WGU C724 : Unit 7 - Module 11 (Quiz Review)
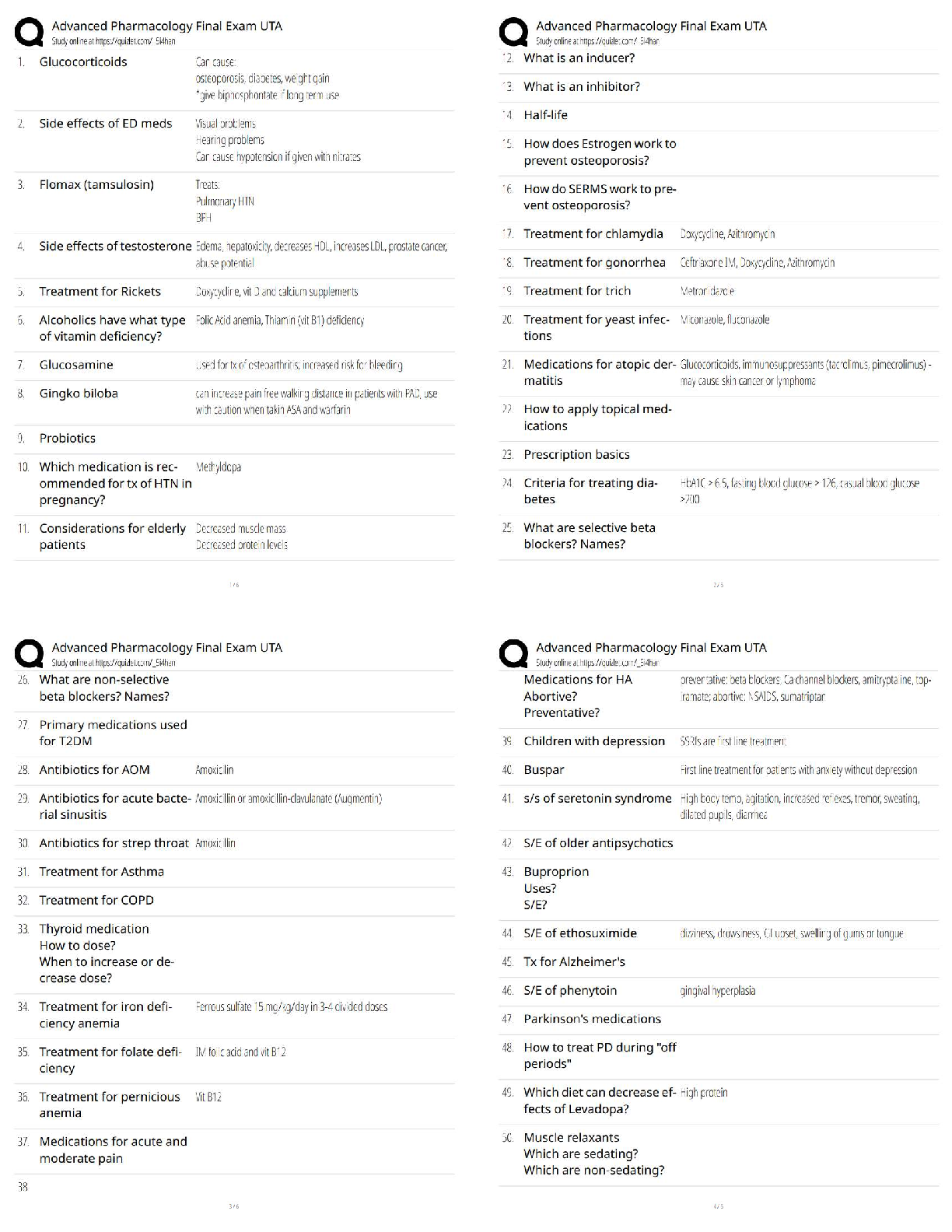
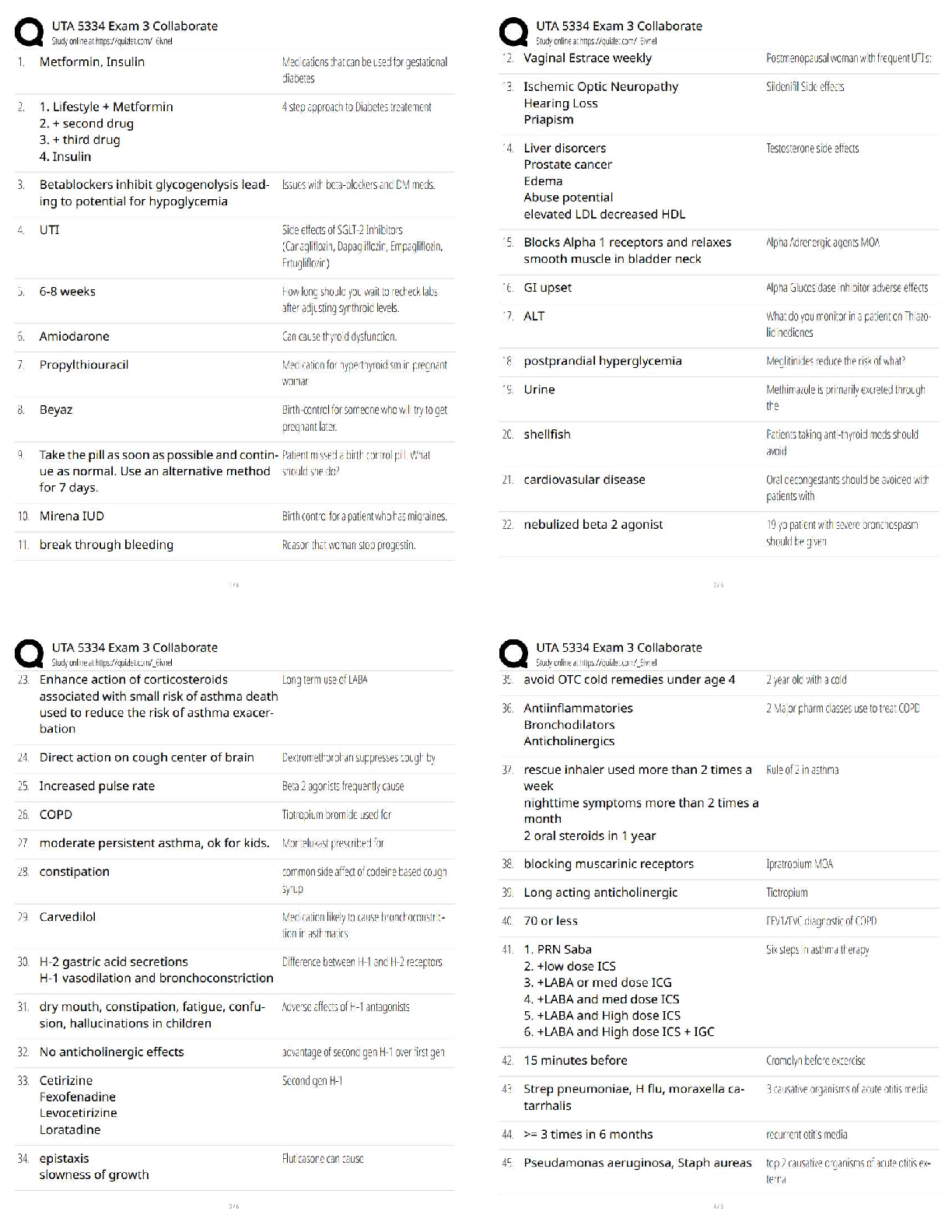
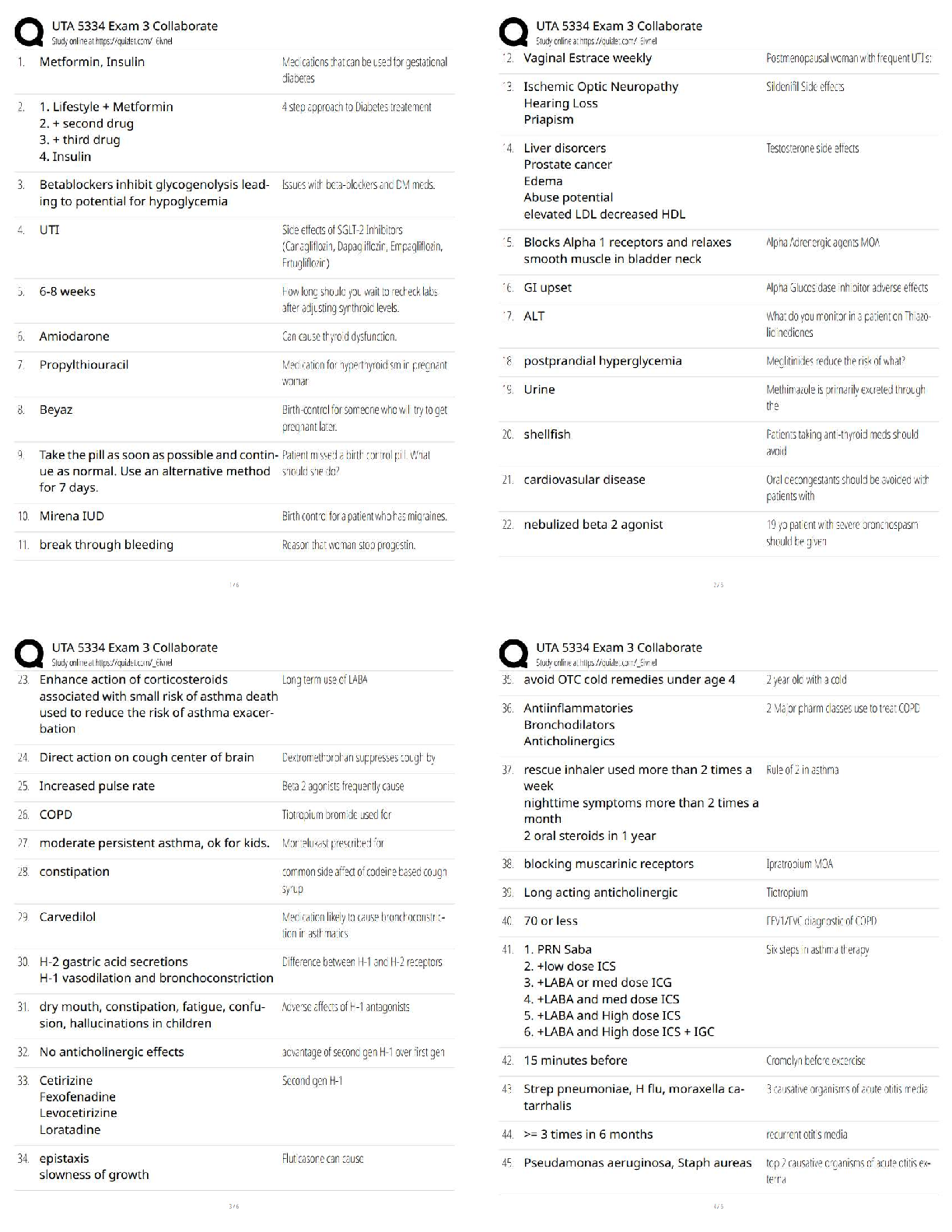
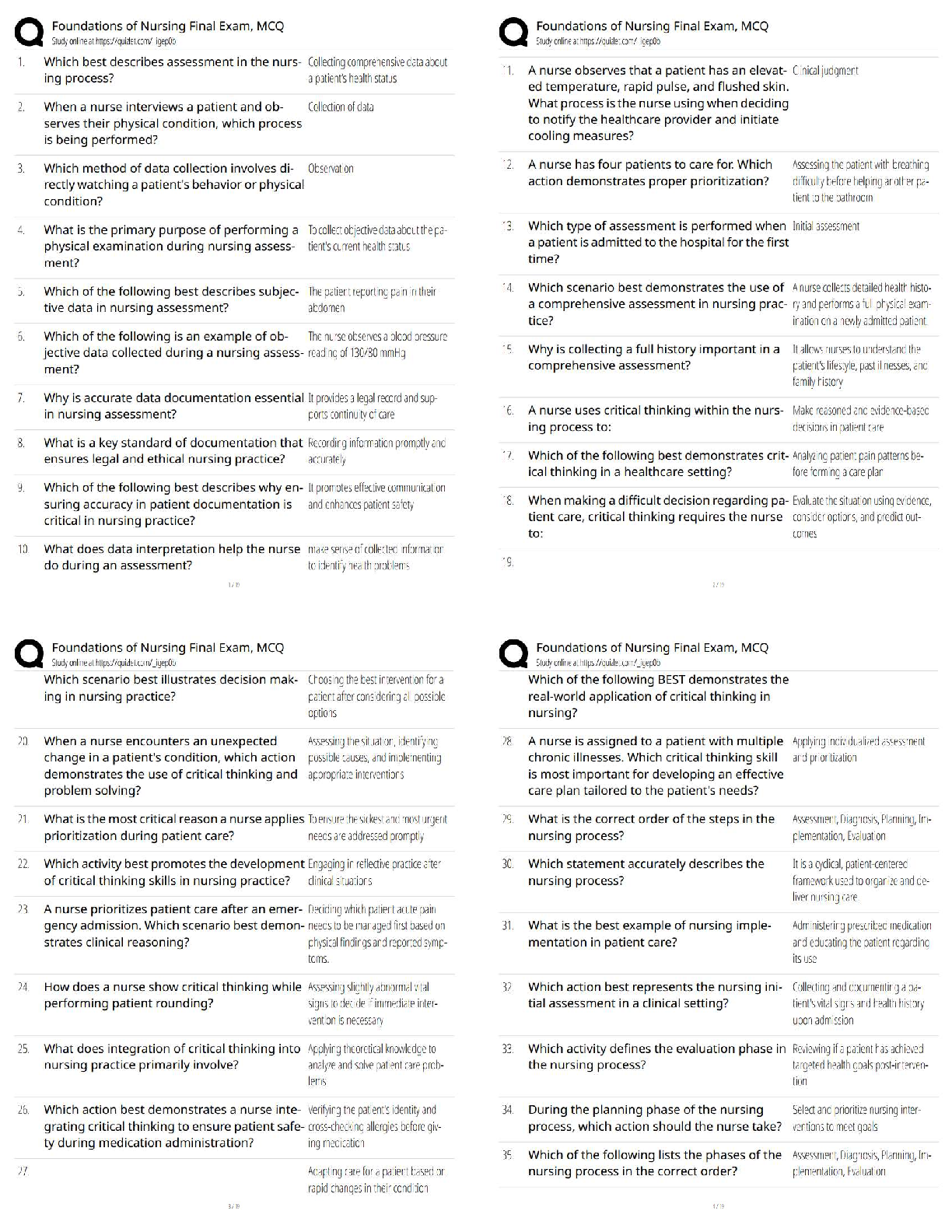
What is the primary goal of information security? Correct answer- Reduce losses related to losses in confidentiality, availability and integrity.
There are many differe
...
WGU C724 : Unit 7 - Module 11 (Quiz Review)
What is the primary goal of information security? Correct answer- Reduce losses related to losses in confidentiality, availability and integrity.
There are many different kinds of malware, which could be a spyware, worm, virus, or Trojan horse. In general, any _______________________________________ that is downloaded and stored on a computer hard drive can cause undesirable damage to the computer or network system. Correct answer- Virus
There are several low-tech attacks that criminals can use to steal sensitive information from individuals in public places. One of the most common methods is ____________________________, in which individuals are offered a gift for completing an application for a credit card. Correct answer- Quid Pro Quo
The U.S. government enacted legislation and regulations to protect privacy and do what else? Correct answer- Enact and enforce security, and manage and retain documentation - Such laws and regulations include the Health Insurance Portability and Accountability Act (HIPAA) of 1996, the Financial Services Modernization Act (aka Gramm-Leach-Bliley Act) of 1999, and the Public Company Accounting Reform and Investor Act (aka Sarbanes-Oxley Act) of 2002.
What can be used to counter the risks, vulnerabilities, and threats experienced by managers in organizations? Correct answer- Security Measures
Which of the following is NOT a component of an organization's framework for security and control? Correct answer- Cost-Benefit Analysis
[True/False] To gain entry to secured location at airports or the building of some government agencies, a photo identification (which is classified as a knowledge authentication method) is all you need to have. Correct answer- False - Photo identification is an identity method, not knowledge method.
Computer-based actions are actions that involved the use of a computer. Which of the following is NOT a computer-based action? Correct answer- Randomizing your online behavior - a behavioral action that can help to deter cyber attack.
The disaster recovery plan (DRP) addresses several issues when an emergency occurs. What item below would NOT be addressed in a DRP? Correct answer- Businesses perform regular backups for operational databases.
Which of the following networks is the easiest for someone to gain access to? Correct answer- Wireless Networks - not all wireless routers are secure and protected, so access is open.
(Select all that apply). People access the Internet all the time. What is considered acceptable online cond
[Show More]
.png)









.png)