Computer Science > QUESTIONS & ANSWERS > DoD Information Security and Insider Threat Answered 2022 (100% Correct) (All)
DoD Information Security and Insider Threat Answered 2022 (100% Correct)
Document Content and Description Below
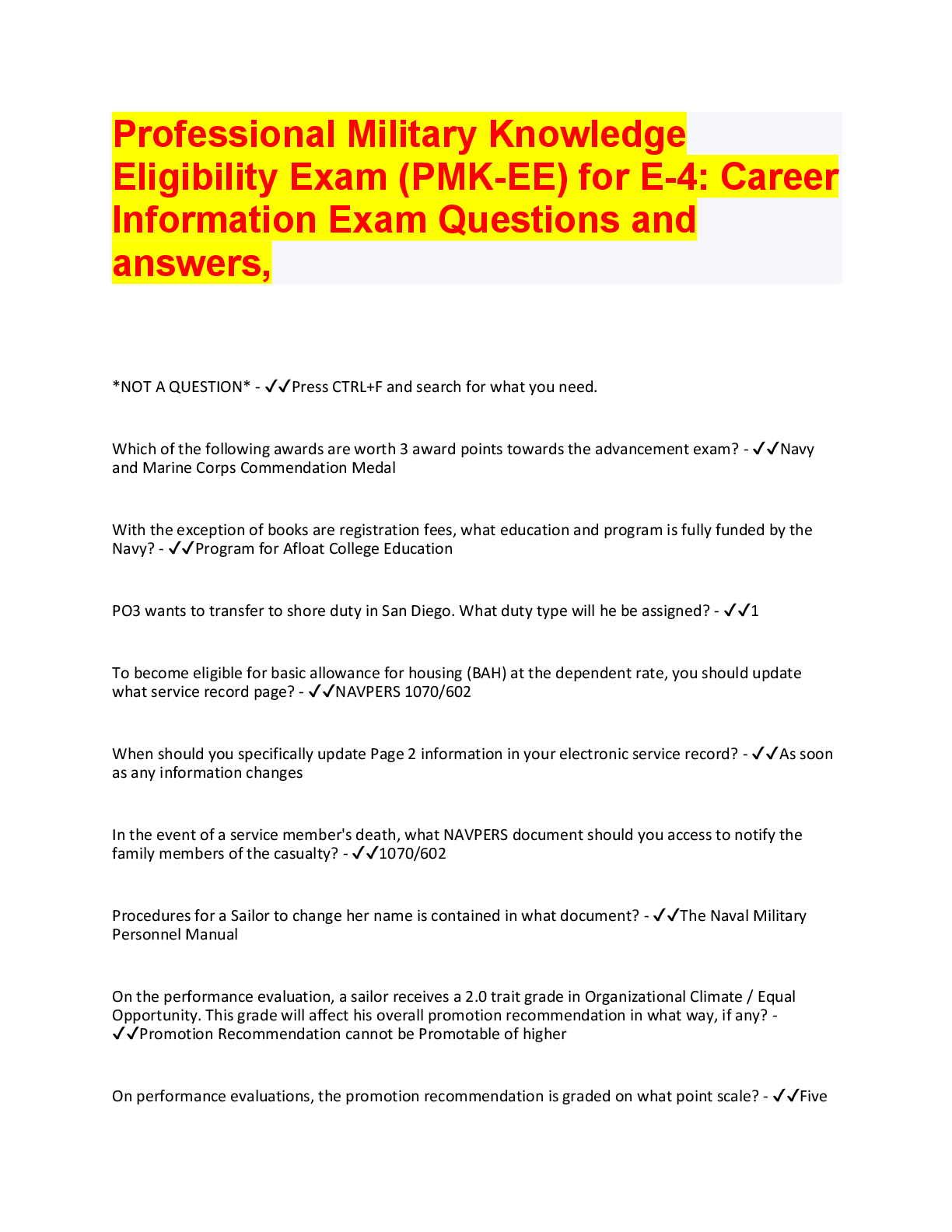
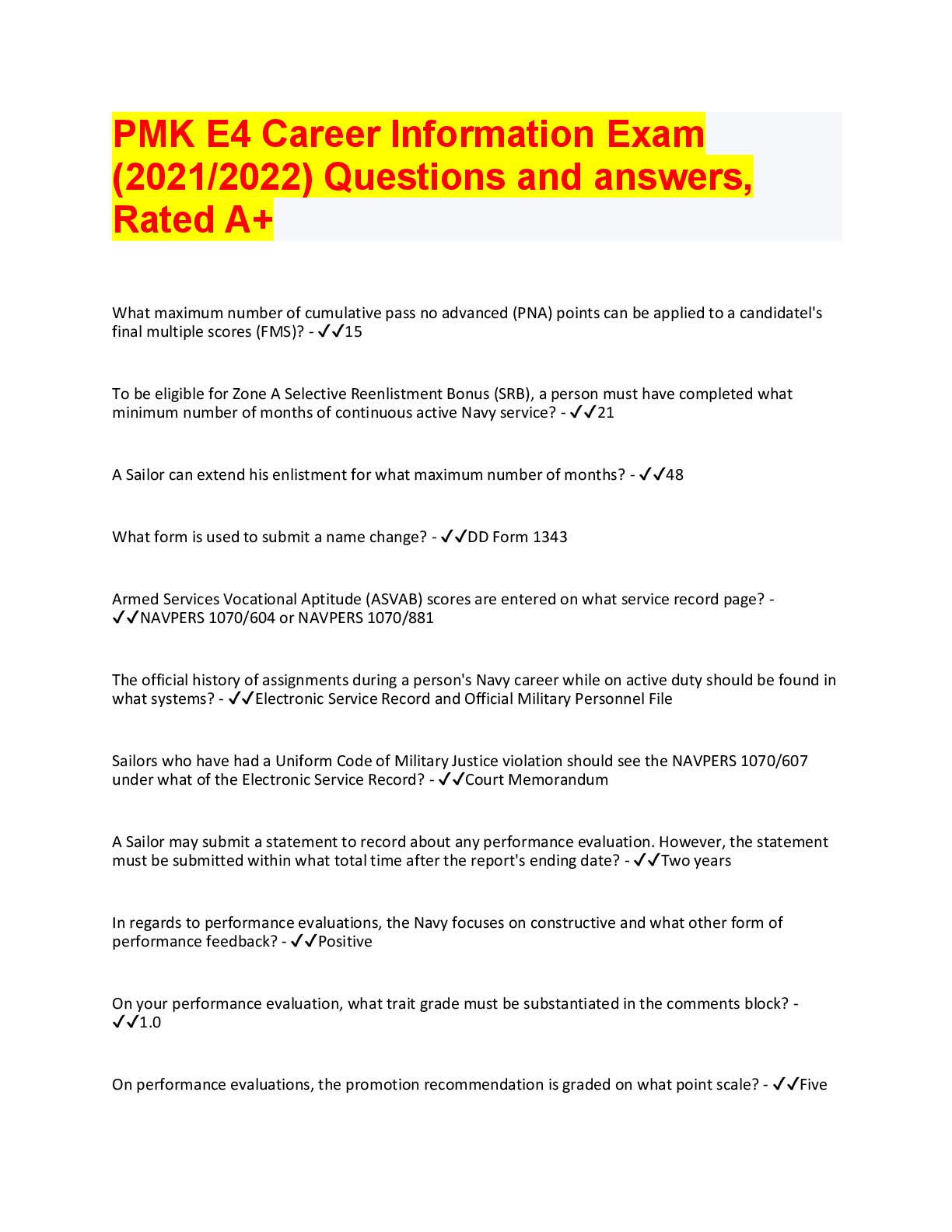
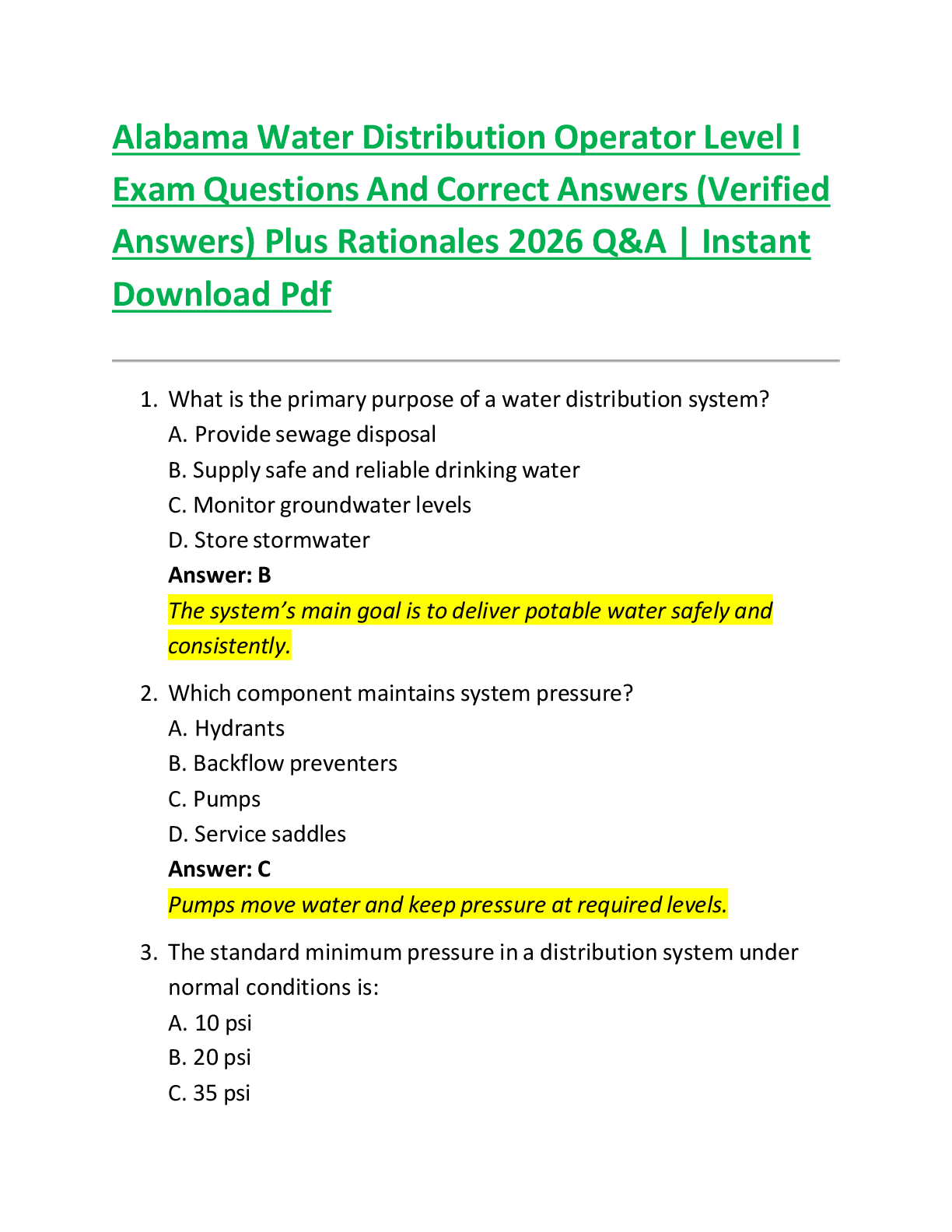
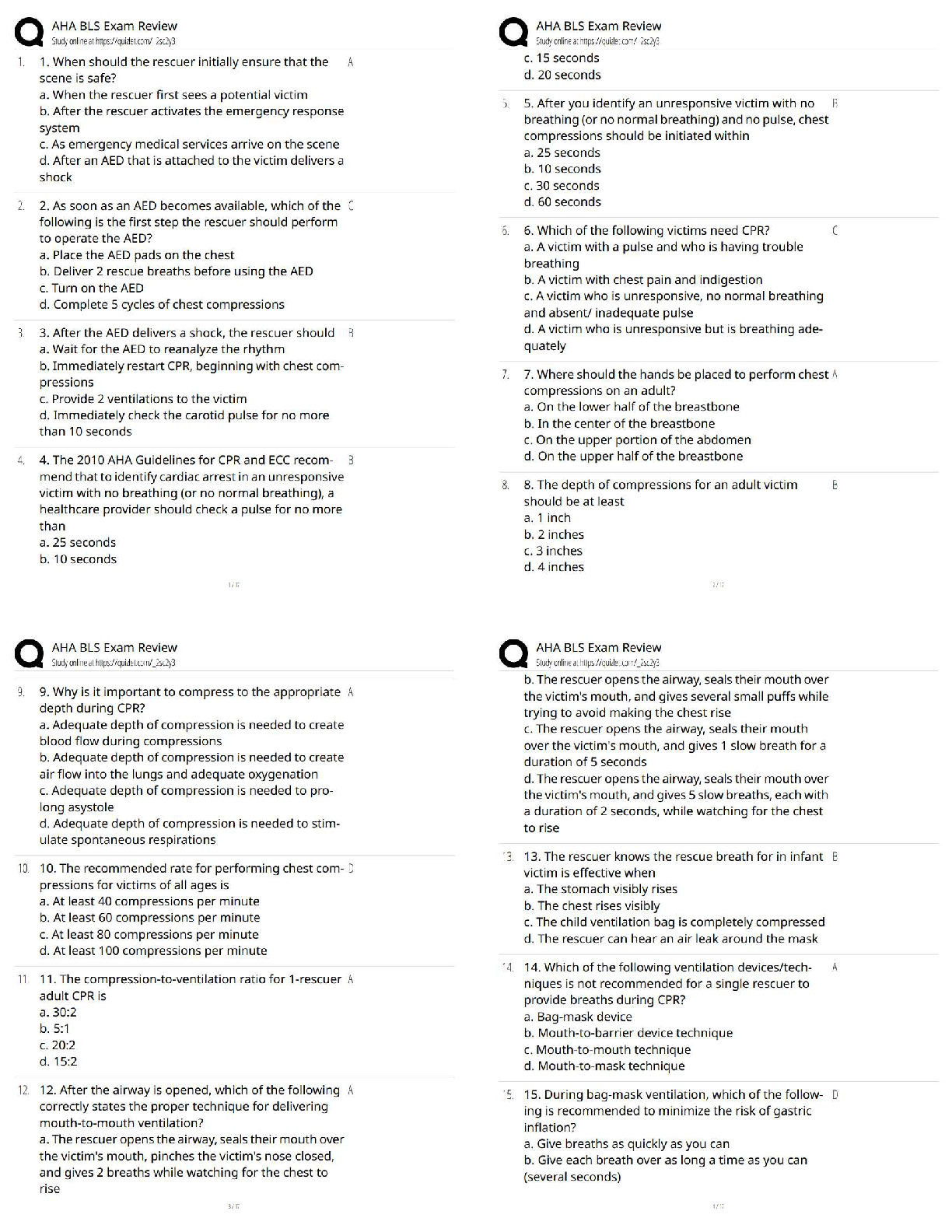
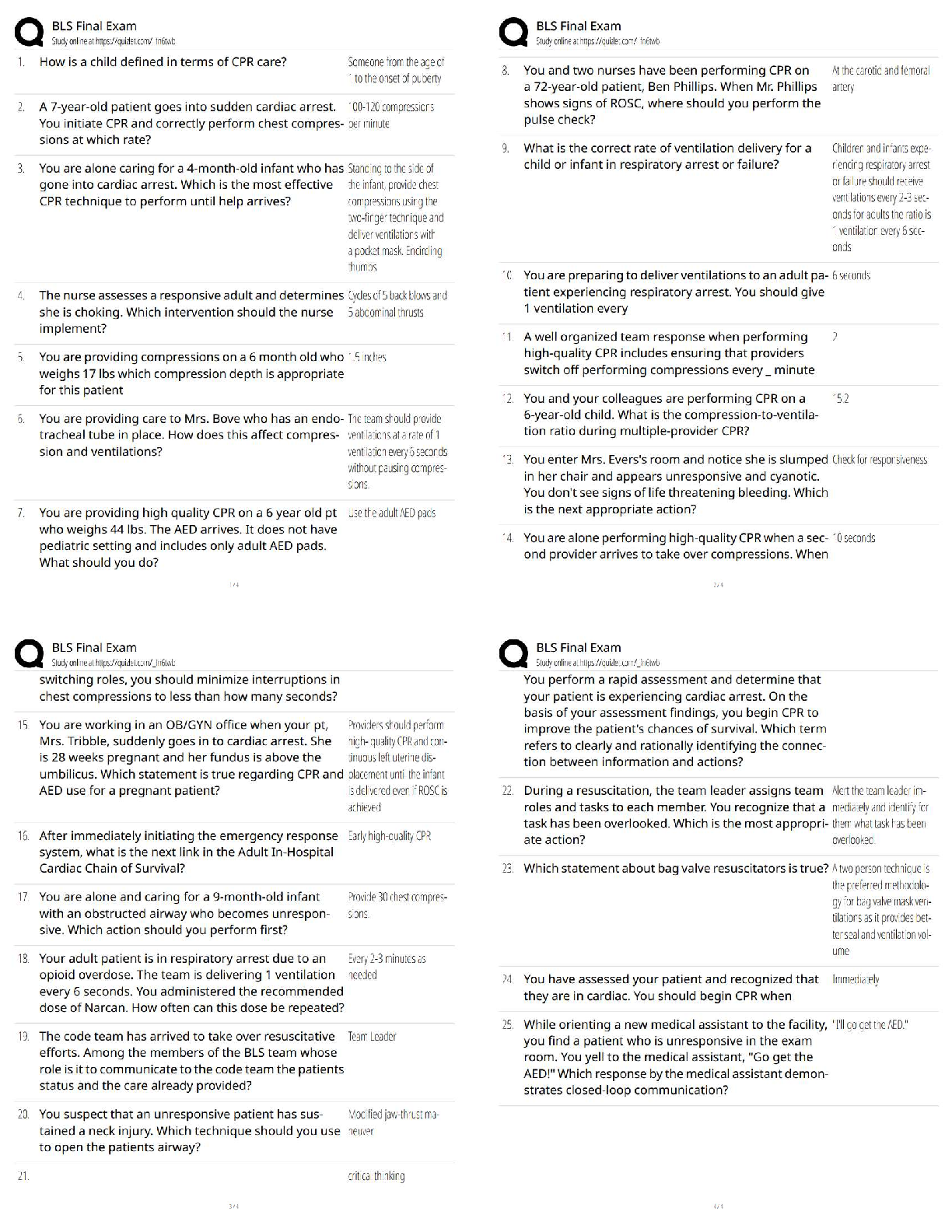
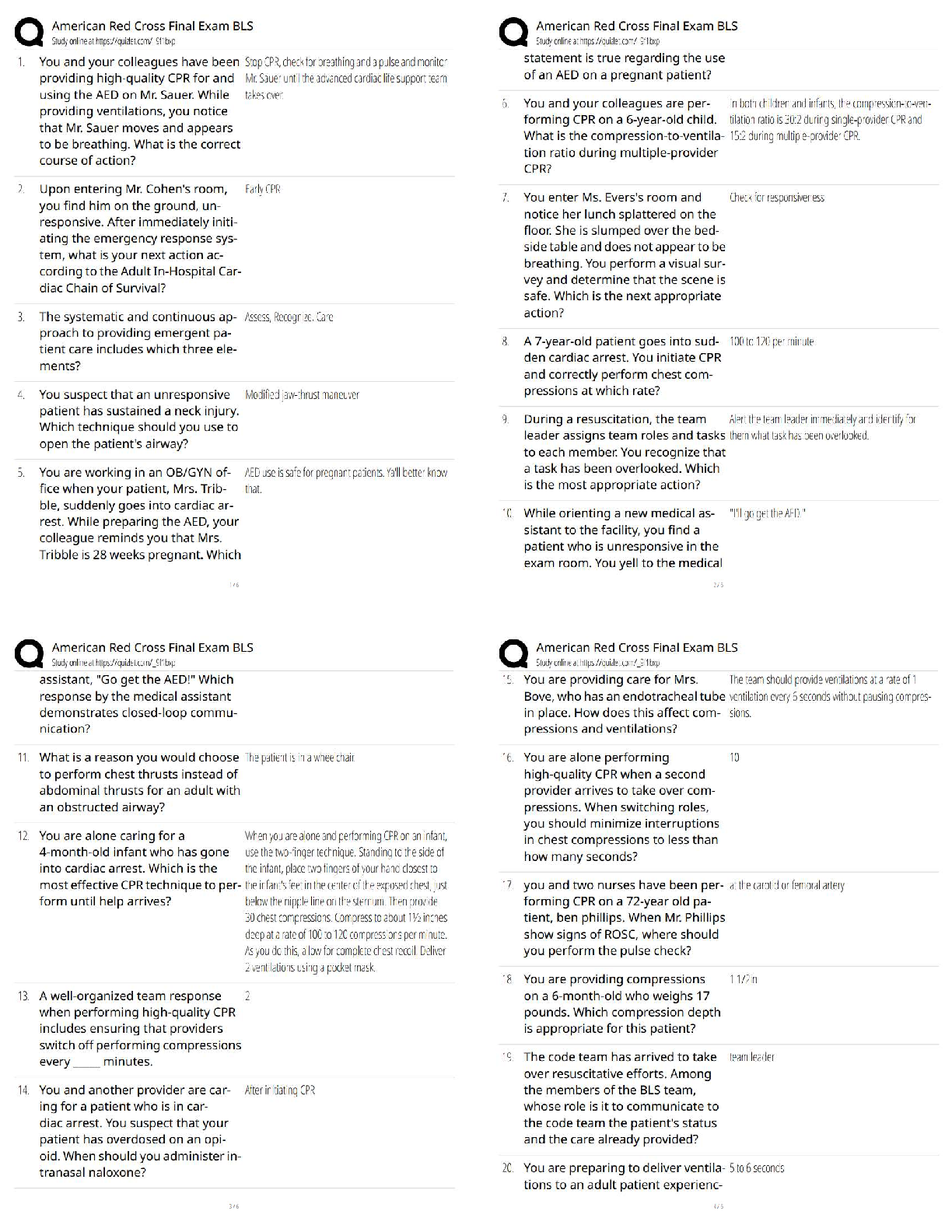
DoD Information Security and Insider Threat Answered 2022 (100% Correct) 1. Authorized access may be granted based on a person's ____________ - ✔✔Employment and contractual relationship with Do ... D 2. Which of the following means to deliberately destroy, damage, or obstruct, especially for political or military advantage? - ✔✔Sabotage 3. A member of your team openly discusses her financial difficulties, and her inability to meet her financial obligations. - ✔✔Report the concerning behavior to your security officer 4. Which of the following is a reportable behavioral indicator? - ✔✔Significant change in work habits 5. Which of these may be considered part of the media? - ✔✔Newspaper reporter, blogger, wiki representative 6. Which of these may be targeted by foreign entities? - ✔✔Personnel lists, classified information, list of facility locations 7. A trained elicitor may gather information by exploiting natural human tendencies, such as - ✔✔A desire to appear well-informed, a desire to be polite, a tendency to gossip, a tendency to believe others are honest. 8. Technological advances impact the insider threat by - ✔✔Presenting new security challenges, allowing large amounts of data to be accessed. 9. Which of the following is a technology-related indicator - ✔✔Accessing systems at unusual hours without authorization, and keeping unauthorized back-ups10. Hostile entities may use social media to ______________? - ✔✔build a profile of a person, search for classified information, quickly recruit someone for spying, gather information on personnel 11. You can help reduce technology-associated insider threats by - ✔✔enlisting countermeasures 12. Which of these activities must be reported? - ✔✔bypassing security rules or protocols, inappropriate copying of classified material, unauthorized disclosure of classified material 13. The acronym EAP stands for ____? - ✔✔Employee assistance program 14. Contractors must report which of these to the insider threat program? - ✔✔Efforts to obtain unauthorized access to classified or proprietary information, any contact that suggests the employee may be the target of attempted exploitation by the intelligence service of another country, efforts to compromise a cleared employee, any contact by cleared employees with known or suspected intelligence officers from any country. 15. Which of the following are true about insider threats? - ✔✔threat can included damage through espionage or terrorism, any person with authorized access to DoD resources by virtue of employment, volunteer activities, or contractual relationship; Threat can include unauthorized disclosure of national security information or through the loss or degradation of department resources or capabilities; The threat that an insider will access information without a need to knowl. 16. The transfer of classified or proprietary information to a system not approved for the classification level or unaccredited or unauthorized systems, individuals, applications or media is a - ✔✔Spill 17. Which of the following is considered a potential insider threat vulnerability? - ✔✔Gambling addiction, disgruntlement, promiscuity, substance abuse 18. Most inside offenders display concerning behaviors before acting directly against their organization. This behavior may include - ✔✔Failure to follow standard procedures (SOP); legal difficulties; violations of workplace policies19. To whom should you report if you are contacted by a member of the media about information you are not authorized to share? - ✔✔Your security office 20. Which of the following are things that adversaries want to know? - ✔✔Countries your organization works with; your organization personnel [Show More]
Last updated: 3 years ago
Preview 1 out of 6 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$7.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Sep 03, 2022
Number of pages
6
Written in
All
Seller

Reviews Received
Additional information
This document has been written for:
Uploaded
Sep 03, 2022
Downloads
0
Views
113