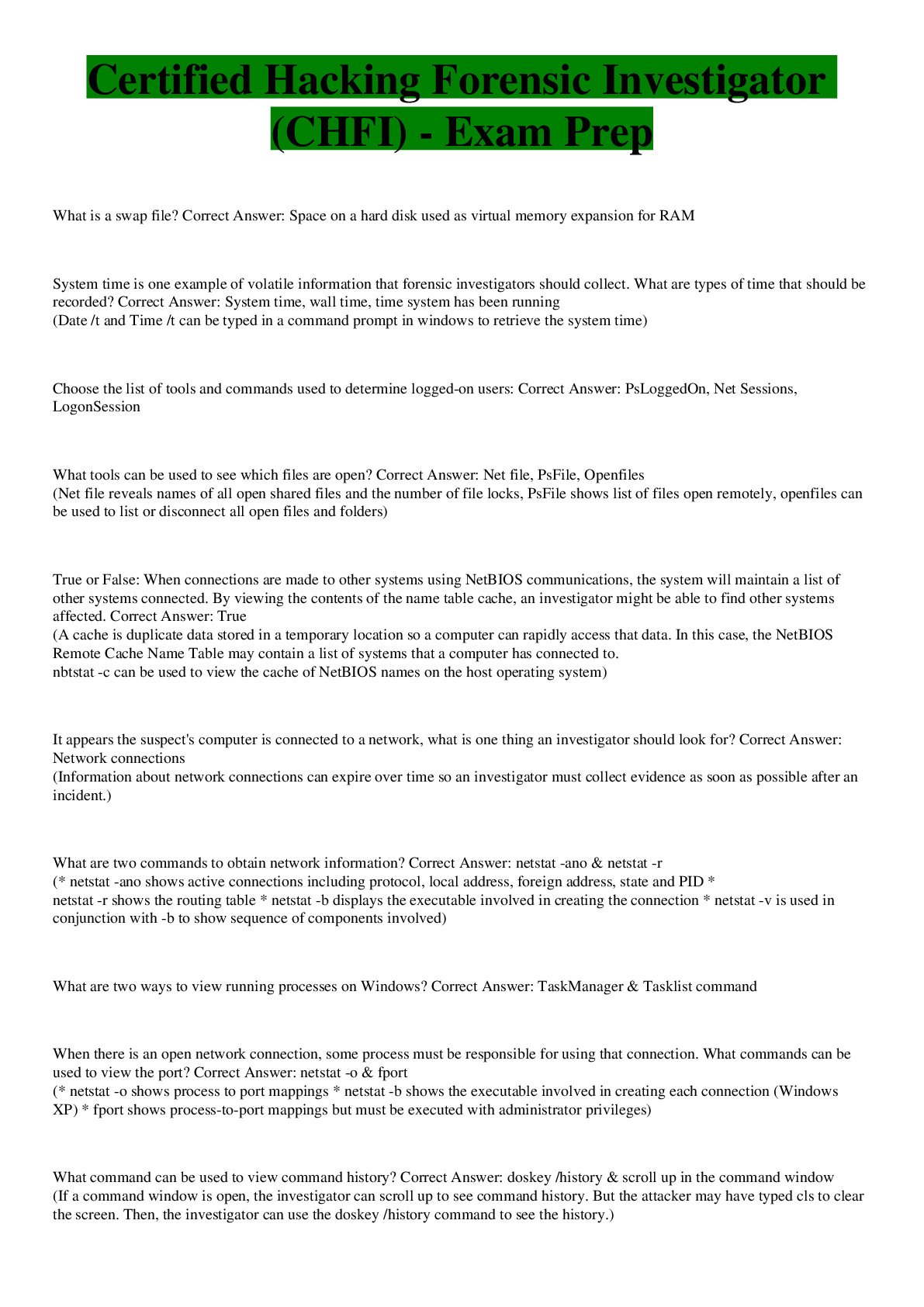
Certified Hacking Forensic Investigator (CHFI) - Exam Prep What is a swap file? Correct Answer: Space on a hard disk used as virtual memory expansion for RAM System time is one example of volat ... ile information that forensic investigators should collect. What are types of time that should be recorded? Correct Answer: System time, wall time, time system has been running (Date /t and Time /t can be typed in a command prompt in windows to retrieve the system time) Choose the list of tools and commands used to determine logged-on users: Correct Answer: PsLoggedOn, Net Sessions, LogonSession What tools can be used to see which files are open? Correct Answer: Net file, PsFile, Openfiles (Net file reveals names of all open shared files and the number of file locks, PsFile shows list of files open remotely, openfiles can be used to list or disconnect all open files and folders) True or False: When connections are made to other systems using NetBIOS communications, the system will maintain a list of other systems connected. By viewing the contents of the name table cache, an investigator might be able to find other systems affected. Correct Answer: True (A cache is duplicate data stored in a temporary location so a computer can rapidly access that data. In this case, the NetBIOS Remote Cache Name Table may contain a list of systems that a computer has connected to. nbtstat -c can be used to view the cache of NetBIOS names on the host operating system) It appears the suspect's computer is connected to a network, what is one thing an investigator should look for? Correct Answer: Network connections (Information about network connections can expire over time so an investigator must collect evidence as soon as possible after an incident.) What are two commands to obtain network information? Correct Answer: netstat -ano & netstat -r (* netstat -ano shows active connections including protocol, local address, foreign address, state and PID * netstat -r shows the routing table * netstat -b displays the executable involved in creating the connection * netstat -v is used in conjunction with -b to show sequence of components involved) What are two ways to view running processes on Windows? Correct Answer: TaskManager & Tasklist command When there is an open network connection, some process must be responsible for using that connection. What commands can be used to view the port? Correct Answer: netstat -o & fport (* netstat -o shows process to port mappings * netstat -b shows the executable involved in creating each connection (Windows XP) * fport shows process-to-port mappings but must be executed with administrator privileges) What command can be used to view command history? Correct Answer: doskey /history & scroll up in the command window (If a command window is open, the investigator can scroll up to see command history. But the attacker may have typed cls to clear the screen. Then, the investigator can use the doskey /history command to see the history.) What are two registry settings that could impact a forensic analysis and investigation? Correct Answer: ClearPageFileAtShutdown & DisableLastAccess (* ClearPageFileAtShutdown - tells the OS to clear the page file when the system is shut down. This will clear virtual memory in the swap file. * DisableLastAccess - disables updating of the last access times on files so the timestamp might not be accurate) What is the Index.dat file used for? Correct Answer: AutoComplete & Redundant information such as visited URLs, search queries, recently opened files (* Index.dat is used for redundant information such as AutoComplete information. * Index.dat can be found in the History folder for Internet Explorer) Which of the following is true about the swap file? Correct Answer: Hidden file in the root directory called pagefile.sys & Registry path is HKEY_LOCAL_MACHINE_SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management (The swap file can be organized as a contiguous space so fewer I/O operations are required to read and write. It is a hidden file in the root directory called pagefile.sys.) Each process of Windows is represented as an _______. Correct Answer: Executive process (Each process on a Windows system is represented as an executive process or EProcess. EProcess block is a data structure containing attributes of the process and pointers to threads and process environment blocks.) What command is used to view EProcess block? Correct Answer: dt -a -b -v _EPROCESS What is the most important element of EProcess? Correct Answer: PEB - Process Environment Block What are the six stages of process creation? Correct Answer: 1. Launch .exe: File Execution Options registry key is checked for debugger value. If yes, process starts over 2. EProcess object created along with KProcess, PEB, and initial address space 3. Initial thread created 4. Windows subsystem is notified of new process and thread 5. Execution of initial thread starts 6. Initialization of address space is complete for new process and thread True or False: The EProcess object is created along with KProcess, PEB, and initial address space Correct Answer: True What tool can parse memory? Correct Answer: Lsproc.pl d:\dumps\test-mem.dmp What is an important consideration for complete memory dump analysis? Correct Answer: Pagefile.sys (The swap file, called pagefile.sys, is virtual memory. Information in the swapfile must also be considered when analyzing memory.) What files contain pool headers? Correct Answer: Pooltag.txt (Windows memory manager generally allocates memory in 4KB pages. Sometimes, 4K would be too large and waste memory. So memory manager allocates several pages ahead of time thus keeping an available pool of memory.) What is the advantage of PMDump? Correct Answer: Dump contents of process memory without stopping the process What does HKEY_CURRENT_USER contain? Correct Answer: Active, loaded user profile for currently logged-on user What does HKEY_USERS hive contain? Correct Answer: All users profiles What does HKEY_LOCAL_MACHINE hive contain? Correct Answer: Configuration information for the system including hardware and software settings What does HKEY_CURRENT_CONFIG? Correct Answer: Hardware profile at startup What does HKEY_CLASSES_ROOT hive contain? Correct Answer: Configuration information relating to which application is used to open various files on the system What registry data type indicates raw binary data? Correct Answer: REG_BINARY What registry data type indicates 32-bit integer? Correct Answer: REG_DWORD What registry data type indicates fixed length text string? Correct Answer: REG_SZ What registry data type indicates variable length text string? Correct Answer: REG_EXPAND_SZ What registry data type indicates multiple strings separated by delimiter? Correct Answer: REG_MULTI_SZ What registry data type indicates no data type? Correct Answer: REG_NONE What registry data type indicates 64-bit integer? Correct Answer: REG_QWORD What registry data type indicates Unicode string naming a symbolic link? Correct Answer: REG_LINK What registry data type indicates series of nested arrays storing a resource list? Correct Answer: REG_RESOURCE_LIST What registry data type indicates series of nested arrays storing a device driver's list? Correct Answer: REG_RESOURCE_REQUIREMENTS_LIST What registry data type indicates series of nested arrays storing a resource list used by physical hardware device? Correct Answer: REG_FULL_RESOURCE_DESCRIPTOR [Show More]
Last updated: 3 years ago
Preview 1 out of 194 pages
Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$15.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Jul 14, 2022
Number of pages
194
Written in
All
Additional information
This document has been written for:
Uploaded
Jul 14, 2022
Downloads
0
Views
54