Computer Science > QUESTIONS & ANSWERS > Official CompTIA Security+ Study Guide (Exam SY0-601) Latest 2022 with complete solution (All)
Official CompTIA Security+ Study Guide (Exam SY0-601) Latest 2022 with complete solution
Document Content and Description Below
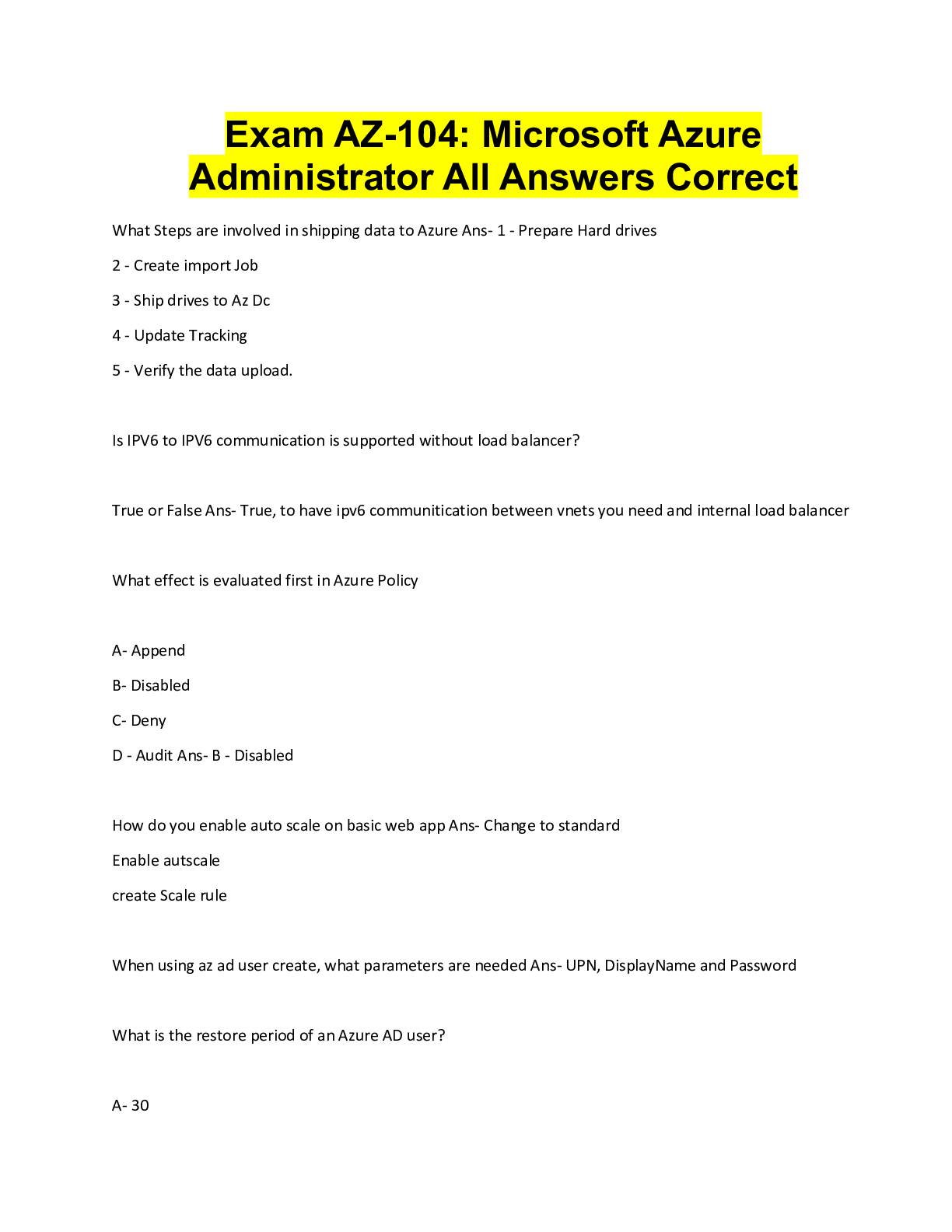
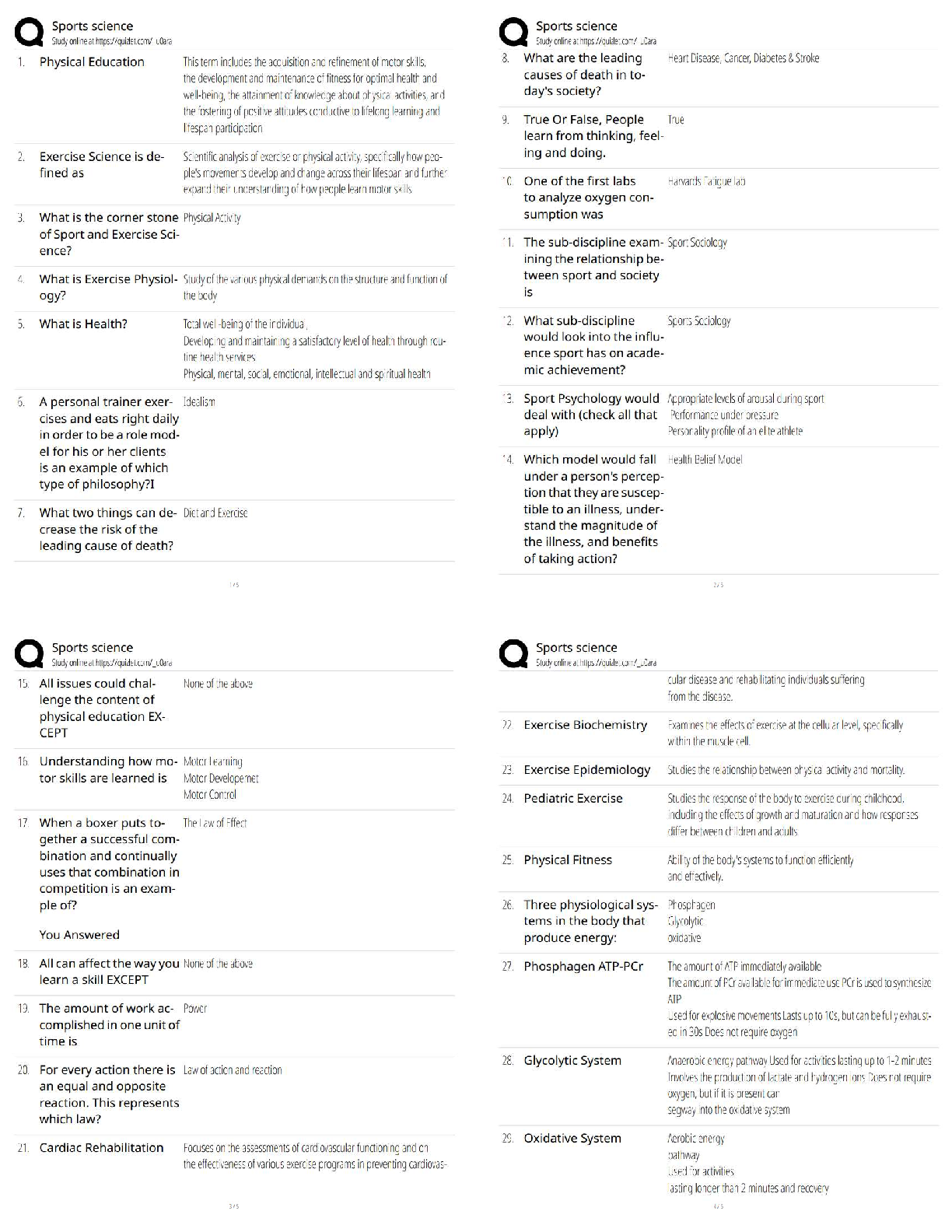
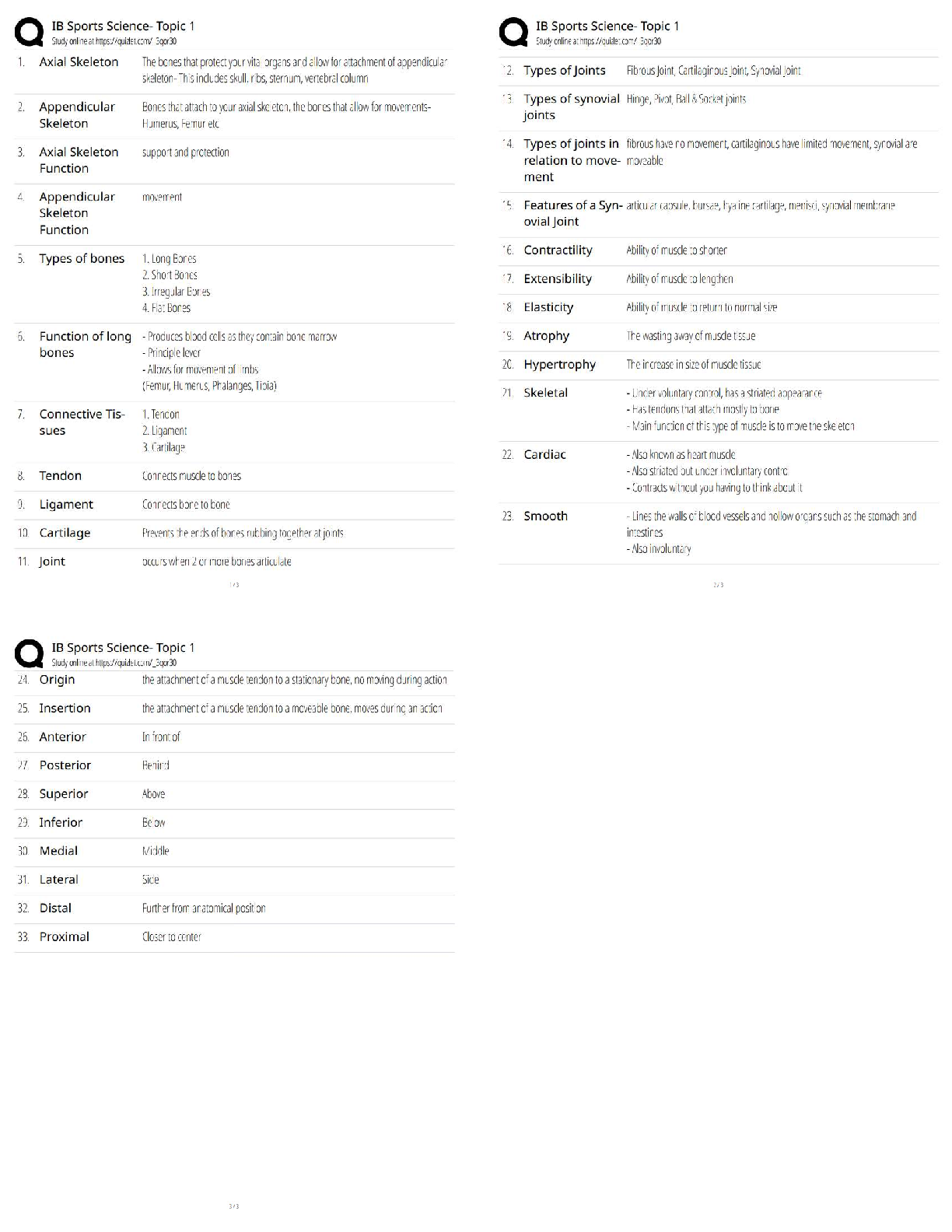
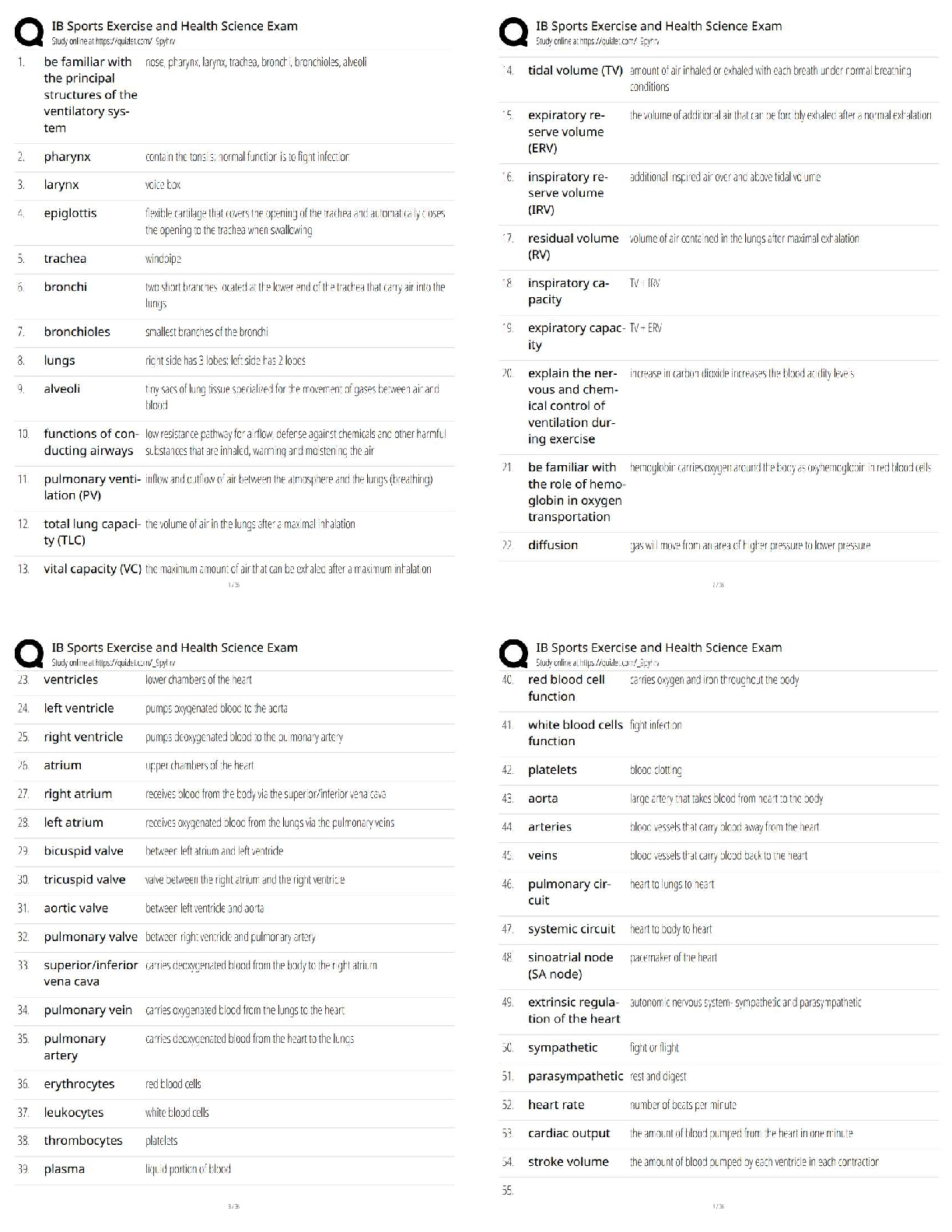
Official CompTIA Security+ Study Guide (Exam SY0-601) Latest 2022 with complete solution AAA (authentication, authorization, and accounting) -Answer- A security concept where a centralized platform ... verifies subject identification, ensures the subject is assigned relevant permissions, and then logs these actions to create an audit trail. ABAC (attribute-based access control) -Answer- An access control technique that evaluates a set of attributes that each subject possesses to determine if access should be granted. account policies -Answer- A set of rules governing user security information, such as password expiration and uniqueness, which can be set globally. ACL (Access Control List) -Answer- A collection of access control entries (ACEs) that determines which subjects (user accounts, host IP addresses, and so on) are allowed or denied access to the object and the privileges given (read only, read/write, and so on). active defense -Answer- The practice of responding to a threat by destroying or deceiving a threat actor's capabilities. adversarial AI (adversarial artificial intelligence) -Answer- Using AI to identify vulnerabilities and attack vectors to circumvent security systems. AES (Advanced Encryption Standard) -Answer- A symmetric 128-, 192-, or 256-bit block cipher based on the Rijndael algorithm developed by Belgian cryptographers Joan Daemen and Vincent Rijmen and adopted by the U.S. government as its encryption standard to replace DES. Agile model (Agile) -Answer- A software development model that focuses on iterative and incremental development to account for evolving requirements and expectations. AH (authentication header) -Answer- An IPSec protocol that provides authentication for the origin of transmitted data as well as integrity and protection against replay attacks. air gap -Answer- A type of network isolation that physically separates a network from all other networks. AIS (Automated Indicator Sharing) -Answer- Threat intelligence data feed operated by the DHS. ALE (annual loss expectancy) -Answer- The total cost of a risk to an organization on an annual basis. This is determined by multiplying the SLE by the annual rate of occurrence (ARO).AP (access point) -Answer- A device that provides a connection between wireless devices and can connect to wired networks. Also known as wireless access point or WAP. API (application programming interface) -Answer- A library of programming utilities used, for example, to enable software developers to access functions of the TCP/IP network stack under a particular operating system. application aware firewall -Answer- A Layer 7 firewall technology that inspects packets at the Application layer of the OSI model. application firewall -Answer- Software designed to run on a server to protect a particular application such as a web server or SQL server. APT (advanced persistent threat) -Answer- An attacker's ability to obtain, maintain, and diversify access to network systems using exploits and malware. Arduino -Answer- Open-source platform producing programmable circuit boards for education and industrial prototyping. ARO (annual rate of occurrence) -Answer- In risk calculation, an expression of the probability/likelihood of a risk as the number of times per year a particular loss is expected to occur. ARP inspection -Answer- An optional security feature of a switch that prevents excessive ARP replies from flooding a network segment. ARP poisoning (ARP spoofing) -Answer- A network-based attack where an attacker with access to the target local network segment redirects an IP address to the MAC address of a computer that is not the intended recipient. This can be used to perform a variety of attacks, including DoS, spoofing, and Man-in-the-Middle. asymmetric algorithm (Public Key) -Answer- A cipher that uses public and private keys. The keys are mathematically linked, using either Rivel, Shamir, Adleman (RSA) or elliptic curve cryptography (ECC) algorithms, but the private key is not derivable from the public one. An asymmetric key cannot reverse the operation it performs, so the public key cannot decrypt what it has encrypted, for example. Also known as Elliptic Curve Cryptography or ECC. ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) -Answer- A knowledge base maintained by the MITRE Corporation for listing and explaining specific adversary tactics, techniques, and procedures. attack surface -Answer- The points at which a network or application receives external connections or inputs/outputs that are potential vectors to be exploited by a threat actor.attack vector -Answer- A specific path by which a threat actor gains unauthorized access to a system. Also known as vector. [Show More]
Last updated: 3 years ago
Preview 1 out of 45 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Also available in bundle (1)
Click Below to Access Bundle(s)

CompTIA Security+ SY0-601 Practice, Study Guide, Exam Review and Exam Questions with Answers Combined Bundle Solution
COMPTIA SECURITY+ SY0-601 BEST EXAM STUDY GUIDE SOLUTION 2022/2023 BEST Security+ SY0-601 EXAM STUDY with Complete Solutions SY0-501 - CompTIA Security+ Certification Exam Questions with Answers...
By Excel 3 years ago
$14
12
Reviews( 0 )
$11.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Aug 26, 2022
Number of pages
45
Written in
All
Additional information
This document has been written for:
Uploaded
Aug 26, 2022
Downloads
0
Views
355