Computer Science > QUESTIONS & ANSWERS > WGU- C725 Questions and Answers with Complete Solutions (All)
WGU- C725 Questions and Answers with Complete Solutions
Document Content and Description Below
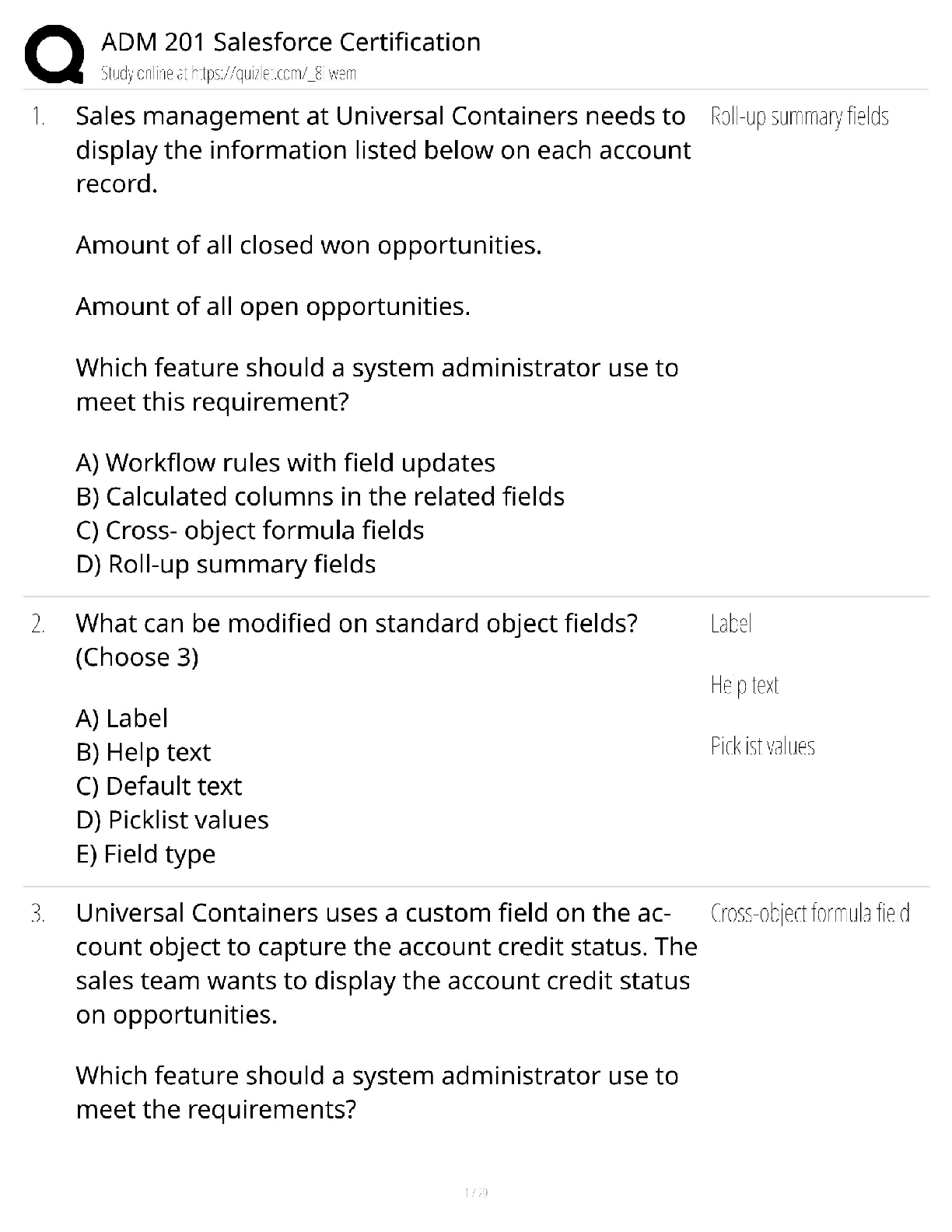
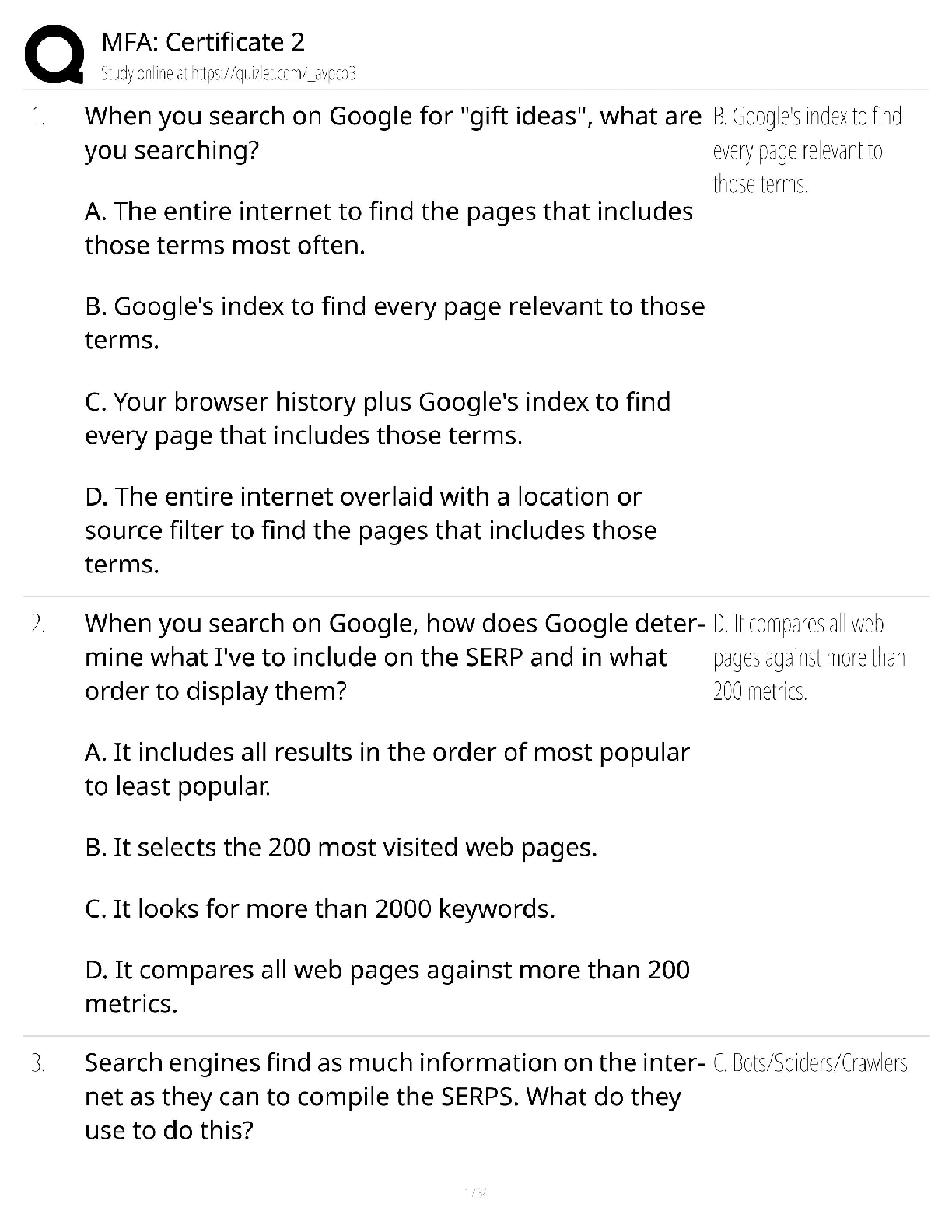
WGU- C725 Questions and Answers with Complete Solutions SOX (Sarbanes-Oxley Act) ✔✔Requires corporate executives to review and modernize their company's financial reporting systems. GLBA (Gram ... m-Leach-Bliley Act) ✔✔Known as the Financial Modernization Act of 1999. It is a United States federal law that requires financial institutions to explain how they share and protect their customers' private information. To be GLBA compliant, financial institutions must communicate to their customers how they share the customers' sensitive data, inform customers of their right to opt-out if they prefer that their personal data not be shared with third parties. What are the three methods of sanitization? ✔✔Overwriting Deguassing Destruction Mandatory Access Control (MAC) ✔✔Uses security labels for access control. Highly restrictive, usually used within government agencies. E.g. TS, SCI, etc. Discretionary Access Control (DAC) ✔✔A means of restricting access to objects based on the identity of subjects and/or groups to which they belong. What are the problems with passwords? ✔✔Passwords can be insecure, and easily broken. Dictionary words are not advised. Passwords are inconvenient, and repudiable. RADIUS ✔✔Remote Access Dial-In User Service; client/server protocol and software that enables remote access users to communicate with a central server to authenticate dial-in users and authorize their access to the requested system or service. Cryptosystem ✔✔is the hardware or software implementation that transforms plaintext into ciphertext (encrypting it) and back into plaintext (decrypting it). Cryptography ✔✔the art of protecting information by transforming it into an unreadable format, called cipher text Cryptanalysis ✔✔The science or art of breaking a cryosystem Cryptology ✔✔The umbrella study of cryptography and cryptanalysis Cryptographers rely on two basic methods of disguising messages ✔✔Transposition, in which letters are rearranged into a different order Substitution, in which letters are replaced by other letters and/or symbols. Symmetric Key Encryption ✔✔Encryption system in which a single key is used for both encryption and decryption. DES. 3DES. AES. Asymmetric Key Encryption ✔✔Encryption system when a different key is used to encrypt and to decrypt. PGP. Rijndael ✔✔This is a block cipher adopted as the Advanced Encryption Standard (AES) by the United States government to replace DES. Although Rijndael supports multiple block sizes, as AES, the block size is fixed at 128 bits. DES ✔✔Symmetric block, 56-bit Triple DES ✔✔Symmetric cipher that applies DES three times to each block of data during the encryption process. 112 bit. AES ✔✔advanced encryption standard, a symmetric uses variable length Pretty Good Privacy (PGP) ✔✔A method of encrypting and decrypting e-mail messages. It can also be used to encrypt a digital signature. Uses RSA. Which ISO/OSI layer defines how to address the physical devices on the network? ✔✔The data link layer handles the transfer of data across the network media. The data link layer handles the moving of data into and out of a physical link in a network. The data link layer is layer 2 in the Open Systems Interconnection (OSI) architecture model for a set of telecommunication protocols. What two modes can IPSEC run in? ✔✔Transport mode, in which protection is applied to upperlayer protocols (TCP or UDP) Tunnel mode, in which an entire IP packet is wrapped inside a new IP packet and attached with a new IP header before it's transmitted through the public network Internet Key Exchange (IKE) ✔✔A protocol that provides the authentication material used to create the keys exchanged by ISAKMP during peer authentication in IPsec. Also sometimes referred to as IPsec Key Exchange. Software Development Life Cycle ✔✔The process that a program goes through. It consists of the development, maintenance, and demise of a software system. The phases include analysis, design, coding, testing/verification, maintenance, and obsolescence STRIDE ✔✔Spoofing Tampering Repudiation Information Disclosure Denial of Service Elevation of Privilege STRIDE- Spoofing ✔✔Authenticity STRIDE- Tampering ✔✔Integrity STRIDE- Information Disclosure ✔✔Confidentiality STRIDE- DOS ✔✔Availability STRIDE- Escalation of Privileges ✔✔Authorization How is the Building Security in Maturity Model (BSIMM) used to measure the maturity of a software assurance program? ✔✔By looking for evidence of security activities in the SDLC Which statement best defines BSIMM? [Show More]
Last updated: 3 years ago
Preview 1 out of 4 pages
.png)
Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Also available in bundle (1)
Click Below to Access Bundle(s)
.png)
WGU C725 Bundled Exams Questions and Answers with Complete Solutions
WGU C725 Bundled Exams Questions and Answers Latest Updated 2022 Rated A
By Nutmegs 3 years ago
$20
13
Reviews( 0 )
$9.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Aug 16, 2022
Number of pages
4
Written in
All
Additional information
This document has been written for:
Uploaded
Aug 16, 2022
Downloads
0
Views
145








.png)